Challenge name:23333!
难度:Easy
考点:文件十六进制、零宽隐写
WriteUp:
-
Winhex打开发现明显特征:
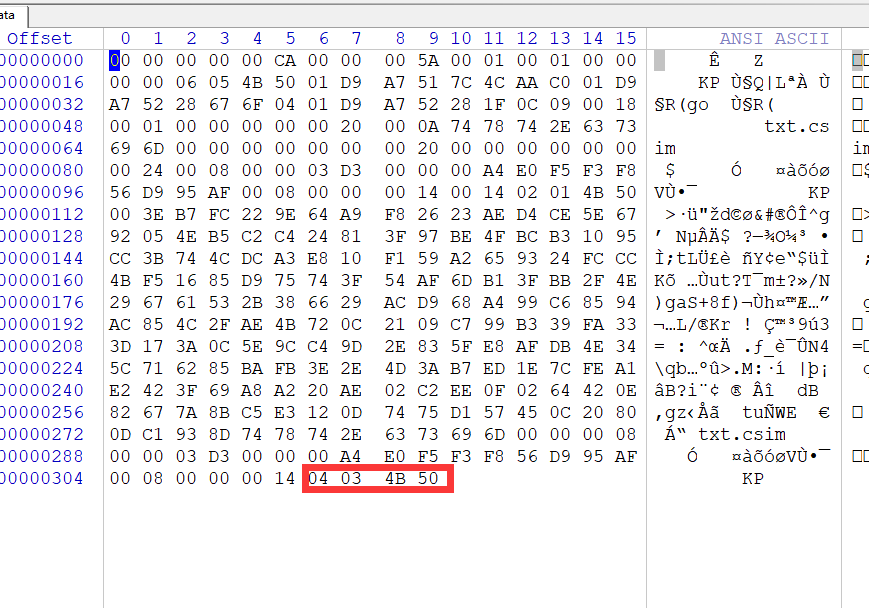
-
编写脚本进行恢复:
input = open(data', 'rb') input_all = input.read() ss = input_all[::-1] output = open('data.zip', 'wb') output.write(ss) input.close() output.close() -
vim,打开:零宽隐写:
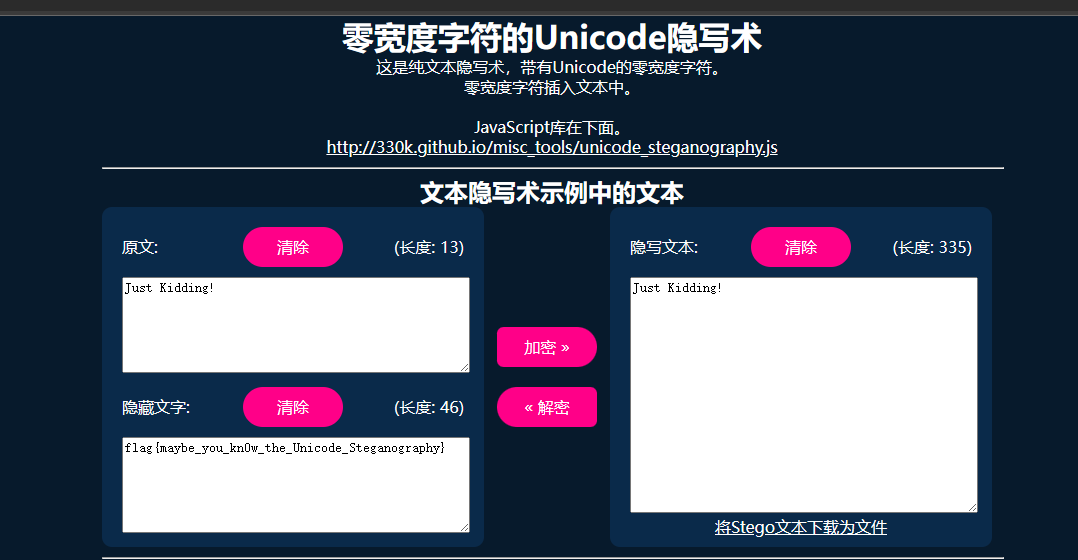
Challenge name:The game of mathematics
难度:Middle
考点:Fuzz
WriteUp:
解压得到key.jpg,是个数独,在线数独求解器 (gwalker.cn)
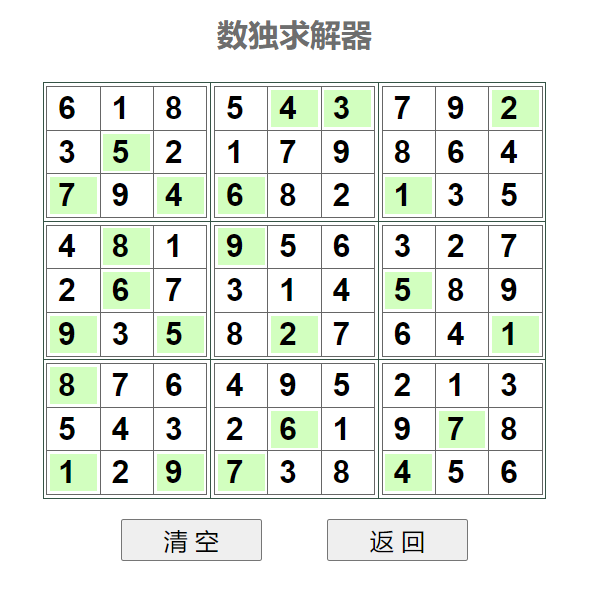
exif信息里找到提示对角线,根据之前求解的数独结果,得到密码为654917276261618641
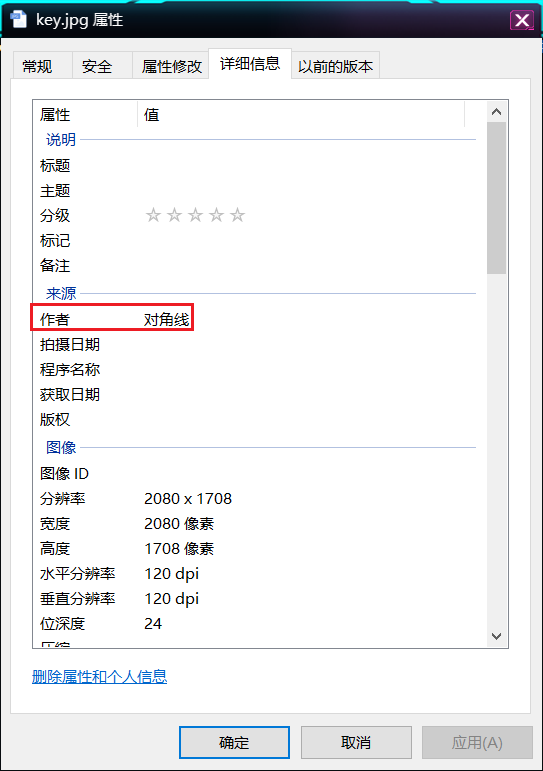
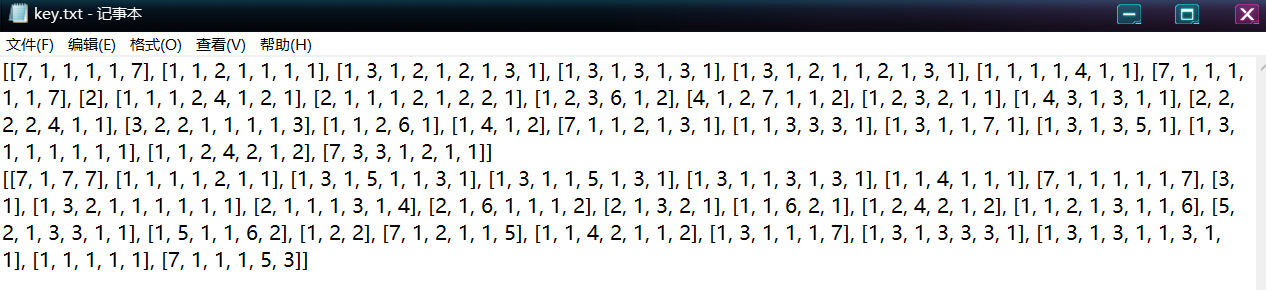
得到一个key.txt,根据题目名称数学游戏,猜测也是个数学游戏,fuzz之后发现是Nonogram数织游戏
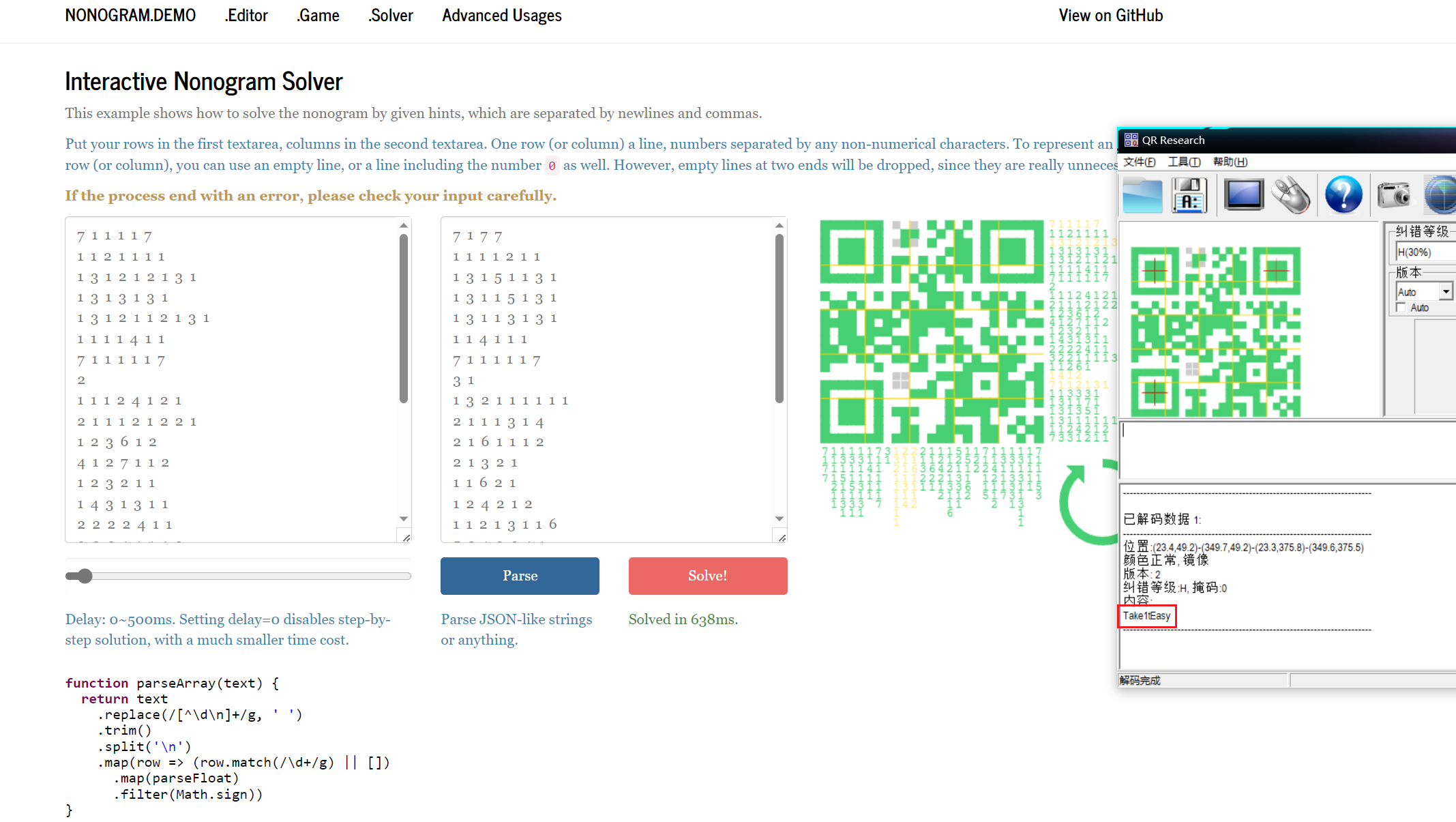
github上可以找到个解析的网站Nonogram (handsomeone.github.io),得到压缩包密码Take1tEasy
解开得到flag
flag{c6ebcf84bcd54bac0803086a4630f673}Challenge name:This is Steganography
难度:Middle
考点:LSB音频隐写、webdings字体
WriteUp:
听wav开头有一些杂音,16进制发现data部分有大量不同寻常的01字节
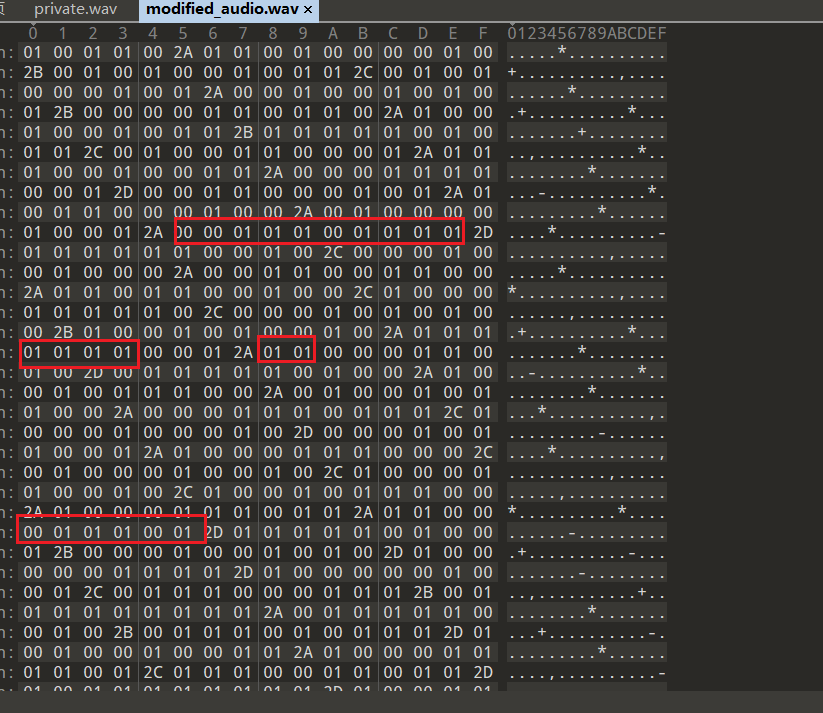
猜测是wav的lsb隐写,写脚本提取
import wave
def read_wav_file(file_path):
with wave.open(file_path, 'rb') as wav_file:
params = wav_file.getparams()
frames = wav_file.readframes(wav_file.getnframes())
return params, frames
def extract_data(frames):
binary_data = ''
for frame in frames:
binary_frame = format(frame, '08b')
binary_data += binary_frame[-1]
return binary_data
def binary_to_bytes(binary_data):
byte_data = bytearray()
for i in range(0, len(binary_data), 8):
byte = binary_data[i:i+8]
byte_data.append(int(byte, 2))
return bytes(byte_data)
def save_data_to_file(data, file_path):
with open(file_path, 'wb') as output_file:
output_file.write(data)
def main():
modified_file_path = 'modified_audio.wav'
params, frames = read_wav_file(modified_file_path)
extracted_data = extract_data(frames)
byte_data = binary_to_bytes(extracted_data)
output_file_path = 'extracted_data.png'
save_data_to_file(byte_data, output_file_path)
print("成功提取隐藏的数据并保存到文件。")
if __name__ == '__main__':
main()
得到一张倒置的图片,是webdings字体(13条消息) 'Webdings' 的字体对照表_webdings字体_chenjieit619的博客-CSDN博客
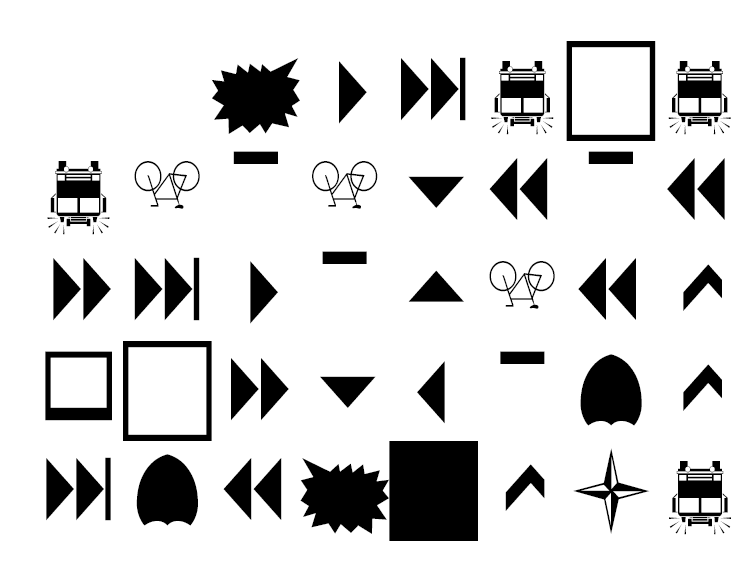
倒置回来后对照表即可得到flag
flag{8d9ad0457c1a8b603978085b0bffcf93}Challenge name:You're also confused, right?
难度:Schrödinger
考点:Xor
WriteUp
根据题目提示,应该与异或有关,根据flag.zip后缀提示,将前几个字节与zip文件头异或
可以得到1234
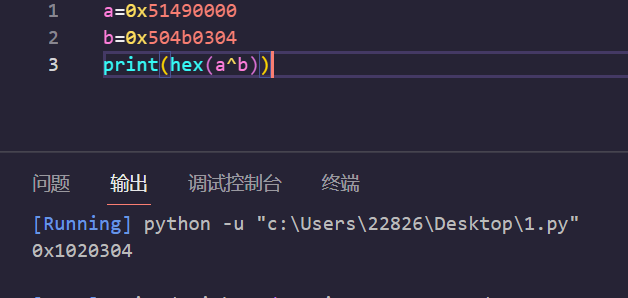
猜测zip文件应该是与0x01-0xff递增逐字节异或的,解密脚本:
with open('flag.zip', 'rb') as input_file, open('result.zip', 'wb') as output_file:
byte = input_file.read(1)
xor_value = 0x01
while byte:
xor_byte = bytes([byte[0] ^ xor_value])
output_file.write(xor_byte)
byte = input_file.read(1)
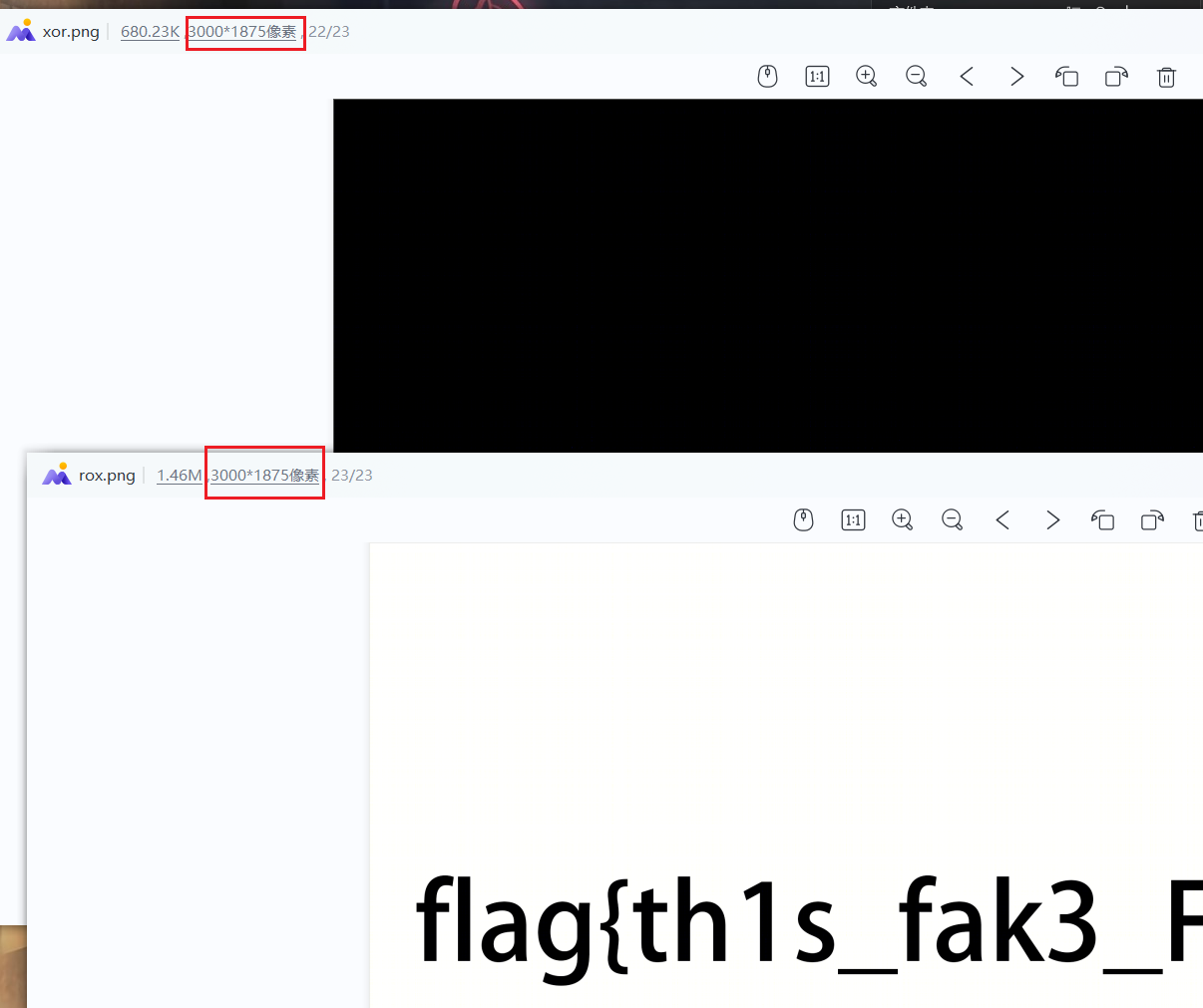
xor_value = (xor_value + 1) % 256 压缩包解开可以得到两张图
发现两张图大小相同,
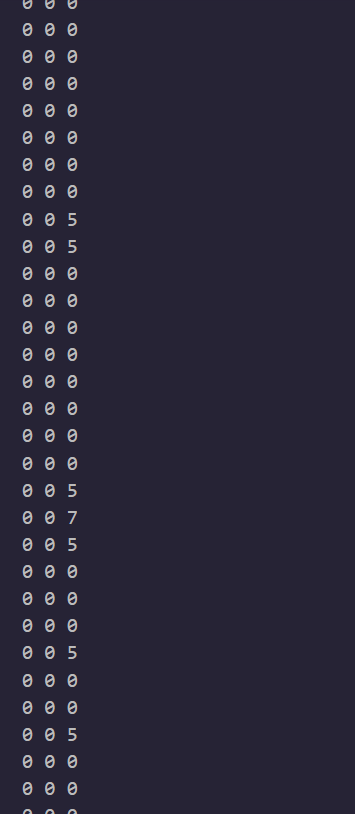
打印xor.png的rgb发现这张图并不是一张全黑的图
结合图片名仍跟异或有关,将两张图逐像素异或
from PIL import Image
image1 = Image.open('xor.png').convert('RGB')
pixels1 = image1.load()
image2 = Image.open('rox.png').convert('RGB')
pixels2 = image2.load()
result_image = Image.new('RGB', image1.size)
result_pixels = result_image.load()
width, height = image1.size
for x in range(width):
for y in range(height):
r1, g1, b1 = pixels1[x, y]
r2, g2, b2 = pixels2[x, y]
r_xor = r1 ^ r2
g_xor = g1 ^ g2
b_xor = b1 ^ b2
result_pixels[x, y] = (r_xor, g_xor, b_xor)
result_image.save('result.png')
得到的图片与rox.png做盲水印得到flag
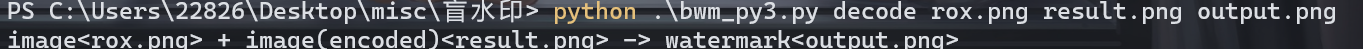
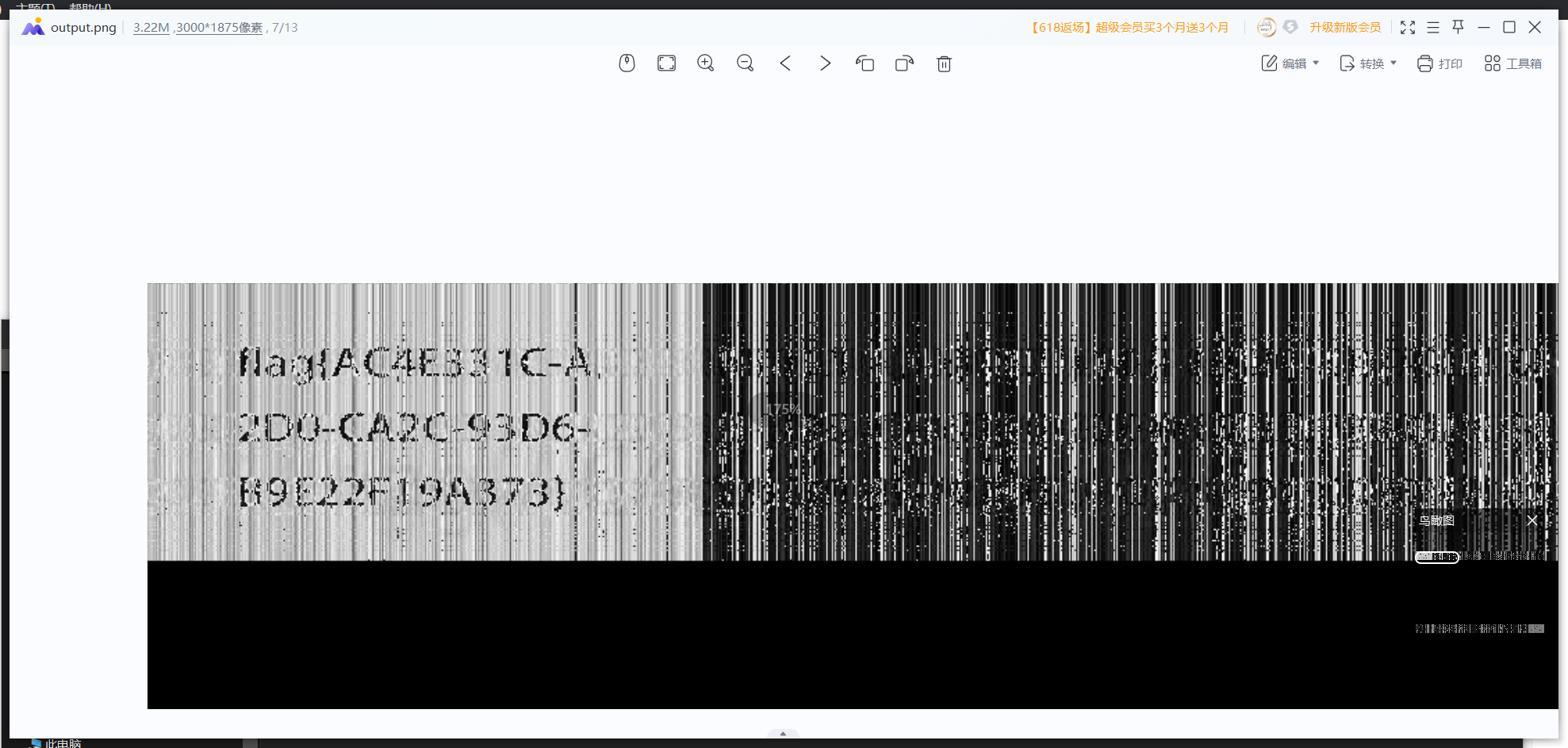
flag{AC4E331C-A2D0-CA2C-93D6-B9E22F19A373}

