MemLabs Lab 4 | Obsession
下载链接:MemLabs_Lab4
Challenge Descryption
My system was recently compromised. The Hacker stole a lot of information but he also deleted a very important file of mine. I have no idea on how to recover it. The only evidence we have, at this point of time is this memory dump. Please help me.
Note : This challenge is composed of only 1 flag.
The flag format for this lab is: inctf{s0me_l33t_Str1ng}
我的系统最近遭到入侵。黑客窃取了很多信息,但他还删除了我的一个非常重要的文件。我不知道如何恢复它。目前我们拥有的唯一证据就是这个内存转储。请帮我。
Progress
Flag
不多谈了好吧:
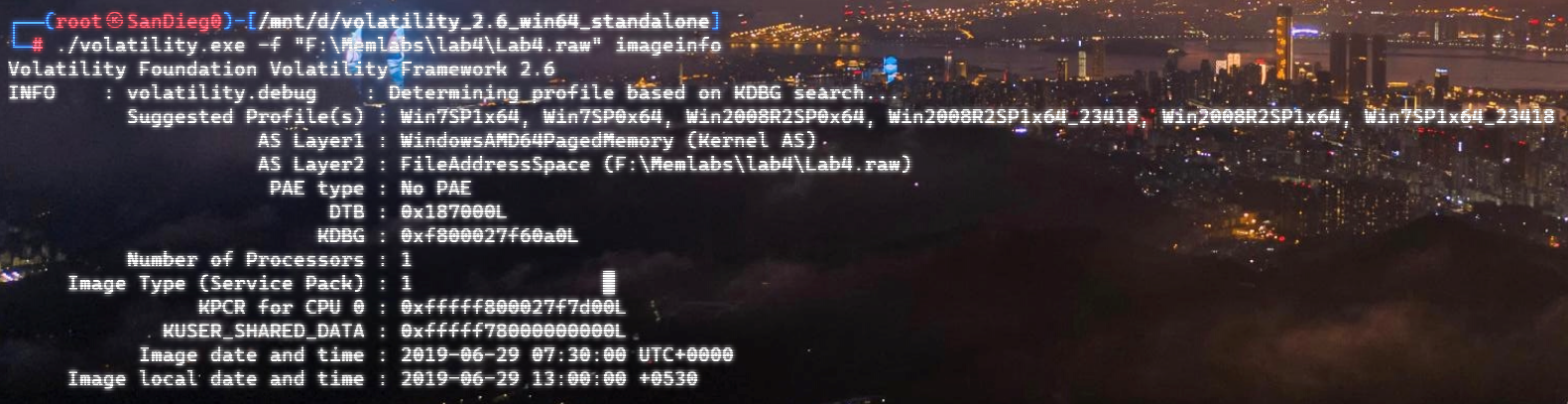
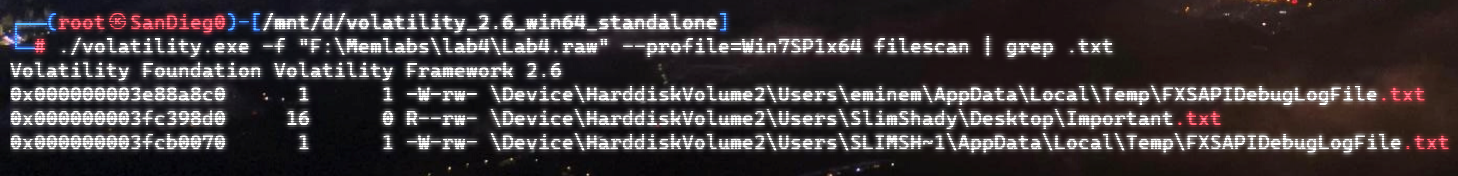
嗨嗨嗨,运气~
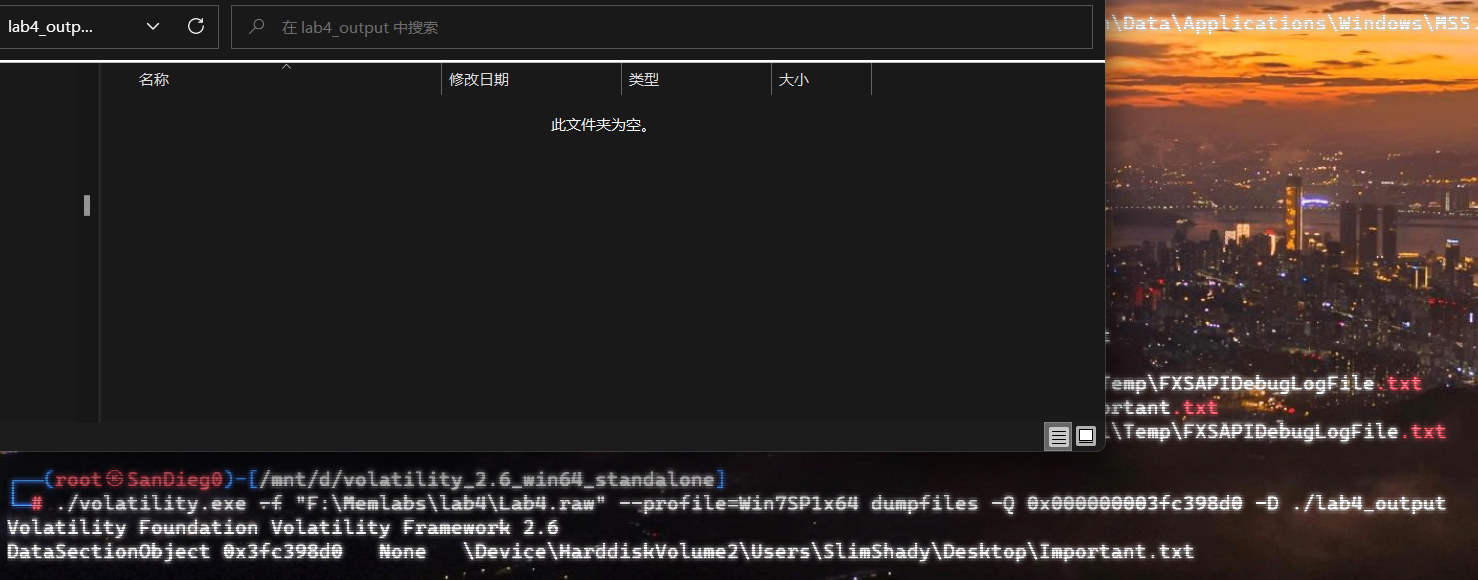
结合描述,文件被删除了,尝试恢复一下。
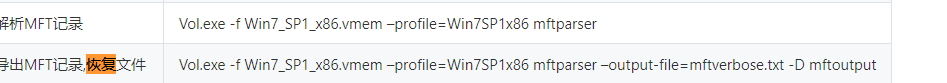
说一下 MFT表:
- NTFS文件系统包含一个叫主文件表(Master File Table)的文件,简称为MFT。对于在 NTFS 文件系统卷上的每个文件,在 MFT 中都至少会有一个条目。 MFT 条目会存储文件所有的信息,包括名称、大小、时间、时间戳、权限和数据内容,或者会存储在 MFT 条目所描述的 MFT 之外的空间。
- 随着文件被添加到 NTFS 文件系统卷,会有更多的条目添加到 MFT ,并且 MFT 大小也会随之增加。但是当从 NTFS 卷中删除文件时,它们的 MFT 条目会被重新标记为空闲状态,并且可以重复使用。但是已为这些条目分配的磁盘空间是不会再重新分配的,并且 MFT 的空间不会减小。
- 文件大小 小于等于 1024字节的文件,会直接存储在 MFT 表中(称为 驻留文件),如果超过1024字节,MFT 表就会包含其位置信息,不会存储文件。(称为 非驻留文件)
在volatility中提供了mftparser插件来查看系统的 MFT表:
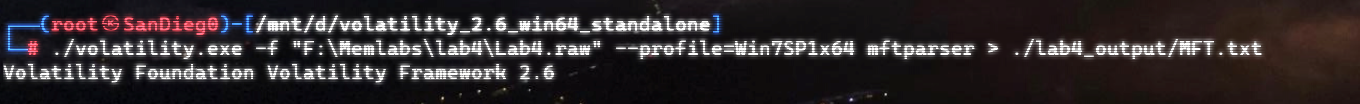

字符串分散开了:inctf{1_is_n0t_EQu4l_7o_2_bUt_th1s_d0s3nt_m4ke_s3ns3}
MemLabs Lab 5 | Black Tuesday
下载链接:MemLabs Lab 5
Challenge Description
We received this memory dump from our client recently. Someone accessed his system when he was not there and he found some rather strange files being accessed. Find those files and they might be useful. I quote his exact statement,
The names were not readable. They were composed of alphabets and numbers but I wasn't able to make out what exactly it was.Also, he noticed his most loved application that he always used crashed every time he ran it. Was it a virus?
Note-1 : This challenge is composed of 3 flags. If you think 2nd flag is the end, it isn't!! 😛
Note-2 : There was a small mistake when making this challenge. If you find any string which has the string " L4B_3_D0n3 !! " in it, please change it to " L4B_5_D0n3 !! " and then proceed.
Note-3 : You'll get the stage 2 flag only when you have the stage 1 flag.
最近我们从客户那里收到了这个内存转储。有人趁他不在时访问了他的系统,客户发现一些相当奇怪的文件正在被访问。找到这些文件,它们可能很有用。客户的原话是这样:
名字不可读。它们由字母和数字组成,但我不清楚它到底是什么。
注 1 :此挑战由 3 个flag组成。如果您认为第二个标志是结束,它不是!:P、
注 2:挑战时有一个小错误。如果您发现任何包含字符串“ L4B_3_D0n3 !! ”的字符串,请将其更改为“ L4B_5_D0n3 !! ”然后继续。
注意 3 :只有当您拥有flag1时,您才会获得flag2。
Progress
Flag 1
不想说了:
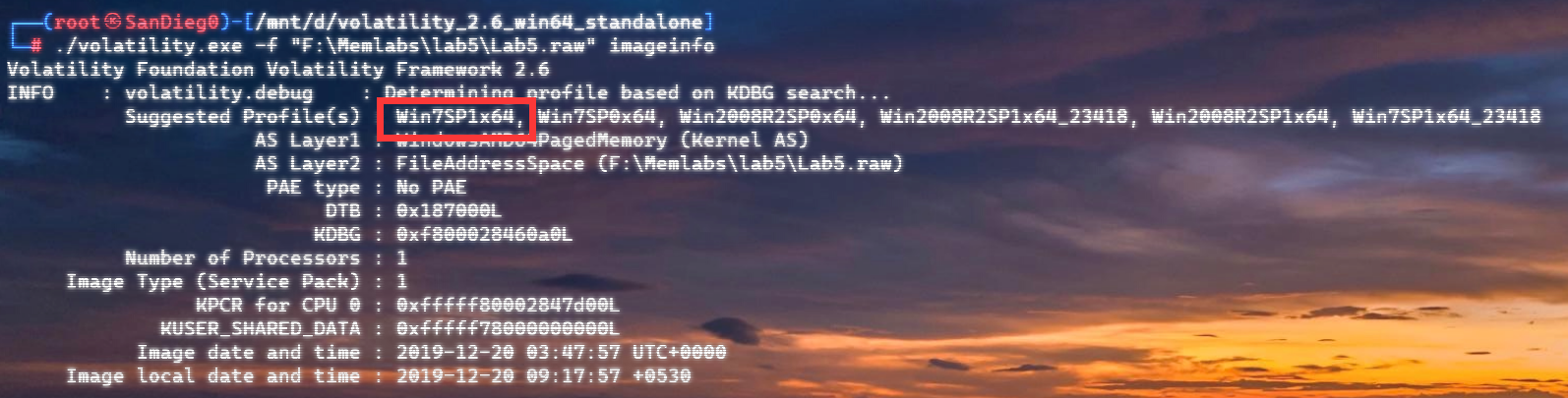
pslist

看到了特殊的进程,查看了命令行历史:
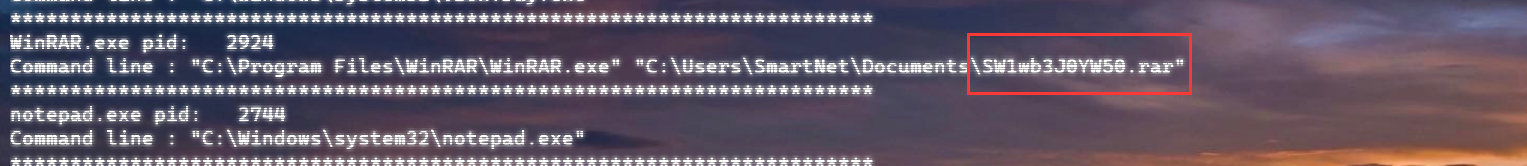
确实不可读🤔,提取出来:
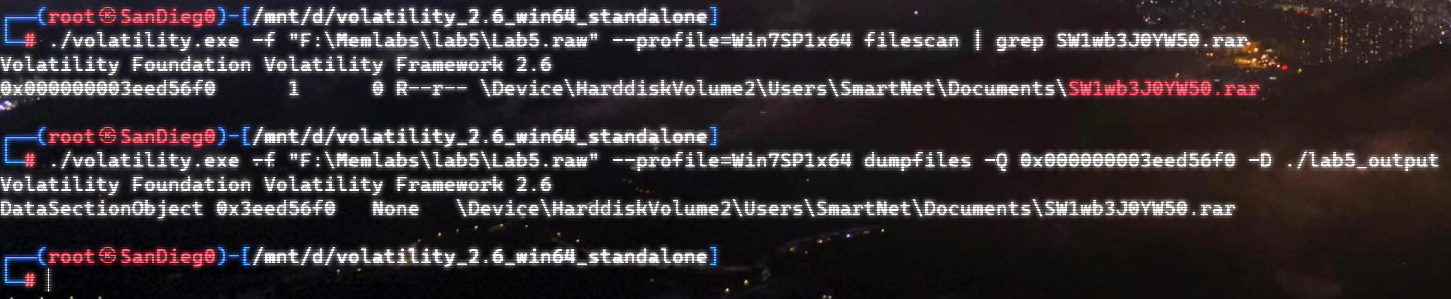
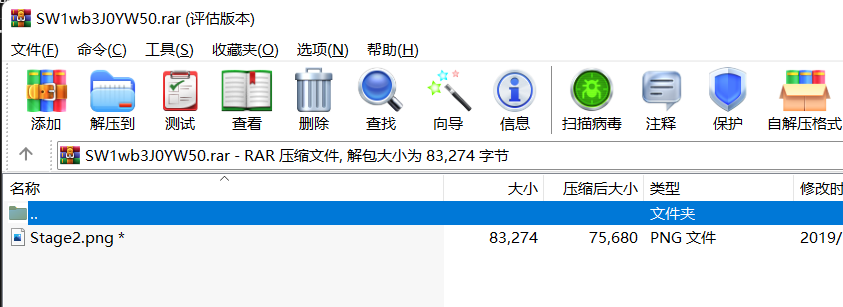
emm,Stage2.png 看来是第二部分了,还得去找第一部分。
这个地方用到了iehistory(想不到吧:P)
iehistory插件可以恢复IE浏览器的历史 index.dat 缓存文件的片段。iehistory可以提取基本的访问协议(如http、ftp等)链接、重定向链接(-REDR)和已删除条目(-LEAK)。此外,不仅仅是IE浏览器,它适用于任何加载和使用的 winnet.dll库 的进程,通常包括 Windows 资源管理器 甚至恶意软件样本。
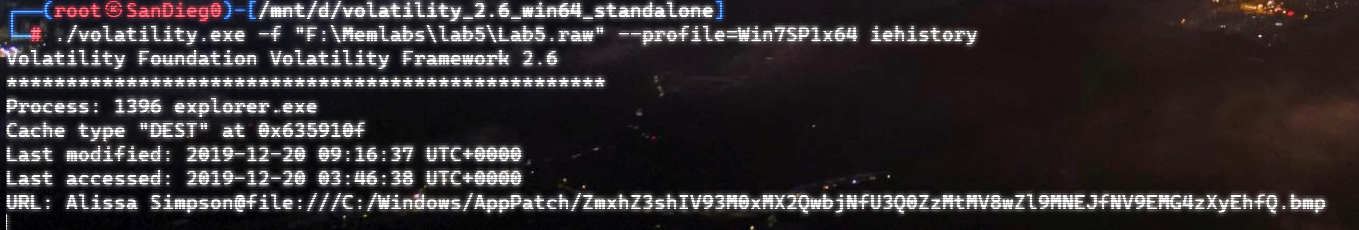
运气不错,熟悉的base64:
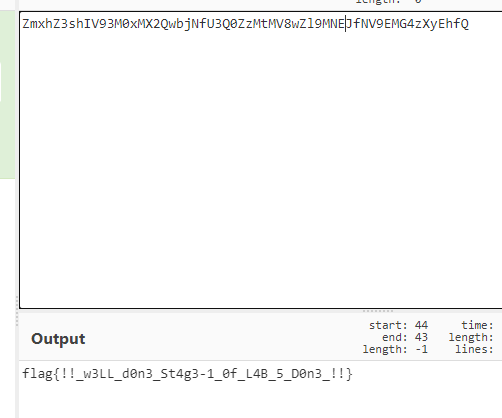
flag{!!_w3LL_d0n3_St4g3-1_0f_L4B_5D0n3!!}
Flag 2
有了第一个flag,去解密压缩包:
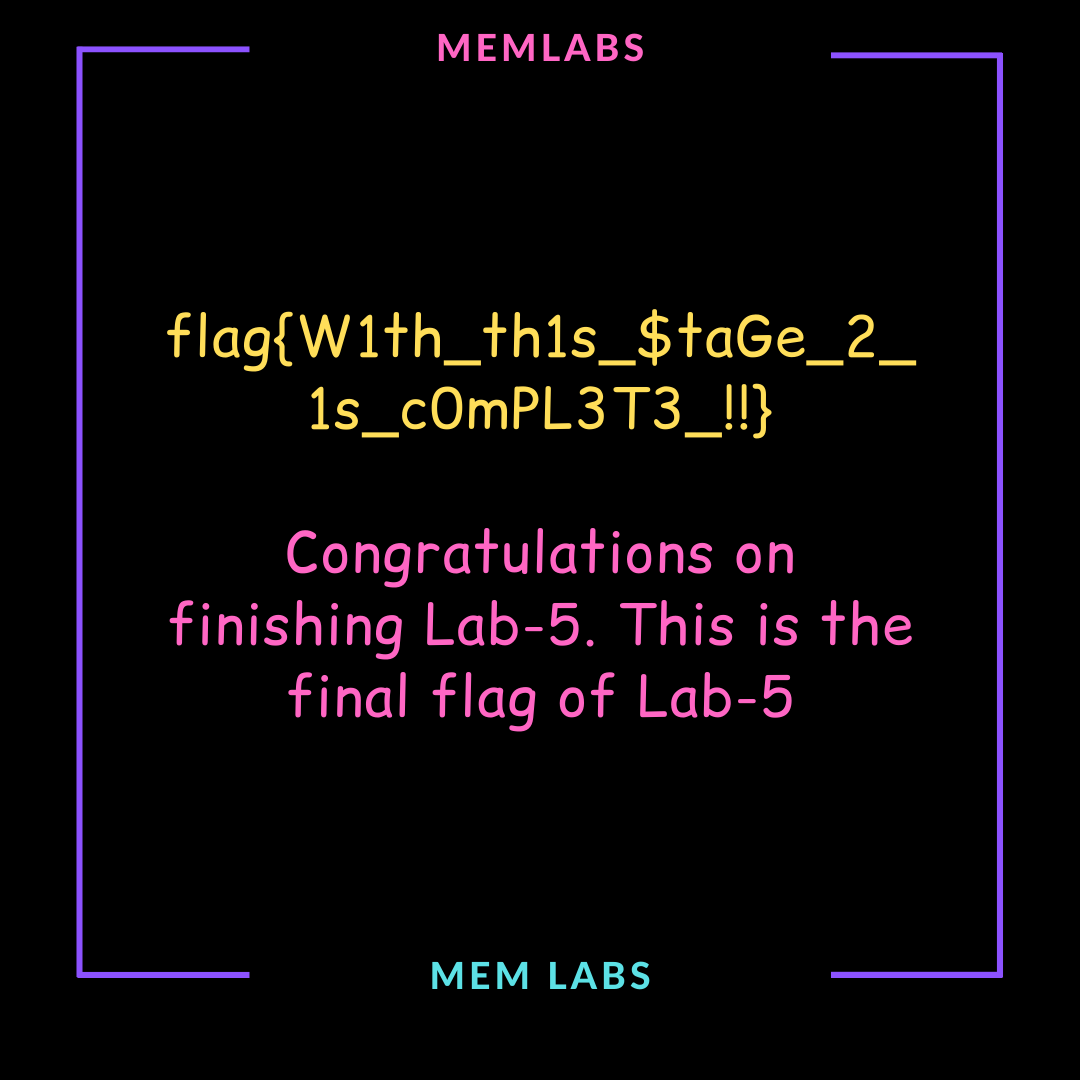
直接出了
flag{W1thth1s$taGe_2_1sc0mPL3T3!!}
Flag 3
前面看到了 notepad.exe,提取文件,转储可执行文件,丢入IDA:
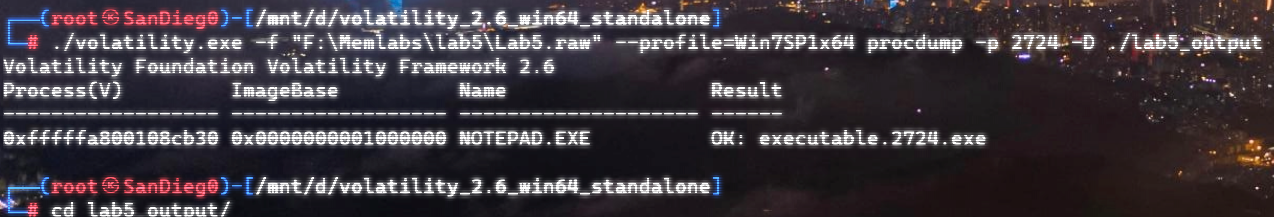
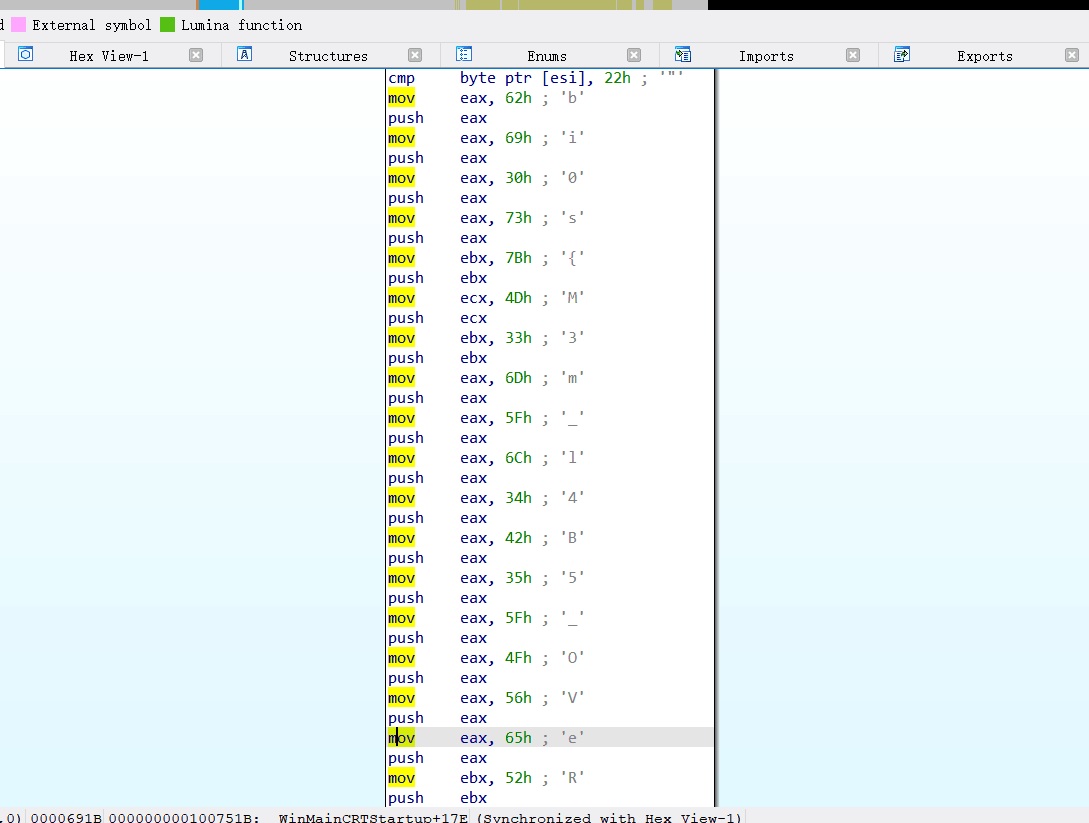
flag3:bi0s{M3m_l4b5OVeR!}
MemLabs Lab 6 | The Reckoning
下载链接:MemLabs Lab 6
Challenge Description
We received this memory dump from the Intelligence Bureau Department. They say this evidence might hold some secrets of the underworld gangster David Benjamin. This memory dump was taken from one of his workers whom the FBI busted earlier this week. Your job is to go through the memory dump and see if you can figure something out. FBI also says that David communicated with his workers via the internet so that might be a good place to start.
Note : This challenge is composed of 1 flag split into 2 parts.
The flag format for this lab is: inctf{s0me_l33t_Str1ng}
我们从情报局收到了这个内存转储。他们说这个证据可能包含黑帮 大卫·本杰明 的一些秘密。这个内存转储是从本周早些时候被 FBI 逮捕的他的一名手下那里获取的。你的工作是通过内存转储,看看你是否能找出一些东西。联邦调查局还表示,大卫通过互联网与他的手下交流,因此这个内存可能是一个很好的案件突破口。
注意 :此挑战由 1 个flag 组成,分为 2 个部分。
本实验的flag格式为:inctf{s0me_l33t_Str1ng}
Progress
The first part of flag
。。。
排查一下可疑进程:
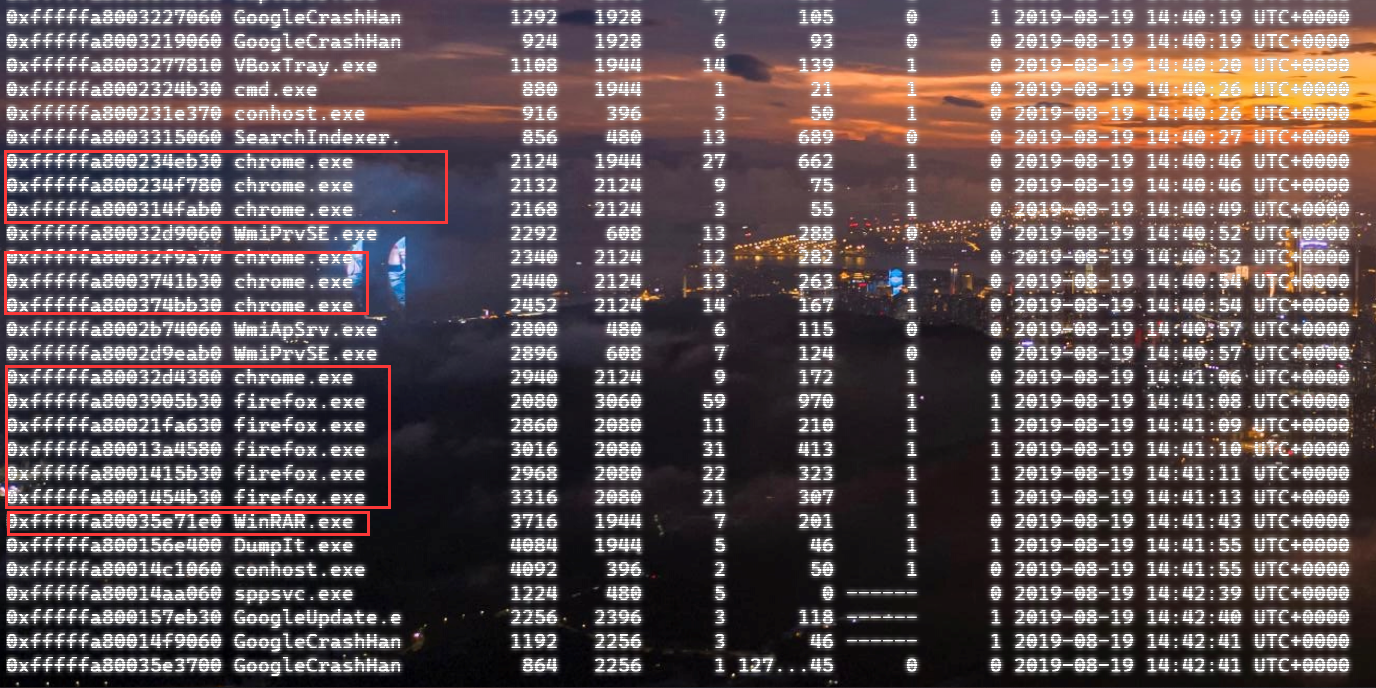
先看WinRAR.exe吧
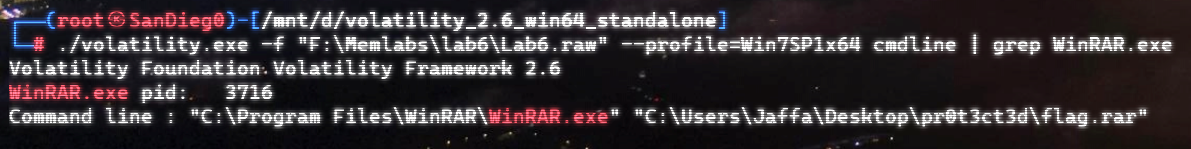

提取一下:
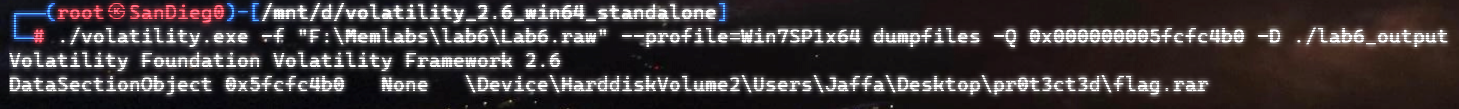
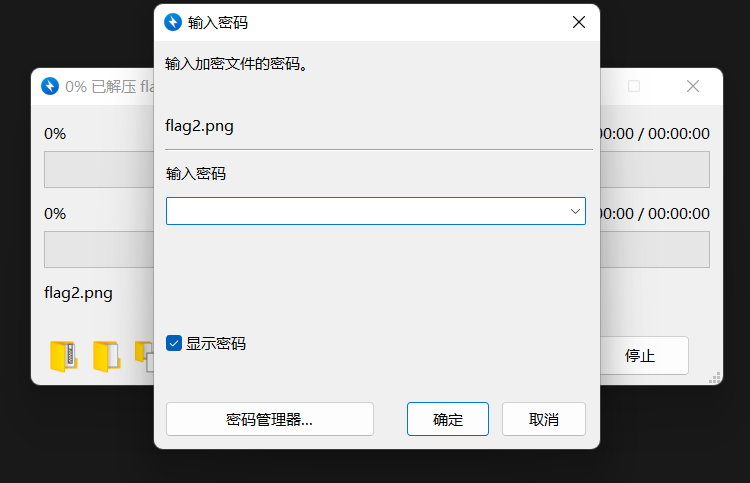
经典,又是加密。。。

🤔emmm,有点生硬:


First Part:aNAm4zINg!_igU3Ss???}
The second part of flag
还有浏览器历史,之前安装过了插件:https://github.com/superponible/volatility-plugins
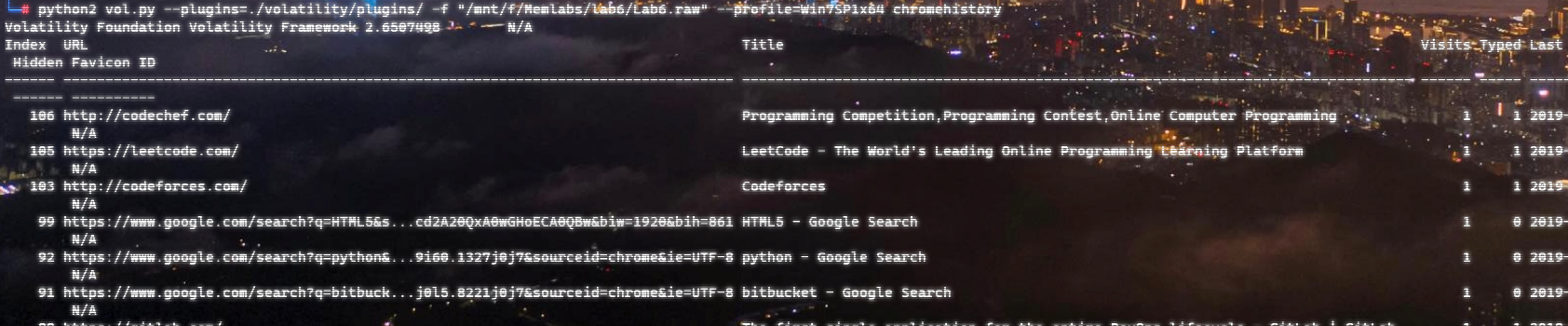
向下翻,有这么一条:

有一条回收站:
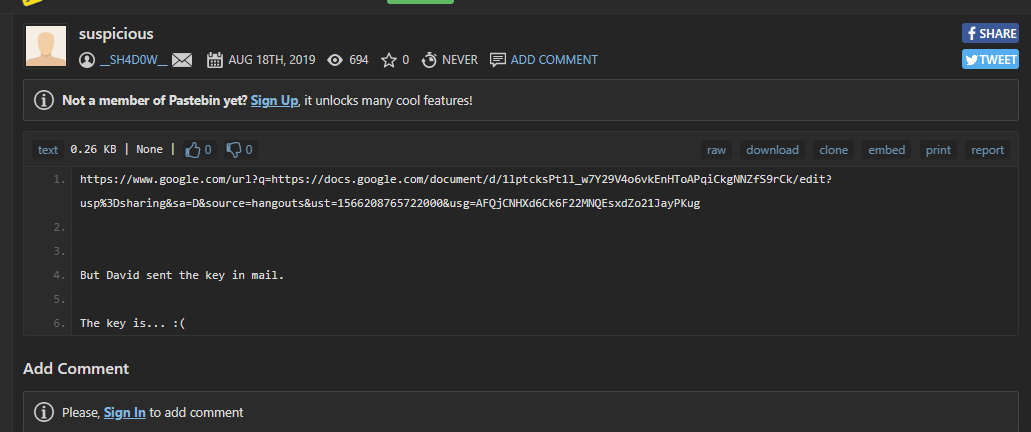
看一下回收站的链接:
Important - Google 文档,google文档
额,全是拉丁语,不过幸好,有Google 翻译
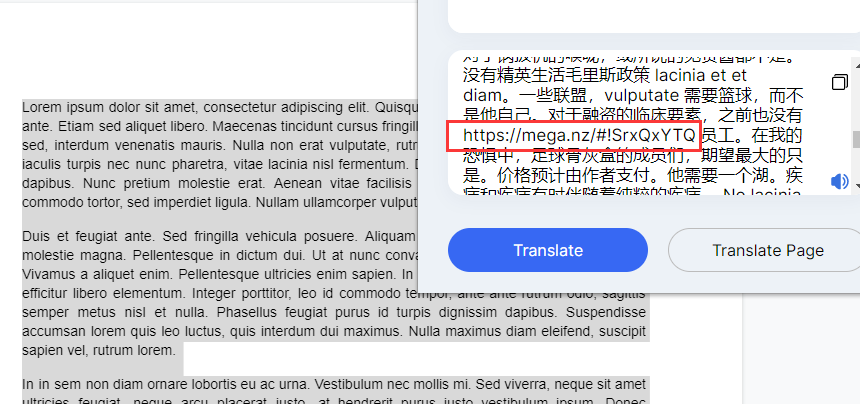
有个网盘链接:Mega网盘
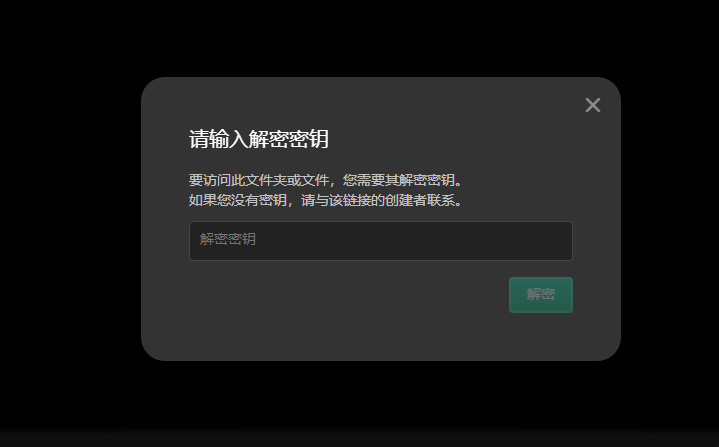
emm又有加密
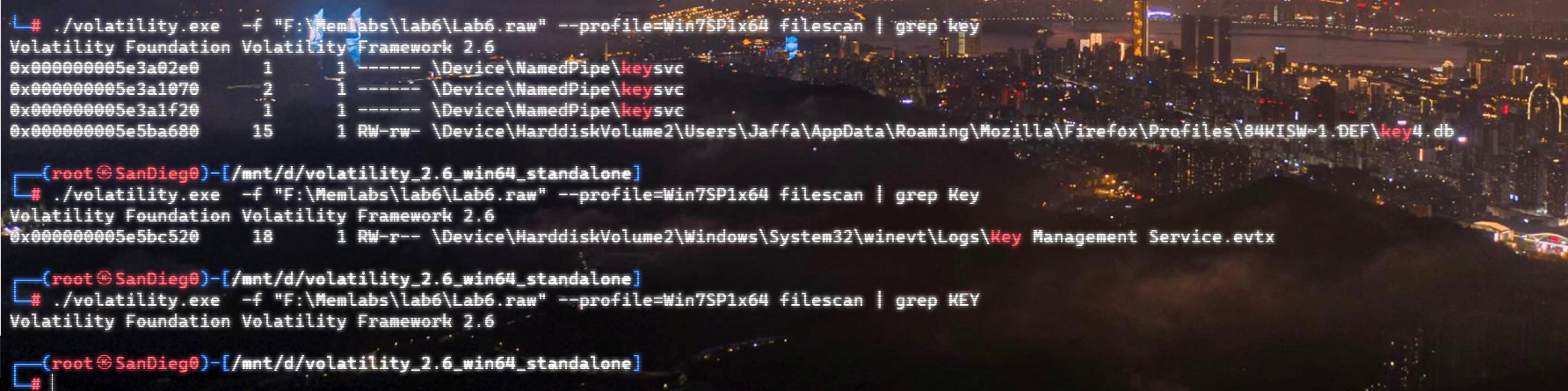
靠运气找Key果然还是行不通吗呜呜呜
直接 strings 全局搜:
strings Lab6.raw | grep "Mega Drive Key"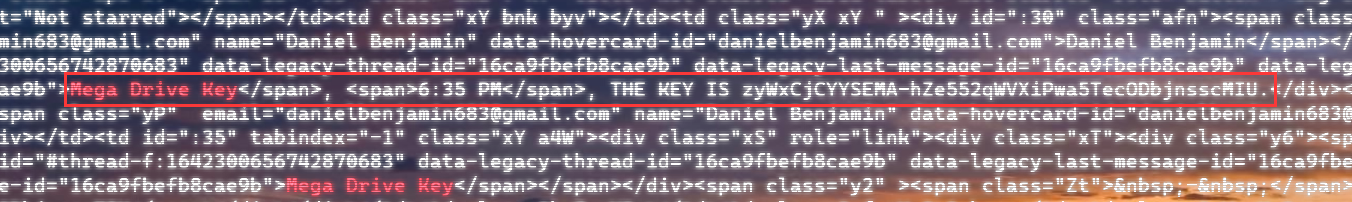

直接看是打不开的,拖进Winhex看看
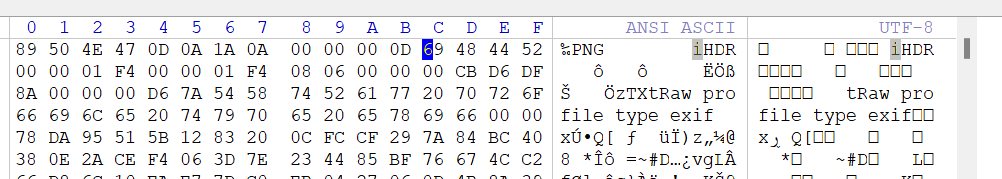
这个地方要大写的IHDR,修复一下,16进制从69改成49
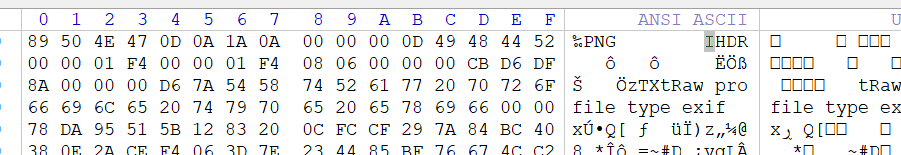

Second part:inctf{thi5cH4LL3Ng3!sg0nn4b3?
综上,flag为:inctf{thi5cH4LL3Ng3!s_g0nn4b3?_aNAm4zINg!_igU3Ss???}

