从寂静的小镇到整座城市,缅甸边境的一大片土地已经成为了跨国犯罪集团的中心,这些集团强迫人们进行大规模的网络诈骗犯罪活动,每年诈骗金额高达数万亿美元。这些诈骗中心在当地迅速蔓延,把人当作商品一样进行贩卖、强行关押、实施其他侵犯人权的行为,并受其胁迫在全球范围内实施诈骗,而缅泰边境的妙瓦底地区正是世界上诈骗中心最集中的地区之一。由于缅甸军政府、叛乱组织和地区军阀之间分裂的地缘政治格局,助长了这些犯罪集团的扩张,从小型的林间工棚到大型的城市院落,由诈骗集团产生的巨额收入支持着他们的日常活动并为缅甸军政府的暴行提供大量资金。
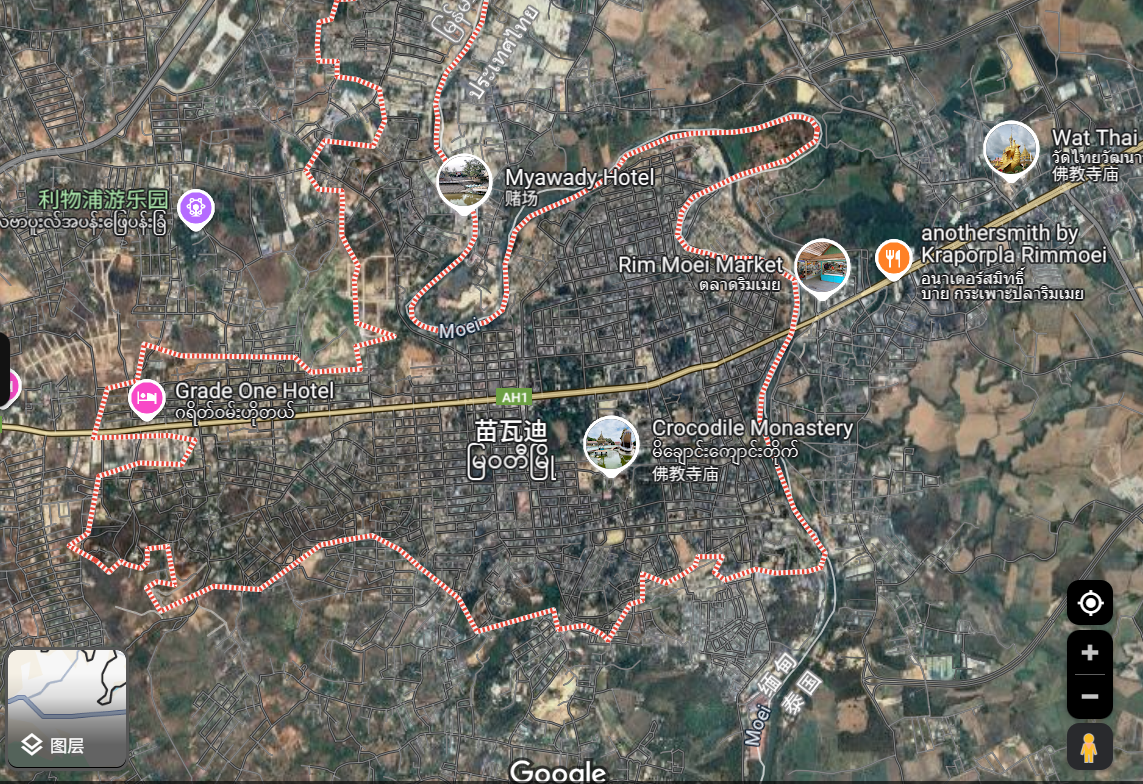
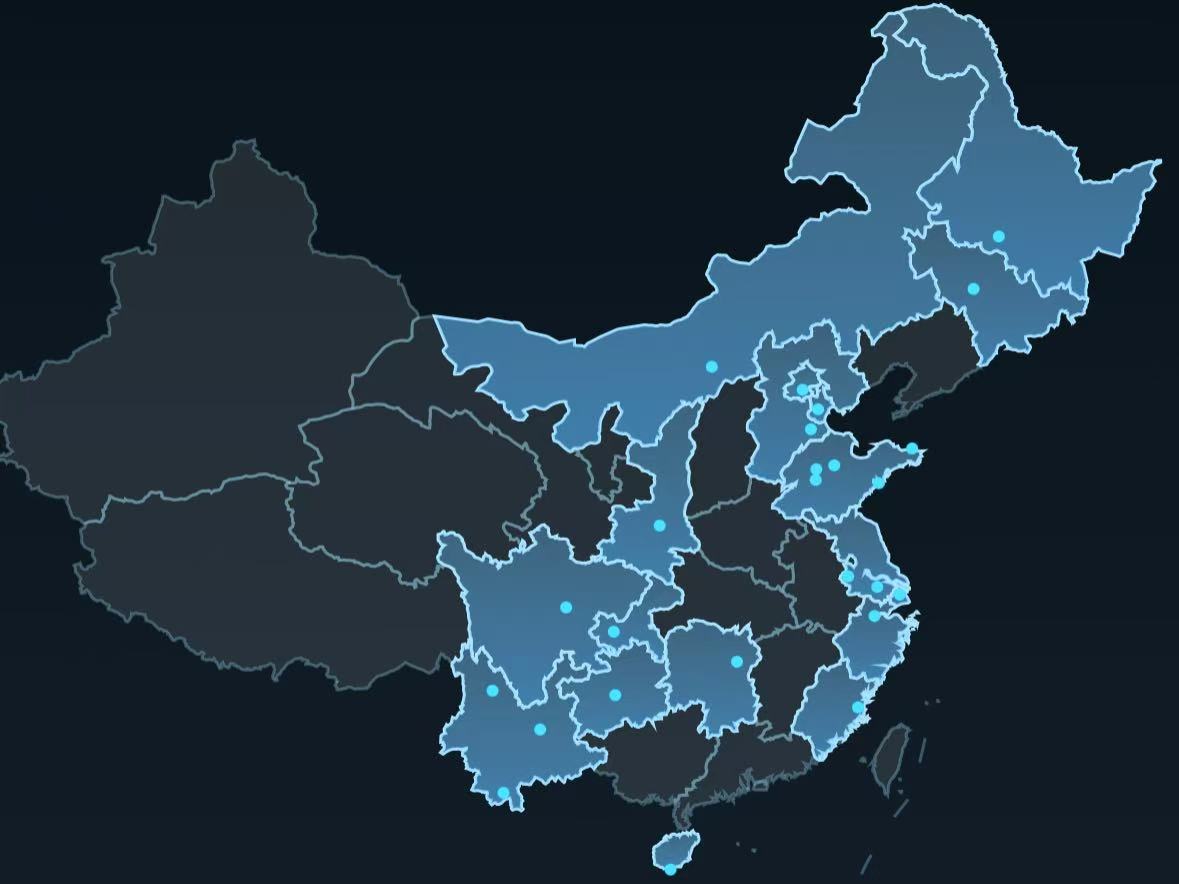
尽管缅甸军政府公开反对,但2024年的手机地理定位数据显示,妙瓦底诈骗中心与首都内比都,以及不同诈骗中心之间的频繁流动,揭示了潜在的犯罪聚集区域。具体情况如下:
- 这些设备经常在诈骗园区(如水沟谷和KK园区)与首都的政府大楼之间频繁出现,表明有组织犯罪与缅甸军政权之间存在某种联系。
- 这些设备在隶属于不同犯罪集团的诈骗园区(如东美园区和泰昌园区)之间流通,表明各个犯罪集团之间也有在进行“合作与协商”。
背景
当地时间2021年2月1日凌晨,缅甸发生军事政变,国家权力被移交给国防军总司令敏昂莱,随后几年间,缅甸军政府失去了对大片地区的控制权,导致犯罪集团得以扩大活动范围。这些组织与原缅甸军政府下属、索奇督上校领导的克伦民族军 (KNA)、民主克伦佛教军(DKBA)等其他武装组织以及各地区军阀合作,将泰缅边境的一片地带变成了世界上诈骗中心最集中的地方之一。2017年,索奇督上校与柬埔寨籍华裔佘智江领导的亚太国际控股集团合作,在佘智江支付470万美元的首付款后,开始在水沟谷开发亚太新城。此外,与14K组织头目尹国驹领导的东美集团还达成了一项开发赛西港的协议。

当地武装组织正是通过向水沟谷等犯罪园区的赌博和电诈企业提供了土地和安全保障获得收入。
这些诈骗中心的出现,很大一部分原因是东南亚地区在博彩领域的法律约束不够严格,大量的犯罪组织受东南亚较为宽松的法律环境所吸引,同时为了应对中国对跨境赌博和洗钱的严苛打击态势,在赌场和酒店方面投入巨资,吸引数百万游客前往该地区。然而,新冠疫情的爆发,导致当地旅游业崩溃,迫使这些组织将赌场业务多元化,实施诈骗活动,吸引来自世界各地的工作人员,强迫他们参与针对全球受害者的网络诈骗。
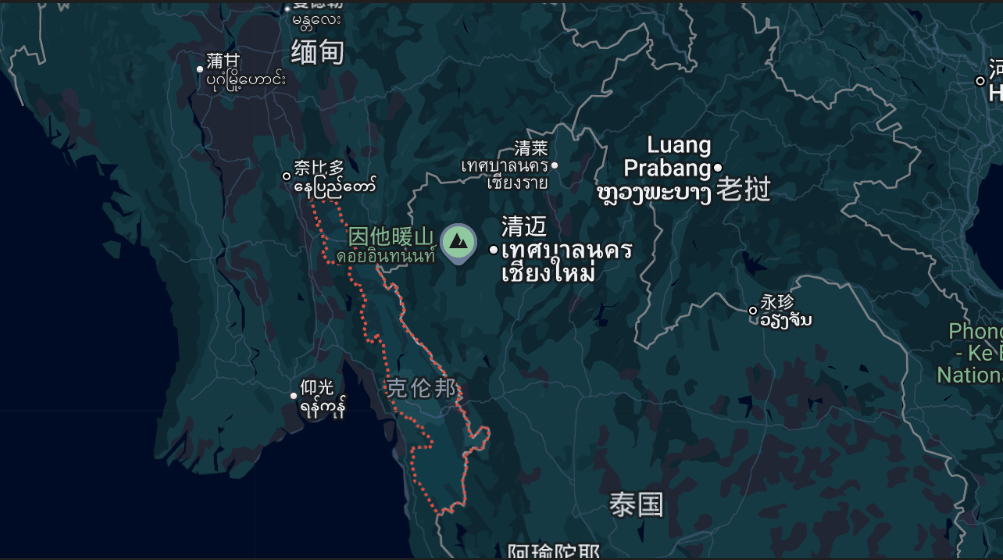
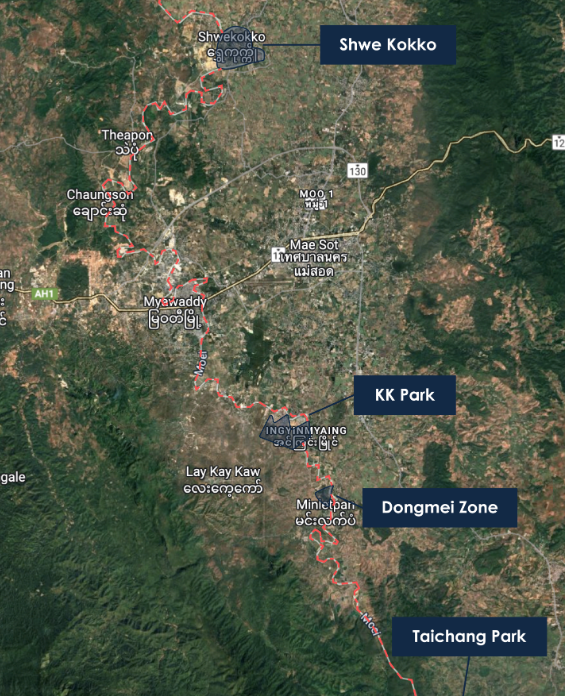
这些中心在掸邦(与中国、老挝和泰国接壤)和克伦邦(与泰国接壤)犯罪行为最为猖獗,当地法治意识淡薄,缺乏管理,缅甸军政府与叛乱组织之间的冲突造就了一种当地无法无天的社会环境。掸邦北部大部分地区被叛军控制,克伦民族联盟 (KNU) 及其武装派别克伦民族解放军 (KNLA) 在克伦邦割据一方。2023年,缅甸北部地区开始严厉打击网络犯罪。打击行动始于佤邦,随后果敢边防军被击败,网络犯罪遭受重创,数万名中国公民遣返回中国,而诈骗中心也被迫搬迁到妙瓦底周边。2025 年 2 月,中国和泰国与缅甸军政府合作,针对缅北犯罪中心展开打击,泰国切断了与缅甸边境地区的电力供应。
尽管缅甸军政府公开谴责并打击这些诈骗网络,但它们之间存在着共生关系。为了换取默许和安全保护,这些诈骗中心会将部分收入输送给克伦民族军。有消息称,克伦民族军与缅甸军政府共享诈骗中心收入,而敏昂莱则与克伦邦和掸邦的主要诈骗园区幕后老板保持联系。
园区
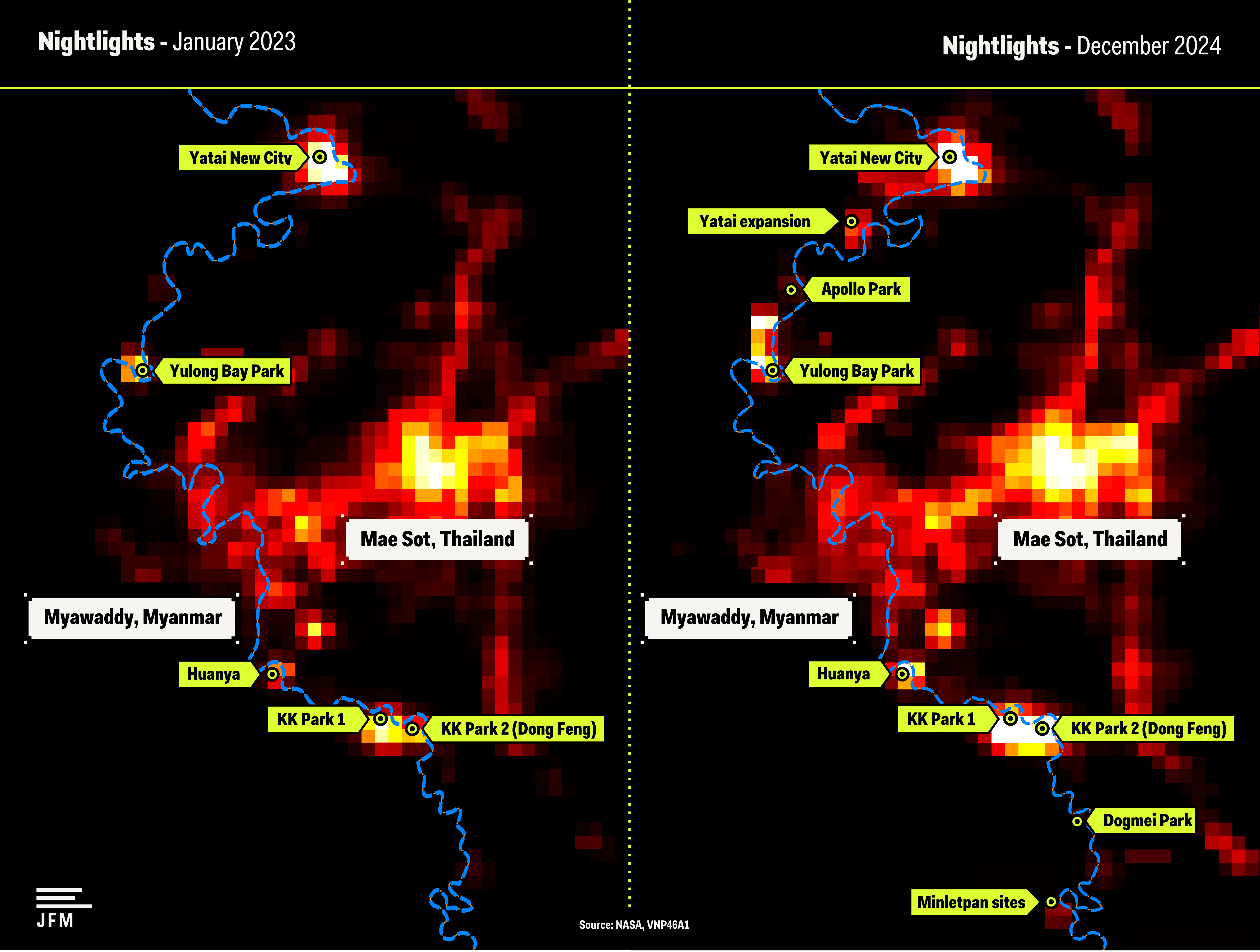
KK园区
目前,它由两个主要区域组成,通常被称为KK园区1号和KK园区2号。
2024年,区块链分析公司Chainalysis的一项调查发现,仅在KK园区内运营的一家诈骗集团在不到两年的时间里就从受害者手中骗取了超过1亿美元。考虑到该地区的犯罪团伙数量,估计实际数字要高出数十倍。
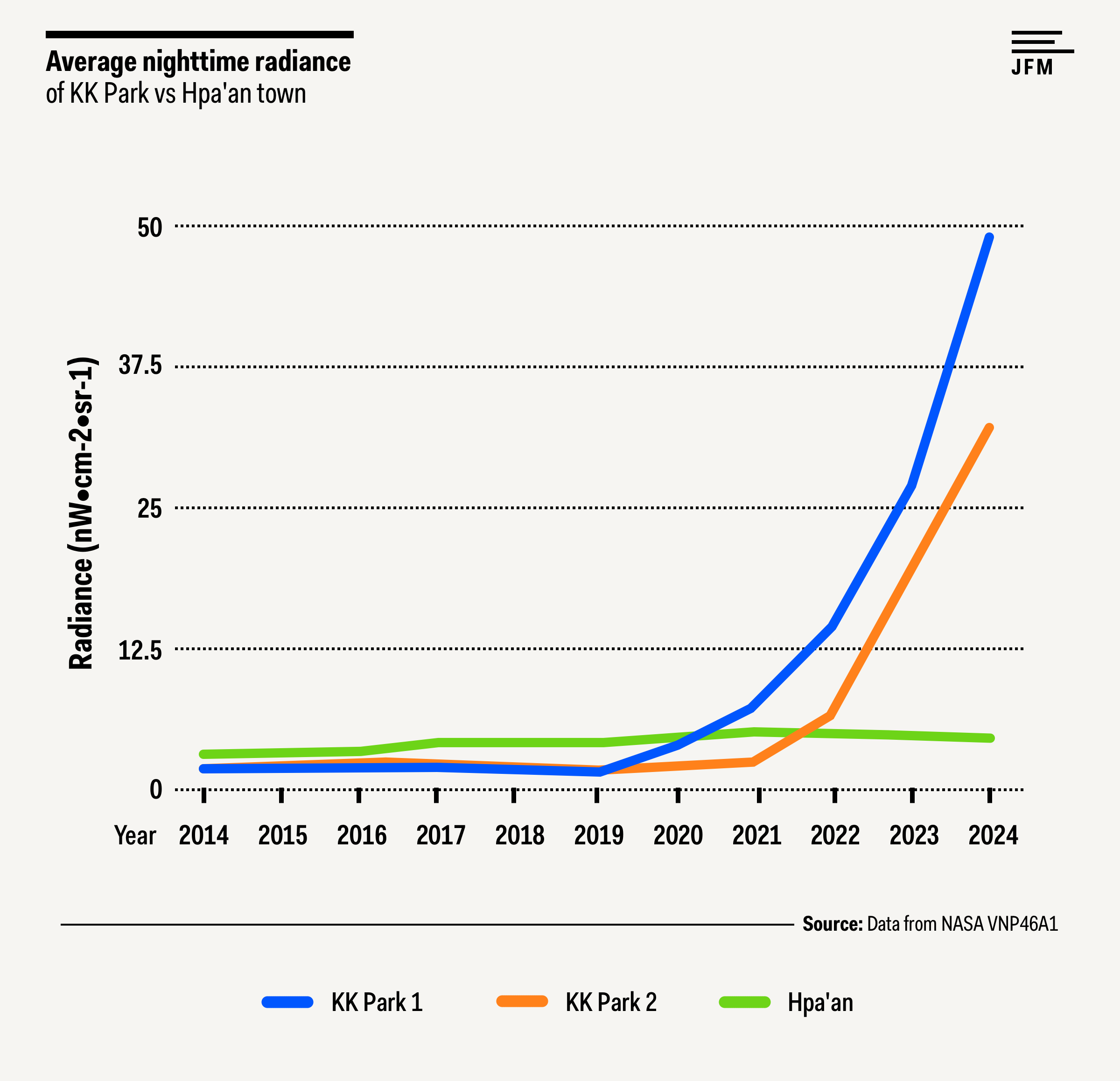
2024年2月至12月期间,KK园区1号和KK园区2号内新建了20多座建筑,连接两地的大片区域也已清理完毕,准备建造新建筑,卫星图像中可见多处地基。这两个区域的每日夜间辐射亮度数据显示,自2022年年中以来,辐射亮度迅速上升。与克伦邦首府帕安的夜间辐射亮度相比,这一增长尤为明显,帕安近年来的夜间辐射亮度实际上略有下降。

亚太新城
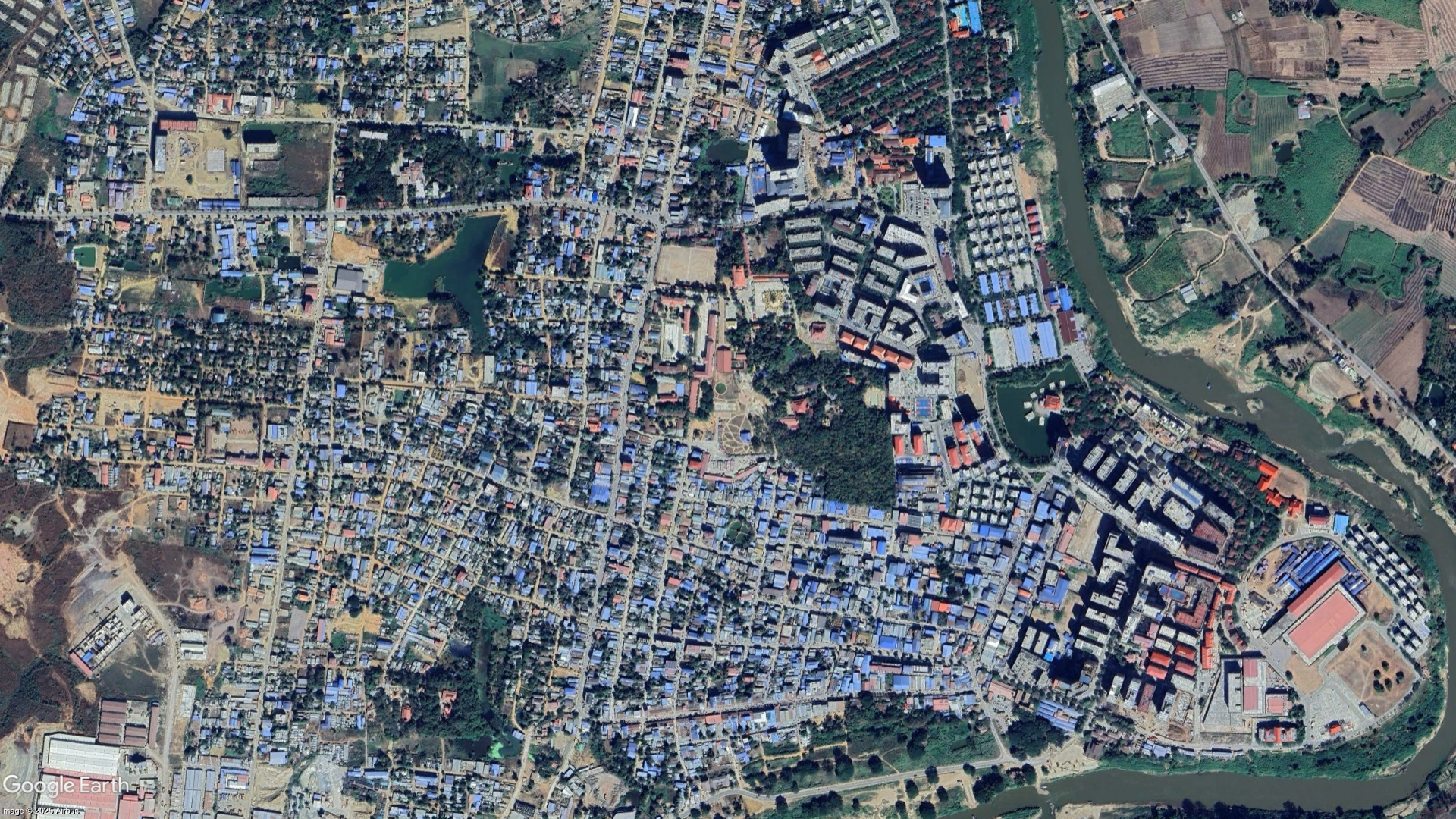
尽管相距 1000 公里,两个大型土地开发项目(一个在缅甸的克伦邦,另一个在柬埔寨的长湾)却有着惊人的相似之处:这两个项目都占地数千公顷,并计划建设机场、酒店和赌场;它们都位于尚待开发的角落;它们都被指控与网络赌博和其他非法活动有关,并且都被误认为是国有企业。
这两个项目都与同一位华裔商人有关:佘志江。
水沟谷是妙瓦底乡北部的一座城市,主要由亚太国际控股集团(亚太)建设。亚太是一家在香港注册的公司,其前董事长是柬埔寨华裔国民佘志江。佘志江目前在曼谷监狱等待引渡回中国,他被指控在东南亚经营非法赌博业务。2016 年,佘志江与索奇督达成协议,由亚太集团将瑞谷口从一个小村庄改造成一个度假城市,并受到克伦民族军的保护。项目于 2018 年获得投资项目批准。亚太集团的建设超出了其投资许可的限制,并在赌场在缅甸合法化之前就开始运营,引起了全国民主联盟政府的审查。尽管佘志江经常被描述为中国人,但他最初在缅甸亚太的公司记录中使用的名字是 Tang Kriang Kai(后来改为 She Zhi Jiang),并且他的国籍是柬埔寨人。柬埔寨政府文件显示,2017 年 1 月,王室下令授予佘志江公民身份,名字为 Tang Kriang Kai,而不到三周后,他就在缅甸投资与公司管理局注册了缅甸亚太公司。2022年在泰国因国际通缉令被捕。克伦边防军仍然忠于佘志江,2024年,齐图为他组织了一场祈祷仪式。

数据调查
调查追踪了 2024 年 1 月至 12 月期间检测到的符合以下条件的设备移动情况:
- 在妙瓦底周边的四个已知诈骗中心之一至少检测到一次此设备,并且在内比都政府部门辖区及其周边政府部门住宅区至少检测到一次此设备。共发现7台符合此标准的设备。
- 在妙瓦底江周边已知的四个诈骗中心位置中,至少有两个位置且至少检测到一次设备,共计213 台设备符合此标准,泰昌园区只有1个设备符合此标准。2024 年,符合此标准的设备有109台来自东美园区。
我们将这些限制访问地点之间的移动可以理解为一个更广泛的网络或行动角色的潜在迹象,将这些原本独立的站点连接起来,这些连线表明它们之间存在着十分紧密的关联。
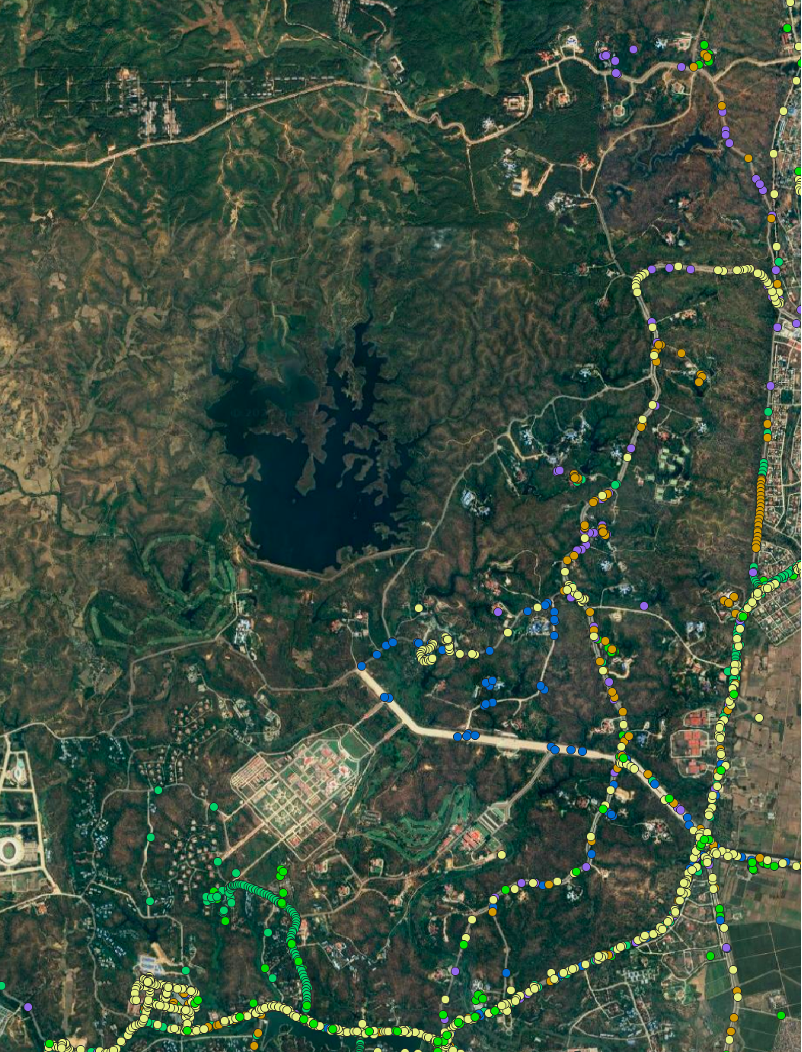
有 6 个设备,暂定为 A、B、C、D、E 和 F ,在水沟谷和内比都的政府部门之间频繁移动:
- 设备A:于2024年6月16日在内比都的南乌寺(Nan Oo Pagoda)被发现,该地点紧邻联邦议会(缅甸立法机构)。这表明该设备所有者可以进入受严密管辖的政府区域,因为该佛塔的建筑群正位于联邦议会的内部区域。
- 设备B:多次造访缅甸外交部、多个部委办公楼和卫生部。该设备还曾造访水沟谷郊外一处不明建筑,该建筑距离自由水上乐园(亚太集团旗下企业)不到一公里,以及谷歌地图上标记为“拟建工业区”的约 76 英亩空地。根据卫星图像,该空地在 2024 年 2 月至 12 月期间遭到砍伐。
- 设备C:曾出现在内比都的交通运输部和部长官邸,还拜访了疑似索奇督的住所。该设备所有者常驻在仰光,然而,该设备在7月份访问了内比都和水沟谷之后,定期访问内比都。根据这些行为分析,该设备所有者很可能拥有进入缅甸军政府管理区域的权限。
-
在访问其他地区之后,2024 年 8 月在水沟谷发现了 D、E 和 F设备。
- 设备D:在抵达水沟谷前约两周曾到访自然资源与环境部,并在约两周后在能源部被探查到,表明它可能在各个部门之间往返。
- 设备E:在抵达水沟谷前,在内比都经历了一系列活动:在商务部、内比都农村公路发展部和民族事务部均被发现。
- 设备F在缅甸中央银行、交通通讯部、体育与青年事务部以及商务部均有出现。值得注意的是,据报道,缅甸中央银行是帮助缅甸军政府逃避国际制裁的主要参与者。
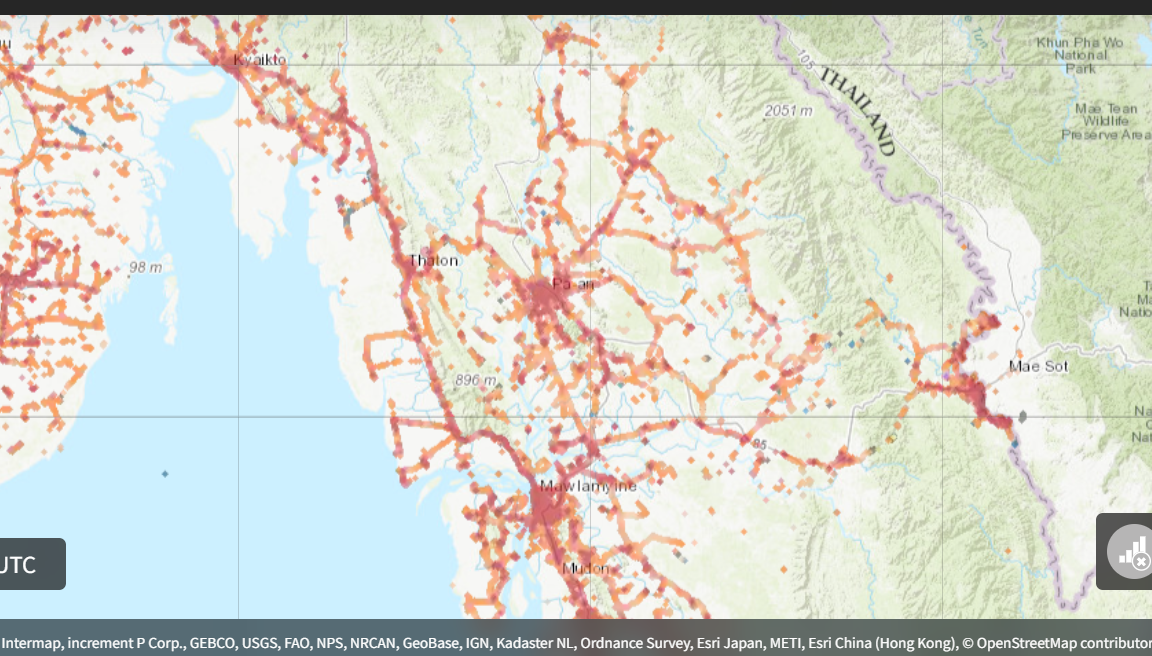
设备
设备 A
- 2024年7月13日至7月17日,A设备在水沟谷(Shwe Kokko)被发现。该设备主要停留在一个不起眼的购物区,但也曾到访过谷口度假村(Kokko Resort)和亚太员工宿舍(Yatai Staff Housing)之间的一个路口。在到达水沟谷之前,该设备于6月16日在内比都的南乌寺(Nan Oo Pagoda)被发现。
设备 B
- 3月16日至3月28日,B设备位于水沟谷(Shwe Kokko)郊外一处空地上的不明建筑内。此前,它曾于2月26日造访过缅甸外交部。同年11月至12月期间,B设备多次造访内比都的重要地点。11月15日和12月3日,该设备被确认位于已知的部长官邸内。11月15日,B设备还造访了内比都部委区最南端的卫生部大楼。12月10日至12月30日,B设备三次造访了部委区北部的卫生部大楼,12月29日,B设备再次在缅甸外交部被发现。
设备 C
- 7月初,C设备在内比都的各部委办公楼内被发现,并于月底前水沟谷(Shwe Kokko)。7月2日,该装置访问了交通运输部,并于7月3日以及7月9日至10日期间在各部委办公楼内被发现。7月23日,C装置出现在水沟谷(Shwe Kokko)的亚太新城(Yatai New City)内,并疑似造访了索奇督(Saw Chit Thu)的住所。该装置在2024年的大部分时间里都位于仰光市内,7月它访问了内比都和水沟谷之后,继续定期造访内比都。
设备 D
- D设备于2024年7月22日在缅甸自然资源与环境保护部被发现。两周后,它于8月4日出现在亚太新城内。不久之后,它返回内比都,并于8月13日在能源部被发现。
设备 E
- 2024年8月中旬,E设备造访了内比都的多个重要部委。8月12日,它造访了商务部南北两处办公楼,并于8月15日再次造访了商务部。8月14日,它访问了内比都农村公路发展部,8月15日又再次访问了该部。同一天,它还出现在民族事务部。不到一周后,E设备于8月20日出现在水沟谷(Shwe Kokko)和湄索(Mae Sot)之间的已知边境口岸,并从8月20日至8月23日多次访问了亚太新城(Yatai New City)和沟谷度假村(Kokko Resort)。
设备 F
- 2024年5月和7月,F设备多次出现在内比都。5月21日,该设备在缅甸中央银行被发现,7月9日,该设备在交通运输部、体育与青年事务部和商务部被发现。7月29日,该设备进入卫生部的两个办公楼,7月30日,该设备再次进入体育与青年事务部。9天后,即8月8日,该设备在亚太新城内被发现。
参考文献
- https://c4ads.org/commentary/hot-lines/
- https://www.irrawaddy.com/opinion/analysis/the-hidden-fallout-from-chinas-cross-border-crime-crackdown-in-myanmar.html
- https://www.frontiermyanmar.net/en/the-mystery-man-behind-the-shwe-kokko-project/
- https://www.nperf.com/en/map/MM/1310460.Martaban/137098.Mytel/signal?ll=17.11979250078707&lg=97.70864144562599&zoom=9
- https://www.voanews.com/a/in-myanmar-internet-restrictions-and-surveillance-increase/7733716.html