不是鸽们,真有人为热爱而战啊???
png_master

有两个可疑的地方,先看第一个,有一段base64
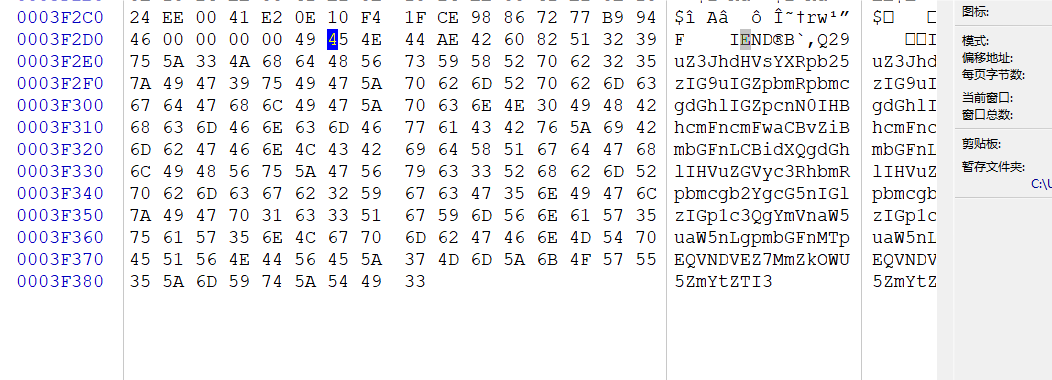
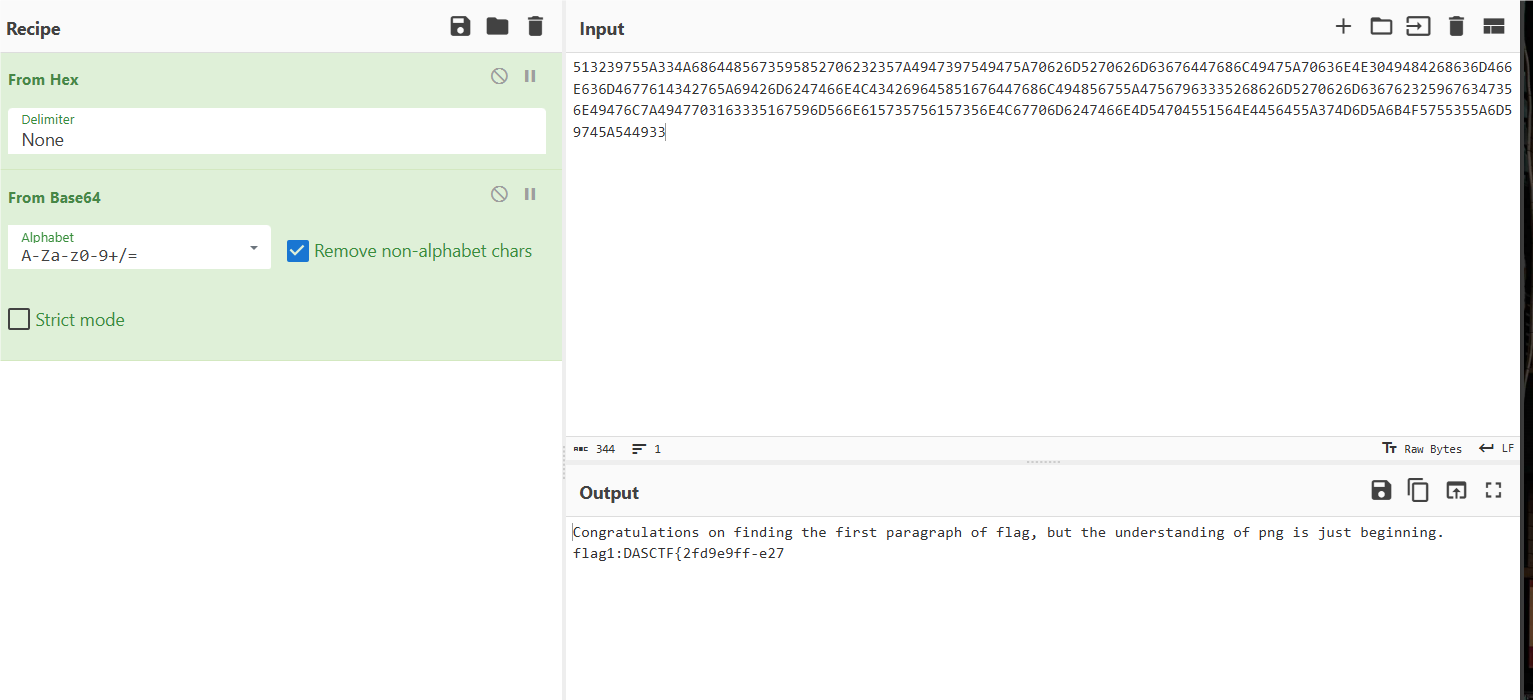
得到第一段flag
第二个是IDAT块异常,导出看一下
补全文件头文件尾爆破PNG宽高:
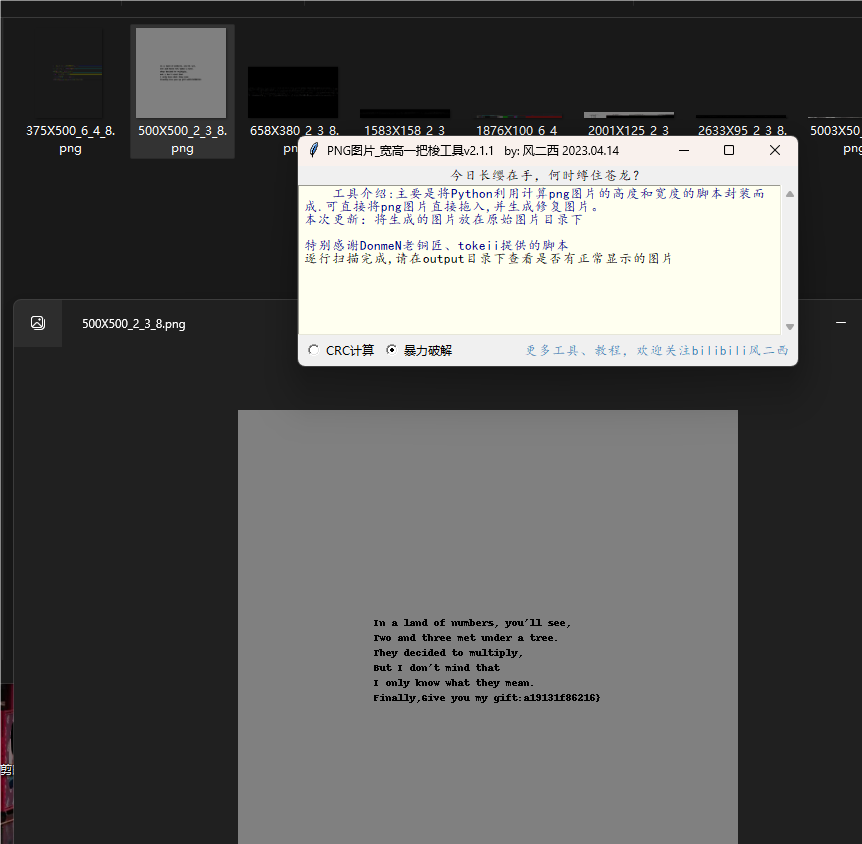
得到了第三段flag
中间缺一部分,把原图拖进stegsolve查看发现alpha plane 0-7左上角均有异常,勾选查看:
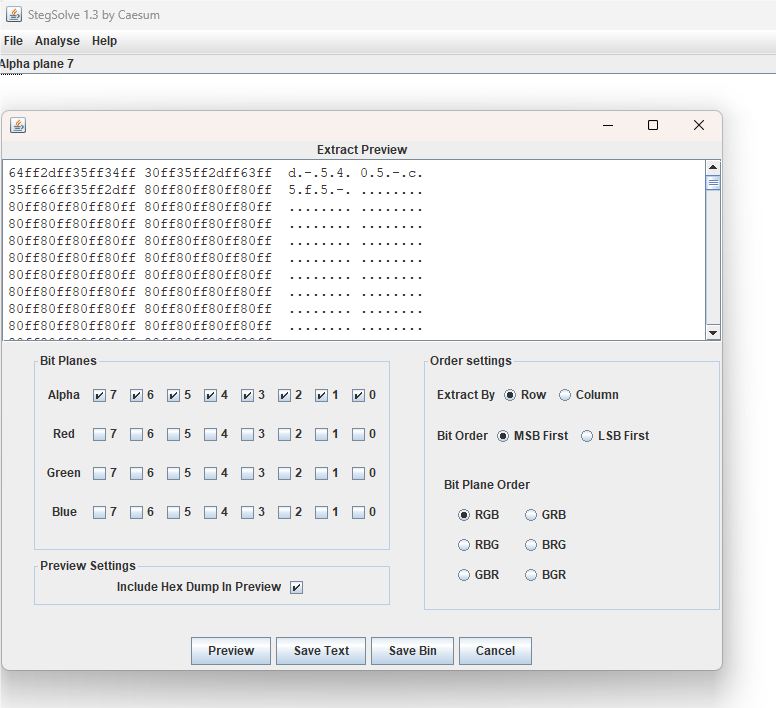
得到第二部分flag
拼接起来:
DASCTF{2fd9e9ff-e27d-5405-c5f5-a19131f86216}
Ez_zip
简单修复一下:
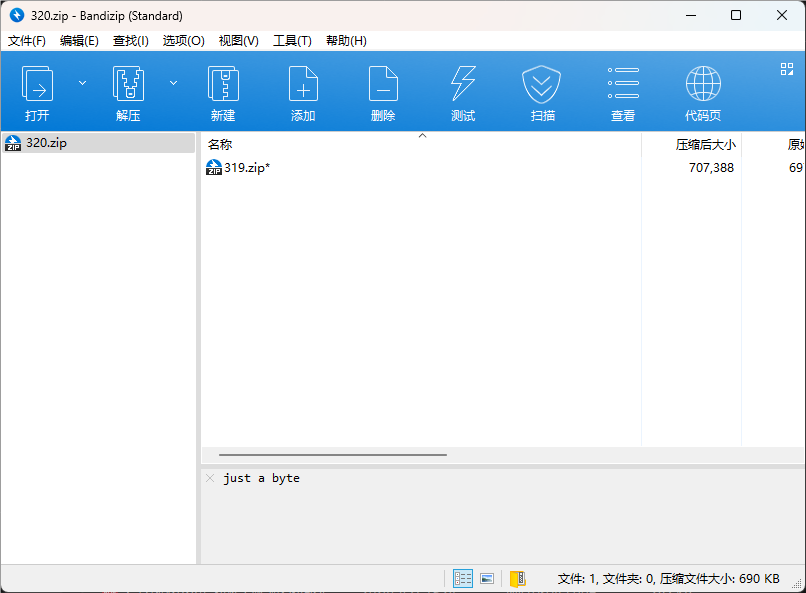
有注释,just a byte
这个地方应该是说密码是byte的意思,所以爆破也挺简单的
遛一遛GPT
import os
import pyzipper
def decrypt_archive_with_hex_key(archive_path, hex_key):
"""Attempts to decrypt a zip file using the given hexadecimal key."""
cipher_key = bytes.from_hex(hex_key)
current_dir = os.get_cwd()
with pyzipper.AESZipFile(archive_path) as encrypted_archive:
encrypted_archive.setpassword(cipher_key)
os.chdir(current_dir)
try:
encrypted_archive.extract_all()
log_message = f"Decryption successful for '{archive_path}' with key: {hex_key}"
print(log_message)
record_decryption_key(hex_key)
return True
except RuntimeError:
# Optionally log decryption failures here
pass
finally:
os.chdir(current_dir)
def record_decryption_key(decryption_key):
"""Records the decryption key used for a successful decryption."""
with open('decryptionKeys.txt', 'a') as key_file:
key_file.write(str(bytes.from_hex(decryption_key)) + '\n')
def iterate_and_decrypt_archives():
"""Iterates over archives from 320.zip down to 0.zip, attempting decryption with keys from 0 to 255."""
for archive_index in reversed(range(321)):
archive_name = f"{archive_index}.zip"
for key_index in range(256):
hex_key = f'{key_index:02x}'
if decrypt_archive_with_hex_key(archive_name, hex_key):
break
if __name__ == "__main__":
iterate_and_decrypt_archives()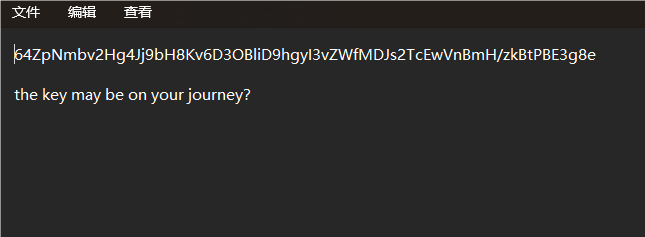
看起来和解密密钥有关系。
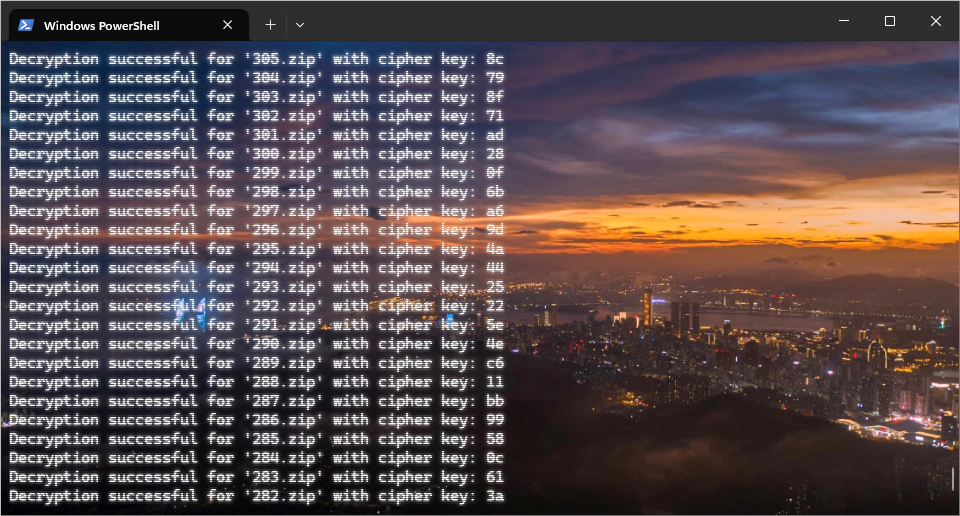
然后发现了密钥是循环的,从11 BB ......4E C6,这样的话,提取出来就是:
11bb9985c016a3785ce42184a07affc897f817da82f0b66ad9a4445222e5e46c
但是AES解密不对,结果要把密钥反过来:
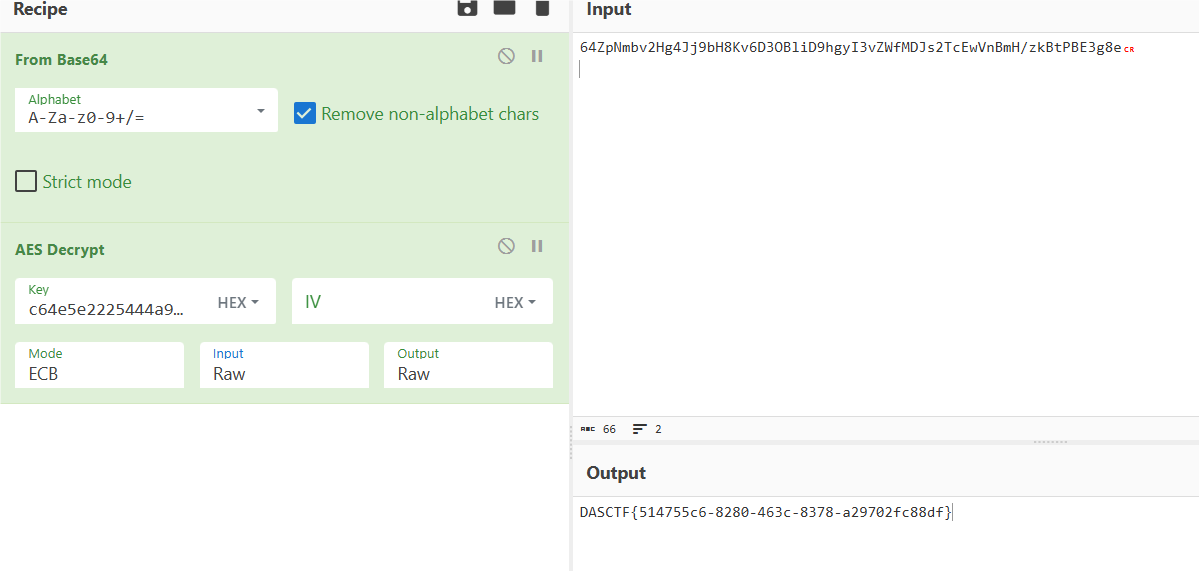
DASCTF{514755c6-8280-463c-8378-a29702fc88df}
ServerMem
Linux内存取证,要做符号表,但其实可以不用,直接strings就好了
个人习惯先过一遍可疑文件:
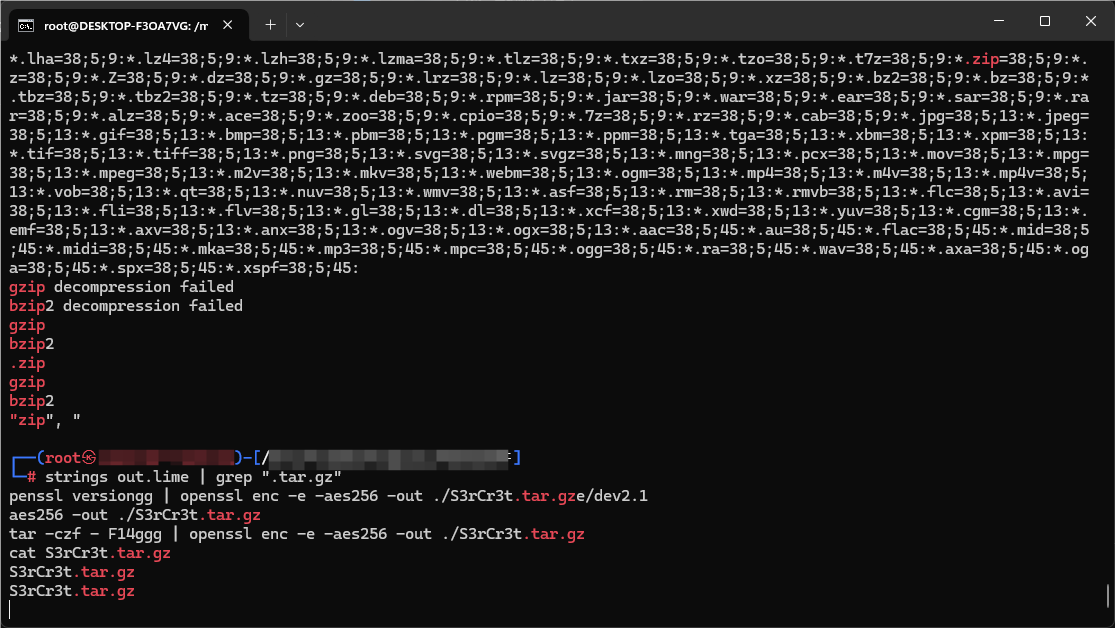
发现有个这个S3rCr3t.tar.gz,并且说明了加密类型是openssl的aes256,经过这种加密的特征就是Salted_加盐值,拖进winhex里:
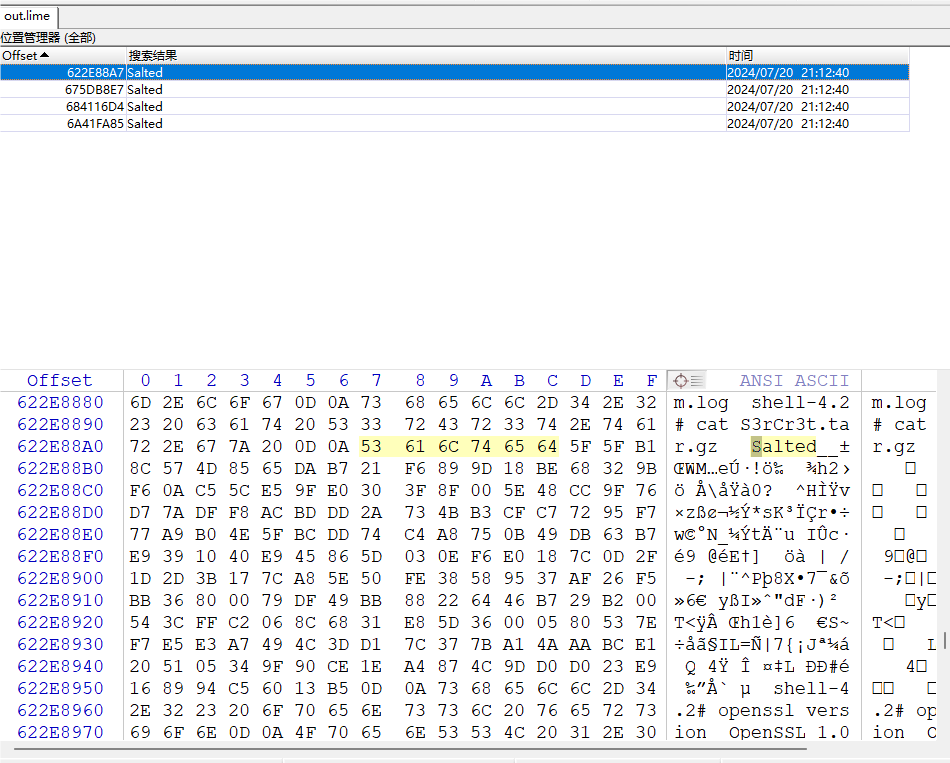
发现有命令,导出来:
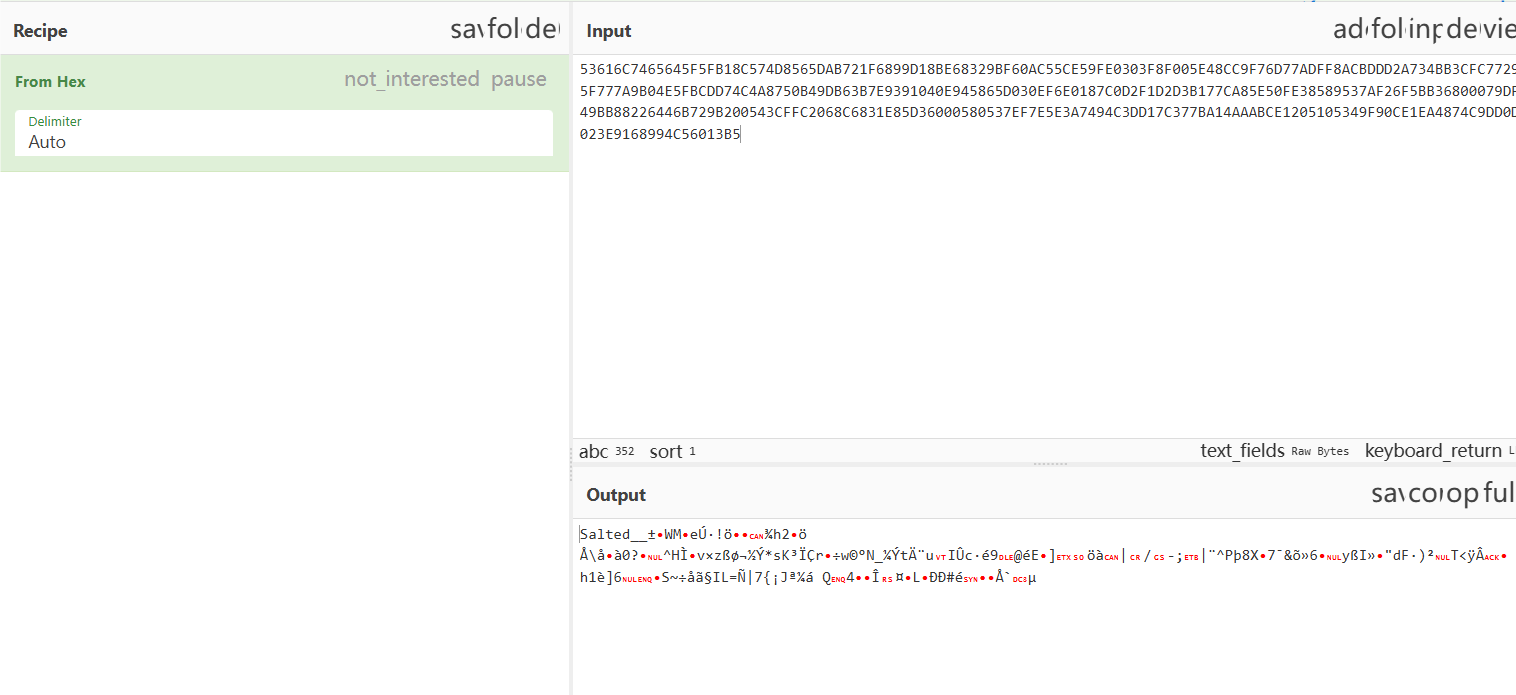
OK,剩下的就是爆搜密钥了,ctfer常见的密钥:keyDASCTFPassword 然后在这里面加数字呗,这样写个脚本就好了:
import re
# 要搜索的字符列表
search_terms = [
b"key", b"password", b"dasctf", b"k3y", b"p@ssword", b"passw0rd",
b"p@ssw0rd", b"secret", b"s3cret", b"s3cr3t", b"s3cre4"#遇到一个加一个,CTFer的好习惯
]
# 要搜索的文件路径
file_path = "out.lime"
# 读取文件内容
with open(file_path, "rb") as file:
data = file.read()
# 搜索字符并打印结果
for term in search_terms:
# 后面可以跟随任意字符的模式
regex = re.compile(re.escape(term) + b".*", re.IGNORECASE)
for match in regex.finditer(data):
matched_text = match.group()
print(f"Found '{term.decode()}' match: {matched_text[:50]}...") # 只显示前50个字节
# 内存取证是这样的,而我们非预期选手考虑的就很多了
找到了密钥:P@ssW0rdddd
然后就是OpenSSL还得用原来版本的进行解密,CentOS镜像我没拉取下来,于是直接更换了某个docker里openssl
https://blog.csdn.net/weixin_44174099/article/details/122089980
更换成功,有命令,直接解密就好了
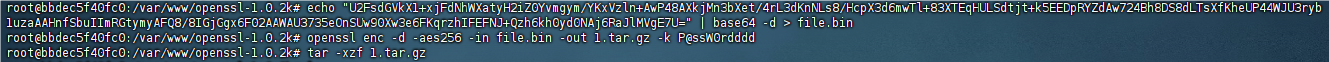

DASCTF{c086cd55-b86a-4ee6-8933-c8bee578148a}

